How to avoid data breaches with GraphQL?
Manage your sensitive data in GraphQL applications (PII, passwords, secrets…)
We released a new feature in Escape that enables you to detect and fix data leaks with GraphQL.
🚫 The GraphQL Access Control issue, what is it?
Access control is the restriction that tells the user who or what can be accessed in your application. When a user can access a forbidden resource, there is an access control vulnerability.
Your GraphQL application has a schema that defines the relationship between objects. You must secure all the paths to avoid having an access control vulnerability.
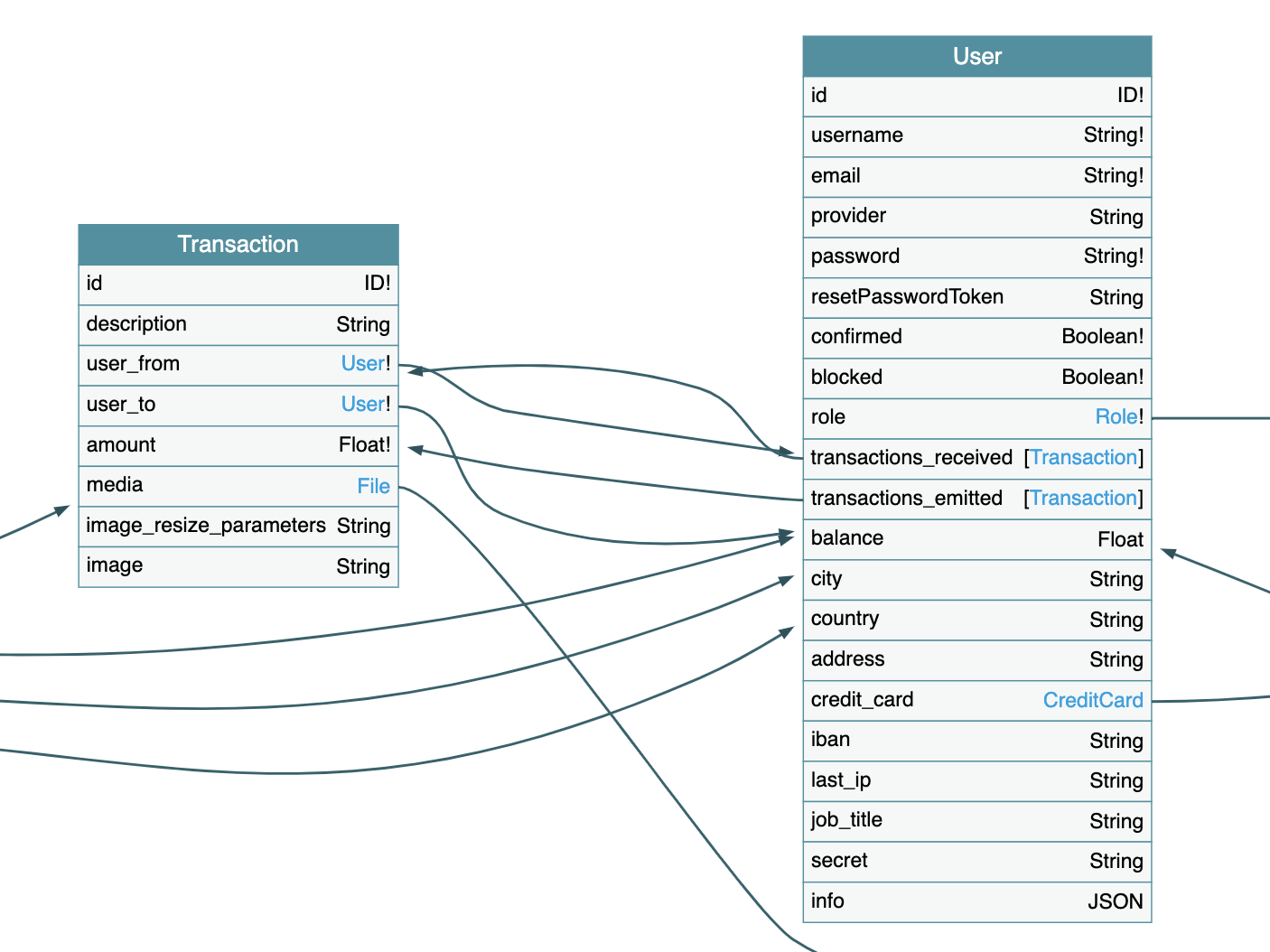
The more your app has objects, the more your app has paths. Using Escape can save you time by scanning all those paths automatically and give you monitoring of your sensitive data.
🛡️ What does Escape do?
Escape DAST will run a legitimate traffic simulation into your app and rebuild a GraphQL schema to explore all paths that land on an object. Our CLI can find tokens, PII, Stripe Tokens, financial information and RSA Keys.
Here are some examples of access control vulnerabilities that Escape can find: Private data: Escape will raise an alert if it successfully accesses any object without being permitted. For example, if a non-admin user has access to CreditCard objects.
Tenant isolation: Escape will raise an alert if it successfully accesses any unique object of this type with two different users. For example, if two users access the same CreditCard object.
If Escape finds those sensitive data, the platform will automatically display it, and you can now start making your app more secure!
⚙️ How to manage your sensitive data?
Here is the Sensitive Data view of a scan run with Escape's GraphQL Security Scanner, which enables you to detect and fix your data leaks.
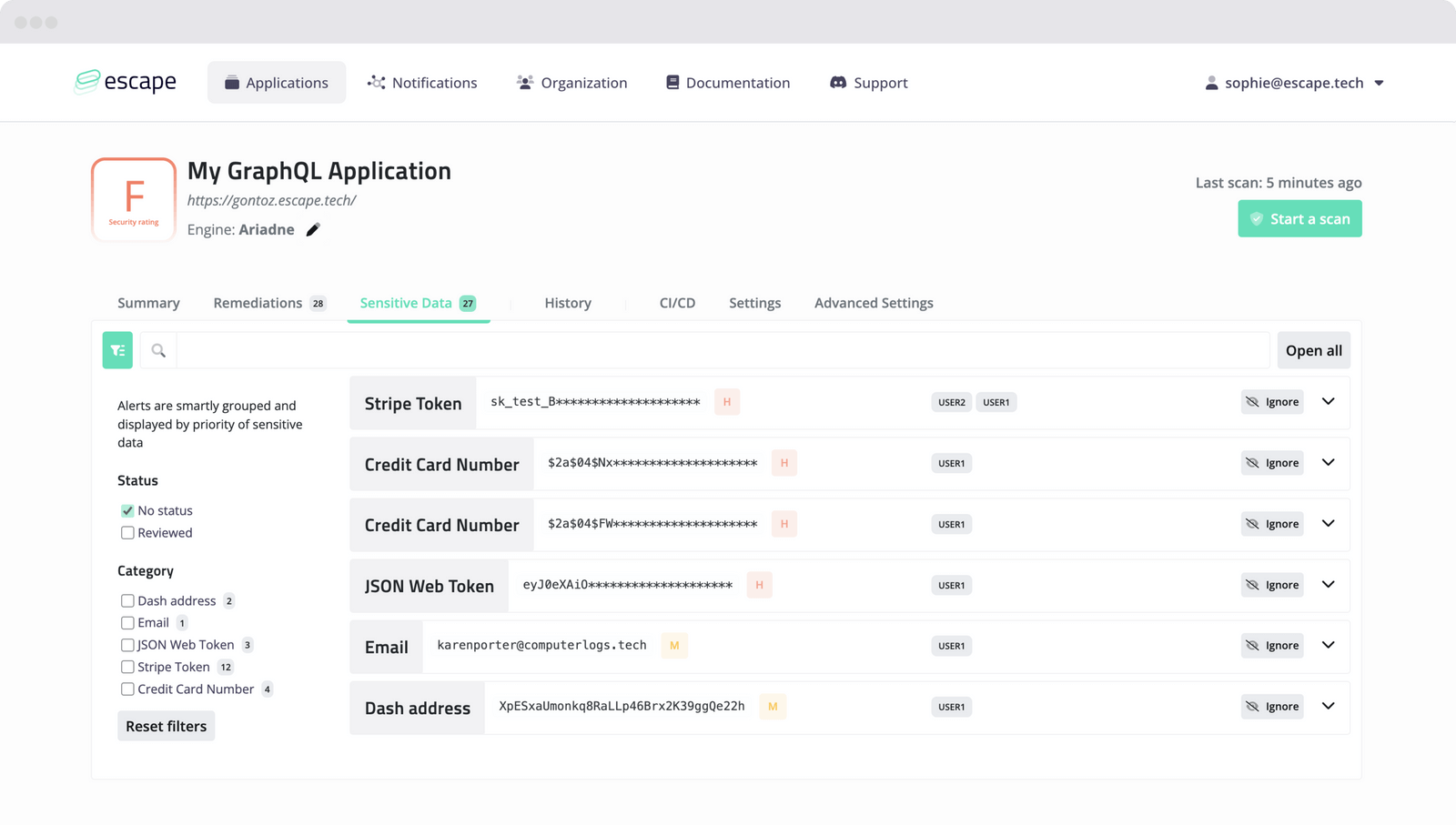
This is an example of all the sensitive data accessible in the app. As you can see, data leaks are classified by severity. High-severity data values like Stripe token, BCrypt hash, and JSON Web Token are found here. But also medium personal data like email or Dash address. You can check all the data Escape can find in the documentation.
You can also see which users have access to this data, which gives you information about tenant isolation, private data, and private fields.
To see where this data was found, open the sensitive data card:
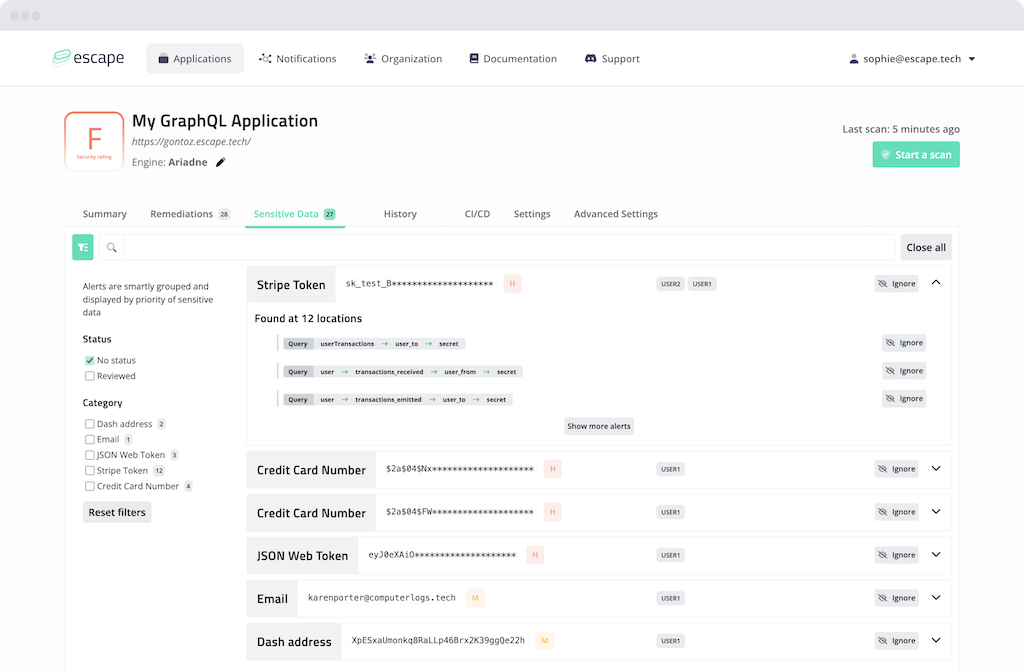
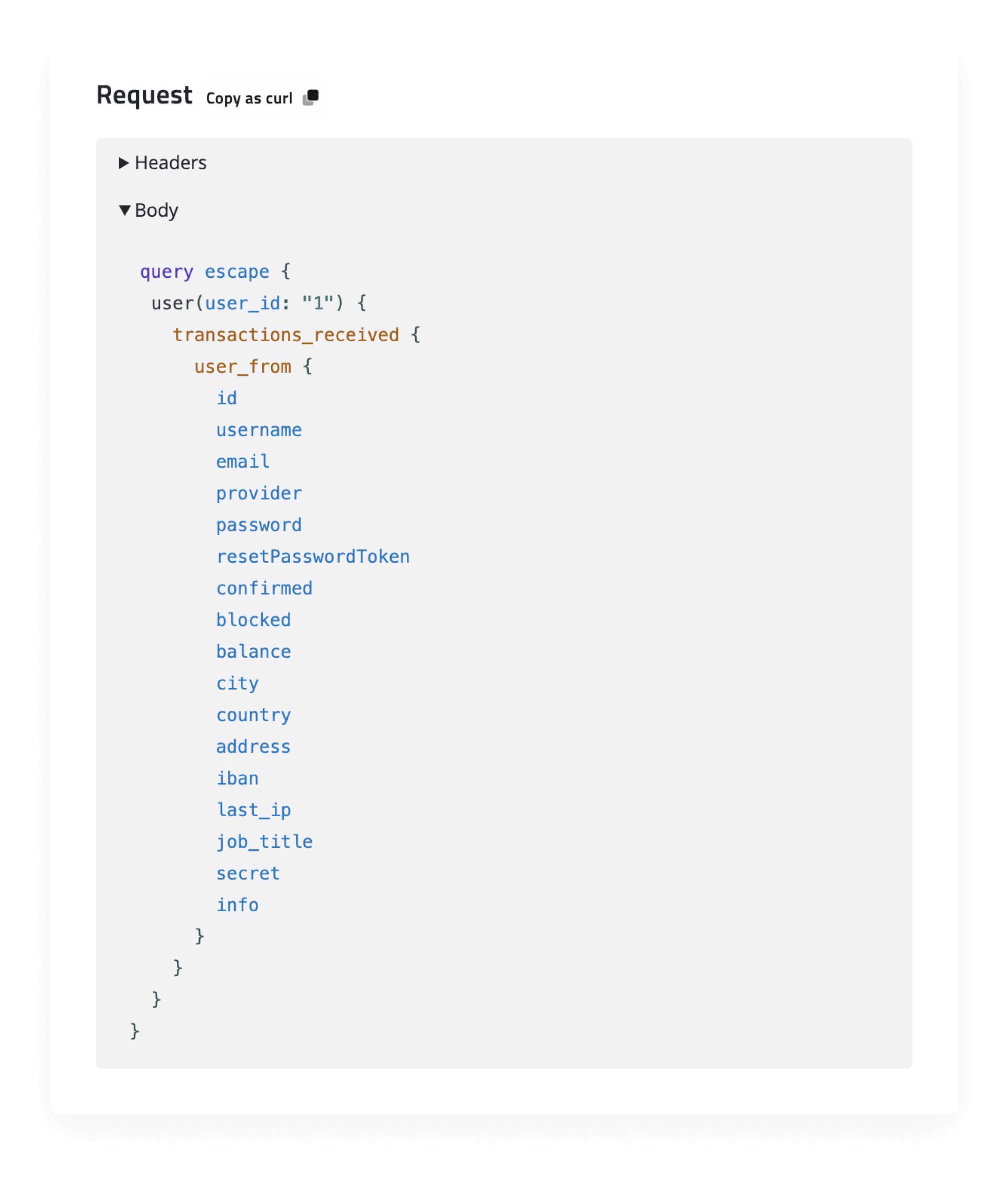
To have more information about how to reproduce the data finding, open the side panel by clicking on the location. Here, you will find information about requests and responses.
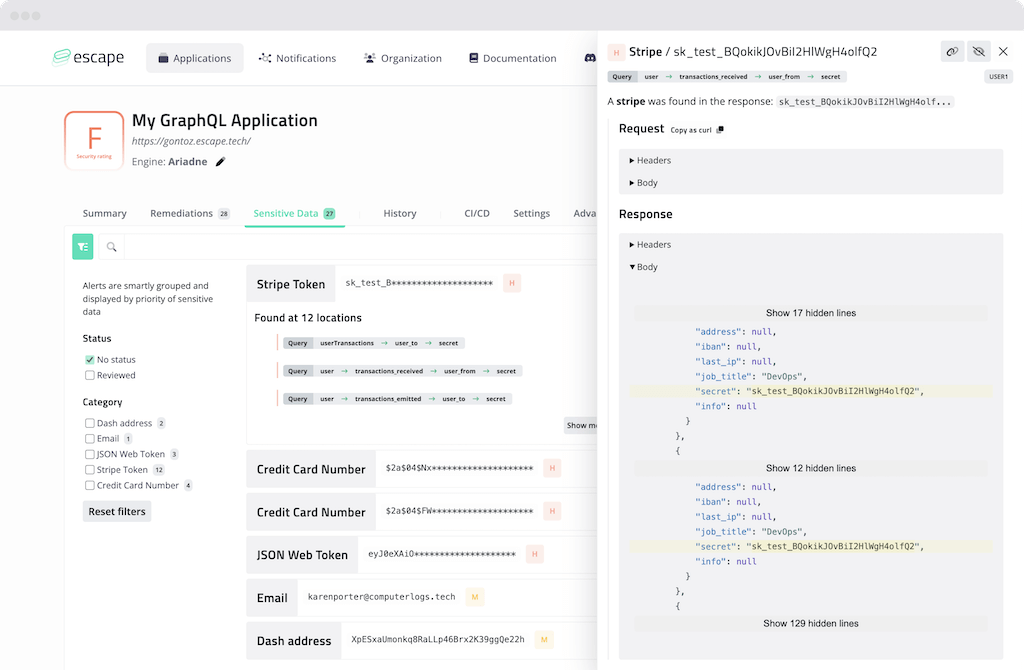
For instance, to reproduce the request, you can copy the query:
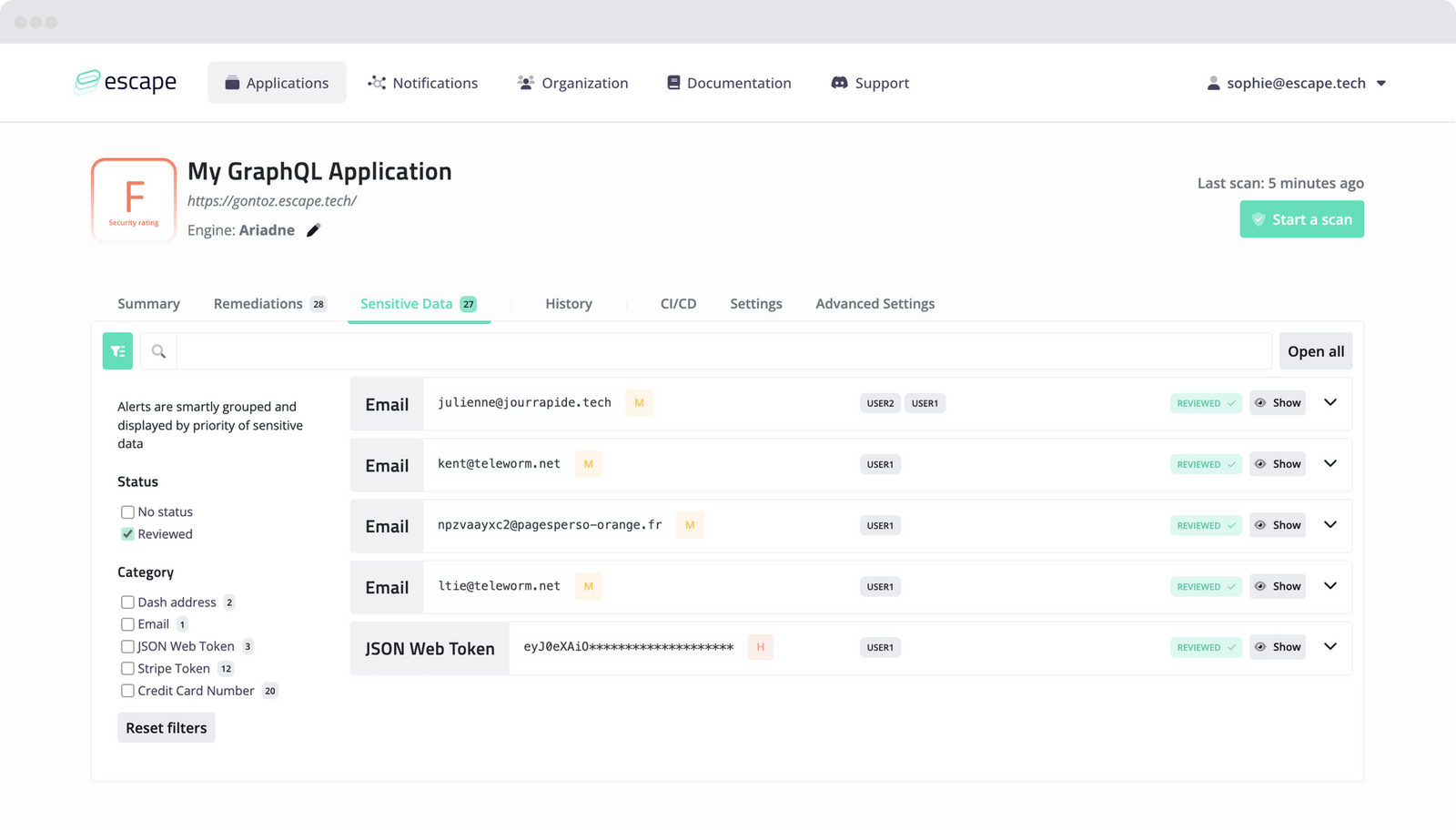
If this data is not sensitive, ignore them. It will be classified as reviewed, as you can see below:
Want to secure your GraphQL application now? Our comprehensive solution identifies and mitigates over 104 advanced security issues, including resolver performance, tenant isolation, sensitive data leaks, injections, error handling, compliance, and more.
You can't secure what you can't see. Let Escape DAST help you build a comprehensive inventory of all your APIs, including GraphQL, REST, and gRPC.
Learn more about Escape DAST
Schedule a time with our product expert to see for yourself how Escape identifies even complex business logic vulnerabilities in your GraphQL applications
Book a demoAdditional resources for GraphQL security
- Authorization through access control in GraphQL
- 9 GraphQL Security Best Practices
- GraphQL errors: the Good, the Bad and the Ugly
