What are the actual benefits of pentesting? Insights from Harsh Modi
This blog is based on our conversation with Harsh Modi, Senior Security Engineer at Bell. It explores what are the benefits of pentesting, and its real-world implications.

In cybersecurity, a question often arises among CISOs and AppSec professionals: Is penetration testing really worth the investment, or is it merely an overrated checkbox in a security program? As cybersecurity threats evolve, organizations increasingly rely on penetration testing (pentesting) to identify vulnerabilities before they can be exploited. But with costs ranging from a few thousand to hundreds of thousands of dollars, what are the actual benefits of pentesting?
In this article, we will share insights from cybersecurity expert Harsh Modi as he explores the benefits of pentesting and how they translate into real-world implications for organizations. Dive right in!
Harsh Modi's Background
With over 8 years of dedicated experience as an Offensive Security Engineer and Penetration Tester, Harsh Modi has honed an exceptional skill set in identifying and mitigating security vulnerabilities. Currently, he is a Senior Security Engineer and Penetration Tester at Bell Canada.
Harsh is also an enthusiastic security researcher and has presented his research at various conferences such as OWASP Vancouver, BSides Vancouver, Edmonton, Calgary, and others, where he shared invaluable insights on different topics ranging from pentesting Android applications to car hacking.
With all his experience in pentesting and offensive security, We decided to challenge him on the actual value of pentesting programs.
Watch the full podcast below:
The True Value of Pentesting
Harsh, as an experienced offensive security engineer, highlights that while the initial rounds of pentesting often reveal numerous vulnerabilities, the process's true value lies in the iterative nature of testing.
"In my experience, there is always something to find." - Harsh Modi
As developers become more familiar with secure software development life cycles and security principles, the number of vulnerabilities decreases, but pentesting remains crucial for identifying more complex issues like business logic flaws.
Pentesting goes beyond the capabilities of automated tools, which are often the go-to for junior cybersecurity engineers.
"Real pentesting has no range [...] sometimes the presentation of those pentests is only one slide." - Harsh Modi
Real-World Implications
Pentesting's implications extend far beyond ticking off compliance requirements. It’s about understanding and mitigating risks before they manifest into significant security breaches. As organizations become more dependent on digital infrastructures, pentesting helps maintain the integrity and security of these systems by continually challenging and testing their defenses.
"Sometimes you are not expecting something to happen... I have lots and lots of stuff where we were able to replace a third-party library on a mobile application that gave us complete access to the phone... we were able to see the contacts, we had a reverse shell and everything." - Harsh Modi
Pentesting Catches Behavioural Issues
For instance, Harsh mentions how even in well-secured environments, pentesting can uncover "business logic flaws" that might not be immediately apparent but could have serious consequences if exploited.
In one of his anecdotes, Harsh recalls an instance where pentesting revealed vulnerabilities in a mobile application that allowed access to user data through a third-party library. This kind of vulnerability, which can grant attackers access to sensitive information, underscores the importance of thorough pentesting in safeguarding not just the infrastructure but also user trust.
Another significant real-world implication is the evolution of social engineering attacks, despite technological advancements.
"Social engineering amazingly works sometimes. [...] There is always the social engineering guy or girl, and he or she comes up and fools someone who is at a much higher level in the Enterprise and gets complete access just by writing an email." - Harsh Modi
This highlights the need for pentesting to include human elements, such as phishing simulations, to prepare organizations against a broader range of potential threats. Understanding and managing third-party risks is critical.
Zero Trust and Third-Party Risks
The Zero Trust model has become a critical strategy today, especially as organizations increasingly rely on third-party software, libraries, and external vendors. Harsh Modi emphasizes that while many companies invest in securing their internal assets, they often overlook the risks posed by third-party components.
These components, which can include anything from open-source libraries to acquired software solutions, are frequently integrated into an organization's systems without thorough vetting or continuous monitoring.
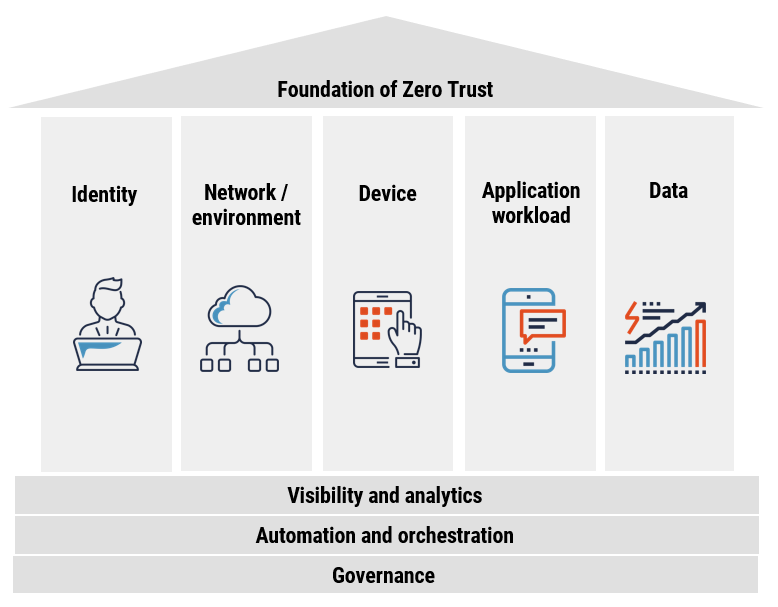
The Zero Trust approach fundamentally changes how organizations view and manage security. Traditionally, trust was granted to internal networks and systems by default, with a focus on securing the perimeter. However, with the rise of cloud computing, mobile workforces, and complex supply chains, this perimeter has become increasingly blurred. Zero Trust advocates for the principle of "never trust, always verify," meaning that every access request, whether it comes from inside or outside the network, must be authenticated and authorized.
"You should not carry your phone because there are lots of sensors in the mobile phone that you have absolutely no control over... those can predict whether you are on the second floor, first floor, third floor, and all those kinds of things." - Harsh Modi
This model is particularly important when dealing with third-party risks. Even if an organization secures its own code and infrastructure, the introduction of external code—be it from a library, a cloud service, or a partner’s system—can create vulnerabilities. These vulnerabilities are often hidden and can be exploited if not properly managed. For instance, a third-party library might contain outdated code with known security flaws, or a newly acquired company's software might have been developed with lax security practices.
Harsh suggests that a rigorous testing and continuous monitoring process for all third-party components is essential. This includes performing security assessments on all external codes before they are integrated, as well as ongoing audits to ensure that these components remain secure as threats evolve.
Furthermore, the Zero Trust model requires organizations to segment their networks and limit the access of third-party components to only what is absolutely necessary. By doing so, even if a third-party element is compromised, the potential damage is contained.
In essence, adopting a Zero Trust approach is not just about securing an organization’s direct assets; it’s about recognizing that every connection, every piece of code, and every external interaction is a potential risk. As the cybersecurity landscape continues to evolve, Zero Trust will likely become a cornerstone of effective security strategies, particularly in managing the growing complexity of third-party risks.
While this approach has become a foundational strategy for securing modern infrastructures, it still faces significant challenges in API security.
APIs, often serving as gateways to critical data and services, can be vulnerable if not properly secured. Current Zero Trust solutions may lack the granularity and comprehensive capabilities needed to monitor and protect APIs effectively, leaving organizations exposed to potential breaches. To truly secure your APIs, consider exploring Escape’s API security solution that go beyond traditional Zero Trust implementations, providing the robust protection your organization needs.
Best Practices for Effective Pentesting
General Recommendations
- Integrate Pentesting into the SDLC: Integrating security practices early into the Software Development Life Cycle (SDLC) can significantly reduce vulnerabilities. Harsh emphasizes the importance of "shift-left" approaches, where security assessments are conducted during the development phase rather than after code deployment.
- Focus on Business Logic: To properly test your application's business logic, the ideal solution is the combination of automated tools with human support. You cannot do one without the other with the current tools on the market.
- Educate and Evolve: Regular training and updates are crucial because well-informed staff can better prevent and respond to threats. Furthermore, organizations must continually evolve their testing methodologies to stay ahead of new attack vectors.
- Documentation and Follow-Up: Proper documentation of pentesting results and subsequent remediation steps are essential. Harsh advises that teams should document everything to ensure continuity and preparedness, even as teams change over time.
- Combine Tools with Human Ingenuity: While tools are necessary, they should not replace human insight. The human mind’s role in understanding and interpreting the results from these tools is irreplaceable, as emphasized by Modi’s advice not to rely solely on automated tools.
"My understanding is that education to the people is much much more important than real life." - Harsh Modi
Spotlight on Asset Inventory
Understanding and maintaining an accurate asset inventory is a fundamental aspect of cybersecurity, yet it's often overlooked. Harsh Modi underscores that many organizations fail to fully grasp the extent of their assets, which can lead to significant security risks. Asset inventory involves cataloging all hardware, software, and digital resources within an organization. This comprehensive understanding is crucial because you can't protect what you don't know exists.
"A lot of companies actually don't know what they own, and it seems a little bit scary to me. Because you should at least know how many things you own over the internet. [...] Asset Management and inventory is a big thing today a lot of people don't do it properly." - Harsh Modi
When an organization lacks a complete and up-to-date asset inventory, it opens the door to numerous vulnerabilities. For example, outdated software or forgotten systems that are still connected to the network may not receive necessary security updates, making them prime targets for attackers. Additionally, as organizations grow and evolve, they often acquire new assets, either through organic growth or mergers and acquisitions. These new assets might include legacy systems or software that were not developed with current security standards in mind, further complicating the security landscape.
To address these challenges, Harsh recommends that organizations regularly update their asset inventories and ensure that they have a detailed understanding of all the components within their network. This process should include identifying the owners of each asset, understanding the purpose and importance of each asset, and knowing the potential risks associated with them. Additionally, integrating asset inventory management with other security practices, such as vulnerability management and incident response, can help ensure that any identified risks are quickly addressed.
Discover All Your Assets in Minutes
Discover, catalog, and contextualize all your exposed assets and their owners in your organization within minutes
Get started nowBy prioritizing a comprehensive asset inventory, organizations ensure that all assets are accounted for and properly secured.
Conclusion
Organizations can boost their security by incorporating pentesting into the development process, focusing on business logic, and making continuous education and documentation a priority.
Sure, pentesting might seem expensive at first, but the insights you gain from thorough testing are worth far more than the cost of missing hidden vulnerabilities.
Automation can help, but it’s crucial to ensure your tools not only support but also understand and continuously learn the business logic behind your applications like the emerging agentic pentesting tools. As the speed of applications' deployment and threats evolve, so should our methods to detect and stop them - making advanced solutions that can pentest applications a necessity, not just a box to check once.
"In my experience, there is always something to find or there is something available." - Harsh Modi
You may also be interested in:
