Top 5 Web3 security breaches: A deep dive into DApp frontend and API vulnerabilities
The world is gearing more into a phase of individual ownership of data and digital assets without external interference. This metamorphosis of the web is commonly called Web3. It combines frontend technology, smart contracts, and other components of backend technology, such as indexing, querying, and database management. Smart contracts, a vital by-product (or a feature) of Web3, are at the core of many use cases.
Initially, interacting with smart contracts without an interface was challenging, especially if you didn't have a developer background. That's where tools like Etherscan made a difference, enabling easier interaction.
Developing user-friendly interfaces was necessary to enhance the usability of smart contracts. Despite existing criticism about the complexity of Web3 technologies, the creation of simplified interfaces has led to increased technology adoption. With improved interactivity, user experience, and mass adoption challenges, the main focus is now shifting toward ensuring Web3 security.
Security breaches and hacks are happening more often in the Web3 space. There are many speculations that the cause of these hacks is because the space is only beginning to take shape and that Web3 is still in its infancy. It is also natural that since these hacks are mainly performed on smart contracts, the bulk of the effort of Web3 security is focused on smart contracts. This can leave room for hackers to exploit the vulnerabilities that may exist on the interface side of things.
This guide highlights five of the most significant security breaches in various Web3 protocols.
Based on real-world examples, we’ll propose actionable remedies, solutions, and best practices to handle these cybersecurity challenges successfully.
TL;DR
- Web3 DApps comprise frontend interfaces and smart contracts
- The interface is prone to security vulnerabilities like DNS attacks, API Phishing, Injection, Unauthorized access
- Web3 stakeholders must prioritize security through thorough audits, user education, and ongoing developer training. Registering contracts for audits incentivizes vulnerability discovery while raising awareness about risks through blog posts and guides helps to protect users.
Web3 DApp components
For this guide, the components of a Decentralized Application (DApp) shift from the generic classification of frontend and smart contracts to INTERFACE and SMART CONTRACTS. The simple explanation is that the front end is beginning to include more elements, like Web3 Application Programming Interfaces (API).
In Web2 development, developers know every app needs an interface and a backend. Web3 follows a similar concept: the smart contract serves as the backend. This smart contract contains all the necessary logic for the protocols to function, including crucial information that ensures smooth operation with proper consideration for gas fees and transaction costs.
On the other hand, interfaces are built to provide a nice-looking view that enables users to interact with these smart contracts. This way, users don't have to learn to code. With just a few clicks, they can approve an exchange to spend 100 USDC from their balance without worrying about executing the transaction on the proper chain.
The interface accentuates smart contract(s)
The significance of the interface might not be fully understood. Consider the scenario where two major blockchain inventions, Uniswap (the most forked decentralized crypto exchange) and Compound (the most integrated lending and borrowing protocol according to DefiLlama), were built without an interface. Would they have achieved widespread adoption and contributed over $6 Billion to the DeFi economy? The interface is crucial in making these protocols user-friendly and accessible to a broader audience.
Since these protocols, the blockchain industry has seen some exciting developments. Within the last few years, Chainlink has brought on-chain price oracles to the market, and since then, interest-rate swap protocols, derivative markets, and other sophisticated features have been created. All of these became possible because these developers and builders dared to build an interface for users to interact with even after they built the smart contracts.
5 Examples of security breaches in Web3 DApps (Frontend & API)
Both the frontend technologies and smart contracts in the Web3 can be targets of attacks, but in this guide, we’re focusing on how the frontend can be vulnerable to hacks and how APIs might expose protocols to security breaches as well. We’ve chosen to discuss specific types of hacks based on 2 main factors: the frequency of occurrence and the hack's impact.
After careful examination, we selected the following examples to share with you:
DNS hijacking
Domain Name Server (DNS) hijacking is a type of DNS attack where an attacker manipulates the point of access, thereby redirecting a user to a malicious site to steal the privileged information of the user or to download malware to gain control of the user’s devices.
Let’s assume a crypto exchange decides to go live after months of building and beta testing, and it needs to register a point of entry for its users, hence, a domain name. They came up with a name called CXchange and decided to register the name CXchange.com. Alongside the domain name, the site is given a unique IP address with which the users are directed to access the exchange.
The DNS record now contains both the IP address and a domain name. If an attacker gains access to the DNS record, they can switch the IP address to point to the malicious page they have created. Of course, the domain name CXchange.com still works; the only difference is that the user is not being served the authentic content by the protocol itself but by an attacker. If the user isn't careful, they can provide privileged information to the attacker by filling out a form or taking an authentication test requiring them to provide their password or private key.
MyEtherWallet DNS Attack (2018)
In April 2018, MEW (MyEtherWallet), a free, client-side interface that helps users interact with the Ethereum blockchain, experienced a DNS hijacking attack. The attack followed the basic principle of DNS hijack. Several reports, including one from QUARTZ, confirmed the attackers stole $150,000 from different users who fell for the scam.
According to the report, users noticed that the site they were re-routed to wasn’t the authentic MyEtherWaller website. However, those who didn't notice and ignored the warning that the website’s TLS certificate was signed by an unknown authority (i.e., was self-signed) fell victim to a scam after providing the private keys to their wallet.
Frontend Injection attacks
Frontend injection attacks, sometimes called Cross-Site Scripting (XSS), are a type of vulnerability that attempts to use a webpage or application to deliver or execute malicious code.
This type of vulnerability isn’t new: it’s been carried over from Web2 to Web3. It’s a sneaky trap that can catch users off guard, and the attacker's goal is to steal sensitive information from the users or perform malicious actions on their behalf.
For example, hackers could steal the user's private keys or login credentials, manipulate the DApp's behavior to perform unauthorized transactions, or even redirect the user to a fake DApp that looks like the original but is under the attacker's control.
The attack is usually carried out by exploiting vulnerabilities in the frontend code of decentralized applications (DApps). Common flaws include failing to validate and clean user input properly or not escaping user-generated content before displaying it on the DApps’ interface. Attackers can use various techniques, such as injecting malicious scripts into input fields, URLs, etc.
Phishing attack
Like many of these attacks, phishing attacks are actually from Web2 modified to be usable in Web3. Unlike other forms of attacks that target either the interface or smart contracts, phishing attacks can be a threat to both.
A phishing attack is a social engineering attack technique where the attacker uses ploys like spam mail, wrong links, and other malicious attempts. The goal is to fool unsuspecting victims by exposing private information like their private keys and passwords to an online account or a DApp. Once the attacker has this information, they can impersonate the user and empty their wallet.
MetaMask Phishing attacks
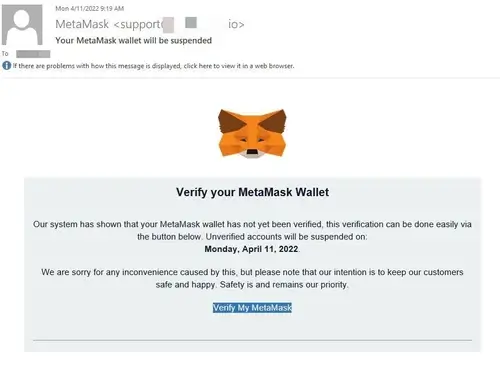
MetaMask is a wallet well-known to many Web3 users. Often referred to as the gateway to the decentralized world, it naturally becomes a target of many cybersecurity threats. Among these, phishing attacks are widespread.
There have certainly been reports of MetaMask users falling victim to this hack, sometimes even more than once. Of course, these incidents aren’t a fault of MetaMask, but we’d like to highlight again: unsuspecting users are the most vulnerable. Awareness and understanding of these security risks within the Web3 community can go a long way in protecting against such threats.
In Q1’2023, it was discovered that some users fell victim to a phishing scam by interacting with a Typeform link masquerading as an authentic link for validators by MetaMask.
API security vulnerabilities
Web3 is shaping the future of various sectors like finance, health, music, and technology. While some aspects are already thriving, others still need refinement. One thing that ties all these achievements together is our use of Application Programming Interfaces (APIs).
Think of an API as a way in which apps or Web3 apps or DApps talk to themselves and exchange information. With the growth of Web3, we see more API providers coming into play, including Thirdweb, API3, Alchemy, and even specific query languages for these APIs like GraphQL. Given the level of reliance on the information provided by these APIs, a vulnerability in the code will extend to the DApp using this API as well.
Infura API Vulnerability (2020)
The Infura API vulnerability of 2020 is a case of an insecure API endpoint. On November 11th, 2020, Infura experienced downtime with their API due to an upgrade they pushed. Before this date, Infura has been running for four years providing stellar and uninterrupted services to its users. This helped build trust and faith between Infura and its users, trust and faith that was put to the test by that unfortunate incident.
Fortunately for Infura, they found the cause quickly and pushed a fix. In a published report, they explained that despite fixing the vulnerability, the damage had been done. While it was unclear who the affected users were and the full extent of the impact, the trust was shattered. Rebuilding that trust takes time, and the cost, both in terms of reputation and potential financial loss, could be substantial.
Unauthorized access to user’s data
Unauthorized access to a user’s data is the by-product of all of the aforementioned, if not all, of the vulnerabilities experienced in Web3. This is simply because when an attacker gains access to this data, it can cause financial loss for the user. If the user owns a contract or a governor of a community contract, their account can be used to act on their behalf without their consent. Besides that, the attacker could also damage the user’s identity and reputation. This isn’t just a hypothetical scenario; It has happened before. This issue could continue to repeat itself without protocols, developers, and users taking proper precautions.
Security measures for frontend vulnerabilities
Protocols and developers must refocus on understanding and addressing these vulnerabilities in the Web3 space. You never know what vulnerabilities you knowingly or unknowingly cause during both development and deployment. This is why it’s recommended that protocols register their smart contracts and interfaces for audits. This way, security researchers are incentivized to find and report these vulnerabilities for fixes. Several security platforms, such as Immunefi and Code Arena are already taking this approach, but integrating comprehensive best DAST tools, like Escape DAST, can further improve this process by continuously scanning for vulnerabilities in both the frontend and backend layers of your applications.
Protocols also need to invest more in user education. Despite all efforts to safeguard users’ funds and identity, protocols can’t control where users choose to share their information. Hence, blog posts or guides on the dangers of exposing your private keys or clicking on scam sites should be created and widely shared.
Train and retrain staff and developers to build secure code and follow best practices during development. Developers must learn to implement strong authentication and authorization mechanisms, input validation and sanitization, use HTTPS for secure communication, limit access to sensitive data, and keep APIs updated with the latest security patches.
Conclusion
Security in the Web3 ecosystem is not a one-time effort; instead, it's an ongoing process. Our deep dive into DApp Frontend and API vulnerabilities showed some of the most critical threats, including phishing attacks, DNS injection, and insecure API endpoints.
But understanding these threats is just the beginning. It’s essential to learn from the past examples we provided and actively prioritize security in every aspect of development and user interaction. Education, regular audits, and dedication to best practices - are foundations of robust security.
As Web3 technology advances, so do the tactics of attackers. We must continuously monitor new Web3 security vulnerabilities and enhance our security measures as we continually improve our products and services.
