Escape vs StackHawk
Update: January 2025. Explore how StackHawk differs from Escape, weigh the advantages and disadvantages of both, and determine the best fit for your company.

StackHawk is a well-known player in the DAST space, offering a developer-friendly approach that helps technical teams catch security issues early in the development process. It prioritizes vulnerabilities using the OWASP Risk Rating Methodology, focusing on impact and exploitability. The platform supports both web applications and API security testing, covering a wide range of API types. Developers can seamlessly integrate StackHawk into their CI/CD pipelines, enabling automated security checks within their existing workflows.
But how does StackHawk compare to Escape’s DAST, API discovery, and API security capabilities?
In this article, we’ll break down the key differences between StackHawk and Escape.
When it comes to security, choosing the right tool can make all the difference—not just in protecting sensitive data but also in maintaining the speed and efficiency of your application deployment. Let's dive in!
Head-to-head comparison: StackHawk vs Escape
Now, let's dive into how StackHawk compares to Escape. We've built this comparison based on the following sources:
- StackHawk's official website & product datasheets
- StackHawk's documentation
- StackHawk's publically accessible demos on YouTube
- Feedback from security professionals
Here you can find the head-to-head comparison of both tools:
StackHawk
Pros
✅ Focuses on empowering developers, good CI/CD integration
✅ Custom attack templates that help to customize security testing
✅ Supports a large number of developer-focused integrations
✅ The risk assessment tool is user-friendly for security engineers with developer backgrounds
✅ Offers scalable pricing plans suitable for startups and growing teams without significant infrastructure investment
Cons
❌ Reliance on ZAP & Limited coverage for business logic vulnerabilities
❌ Discovers APIs only within code repositories. No external API discovery capabilities or enriched API inventory
❌ You need to have OpenAPI specs on hand to start scanning. Spec uploads and configuration require manual effort, which could be difficult to do for larger organizations or more complex applications with large development and lean security teams
❌ StackHawk scan results payload is organized as a list of every unique finding across the scan. It provides information about vulnerability, risk, confidence, paths and may include OWASP Cheatsheet, but does not offer detailed remediation code snippets for developers
❌ StackHawk's prioritization is based on the OWASP Risk Rating Methodology. The OWASP Risk Rating Methodology primarily focuses on the technical aspects of security issues, such as their impact and exploitability. It may not take into account the specific context of your application, its users, or your business objectives.
❌ While it could be good for small to mid-sized teams, larger enterprises might find its capabilities insufficient for extensive or highly customized needs
Escape
Pros
✅ Agentless API discovery for both externally exposed and internal APIs.
✅ OpenAPI specification generation from automated API schema generation. It continuously monitors for and detects any changes or versions in the API schema over time.
✅ Proprietary business logic security testing algorithm for APIs, SPAs and microservices that's able to detect BOLA, IDOR, and Access Control issues
✅ Developer-ready remediation code snippets that are tailored to each development framework, fast-tracking patching and significantly improving efficiency
✅ Ability to prioritize the most critical applications by business context, data sensitivity, and exposure
✅ Integration with well-known security platforms like Wiz
Cons
❌ Advanced feature sets like custom security rules may require specialized knowledge, potentially presenting a learning curve for some users.
❌ Number of integrations with some of the operational tools can be limited
Learn more about Escape
Schedule a time with our product expert to see for yourself how Escape DAST identifies even complex business logic vulnerabilities and integrates with your modern stack.
Book a demoLet's zoom in on the details: StackHawk vs Escape
API Discovery
You can't secure what you can't see, so the faster you get to see what are the APIs exposed on the internet, the more you reduce the risk of API security breaches.
Both StackHawk and Escape provide API discovery solutions, but their approaches, depth of discovery, and enrichment capabilities differ significantly.
StackHawk:
- Discovers APIs only within code repositories.
- Focuses on scanning application source code and configurations to extract API endpoints.
- Primarily used for internal development and security testing during the software development lifecycle (SDLC).
- Identifies API endpoints but does not offer extensive classification.
