API gateway security: 8 best practices

Are your API gateways well secured? If you have doubts, then they are not. API gateways play a large role in securing the flow of data between clients and backend services. But with the surge in API adoption (nearly 90% of developers are using APIs) and the increasing sophistication of cyber attacks, ensuring the security of your API gateway is more critical than ever.
At the enterprise level, most APIs are deployed using API gateways. For instance, a banking application could leverage an API gateway to seamlessly invoke and consolidate results from different services. Whether securely processing payments or offering customers real-time access to financial data, API gateways play a crucial role in enhancing the overall user experience.
So how can you ensure your API gateways are secured? This is also one of the questions we hear from the potential customers. Don't worry! We've got you covered with eight best practices tailor-made to enhance your API gateway security.
What is an API gateway?
An API gateway is a critical component in modern software architecture that acts as an intermediary between clients and backend services, providing a centralized entry point for managing and securing access to APIs. It serves as a single point of entry for clients, abstracting away the complexities of the underlying microservices architecture and providing various functionalities such as routing, security, rate limiting, authentication, and monitoring.
Interestingly, as technology evolves, many API gateways adopt features typical of API catalogs or API portals, such as documentation and user management.
A visual learner? Discover the video below to learn more about what is API gateway:
Existing API gateway types
Here are several examples of the API gateways that might need to be secured:
- NGINX: NGINX is a high-performance web server and reverse proxy that can also function as an API gateway. It offers features such as request routing, load balancing, SSL/TLS termination, and caching, making it suitable for handling API traffic at scale.
- Kong: Kong is an open-source API gateway built on top of NGINX and Lua scripting language. It provides a rich set of features including authentication, rate limiting, logging, and plugin architecture for extending functionality.
- Amazon API Gateway: Amazon API Gateway is a fully managed service provided by AWS (Amazon Web Services) for building, deploying, and managing APIs at scale. It offers features such as request/response transformation, authorization, throttling, and integration with AWS Lambda and other AWS services.
- Apigee: Apigee, now part of Google Cloud, is a comprehensive API management platform that includes an API gateway component. It provides capabilities for API security, traffic management, analytics, and developer portal, catering to the needs of enterprises with complex API ecosystems.
These examples illustrate the diversity of API gateway solutions available in the market, each with its own set of features, deployment options, and integration capabilities to meet the specific requirements of different use cases and organizations.
What is API security?
API security involves implementing measures and protocols to protect APIs from unauthorized access, misuse, and malicious API attacks. It encompasses practices such as authentication, encryption, input validation, rate limiting, and monitoring to ensure the integrity, confidentiality, and availability of APIs and the data they handle.
With APIs dominating dynamic Internet traffic around the globe (57%) and API secret sprawl on the web, organizations of all sizes and not only enterprises must think about protecting their applications.
The API gateway's role in security
The API gateway serves as a critical component in ensuring the security of APIs. API gateways typically have the capability to execute the following functions:
- Centralized entry point: The API gateway acts as a centralized entry point for managing and securing access to APIs.
- Enforcement of security policies: It enforces security policies such as authentication, authorization, encryption, rate limiting, and monitoring to protect against unauthorized access and data breaches.
- Secure communication: The API gateway facilitates secure communication between clients and backend services, ensuring that data exchanges are protected from interception and tampering.
- Abstraction of complexity: It abstracts away the complexities of the underlying architecture, providing a simplified interface for clients to interact with backend services securely.
- Protection of API endpoints: The API gateway protects API endpoints and the data they handle by implementing essential security functionalities.
- Mitigation of security threats: By providing essential security functionalities, the API gateway helps mitigate various security threats, including unauthorized access, data breaches, and other malicious activities.
While API gateways offer essential basic security controls for APIs, they may not fully address API-specific threats or business logic vulnerabilities. API gateways primarily serve as critical components for API management rather than comprehensive security solutions. Therefore, organizations should complement API gateway security with additional measures, like automated API security testing tools, to effectively protect their APIs and mitigate potential risks.
8 API gateway security best practices
API gateways, if compromised, can pose significant security risks.
Before diving into the best practices, let's examine a common pitfall in API gateway security. Consider a scenario where a poorly configured authorization policy exposes vulnerabilities. An API gateway requires a secret (such as an API key) for accessing an endpoint. However, if the request is forwarded to the backend service without proper authorization enforcement, the backend automatically authorizes the request. As a result, anyone with access to the backend service within the internal network can bypass authentication entirely.
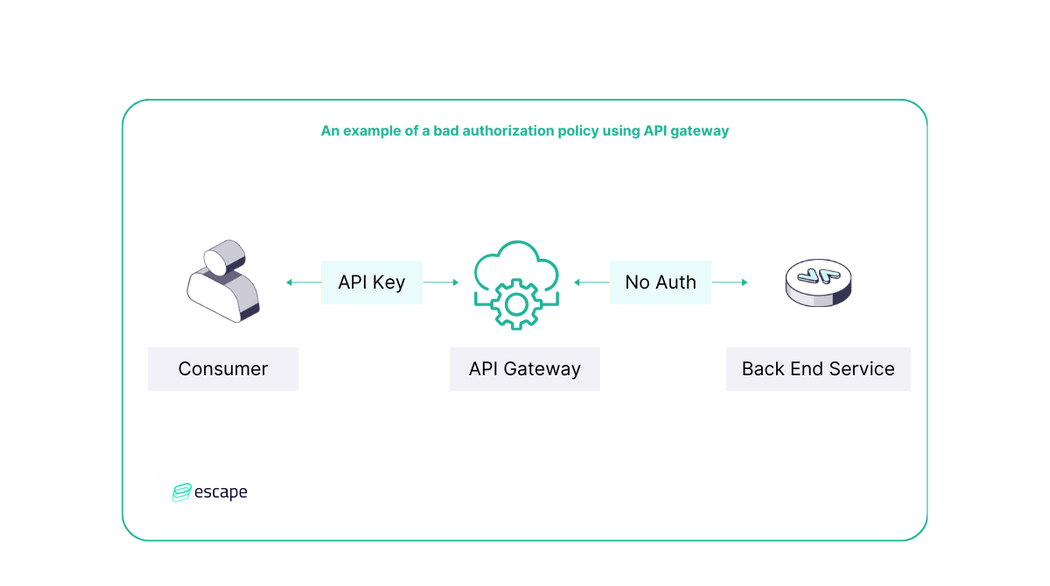
This oversight can lead to unauthorized access to sensitive data and potential data breaches - the service becomes vulnerable to server-side request forgery (SSRF) attacks.
Now, let's explore eight essential best practices for API gateway security and mitigate such risks:
- Implement strong authentication: Authentication is the process of verifying the identity of clients accessing the API gateway. Robust authentication mechanisms such as OAuth, API keys, or JWT tokens should be used to validate the credentials of users and ensure that only authorized entities can access API resources.
- Enforce authorization policies: Define granular access controls and authorization policies to restrict access to specific API resources based on user roles and permissions.
- Enable encryption: Encryption is essential for protecting data transmitted between clients and the API gateway from eavesdropping and tampering. Employing encryption protocols such as HTTPS/TLS ensures the confidentiality and integrity of data exchanges, protecting sensitive information from unauthorized access.
- Implement input validation: Validate and sanitize incoming requests to prevent common security vulnerabilities such as injection attacks (e.g., SQL injection, XSS) and protect against malformed or malicious input.
- Enforce rate limiting and throttling: Rate limiting and throttling mechanisms help prevent abuse and mitigate denial-of-service (DoS) attacks by limiting the number of requests that clients can make to the API gateway. This ensures fair usage of API resources and maintains the performance and availability of the system.
- Secure configuration management: Proper management of API keys, secrets, and certificates is essential for maintaining the security of the API gateway. Organizations should follow best practices for secure configuration management that we detailed in our recent report, "The State of API Secret Sprawl", to minimize exposure of sensitive information and prevent unauthorized access to API resources.
- Monitor and audit API Traffic: Deploy monitoring and logging solutions to track API usage, detect anomalies, and audit access patterns for security compliance and forensic analysis.
- Regularly update and patch: Keep the API gateway software up to date with the latest security patches and updates to address known vulnerabilities.
Can Escape help you ensure your API gateway security?
Yes, the Escape API Security & DAST Platform integrates with your existing API gateways (for example, Mulesoft, WSO2, AWS, and Kong).
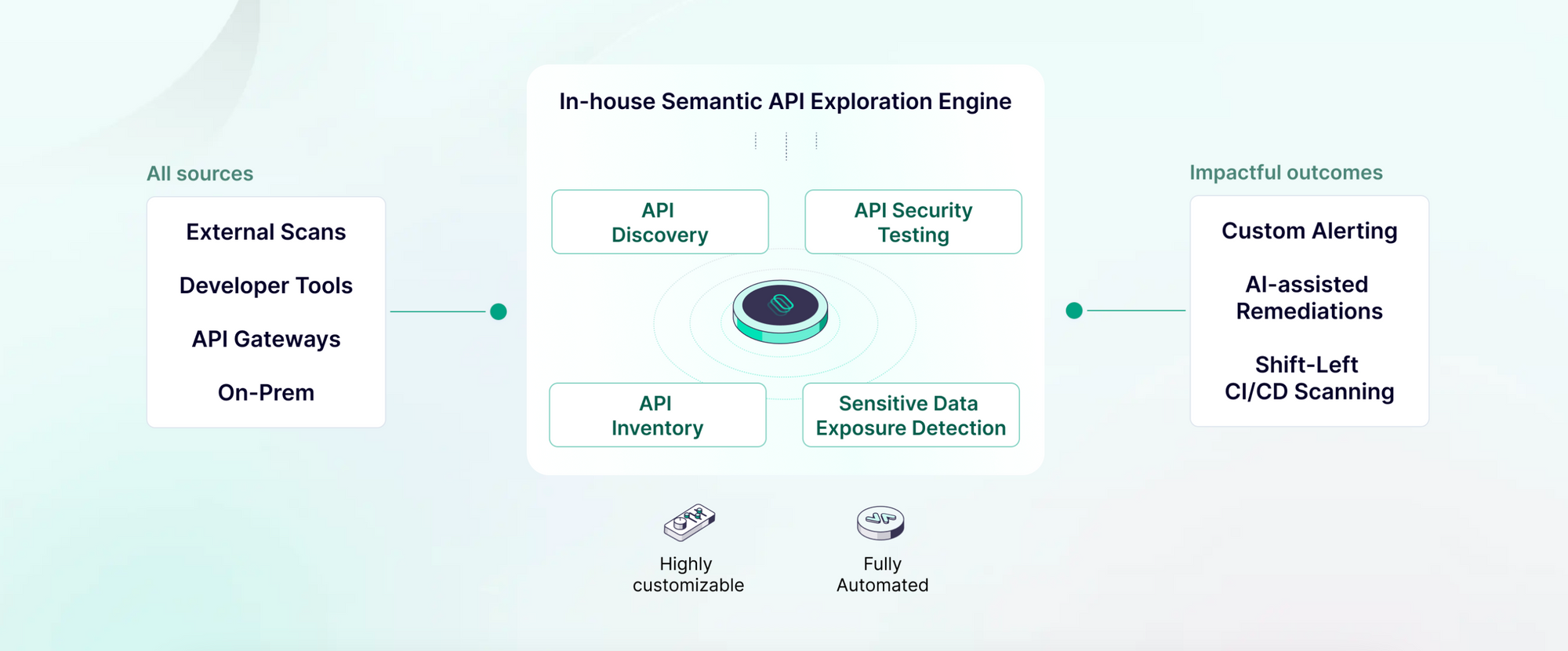
From a diverse range of sources, including API gateways, Escape combines all aspects of API security.
First, it helps you get an inventory of all your APIs (including RESTful, GraphQL, and gRPC) in minutes. Escape's API discovery helps you to get information on everything your developers expose online (which could happen before your AppSec team was even there, right?), including Shadow APIs and Zombie APIs.
After that, Escape conducts a comprehensive series of dynamic application security tests with its proprietary algorithm to thoroughly assess vulnerabilities. This process provides a clear picture of all risks, including detection of OWASP Top 10 and complex logic flaws like sensitive data leaks.
The best part is all of this can be done in as little as 15 minutes, without complex integrations or traffic monitoring.
