Top 6 API security testing tools in 2025: a full review
When it comes to securing applications and APIs, the best API security testing tools are indispensable. These advanced solutions detect vulnerabilities by continuously scanning for weaknesses and simulating real-world attacks.
But how do you choose between all API security testing vendors?
Agentless API security tools are transforming application security by overcoming the pitfalls of traffic-based solutions like Noname security (part of Akamai) or Salt Security, which burden teams with long setup times and limited remediation guidance for their development teams. Instead, modern tools reduce workloads, minimize false positives, and integrate seamlessly into CI/CD pipelines.
You have a bunch of different vendors that will tell you, you know, here's all the issues with it and they'll give you like paragraphs over paragraphs and paragraphs of generic description of like, here's your SQL injection. Here's how it maps to OWASP Top 10 and developers will just skip it. They'll be like, I don't care about it. What do I need to fix? You know, so just make it more understandable, make it more actionable to developers, and make it short because nobody got time. - Aleksandr Krasnov, Principal Security Engineer at Meta
What sets the best API security testing tools apart is their ease of deployment, in-depth business logic security testing for vulnerabilities like BOLA and IDOR and ability to help developers remediate issues. They provide real-time feedback, freeing up security teams to focus on strategic priorities and scaling application security with limited resources.
This article explores the best API security testing tools, their pros and cons, and how they can help secure your applications and APIs as a critical part of your cybersecurity strategy.
Why is choosing the best API Security tool important?
API security is crucial because it protects the integrity of your data and services. APIs, being the connecting threads between different software applications, are vulnerable to attacks. Ensuring their security means protecting your application's core functions and the sensitive data they handle.
According to Derek Fisher in the Elephant in AppSec podcast, "mindset we all in the security space need to have: assume that everybody within your network or within your system is adversarial".
You have to model all possible threats to your APIs and integrate the action plan into your Application Security program to strengthen your organizational API security posture.
In 2024 alone, we've already suffered several API breaches, including Spoutible, Trello, and Glow. A breach a month keeps the security team on alert, not the hackers away...
Want to know more about how to proceed? Deep dive into our detailed API security checklist.
Why do traffic-based API security tools make the lives of application security engineers harder?
As seductive as network-based API protection is, there are also significant drawbacks to this approach.
Network API security testing vendors, however, often struggle with the initial step of discovering your APIs. They often require installing agents or monitoring traffic, which can be intrusive and resource-intensive. They are also difficult to integrate and don't offer visibility outside of API gateways, WAFs, or proxies.
As simple as it is, complex and lengthy deployment processes can leave APIs exposed, increasing the risk of breaches.
More than that, traffic-based API security tools often struggle to integrate with modern DevSecOps practices. They typically only protect APIs after they have been deployed and do not integrate smoothly with CI/CD pipelines.
This is where the best API security tools excel, addressing these limitations by offering agentless API discovery from code, business logic security testing with DAST instead of listening to the traffic, offering seamless CI/CD integration, and providing detailed code remediations for developers.
Now, you can jump to the best API security tools below.
Key features to look for in the best API security testing tools
So, let's examine the main features that make the best API security tools:
API Discovery & Inventory
Don’t know what your developers expose online? Here is when API Discovery and Inventory come into play. Every undocumented API feels like a ticking time bomb, a potential gateway for malicious breaches.
To ensure that the organization's data and services remain protected and bridge the gap between innovation and security, your top priority is to create a comprehensive inventory of all used APIs.
Need more information about API discovery? Check out here why API discovery is important and what is the difference between automated and manual approaches.
Automated API Discovery tools are indispensable to ensure efficiency, accuracy, and comprehensive coverage. Manual discovery should be seen as a complementary approach rather than a primary method in modern API management.
API Security in CI/CD
If you want to catch and fix API security issues early in your development process, you must integrate security within your CI/CD pipeline. It helps you ensure your applications are built securely from the ground up and helps your organization to shift left testing of APIs.
Custom security tests
Each organization's API stack and their structure are not the same. You, as a security engineer, sometimes need to be able to write or extend your automated security tests to find vulnerabilities specific to your APIs. This can be particularly useful for running static security assessments on your web applications, identifying regression bugs, or investigating specialized in-house security concerns.
Support in remediation
Tired of struggling to get developers on board with API security in the SDLC? Making life easier for your developers is important to ensure swift security fixes. Detailed remediation code snippets help to break down complex security issues into simple, actionable steps, so your developers can quickly fix any problems that pop up.
Ease of deployment
No one wants a complicated setup process. The faster you can start scanning, the faster you can protect your organization. Agentless solutions are your best bet: An agentless deployment method involves gathering data without the need to alter application code and without inserting any agents into the application's communication path.
No fuss, just quick and efficient protection.
Testing undocumented APIs
Hidden vulnerabilities can be a big risk. Testing undocumented APIs is important to find those hidden weaknesses and keep your data safe from potential threats.
Contextual risk-based prioritization
Prioritizing security tasks is vital. Contextual Risk-Based Prioritization is a strategy used in risk management and security to determine the priority of addressing vulnerabilities or threats based on their potential impact and context within a specific environment.
It helps you focus on what's most important first for your business, making sure you're putting your efforts where they matter the most.
Top API security tools
Escape
Escape is built to help you get the value out of its platform in the shortest time possible. It allows you to discover your APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This ensures that all APIs, including those not actively in use, are discovered and documented.
It's a dynamic application security testing (DAST) tool - a type of black-box testing that checks for security problems while the software is actually running. For testing, Escape relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in modern API types like GraphQL. Escape's algortihm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Escape helps security teams automate testing for OWASP Top 10 and complex business logic flaws at scale.
In addition, actionable remediation code snippets for every finding and native CI/CD integration empower developers to adopt security by design.
Want to see Escape's API discovery capabilities in action? Check out the video below:
Pros
- Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
- Automated schema generation that helps you to launch scans right away and reduces the need for maintenance
- In-depth GraphQL testing capabilities and lowest false-positive rate
- Ability to prioritize the most critical API by business context, data sensitivity, and exposure.
- Actionable remediation code snippets for developers that help you build better relationships with them
- Effortless custom checks integration to automate security tests tailored to specific APIs
- Easy-to-set-up automated testing and integration with CI/CD pipelines. Ideal for both beginners and advanced users.
- Open-source extensions like GraphQL Armor
Cons
- Advanced feature sets may require specialized knowledge
- Number of integrations with some of the operational tools
Noname Security (recently acquired by Akamai)
The Noname API Security Platform (recently acquired by Akamai) proactively secures environments from API security vulnerabilities, misconfigurations, design flaws, and provides API attack protection with automated detection and response.
Noname Active Testing sometimes gets confused with a DAST, but that is not its functionality. Noname Active Testing compares an API with its Swagger file to assess its conformance.
Pros
- Easy to understand for network engineers (though the learning curve might be steeper for security engineers with another background)
- Focuses strongly on helping to ensure regulatory compliance.
- Since they’re looking at API traffic, they’re able to detect exploits in runtime, but it only helps to adapt a reactive approach.
- The findings from Noname may appear to be real detection events, but they are often quite basic, such as merely checking if an authentication header is present.
- Noname covers a broad range of API types.
Cons
- Setup time: The customization process can be time-consuming, requiring more upfront investment in setup. Testing requires full application deployment first, as well as ingesting logs from your staging or lower environments.
- If your primary concern is detecting APIs, being reliant on network logs doesn’t really solve your problem, as it requires them to be behind your normal network flows in the first place! This is because network logs can only capture traffic that is actively passing through your network. Therefore, they can only detect APIs that are already being used and generating traffic. You're at risk of missing exposed and vulnerable Shadow APIs.
- Detection alerts are heavily based on baselines, which makes them very noisy and full of false positives.
- Testing requires manually uploading schemas when they change - it doesn’t automatically detect them.
- Response actions are incredibly cumbersome - you get drowned in these alerts and then respond by building WAF rules.
- You can't accelerate the remediation process because of the lack of actionable remediation code snippets for developers.
- Not accessible for small and medium-sized businesses: pricing starts at $150,000 entry level package for 1 year
Salt Security
Salt Security was founded in 2016 by alumni of the Israeli Defense Forces (IDF) and serial entrepreneur executives in the cybersecurity field and is based in Silicon Valley and Israel.
It is an API security platform that offers a comprehensive solution for all APIs, providing robust API discovery and attack prevention capabilities. It provides a deep contextual analysis of API traffic to detect and prioritize potential threats based on their real-world impact.
Pros
- Supports a wide range of API protocols: REST, GraphQL, SOAP, and gRPC.
- Real-Time Detection: The platform can detect certain security threats in real-time based on network traffic.
- Integration Options: Salt Security offers numerous integration points for network logs and can detect sensitive data using these logs.
- Posture Management: Users can save searches as posture rules, enhancing ongoing security assessments.
Cons
- High cost for small businesses: $50,000/Start up plan Console Access and Support + up to 5M API calls/month for 12 months and $350,000 for Enterprise plans.
- Limited Testing: The system lacks comprehensive testing capabilities, as it primarily analyzes network logs without testing actual payloads, leading to potential blind spots in detection.
- Header-Based Alerts: Most alerts are based on HTTP headers rather than payloads, which may cause confusion and diminish the effectiveness of threat detection.
- Basic Scanning: Scanning capabilities are considered basic, primarily crawling known API endpoints without proactively discovering dormant or unmonitored APIs outside of API gateways, proxies, or WAFs.
- Noisy Risk Scoring: Risk scoring is very basic and can generate a lot of noise, complicating prioritization.
- High Costs: Utilizing traffic mirroring for detection can significantly increase logging costs, making it a potentially expensive option for organizations.
- Lack of Actionable Remediation: The absence of actionable remediation code snippets slows down the fixing process.
StackHawk
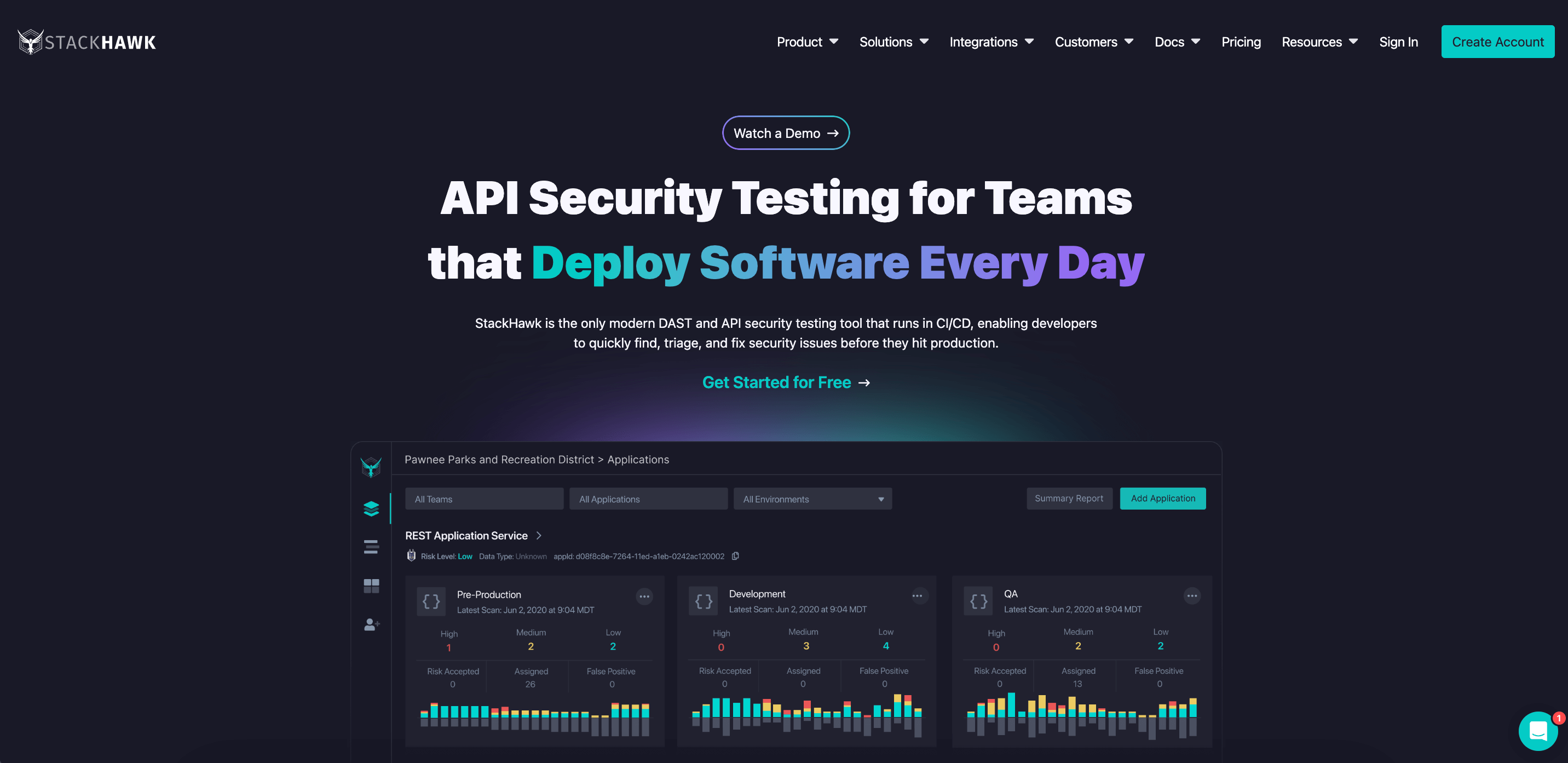
Stackhawk is a DAST tool that scans APIs for potential vulnerabilities. Stackhawk is built on top of OWASP ZAP and works by simulating an attack, which is based on common open-source vulnerabilities like OWASP top 10 or custom attack definitions, and observing how the API responds. In other words, it tries to leverage known vulnerabilities on the API to observe how it reacts to them to determine if the API is secure against the vulnerability or not.
Stackhawk provides integration with your CI/CD so that you can automate the testing of every API endpoint in your application.
Stackhawk balances ease of deployment with advanced risk-based prioritization. Offers an intuitive dashboard for monitoring and responding to threats.
Pros
- Easy setup for smaller teams or organizations with good pricing options to get started.
- The risk assessment tool is user-friendly for security engineers with developer backgrounds.
- Supports a large number of integrations.
- Tests various API types.
Cons
- Reliance on ZAP & Limited coverage for business logic vulnerabilities
- Discovers APIs only within code repositories. No external API discovery capabilities or enriched API inventory
- You need to have OpenAPI specs on hand to start scanning. Spec uploads and configuration require manual effort, which could be difficult to do for larger organizations or more complex applications with large development and lean security teams
- StackHawk scan results payload is organized as a list of every unique finding across the scan. It provides information about vulnerability, risk, confidence, paths and may include OWASP Cheatsheet, but does not offer detailed remediation code snippets for developers
- StackHawk's prioritization is based on the OWASP Risk Rating Methodology. The OWASP Risk Rating Methodology primarily focuses on the technical aspects of security issues, such as their impact and exploitability. It may not take into account the specific context of your application, its users, or your business objectives.
- While it could be good for small to mid-sized teams, larger enterprises might find its capabilities insufficient for extensive or highly customized needs
Rapid7
InsightAppSec is part of Rapid7's security suite, providing Dynamic Application Security Testing (DAST) for mature and maturing Application Security professionals. It offers a robust API discovery and a strong emphasis on remediation support. More than that, InsightAppSec incorporates extensive security coverage and detailed guidance for fixing vulnerabilities.
Pros
- Part of the overall comprehensive vulnerability platform
- Rich reporting and integrations
- Covers various applications
- Extensive dashboard customization options
- Supports Swagger files
- Custom attack templates that help to customize security testing but might require a lot of maintenance
Cons
- Lack of API discovery and inventory
- It treats APIs and applications the same, without distinguishing between the unique requirements of API security
- Lack of quality support for GraphQL APIs.
- Long scanning times & lots of false positives
- Testing requires manually uploading schemas when they change - it doesn’t automatically detect them
- You can't accelerate the remediation process because of the lack of actionable remediation code snippets for developers.
- Lack of alerting workflows
Traceable API security
Traceable’s API security platform empowers security teams with comprehensive API discovery, risk assessment, and real-time threat prevention. It helps organizations identify vulnerabilities, stop data exfiltration attacks, and gain deep analytics for proactive defense.
With its strong roots in Application Performance Monitoring (APM), Traceable excels in API tracing and behavioral analytics—giving it a unique edge in detecting sophisticated threats. However, its integration complexity and developer experience may not align with every team’s workflow, making it essential to evaluate its suitability based on your security needs.
Pros
- Comprehensive tracing and detection: Traceable uses application performance monitoring (APM) roots, enabling sophisticated tracing. This includes detailed application maps and looking up users via session IDs.
- Custom-built detections: Its detection capabilities are advanced and highly customizable, helping identify complex threats within API environments.
- Testing based on actual traffic data and without authentification: Traceable uses contextual fuzzing based on API traffic, making tests feel relevant. The primary benefit is being able to run tests without setting up authentication. This functionality appears to leverage logs that include authenticated users, allowing tests to be conducted as those users and fuzzing their payloads. However, this method presents significant constraints. It really limits the kinds of testing you can do - whether that’s testing with sensitive data or specific user types. It also limits which APIs will get tested, as if there’s no traffic there’s no test..
Cons
- Heavy integration lift for API discovery: Requires network or agent-based integrations, which can complicate and slow down deployment.
- Not a developer-friendly testing experience: Testing results are presented in a way that may not be easily actionable for developers, potentially extending the time required to address vulnerabilities and leading to frustration.
- API security testing process feels very manual: The UI is very much built around creating test suites and then kicking off those scans, rather than a true CI/CD integration (although it does technically have those). If you look for ways to automate and scale your security scans in CI/CD, Traceable won't be a good solution.
- Reliance on traffic data for testing: APIs without active traffic, as well as those located outside of API gateways, WAFs, or proxies, may not be tested effectively.
Conclusion: API security tools adapted to your needs
Selecting the right API security tool depends on your specific needs and existing infrastructure. Whether you prioritize comprehensive coverage, ease of deployment, or contextual threat analysis, there's a tool tailored to your requirements. In 2024, staying ahead in cybersecurity means choosing an API security tool that not only protects but also automates your API management and allows you to customize your needs.
💡 Want to learn more about API security? Check out the following articles:
- API Security Checklist
- How to secure APIs built with FastAPI: A complete guide
- API gateway security: 8 best practices
- API Security GPT Bot
- What is an API attack, and how to prevent it?
Prefer hands-on learning? Check out our API Security Academy and learn how to secure your GraphQL applications.