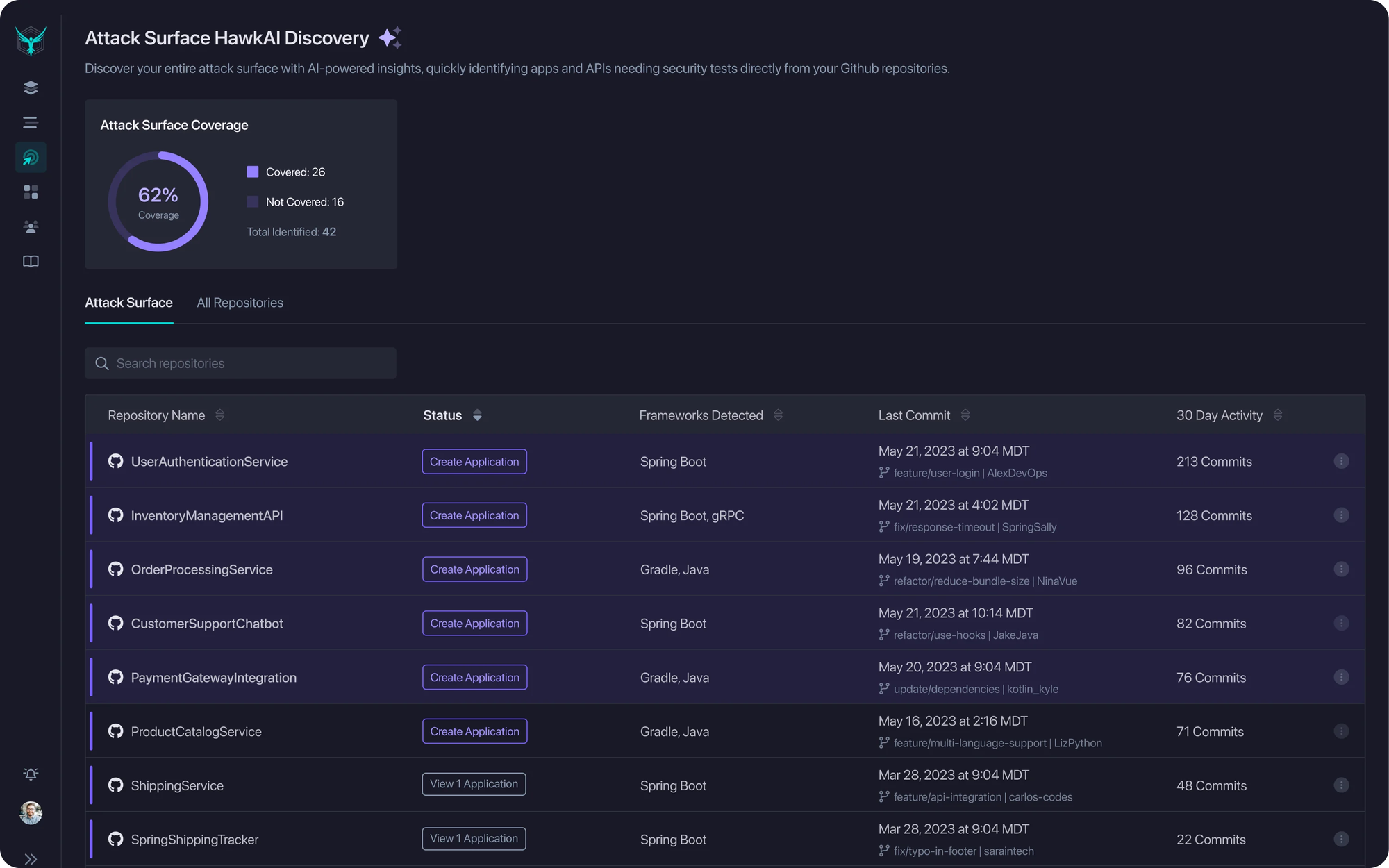
Escape:
- Unlike StackHawk, Escape goes beyond code repositories by performing external scanning to discover publicly exposed APIs. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques.
- Integrates with API gateways (ex. Axway, Kong Gateway and Kong Connect and Mulesoft..), cloud providers (ex. AWS, Azure), other security solutions like Wiz, and CI/CD pipelines to enrich the inventory with additional data. To scan internal APIs behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
- Provides a broader and more dynamic discovery mechanism.
- Classifies APIs based on business context, risk level, and data sensitivity.
- Leverages machine learning to categorize and prioritize discovered APIs.
With Escape, to get started all you need is to put in your main domain name, so you can build inventory without any intervention from the development team. Simplified deployment processes minimize the need for specialized knowledge and extensive internal resources.
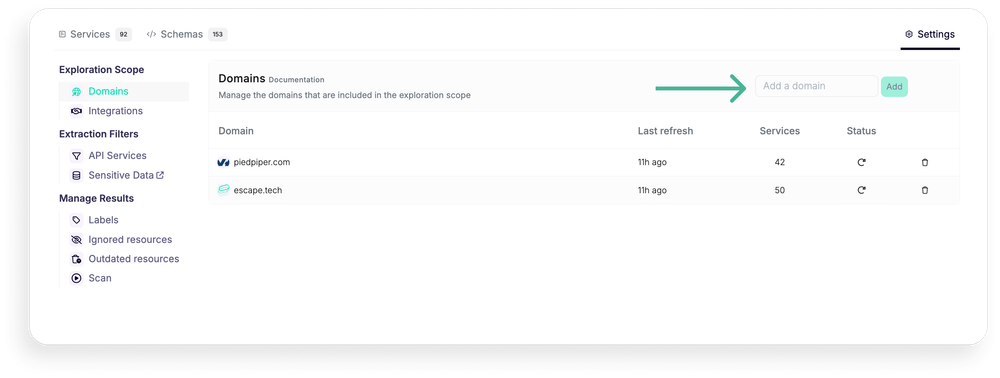
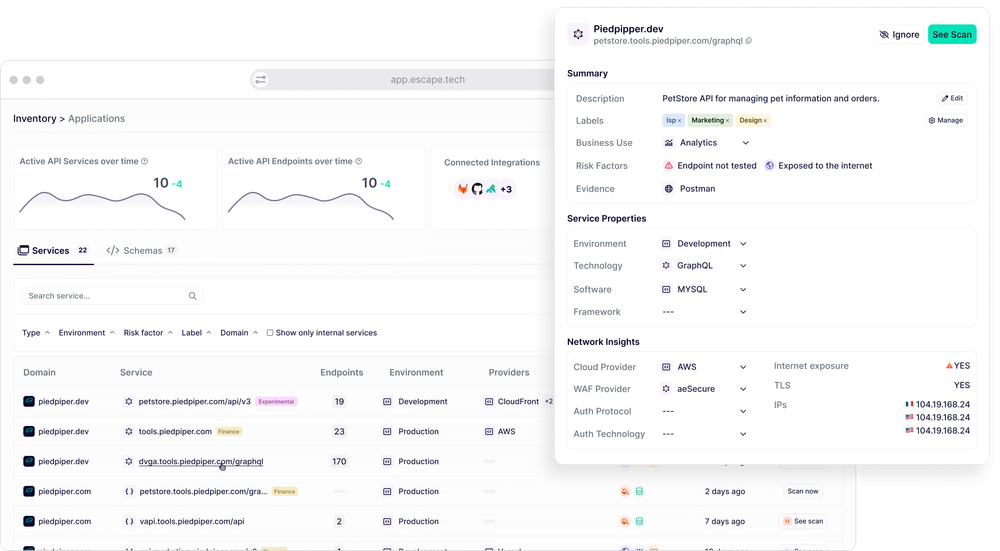
Schema Reconstruction (Building Back API Schemas)
- StackHawk:
- Does not generate or reconstruct OpenAPI schemas.
- Security scanning relies on manually provided API specifications.
- Escape:
- Automatically reconstructs API schemas (OpenAPI format) from discovered endpoints.
- Uses AI-based techniques to infer missing documentation and detect security gaps.
Deployment
You've decided to scan your APIs & Single Page Apps for vulnerabilities. Now what? Great security platforms allow you to start right away, so you don't have to wait or include multiple team members to access your security posture.
StackHawk
One of the differences with Escape is that StackHawk itself is not a SaaS scanner that runs entirely from the cloud, but it does allow cloud-based deployments through CI/CD and containerized environments. You have several deployment options:
- Local deployment: according to StackHawk documentation, first, you are required to install HawkScan in your local environment via Homebrew. Can lead to security inconsistencies if team members leave or change devices.
- In CI/CD: StackHawk is designed to run within CI/CD workflows. It integrates with: GitHub Actions, GitLab CI/CD, Jenkins, CircleCI, Azure DevOps
- Docker & Kubernetes: Runs within containers but does not perform full Kubernetes-wide security scanning
Escape
- Agentless Deployment: Escape provides an agentless security solution, eliminating the need for installing agents on servers or applications. This approach simplifies deployment and reduces potential performance overhead. You can test all your exposed APIs, SPAs and microservices without the need for deployment. Either enter the domain name or connect the integrations you need.
- CI/CD Integration: Escape integrates seamlessly into CI/CD pipelines, enabling automated security testing during the development process.
It integrates with: GitHub Actions, npm package, Public API, GitLab CI/CD, Bitbucket Pipelines, CircleCI, Jenkins, Azure DevOps
- Private Locations: Escape's Private Locations enable secure detection, fingerprinting, and scanning of internal applications behind your organization's firewall or VPN. This is achieved through the Escape Repeater, a lightweight, open-source tool developed in Golang. The Repeater establishes a reverse tunnel between Escape and your internal network, providing a secure channel for performing scans and retrieving results.
- Deployment Methods:
- Docker Deployment: The Repeater can be deployed using Docker CLI, Docker Compose, or other container orchestration tools.
- Kubernetes Deployment: For Kubernetes environments, the Repeater can be deployed as a Kubernetes deployment, allowing it to access resources within your cluster.
- Deployment Methods:
Security Testing: StackHawk vs. Escape
| Feature | StackHawk | Escape |
|---|---|---|
| Testing Approach | StackHawk is AppSec software built on ZAP (open-source web app DAST scanner, former OWASP ZAP) | DAST scanner with proprietary business logic security testing algorithm |
| Scanning Scope | Pre-defined endpoints & apps only (must be configured in the pipeline) | Full API and Front-End Inventory Scanning (including detected exposed external shadow APIs, zombie APIs, and misconfigurations) |
| Authenticated Testing | ✅ Supports authentication mechanisms (API keys, OAuth, JWT, session-based auth) | ✅ Supports authentication mechanisms (OAuth, API keys, JWT, multi-factor auth) |
| Testing in CI/CD | ✅ Integrated into CI/CD pipelines (GitHub Actions, GitLab CI/CD, Jenkins, CircleCI, Azure DevOps) | ✅ Integrated into CI/CD pipelines (GitHub Actions, GitLab CI/CD, Bitbucket Pipelines, CircleCI, Jenkins, Azure DevOps, npm) |
| Agentless Testing | ❌ Requires HawkScan installation within CI/CD or local environment | ✅ Agentless – scans APIs, SPAs, and microservices without requiring local installation or modifications |
| Kubernetes Security Testing | ❌ Limited – Can scan APIs in Kubernetes but does not provide cluster-wide security insights | ✅ Escape Repeater scans internal APIs running in Kubernetes & private networks |
| GraphQL Security | 🌕 Supports GraphQL API security testing but does not cover business logic vulnerabilities | ✅ Supports GraphQL API security testing with a proprietary algorithm |
| Schema Validation | ❌ No automatic schema validation – Requires an OpenAPI spec file for best results | ✅ Automatically reconstructs API schemas from code and detects schema vulnerabilities |
| Detected Vulnerabilities | 🌕 Covers OWASP API Top 10 risks like injection, broken authentication, and security misconfigurations | ✅ Escape covers OWASP API Top 10 and thousands of test scenarios across 145 vulnerability categories (security assessments), especially focusing on business logic vulnerabilities like IDOR, BOLA, and access control |
| False Positive Reduction | ❌ May require manual tuning of test configurations | ✅ Uses AI-based classification to reduce false positives & prioritize real threats |
| External API Testing | ❌ No external API scanning – Only scans APIs configured within the CI/CD pipeline | ✅ Scans both internal & external APIs |
| Remediation Guidance | 🌕 Provides detailed insights on vulnerabilities but requires developers to manually tailor them | ✅ Provides developer-ready remediation recommendations tailored to their framework & security enforcement policies |
Custom security tests
Both StackHawk and Escape offer unique approaches to custom security tests. Below, you can find the detailed comparison:
| Feature | StackHawk | Escape |
|---|---|---|
| Custom Test Configuration | Manual YAML-based test customization StackHawk only supports Custom Test Scripts that meet the following criteria: must be written in JavaScript or Kotlin, must include either a scan() or scanNode()example function, or both, must be an active scan test | YAML-based security tests that require no manual maintenance |
| Maintenance Effort | ❌ Requires manual updates & maintenance of test configurations | ✅ Fully automated & updated by Escape's AI engine |
| Test Availability | ❌ Only available in security scans, not API discovery | ✅ Available in both API discovery & security testing |
| New API Changes & Updates | ❌ Requires developers to modify YAML files when APIs change | ✅ Escape dynamically adapts to API changes without manual intervention |
Remediation guidance for developers
StackHawk scan results payload is organized as a list of every unique finding across the scan. It provides information about vulnerability, risk, confidence, paths and may include OWASP Cheatsheet, and it offers quite detailed remediation guidance for developers, but it can't be tailored to their development framework.
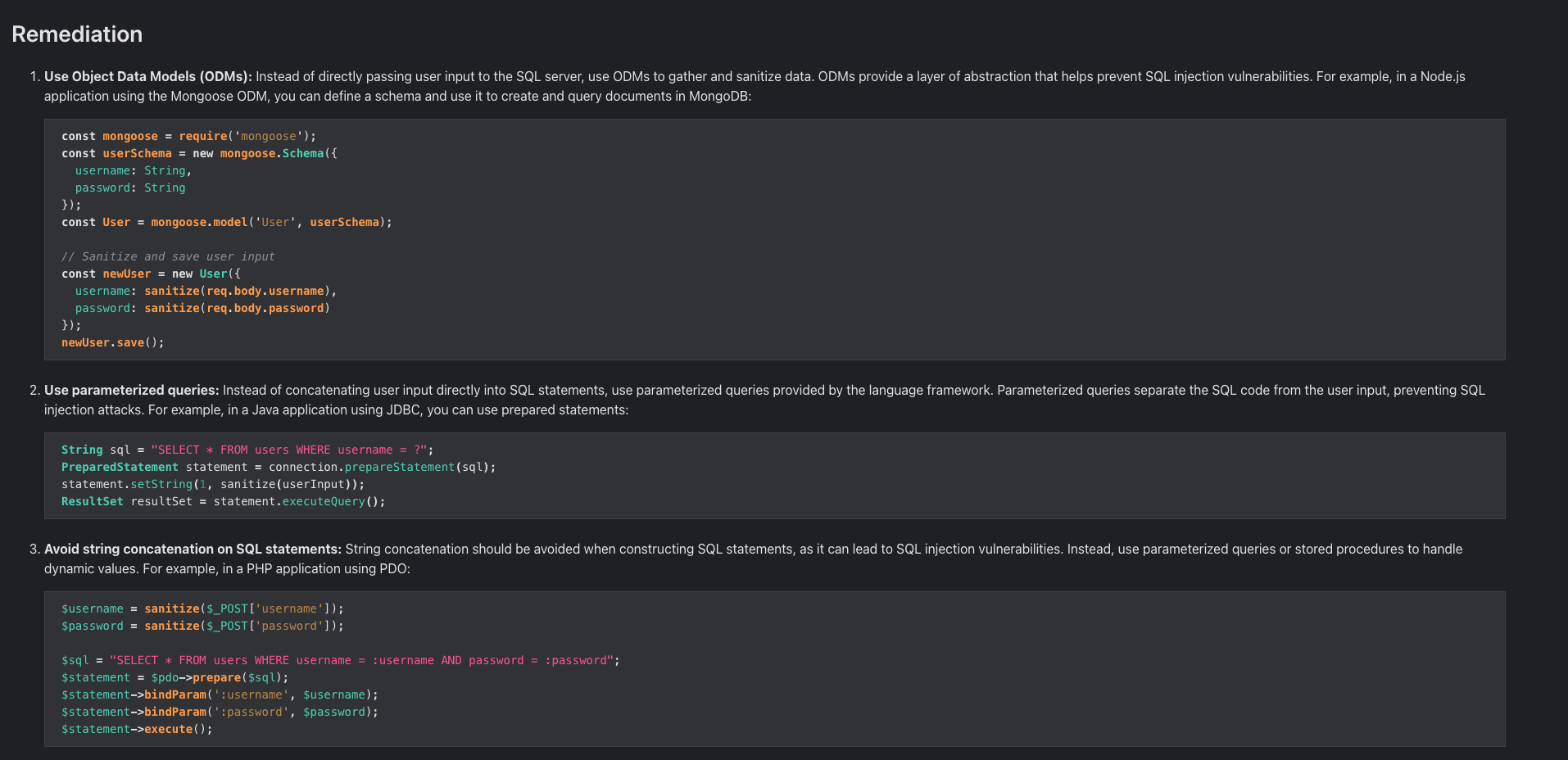
The difference between StackHawk and Escape is that Escape offers detailed remediation code snippets that are tailor-made for major frameworks:

More than that, Escape aims to educate developers about security best practices, so they not only fix vulnerabilities but also understand how to prevent similar issues in future development and adopt security by design.
"It's been a huge benefit for the development team."
Nicolas Gaudin, CISO, Shine
Context: the key to strengthening your business security
StackHawk's prioritization is based on the OWASP Risk Rating Methodology. The OWASP Risk Rating Methodology primarily focuses on the technical aspects of security issues, such as their impact and exploitability. It may not take into account the specific context of your application, or your business objectives. As a result, it may not align perfectly with your organization's risk tolerance or priorities.
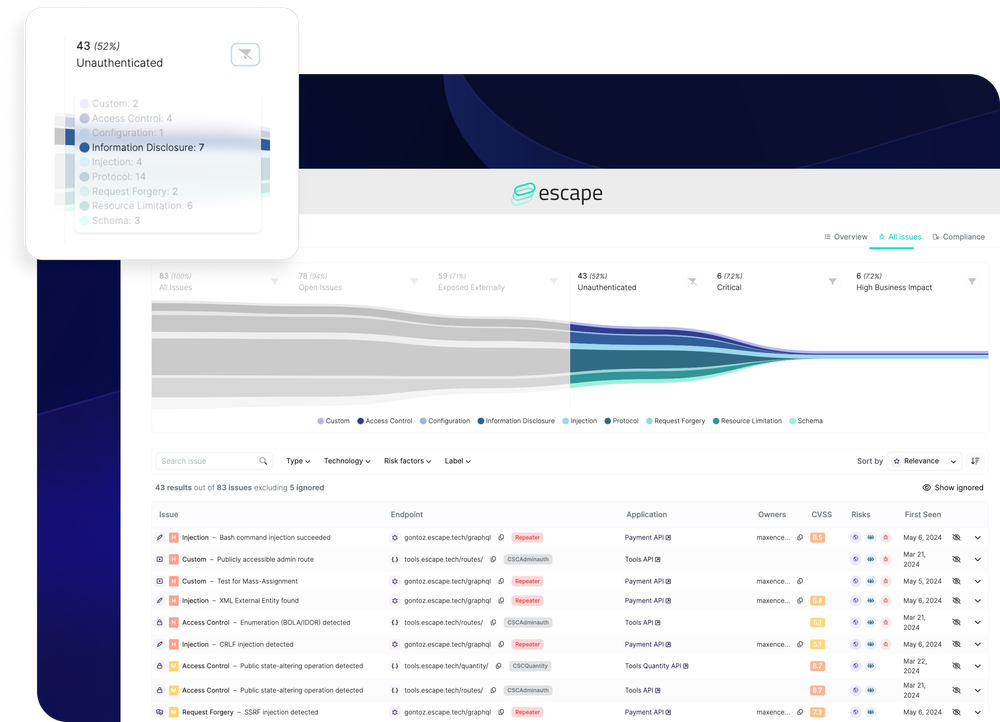
With Escape, each remediation comes with a detailed explanation of why a particular vulnerability is a high, medium, or low risk in your specific context.
Scoring and categorization take into account factors such as
- whether they can be reproduced with or without authentication,
- if the endpoint is publicly exposed on the internet
- if the API schema is public
This detailed scoring and categorization system will help you make informed decisions about which vulnerabilities should be addressed first and allocate your resources efficiently. It prevents unnecessary panic over low-risk issues and ensures that critical high-risk vulnerabilities that are important to your business are promptly remediated.
Conclusion
We hope this comparison was useful. So, let's wrap it up!
While both Escape and StackHawk offer valuable features, Escape stands out with its agentless API discovery, automated schema generation, and proprietary business logic security testing algorithm. These capabilities enable organizations to identify and address vulnerabilities more efficiently, without the need for manual configurations or extensive maintenance. Additionally, Escape provides developer-ready remediation code snippets, tailored to various development frameworks, which streamline the patching process and enhance overall security posture.
To put it simply, if your goal is to attain comprehensive security observability and accelerate the remediation process within your development team, Escape is your top choice! With Escape, you can be assured that no Shadow or Zombie applications will slip through the cracks and will be tested for business-critical vulnerabilities.
Learn more about Escape
Schedule a time with our product expert to see for yourself how Escape DAST identifies even complex business logic vulnerabilities and integrates with your modern stack.
Book a demo💡Want to learn more? Discover the following articles:
