Twilio's Authy Breach: The Attack via an Unsecured API Endpoint
A recap of Twilio's Authy app breach, which exposed 33 million phone numbers. Including the impacts, lessons learnt and recommendations to enhance your security.

In a recent incident, Twilio's Authy app has suffered a significant breach, exposing 33 million phone numbers. The attack by an adversary named ShinyHunters, who leaked a CSV text file, occurred through an unsecured API endpoint, according to Twilio's official communication. It allowed adversaries to verify the phone numbers of millions of Authy multi-factor authentication (MFA) users.
#Twilio has confirmed that an unsecured API endpoint allowed #ShinyHunters threat actors to verify and leak the phone numbers of 33 million of Authy MFA users:#APISecurity
— Sam Stepanyan (@securestep9) July 4, 2024
👇https://t.co/JFYH3c0COi pic.twitter.com/izQa025MZB
Even though Twilio has taken action to secure this endpoint and no longer allows unauthenticated requests, this incident is a stark reminder of the necessity to implement strong security measures for your APIs.
Incident Recap
Twilio, a leading cloud communications provider, revealed that threat actors exploited an unsecured API endpoint associated with Authy, its popular two-factor authentication (2FA) app.
This breach was first disclosed by the cybercriminal group ShinyHunters, who leaked a CSV file containing the compromised phone numbers on BreachForums.
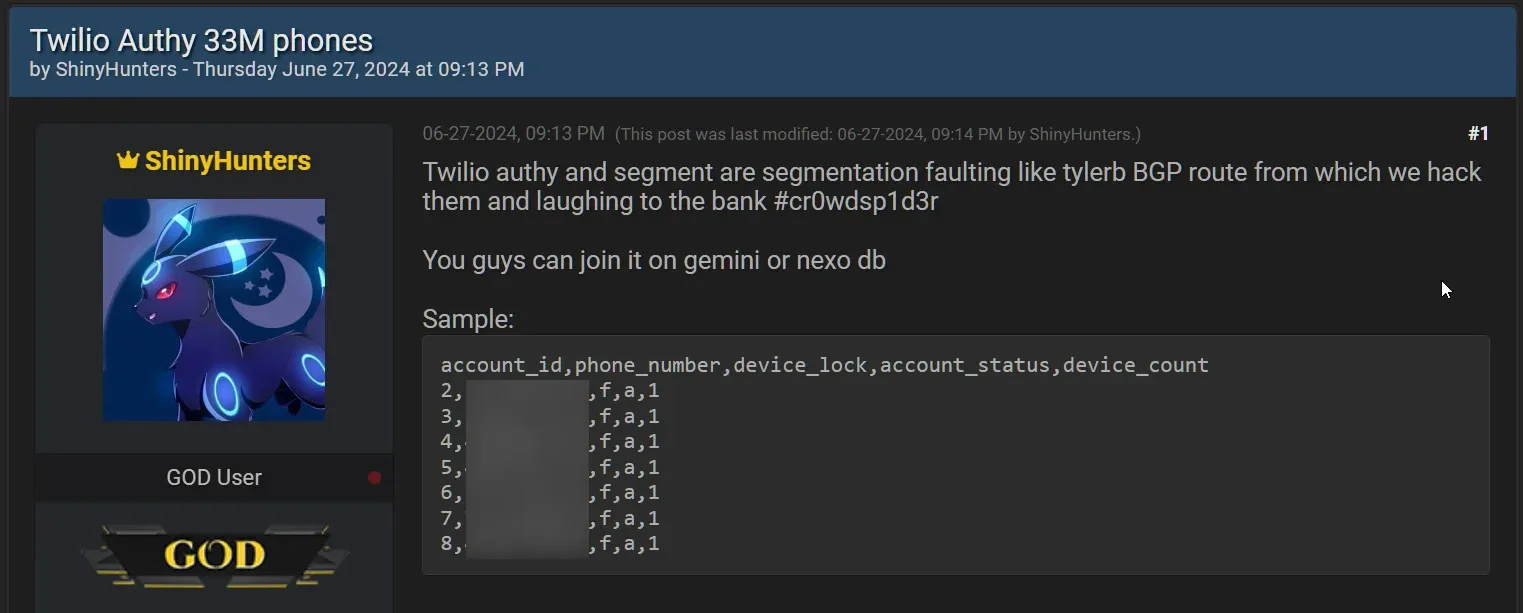
The CSV file included 33,420,546 rows of data, encompassing account IDs, phone numbers, an "over_the_top" column, account statuses, and device counts.
The incident was confirmed by Twilio, which stated that the unauthenticated endpoint had been secured and that no further access to Twilio’s internal systems or other sensitive data had been detected.
Twilio’s Response and User Recommendations
In response to the breach, Twilio took steps to secure the compromised endpoint, preventing unauthenticated requests. The company also issued a precautionary advisory for all Authy users to update their apps to the latest versions (Android: 25.1.0 or later, iOS: 26.1.0 or later) to incorporate the newest security updates.
Despite the swift action to secure the endpoint, Twilio warned that the exposed phone numbers could still be used for phishing and smishing attacks. Thus, users are urged to maintain heightened vigilance and to scrutinize any unexpected texts or messages they receive and should consider enabling additional security features such as biometric authentication and app-specific PINs to further protect their accounts.
Lessons Learned
The breach highlights several critical issues present in API security:
- API Management and Security: The exploitation of an unauthenticated endpoint reveals significant gaps in API security. This breach serves as a stark reminder of the importance of securing all API endpoints with robust authentication and authorization mechanisms, especially in light of the API Sprawl taking place in recent years. A recent Escape's study revealed over 18,000 publicly exposed API secrets across 1 million popular domains, with 41% deemed highly critical. This shows the significant potential for unauthorized access and data breaches. It is likely only a matter of time before these leaked API keys can be used in a future attack.
- API Visibility: The incident shows that organizations need to remain vigilant against cyberattacks that could target their APIs, particularly those managing large volumes of sensitive data. Automated API Discovery and Inventory are now crucial.
- Timely Updates and Patches: Regular updates and security patches are essential in mitigating potential vulnerabilities. Twilio’s call for users to update their Authy apps is a step in the right direction to enhance security measures.
Recommendations
The following measures are recommended for users and organizations alike:
- API Security Best Practices: Organizations must implement robust API security practices, including :
- Implement Strong Authentication: Ensure all API endpoints require authentication using robust methods like OAuth tokens, API keys, or JWT (JSON Web Tokens). This prevents unauthorized access by verifying the identity of clients before granting access to resources.
- Enforce Authorization Controls: Implement fine-grained authorization to limit access based on user roles and permissions. This ensures that authenticated users can only access resources they are authorized to use, reducing the risk of unauthorized data exposure.
- Automated API security testing: Employ automated API security testing tools like Escape DAST. By leveraging automated solutions tailored for API security testing, you can efficiently identify vulnerabilities, exposed sensitive data, and weaknesses that manual testing might overlook.
- Implement or enhance API Governance: Governance is about establishing policies, frameworks, and barriers that go beyond individual API management platforms. Managing APIs well means documenting them thoroughly, keeping track of their lifecycles, listing all sensitive data they handle, and making sure only authorized access is allowed. Discover more about how to implement efficient API governance policies here.
- Test Early: Integrate security early in the software development lifecycle to detect and mitigate threats before they're in production. Make sure you choose tools that can be user-friendly for your developers and provide actionable remediations. It'll be easier for your development team to implement the fixes if they have a code snippets associated with their development frameworks.
- Regular Audits and Testing: Conduct regular security audits and penetration testing of APIs to identify vulnerabilities proactively. Implement necessary fixes and improvements based on audit findings.
- Security Training: Introduce security training for your API developers to help them follow secure coding practices and ensure you are covered on all sides.
The breach of Twilio’s Authy app is a reminder of the very real risks that can impact your organization everyday. It highlights the importance of securing your API endpoints and the need for proactive API security measures.
Want to prevent breaches like Twilio with Escape DAST?
Learn from our product expert how you can detect even business logic flaws
Get a demo💡Want to learn more? Discover the following articles:
