Top Qualys Alternative: Escape vs Qualys
Looking for a Qualys alternative? In this article, we compare Escape with Qualys to help you choose the right security testing solution

Qualys has been a well-known player in the application security space for many years, particularly in the area of Dynamic Application Security Testing (DAST). However, as security needs have evolved with modern applications and APIs, more organizations are exploring alternatives. Escape, for example, offers a different approach to DAST, focusing on efficiency and accuracy for both legacy and modern applications.
In this article, we’ll compare Escape and Qualys to help you understand the key differences and why some companies are considering a switch.
Why Are More Companies Seeking a Qualys Alternative?
Founded in 1999, Qualys has long been a leading provider of cybersecurity solutions. However, in recent years, Qualys's DAST offering has faced criticism, especially when it comes to testing modern applications and APIs. Issues such as slow scan times, excessive noise, and less accurate results have led many organizations to reconsider whether Qualys DAST is the right fit for today's fast-evolving environments.
Legacy DAST scanners like Qualys often present challenges: difficult configurations, frequent maintenance, and tests that may not align with the specific needs of modern applications and APIs. These tools sometimes rely on irrelevant or outdated tests that fail to find business logic vulnerabilities in modern applications or accurately reflect your API's actual configuration, leading to inefficiencies and gaps in security coverage.
TL;DR: Escape DAST vs Qualys DAST
Now, let's dive into how Escape compares to Qualys. We've decided to build this comparison mainly based on the feedback from former Qualys clients who decided to evaluate Escape as its alternative, but also based on the following sources:
- Qualys official website
- Feedback from an independent industry analyst who used to run DAST scans with Qualys WAS scanner
- Demos and official documentation
- Feedback from security professionals (whether Qualys's and Escape's current customers or not)
| Feature | Qualys | Escape |
|---|---|---|
| Application discovery | 🌕 Can discover web applications via TotalCloud integration (AWS, Azure),MuleSoft API Connectors, and Swagger API Discovery | External discovery and internal discovery from code and through various connectors (Wiz, Akamai, AWS, Postman and others..) for web apps and APIs |
| Testing Approach | Traditional DAST scanner focused on basic vulnerability detection | DAST scanner with a proprietary business logic security testing algorithm |
| API Testing | 🌕 Limited API security features, but recent releases support API discovery and some API-specific vulnerabilities | ✅ Native support for external and internal APIs |
| Scanning scope | 🌕 Web apps and recently introduced APIs, limited to REST APIs with available specifications or Postman collections | ✅ Full API and web app scanning - internal and external (including detected exposed external shadow APIs, zombie APIs, and misconfigurations) |
| Authenticated Testing | 🌕 Limited: basic login, OAuth2, Selenium automation, and form-based authentication. | ✅ Supports authentication mechanisms (OAuth, API keys, JWT, multi-factor auth, Playwright, custom auth workflows.. ). Escape’s proprietary AI agent detects login fields and fills them in automatically, and shows where authentication went wrong |
| Testing in CI/CD | ❌ Super limited CI/CD integration, primarily through API with a lot of manual configuration. | ✅ Native integration with CI/CD pipelines (GitHub Actions, GitLab CI/CD, Bitbucket Pipelines, Jenkins, Azure DevOps, npm) |
| GraphQL Security | ❌ No native GraphQL support | ✅ Supports GraphQL API security testing natively |
| Compliance | 🌕 Standard compliance reporting with recent updates for API compliance | ✅ Detailed compliance reports + Compliance matrix feature for unified compliance view |
| Detected Vulnerabilities | 🌕 Focus on basic vulnerabilities (shown OWASP Top 5 2021) and other common security checks, a lot of manual tweaking required to find something deeper | ✅ Escape covers OWASP API Top 10 and thousands of test scenarios for web apps and APIs across 162 vulnerability categories (security assessments), especially focusing on business logic vulnerabilities like IDOR, BOLA, and access control |
| Custom security tests, including from pentest results / incidents | ❌ No, limited customization options | ✅ YAML-based security tests that require no manual maintenance—support for both discovery and security testing |
| False Positive Reduction & Triaging | ❌ Former users complain false positives and time spent to filter through noise | ✅ AI-based classification to reduce false positives and severity score based on business context and exploitability |
| Remediation Guidance | ❌ Provides very generic recommendations on vulnerabilities and requires developers to manually tailor them. | ✅ Provides developer-ready remediation recommendations tailored to each development framework |
Qualys
Pros
✅ Bundled with other Qualys platform offerings: If your organization is already using other Qualys products, Qualys WAS & API security can be bundled and managed within the same ecosystem
✅ Cost-effective for existing Qualys customers: For organizations already subscribed to the Qualys platform, adding an API security module might be relatively cheap
Cons
❌ Noisy and slow scans: According to a former user feedback, Qualys API scans are often slow—taking up to 12 hours to complete—and can generate a high volume of false positives, making it harder to focus on actual security risks
❌ Limited API support: Only supports REST and SOAP APIs
❌ Dependence on predefined schemas: To perform effective scans, Qualys requires accurate Swagger/OpenAPI files, which can be cumbersome to maintain and manage
❌ No actionable remediations: Qualys does not provide developer-friendly code snippets, which can slow down the security patching process.
❌ Limited reporting and UI: The reporting features in Qualys are relatively basic, offering limited insights and prioritization features. This makes it harder to efficiently manage vulnerabilities and risks at for enterprise scale
Escape
Pros
✅ Addition of agentless API discovery to its DAST scanning: Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
✅ Automated API documentation generation that helps you to launch scans right away and reduces the need for maintenance
✅ In-depth GraphQL testing capabilities and lowest false-positive rate
✅ Ability to prioritize the most critical API by business context, data sensitivity, and exposure.
✅ Actionable remediation code snippets for developers that help you build better relationships with them
Cons
❌ Advanced feature sets may require specialized knowledge
❌ Number of integrations with some of the operational tools
In-Depth Comparison: Escape DAST as an alternative to Qualys
Application discovery
Qualys focuses primarily on monitoring and securing assets like web applications, APIs, and cloud resources. To get started, you need to import web applications and APIs via a CSV or TXT file, which helps to bring your assets into the system for scanning and monitoring. Once the assets are imported, you can add connectors to integrate with other platforms such as AWS, Azure, or MuleSoft API Connectors.

These connectors are primarily designed to discover Swagger files within specific environments, but they cannot reconstruct API endpoints from code.
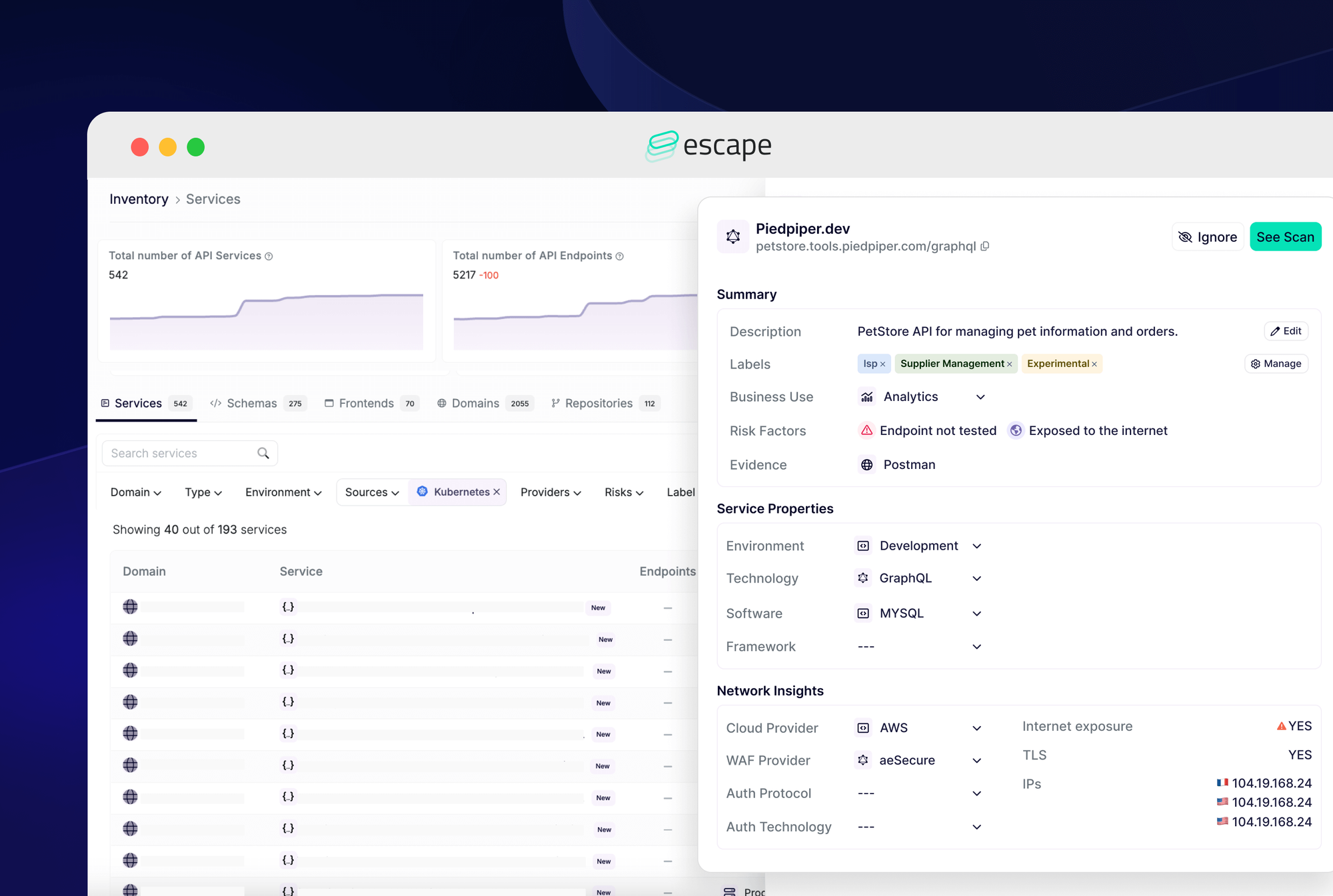
In contrast, Escape offers a fully automated web app and API discovery solution, designed to deliver immediate value. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify web apps and especially APIs quickly—often within minutes. This ensures that all applications, including those not actively in use, are discovered and documented.
Unlike Qualys, Escape DAST eliminates the need to manually input each URL in the file to import into the tool or upload API specifications. You simply enter your main domain, and Escape takes care of the rest, building a comprehensive API & web app inventory effortlessly. Simplified deployment processes minimize the need for specialized knowledge and extensive internal resources.
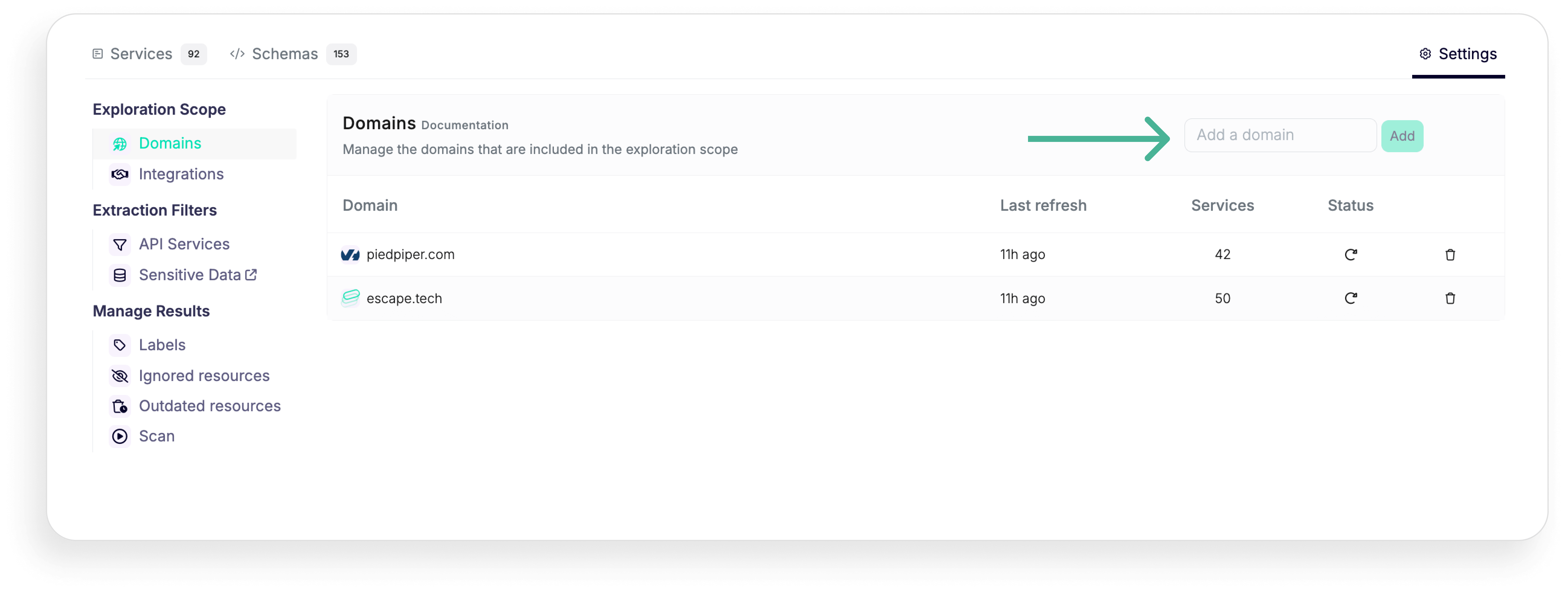
Once you've discovered all your exposed applications and APIs, you can enrich the data discovered and classified by connecting with your developer tools like Postman, GitHub, and GitLab, cloud platforms like AWS and Azure, and gateways like Apigee, Axway, Kong Gateway and Kong Connect and Mulesoft.
To scan internal applications behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
Scan setup
With Qualys, setting up and maintaining scans can be a bit cumbersome.
After adding an application to the list, you have to manually start the scan. Additionally, you need to manually define the option profiles and select authentication settings from a separate profile, which requires additional configuration steps. The authentication setup cannot be done directly within the application configuration; instead, you must set it up in the authentication section and then associate it with the web application separately. This multi-step process can feel disjointed and time-consuming.
For APIs, Qualys requires manual upload of API schemas to start scans, as it doesn't automatically generate schemas. Users need to ensure the Swagger version 2.0/OpenAPI 3.0 file (JSON format) is visible to the scanning service or that the Postman collection is uploaded to the scan settings so the APIs can be tested for common application security flaws.
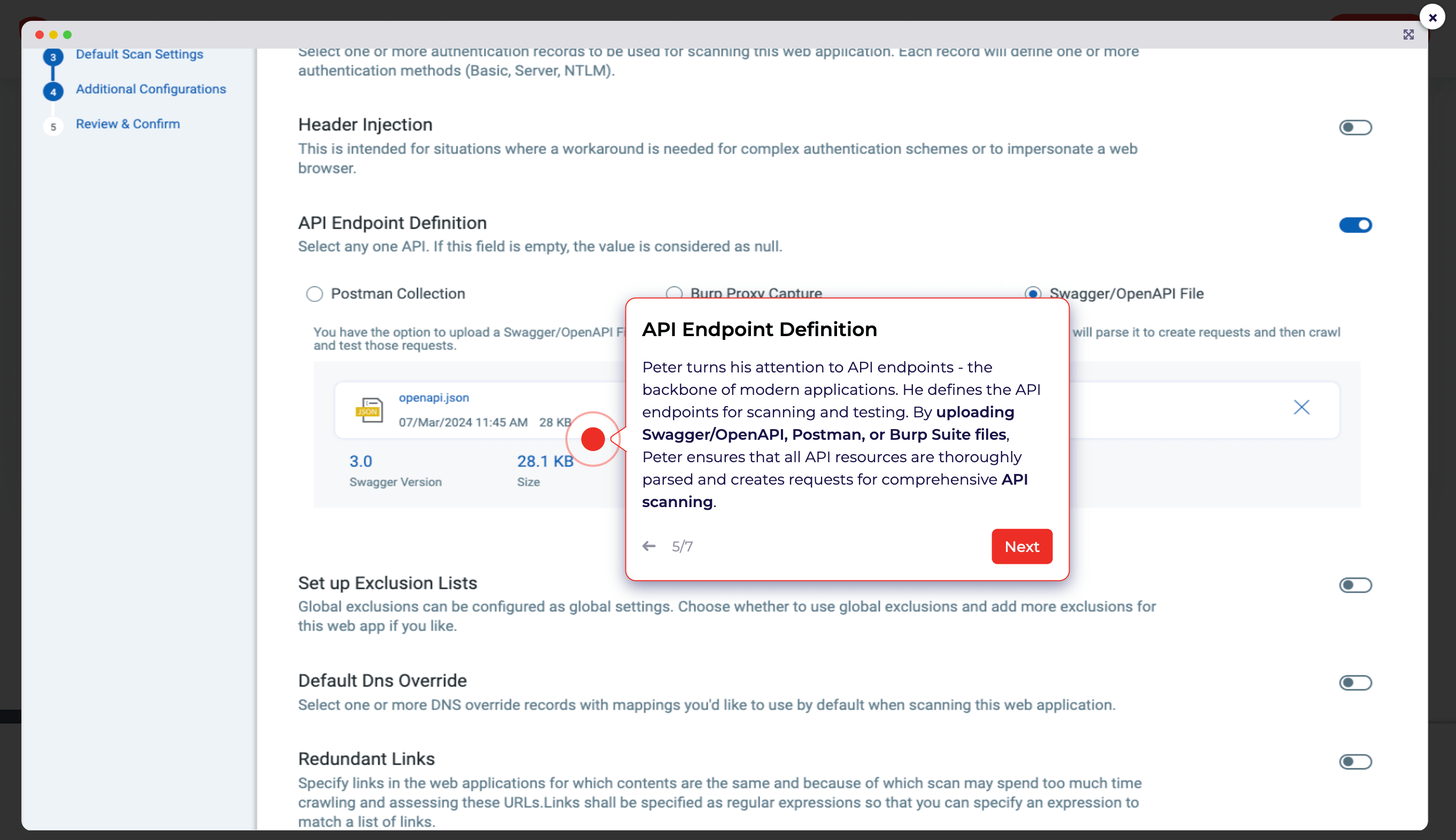
After you've uploaded the schema, you must also set up an option profile (a set of scan configuration options in Qualys).
Qualys WAS does not handle APIs natively. To conduct thorough API security testing, you must create a profile specifically configured for API testing, which includes the 30 tests aligned with the OWASP API Top 10. It's important to note that API compliance tests limit full coverage to basic vulnerabilities and do not cover business logic security testing.

In contrast, Escape uses a proprietary machine learning algorithm to automatically reconstruct API documentation. Of course, to improve overall coverage, you might need to configure authentication and upload specifications you might have on your side, but it's not a requirement to start initial scans.
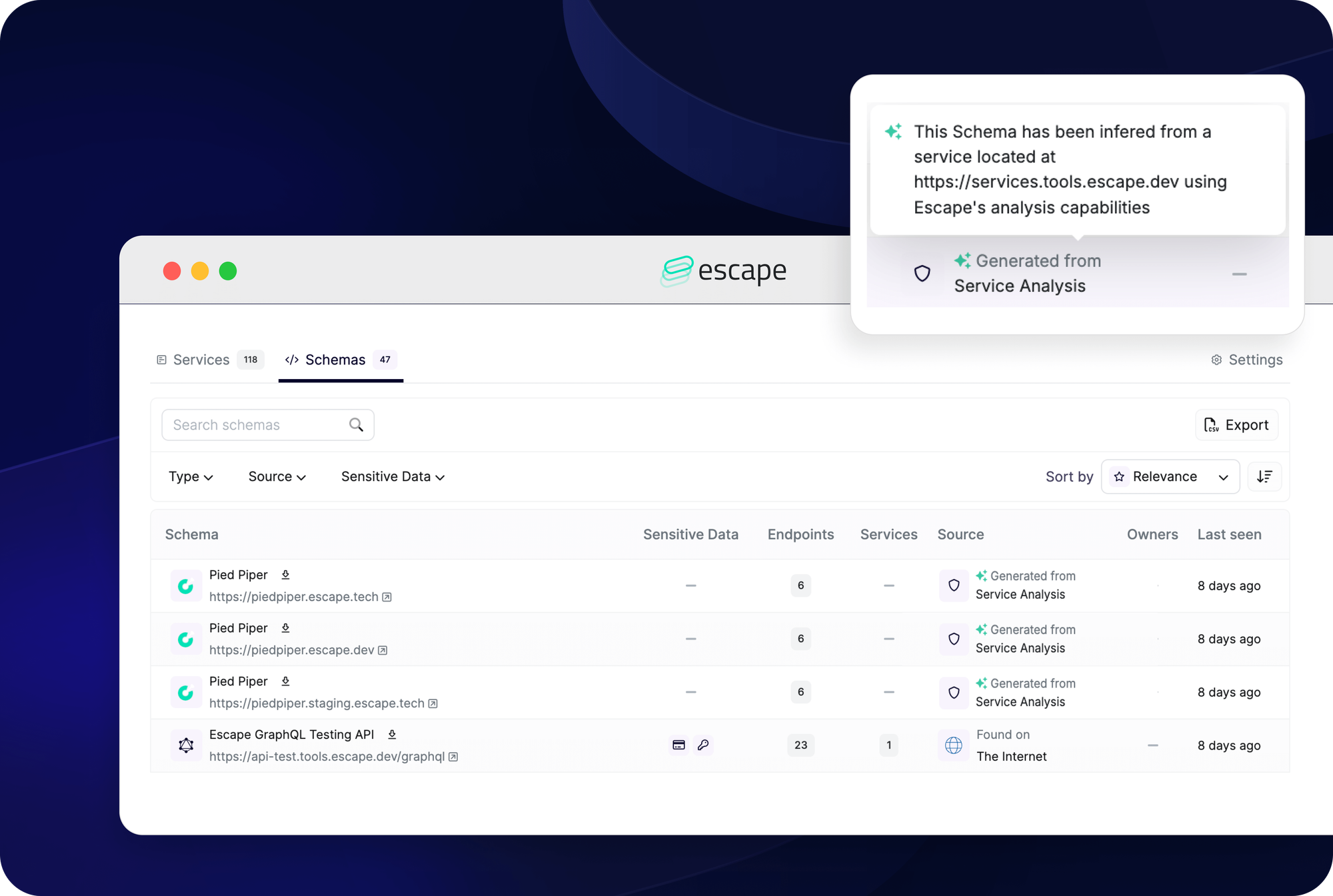
This ensures that any changes in your API structure are immediately reflected, allowing for continuous and accurate security scanning, without the need for constant intervention.
Security Testing
Qualys’ security testing, integrated within its TotalAppSec tool, primarily focuses on identifying vulnerabilities outlined in the OWASP Top 10 or basic compliance checks. While Qualys has recently begun supporting native handling of APIs (only REST and SOAP), it mainly addresses common issues like authentication and authorization flaws, rate limiting, and injection vulnerabilities. Its capabilities depend heavily on the presence of an accurate Swagger file and a predefined schema.
Qualys does offer some secret detection capabilities, but these are focused more on scanning stored data rather than being specifically designed for detecting secrets like API tokens or keys.
Escape relies on its proprietary web application crawling algorithm and feedback-driven Business Logic Security Testing algorithm. Together, they help Escape DAST to excel in detecting even complex business logic vulnerabilities, especially in SPAs and modern API types like GraphQL. Escape's algortihm addresses GraphQL complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Escape’s business logic testing is robust, and it includes comprehensive secret detection across various environments, not just repositories. Here is the full list of secrets that Escape can detect.
The platform also prioritizes reducing noise, ensuring that logs are concise and directly tied to meaningful vulnerabilities. This results in a more efficient scanning process that minimizes unnecessary data, making it easier for teams to focus on critical issues.
Coverage = Covered Endpoints / Total Number of Endpoints, where:Covered Endpoints = OK + SERVER ERRORTotal Number of Endpoints = OK + SERVER ERROR + UNAUTHORIZED + RATE LIMITED + REDIRECTED + SKIPPED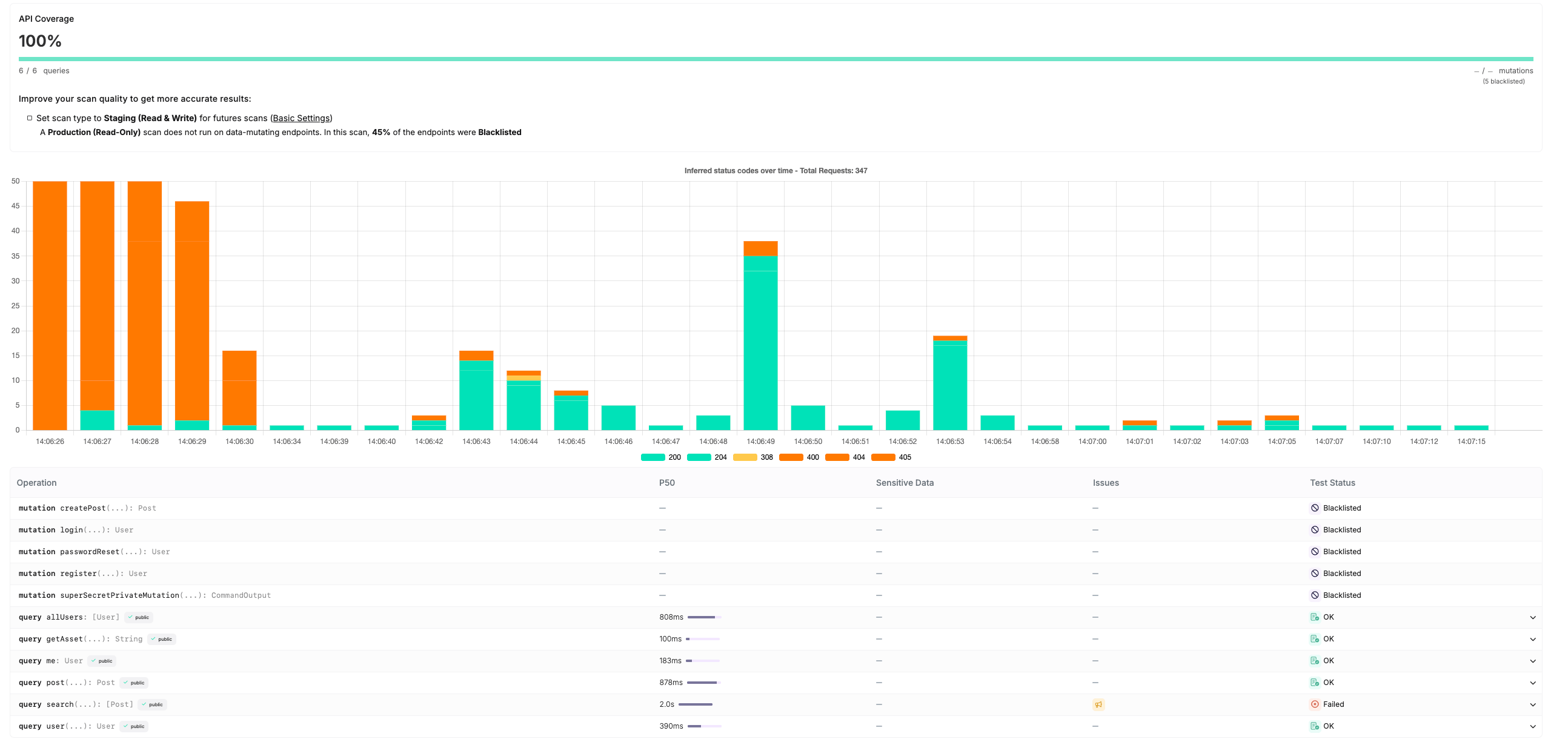
GraphQL API support
Qualys does not natively support GraphQL APIs. This means that if your stack includes GraphQL APIs, Qualys won't be able to scan them directly. GraphQL, a query language for APIs, has gained significant traction in recent years due to its flexibility and efficiency, but it is not currently compatible with Qualys's scanning and integration capabilities, which rely on traditional REST APIs.
In contrast, Escape has exceptional support for GraphQL Security Testing, integrating more than 100 GraphQL-specific tests, like aliasing and batching attacks, and even the most complicated access control issues.
“Escape is an innovative tool, and its results and algorithms are truly impressive. It was able to find GraphQL vulnerabilities that their competitors haven't seen. It also provides me with extensive testing capabilities." - Pierre Charbel, Product Security Engineer, Lightspeed
Contrarily to other scanners, Escape handles GraphQL natively and not as another HTTP API. Even better, our engine is capable of suggesting code fixes for all findings and all GraphQL engines to maximize developer productivity when fixing issues.
Escape relies on a powerful feedback-driven graph exploration algorithm that can explore and understand the business logic of your GraphQL API.
Remediation for developers
Detecting vulnerabilities is only the first step; providing developers with actionable remediation guidance is equally important.
Qualys provides generic remediation information in a text format without offering tailored code snippets, potentially increasing the burden on developers.

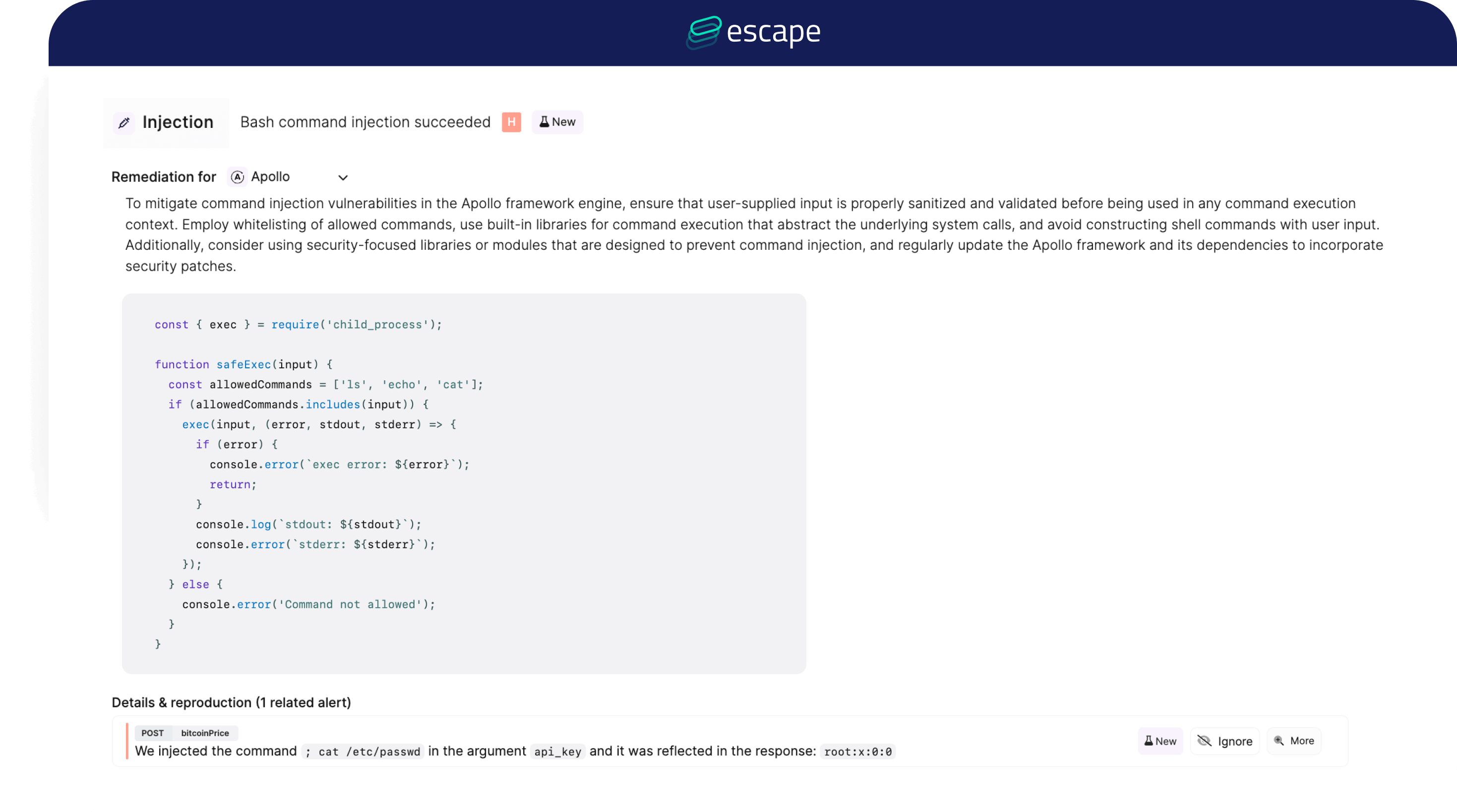
Escape goes above and beyond by offering tailored remediations and code snippets to address identified vulnerabilities efficiently.
Reporting
One significant issue with Qualys is its lack of a structured approach to prioritizing vulnerabilities.
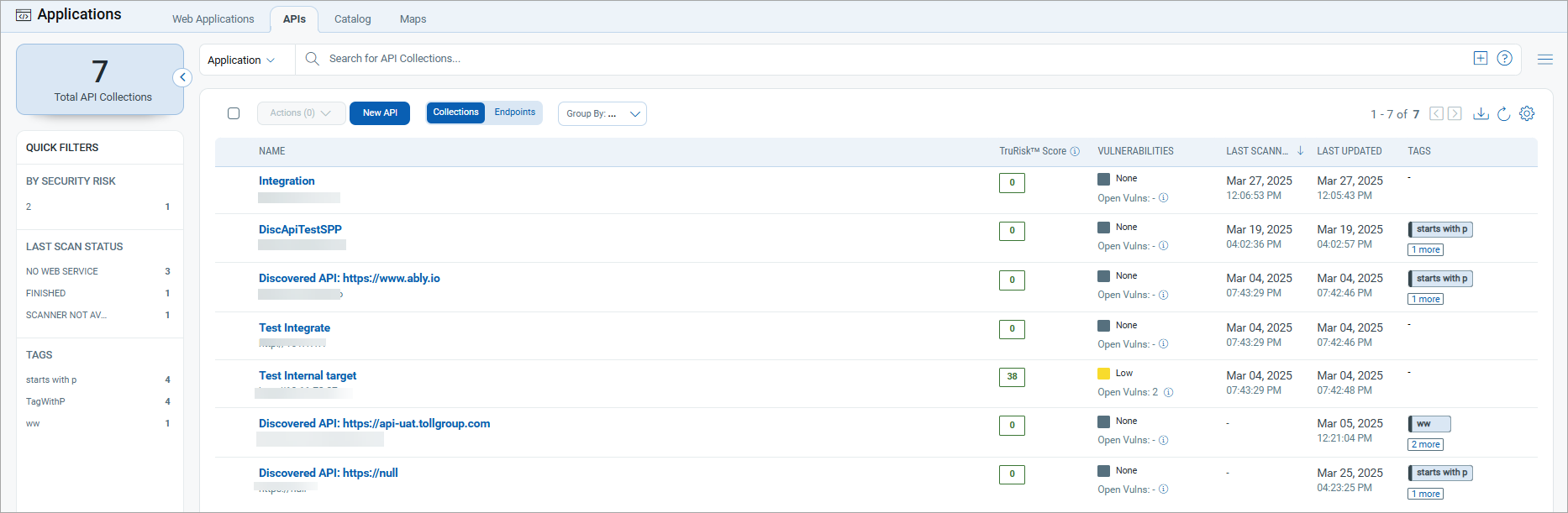
Qualys has just recently launched new UI with a metric called the TrueRisk™ score, which, similar to Escape Severity, incorporates exploitability calculations. New UI is definitely better than previous version and also has an ability to customize dasboarding through widgets which can be useful for certain organizations.
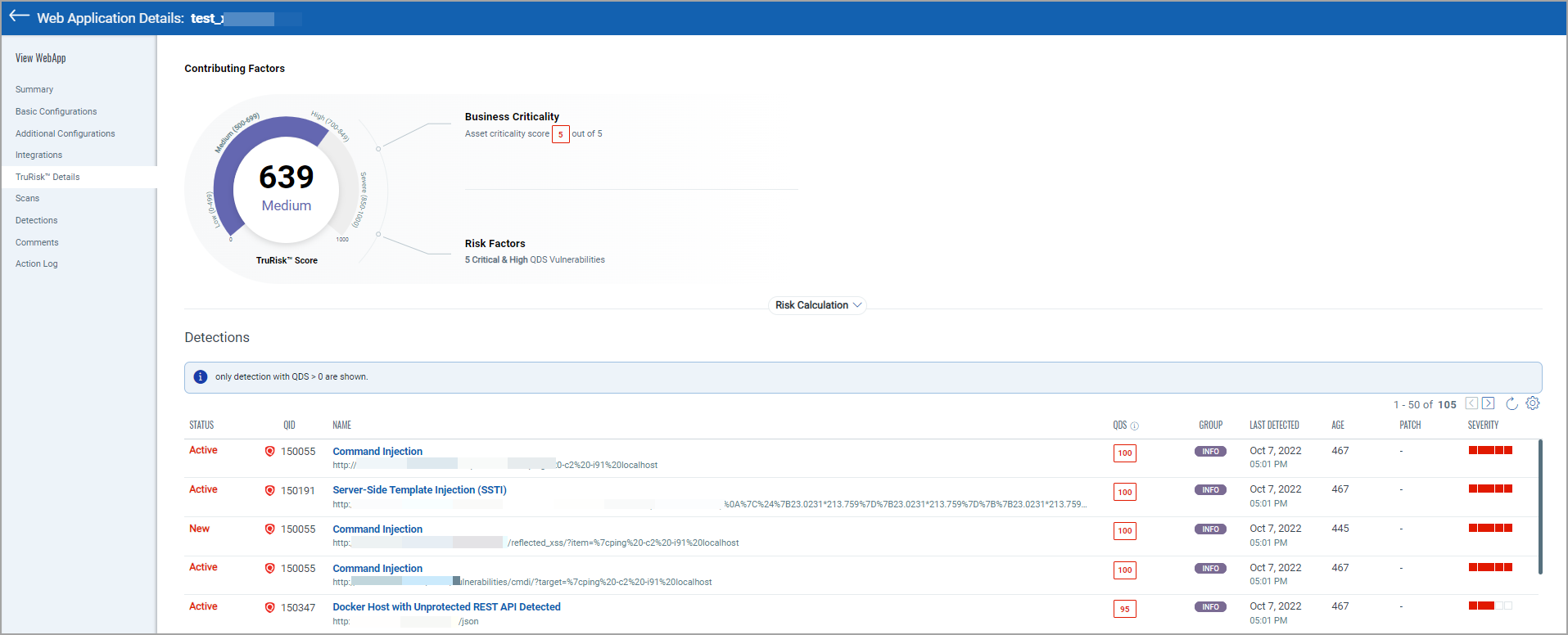
The downsides is that sometimes it's hard to visualize in a single view a true volume of critical vulnerabilities that require patching.
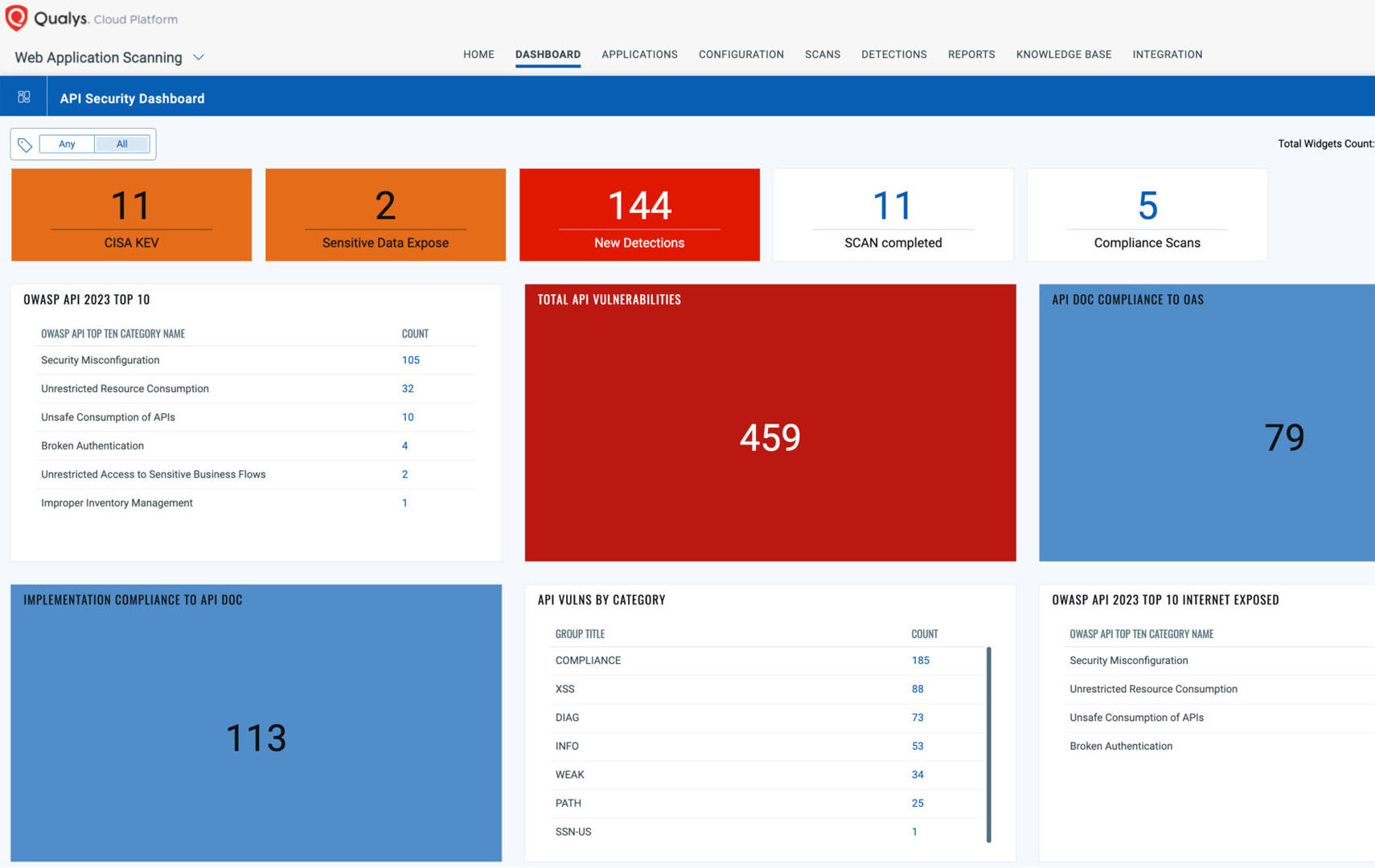
Additionally, their new API security dashboard provides basic information on discovered APIs, vulnerabilities, and compliance checks. However, the dashboard lacks depth in prioritization features, offering limited insights into which vulnerabilities pose the business greatest risk. As a result, security teams might find it challenging to quickly identify and focus on the most critical API risks, making it less effective in environments with large and complex API infrastructures.
Escape, however, offers a distinct advantage with its vulnerability prioritization funnel. This feature automatically identifies and prioritizes business-critical vulnerabilities, ensuring that the most significant threats are addressed promptly. In addition, it clear shows each application's code owner.
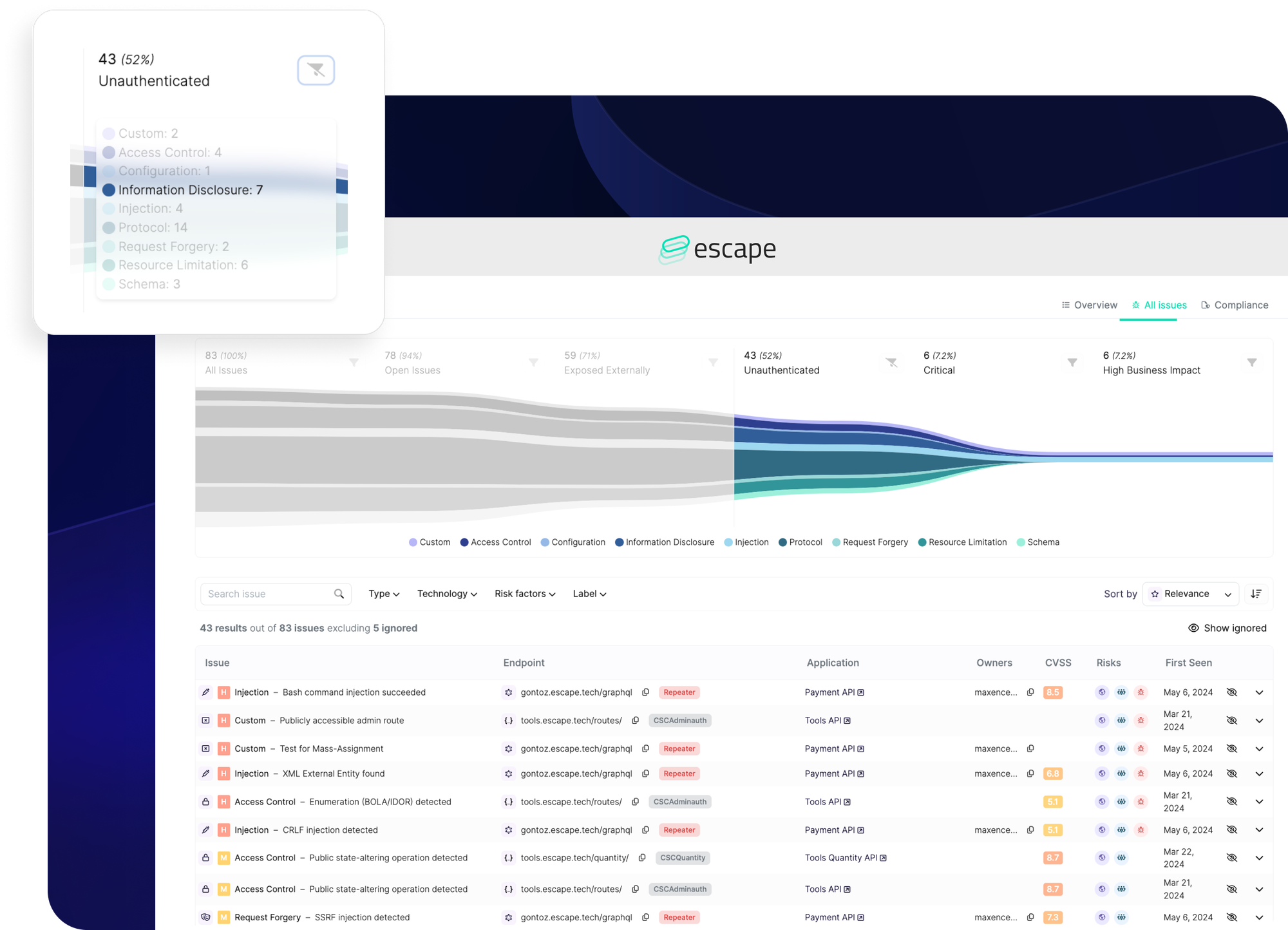
By streamlining the prioritization process, Escape enables security teams to focus their efforts where they matter most, enhancing overall security and providing peace of mind that critical vulnerabilities are being effectively managed.
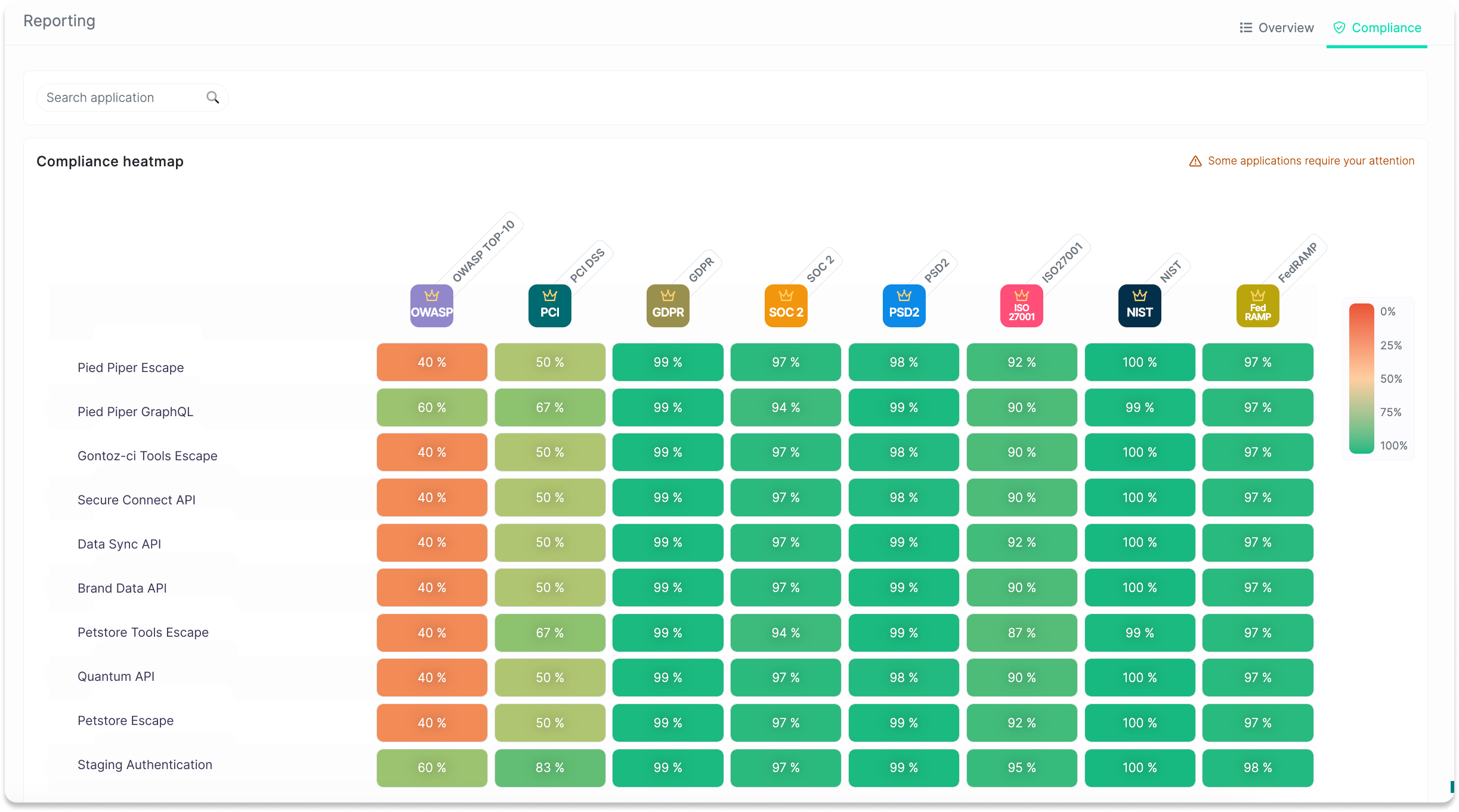
By integrating regulatory frameworks like PCI-DSS, GDPR, and HIPAA, Escape also highlights which APIs pose the greatest risks in terms of compliance violations in a unified view.
Conclusion
While Qualys provides basic vulnerability scanning coverage and can be cost-effective for existing users, it falls short as an enterprise-level automated API security solution. For organizations seeking comprehensive coverage across all API types, especially at scale, Qualys lacks key features such as automated, comprehensive API discovery, advanced testing capabilities for APIs like GraphQL, and actionable remediation guidance for developers. These limitations make it less suitable for organizations that require robust, automated security tools tailored specifically for modern, diverse API environments.
When searching for a Qualys alternative, it's crucial to consider the specific needs of your organization's application security strategy. While Qualys has improved in 2025 with its new UI, basic support for API testing and TrueRisk™ score, its manual configuration for CI/CD integration, API testing, and its lack of support for GraphQL may not meet the demands of every modern development environment.
In contrast, Escape offers a seamless, AI-driven approach with native support for GraphQL, automatic CI/CD pipeline integration, and a more user-friendly scan setup and authentication process. For organizations seeking an alternative to Qualys, Escape provides a comprehensive, automated solution that focuses on reducing false positives and prioritizing vulnerabilities based on business impact.
If you’re evaluating Qualys alternatives, it’s important to weigh the benefits of a more automated, dynamic testing solution like Escape, especially for modern web apps and APIs. Escape’s AI-powered scanning and support for evolving technologies offer a more streamlined security testing process, making it a viable option for companies looking to enhance their application security beyond what Qualys provides.
If you still have doubts, take a moment with our team and see directly during a demo why Escape is a better choice for your DAST.
Learn more about Escape DAST
Schedule a time with our product expert to see for yourself how Escape identifies even complex business logic vulnerabilities in your APIs without long scanning times. In all your modern applications.
Get a demo💡Want to learn more? Discover the following articles:
