Vulnerability Management Lifecycle: 5 Steps and Best Practices
Maintaining robust security of your organization is not just crucial in 2023 – it's a survival strategy. The recent data breach at 23andMe in October 2023 is a case in point. This incident, where a credential-stuffing attack led to unauthorized access to customer accounts, underscores a harsh reality. Even biotech companies, handling sensitive genetic data, aren't immune to cyber threats. It shows us how vulnerabilities, if left unchecked, can compromise not just data but also customer trust. This is precisely why a meticulously crafted Vulnerability Management Lifecycle is indispensable for any organization that values its digital integrity.
Leveraging our collective expertise, we're here to guide you through the essential 5 steps of vulnerability management, making sure you're not just ready, but also quick on your feet when it comes to cyber threats. Our goal is clear – stick to the best practices, because that's the solid ground on which your unbreakable security will stand.
After reading this article, you'll:
- Understand the significance of a comprehensive vulnerability management
- Master the 5 key steps in vulnerability management lifecycle for a proactive security approach
- Be prepared to turn vulnerabilities into well-managed risks effectively
What is the vulnerability management lifecycle?
The vulnerability management lifecycle is a vital and continuous process that systematically enables organizations to identify, prioritize, and mitigate vulnerabilities within their IT infrastructure. It encompasses a thorough assessment of potential security weaknesses, prioritizing them based on risk, followed by effective mitigation strategies. The cycle includes constant validation and reporting to ensure vulnerabilities are comprehensively managed. This approach is essential for reinforcing an organization's security framework, protecting sensitive data, and reducing the likelihood of cyber exploitation.
This lifecycle is not just a security measure but a strategic necessity. With the evolving threat landscape, as exemplified by recent CISA alerts on new vulnerabilities like the Google Skia Integer Overflow (CVE-2023-6345) and ownCloud graphapi Information Disclosure (CVE-2023-49103), the urgency for a robust vulnerability management process has never been more pronounced.
Understanding the importance of vulnerability management
As we dive into the importance of vulnerability management, it’s vital to recognize its role as the key in any robust cybersecurity strategy. A methodical approach to managing vulnerabilities contributes significantly to cyber risk reduction and data breach prevention. To highlight this point, let's consider the 4 ways vulnerabilities can impact an organization's security:
- Vulnerabilities can serve as entry points for hackers, potentially leading to catastrophic data breaches.
- Unaddressed security weaknesses can harm an organization's reputation and lead to a loss of customer trust.
- The financial implications of a breach can be severe, including regulatory fines and remediation costs. According to the IBM Cost of a Data Breach Report 2023, the global average cost of a data breach in 2023 was $4.45 million.
- A robust vulnerability management process can help protect sensitive information from unauthorized access.
Effective vulnerability management actively protects various aspects of an organization's digital framework. It’s about much more than just patching up software; it’s a comprehensive strategy that ensures security measures evolve as fast as the threats themselves.
Below you can find benefits to organization based on each vulnerability management outcome.
| Vulnerability Management Outcomes | Benefits to Organization |
|---|---|
| Early Identification of Risks | Allows for swift action and reduces the chance of exposure |
| Regular Security Assessments | Maintains a robust defense system against evolving cyber threats |
| Strategic Patch Management | Minimizes windows of opportunity for attackers to exploit weaknesses |
| Compliance with Regulations | Ensures the organization meets industry standards, avoiding fines |
| End-user Education | Enhances the overall security culture of the organization |
We cannot overlook the fact that vulnerabilities are not just flaws within our systems—they are potential threats to our operational integrity. The essence of vulnerability management lies in its ability to transform potential weaknesses into strengths—by not just reacting to threats, but anticipating and preventing them.
Stay with us as we further explore how understanding the nuances of vulnerability management will help you to ensure our organization's resilience in the face of cyber risks.
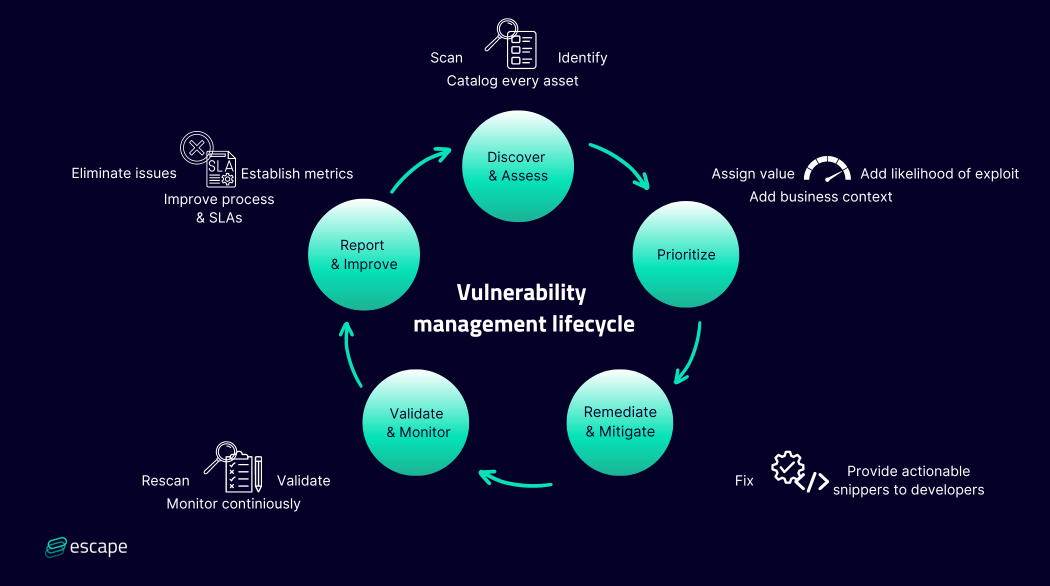
What are the 5 steps of the vulnerability management lifecycle?
The five main steps of the vulnerability management lifecycle are:
- Step 1: Asset discovery and assessment
- Step 2: Prioritization of identified vulnerabilities
- Step 3: Remediation and mitigation
- Step 4: Validation and monitoring
- Step 5: Reporting and improvement
Below you can find the detailed schematic representation of each step in the lifecycle:
At this stage, our main goal is to set up a strong system for managing vulnerabilities.
Let's start by identifying assets and defining the scope, establishing the ownership, and clarifying roles.
Initiating the vulnerability management process
Identifying assets and defining the scope
At the heart of an effective vulnerability management program lies the rigorous process of asset identification. It's imperative for us to thoroughly catalog every asset within our organization's attack surface, acknowledging both the tangible and intangible variables. We categorize and prioritize the critical assets, evaluating their significance and susceptibility to potential threats. This helps to construct a well-defined vulnerability management scope, incorporating all facets of our digital and physical infrastructure.
- Inventory of digital assets – Starting with our software applications, databases, and network configurations.
- Catalog of hardware components – Spanning from servers to user-endpoint devices.
- Assessment of data criticality – Identifying which datasets are essential for our operations and carry the highest level of importance and risk.
- Evaluation of intellectual property – Accounting for proprietary processes and technologies.
“You can't secure what you can't see, right?”
Establishing ownership and roles
For robust vulnerability management, effective leadership and clear-cut roles are non-negotiable. Assigning ownership for different assets and segments of the vulnerability management process fosters accountability and ensures that tasks are not just assigned but are also executed with precision.
Based on our experience at Escape, below is an example of the division of roles in application security assets within the organization. From the Chief Information Security Officer (CISO) overseeing the overarching strategy to the Security Engineers conducting vulnerability scans, a clear definition of cybersecurity roles is fundamental to driving quick and decisive action in the event of a vulnerability being detected.
| Role | Responsibility | Accountability in Security |
|---|---|---|
| CISO | Strategic oversight of vulnerability management program | Ultimate decision-making and risk management authority |
| Security Engineer | Conducts vulnerability assessments and analysis | Identifying and evaluating potential vulnerabilities, and ensuring their resolution by the development team |
| Development team | Fix identified vulnerabilities | Ensuring vulnerabilities are remediated in a timely manner |
| End users | Adhering to security policies; vigilant reporting | First line of defense against social engineering attacks |
We do not only recognize the criticality of vulnerability management ownership, but also the necessity to ingrain a culture of accountability in security practices organization-wide. By establishing this framework, we lay a solid foundation to successfully manage and neutralize the risks that vulnerabilities pose to our enterprise.
Step 1: Asset discovery - the foundation of effective vulnerability management
One of the most critical steps of vulnerability management lifecicle is the asset discovery process. Why is it so vital? Well, it's relatively straightforward: before we can protect our assets, we must first know precisely what they are, where they are located, and the role they play in our network ecosystem. It's the comprehensible blueprint that ensures every aspect of our network inventory is accounted for — setting the stage for effective vulnerability management.
A multi-faceted approach to asset discovery should be employed, integrating various techniques and state-of-the-art tools that aid in maintaining an updated and accurate repository of our hardware and software assets. Let's explore the key elements that constitute a thorough asset discovery process.
1.Network Scanning: Systematic scan of network to detect any connected devices. This scan helps to uncover the inventory of assets that make up our operational infrastructure.
For those involved in the technical aspects of asset discovery, a basic network scanning tool can be invaluable. Below is a simple Python script utilizing the Nmap library, a popular network discovery tool. This script scans a network range to identify active hosts, which is a fundamental step in asset discovery:
# Python script for basic network asset discovery
import nmap
# Initialize the scanner
nm = nmap.PortScanner()
# Scan a range of IPs for active hosts
nm.scan(hosts='192.168.1.0/24', arguments='-sn')
# List discovered hosts
print("Discovered hosts:")
for host in nm.all_hosts():
print(f'Host : {host} ({nm[host].hostname()})')
print(f'State : {nm[host].state()}')
2.Software Enumeration: Software solutions fleetingly change and update. Through enumeration, we catalog all the applications, ensuring we keep pace with the latest versions and configurations.
According to Gartner's latest study, it is predicted that by 2027, 75% of employees will acquire, modify, or create technology outside of IT's visibility, further escalating this issue.
When cataloging all the applications, you shouldn't forget about APIs. Traditional API security solutions rely on observing real API traffic to detect and monitor APIs. This process happens through the deployment of an agent or the integration with API Gateways and proxies.
Shadow APIs, since they are deployed outside of the organization’s API Gateways and proxies, often go undetected, creating blind spots. Well-meaning developers may create them to speed up their work, or they could be remnants from previous software versions. This is where tools like Escape can be extremely vital for your organization. The agentless technology developed by Escape gives you complete visibility into APIs exposed by your organization within minutes.
3.Device Tracking: As devices connect and disconnect from the network, it's crucial to track these movements to understand our current defensive posture at any given time.
Once you've finalized your inventory, it's time to scan all your networks, applications, and systems to detect underlying vulnerabilities. The best approach is to conduct continuous and automated discovery and assessment.
Depending on the asset that you need to scan, you might use
- Network vulnerability scanners that dissect network services, configurations, and potential entry-points for threats.
- Wireless Scanners that assess security vulnerabilities in wireless networks, including Wi-Fi routers and access points.
- Application security scanners that specifically target applications, detecting security flaws like SQL injection and cross-site scripting vulnerabilities.
Keep in mind that these are just a couple of examples of potential vulnerability scanner types you might need for your organization. No two organizations are the same. You can find the complete list of vulnerability scanners on the OWASP website.
These automated systems can be complemented by penetration testing, where real human simulates cyber attacks on organization's defenses to examine how they would hold up during a real breach. You can learn further about different types of penetration testing in this article. And if you have any GraphQL-based applications in your arsenal, check out our series of articles on pentesting GraphQL.
Once an assessment has been completed and you've built a full inventory of all your assets and their vulnerabilities, the next stage is prioritizing vulnerabilities.
Step 2: Assessing vulnerability severity and impact
Like the traditional stance on vulnerability management is usually, do you see all of your assets? Do you know the number of all of your assets that you have? And based on that, do you see the number of your vulnerabilities? So focus on, can you actually see everything that you have? And then can you actually scan everything that you have? And then once you get to the point of like, okay, you know, we have everything, we scan everything. Now we have the problem of, you know, we have 10,000 plus criticals, 100,000 plus highs and bajillion medium and lows. That's where you start to think about maybe we need to prioritize some areas and not so much others. And that's where the security engineers have to step in place: how does our business work? And this is what I think is crucial for security engineers to kind of step away a little bit from engineering and look into the business. - Aleksandr Krasnov, the principal security engineer at Meta
Assign value, judge severity and impact
It's not just about finding vulnerabilities; it's about evaluating their potential impact.
You need to evaluate each vulnerability against multiple criteria:
- The potential impact on business continuity and data integrity
- The likelihood of the vulnerability being exploited
- The significance of the affected system to our daily operations
- The legal and compliance ramifications of a security incident stemming from the vulnerability
This is where assessment frameworks, such as the Common Vulnerability Scoring System (CVSS). By assigning a severity ranking, from 0 to 10, vulnerabilities are categorized based on the risk and urgency they pose to your network.
In addition to CVSS framework, you can consult OWASP's TOP 10 list of vulnerabilities where each main vulnerability is listed and judged by 3 main criteria: exploitability, detectability, and impact type.
But beware, try to think beyond the common instructions. For CISOs and security engineers, understanding the business logic is essential in prioritizing vulnerabilities. So when evaluating your vulnerabilities either spend some time to truly dig into understanding your business or make sure you use tools like Escape which are trained on AI to understand the business logic of applications to find, fix, and help you prioritize.
Vulnerabilities are always evolving. The recent addition of critical vulnerabilities to CISA's Known Exploited Vulnerabilities Catalog, including CVE-2023-6345 and CVE-2023-49103, highlights the critical need for continuous monitoring. Understanding your business is paramount for making informed judgments and prioritizing effectively and promptly.
Informed assessments ensure that prioritization aligns with your organization's unique operational context and risk tolerance, enhancing the effectiveness and strategic value of vulnerability management. This approach provides a clear perspective on where to direct your remediation efforts for maximum impact.
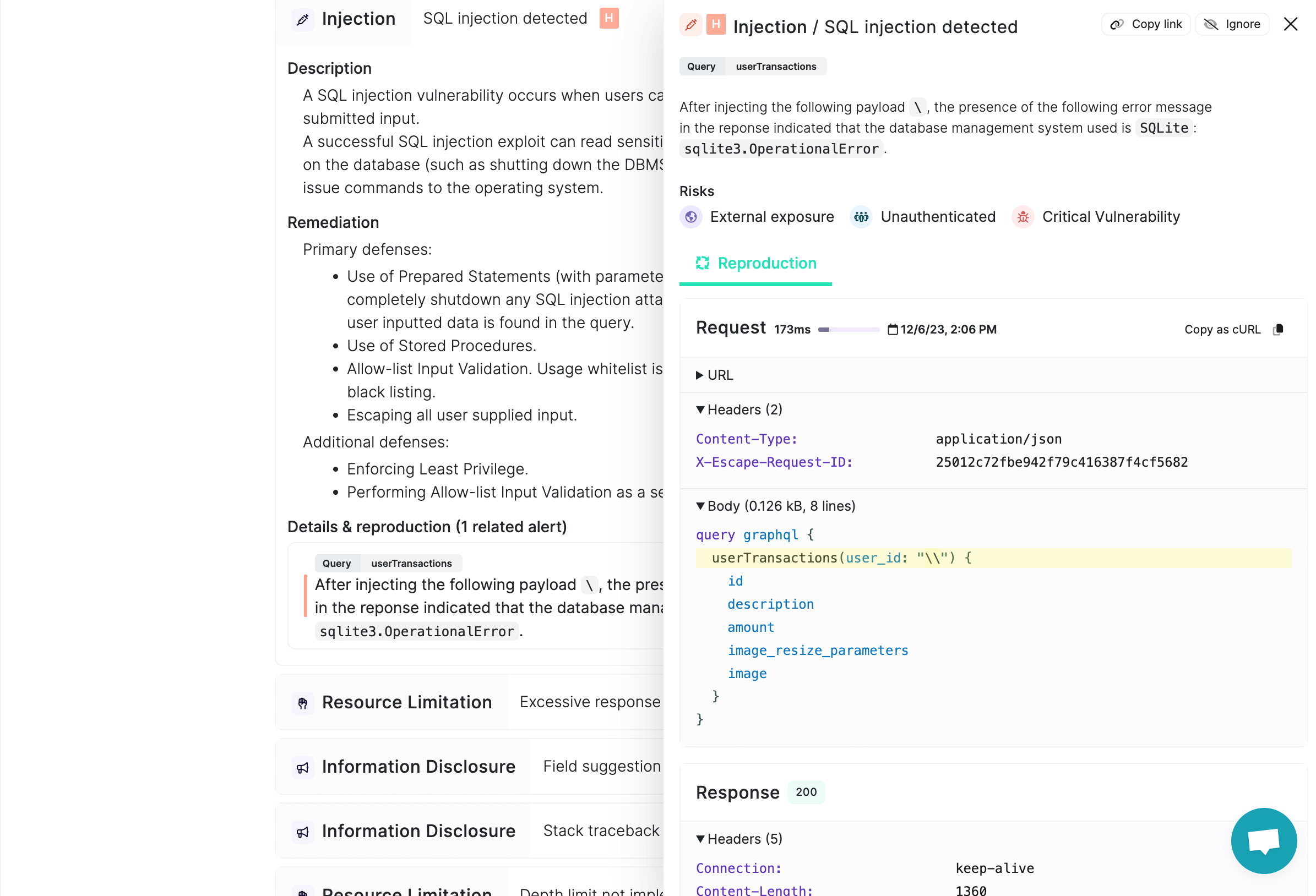
Step 3: Remediation strategies to mitigate identified vulnerabilities
We know that identification is only part of the battle; effective remediation is where vulnerabilities are no longer the organization's weaknesses.
Depending on the impact, an ease of exploitability and threat of exposure of each vulnerability you can choose one of the following moves:
- Embrace the risk: if the vulnerable asset isn't mission-critical and the exposure threat is minimal, you might opt to roll the dice and accept the risk.
- Mitigate the vulnerability: Rather than eliminating the vulnerabilities, you can strategically make it difficult to impossible for an attacker to exploit them. It's not a fix-all, but robust policies and protections can create a good defense for your systems. For example, you can implement strict access controls to limit threats to the most critical functionality or employ intrusion detection systems for early warnings of unusual activities.
- Full-on remediation: You can completely remediate the vulnerability. This is the preferred option if the vulnerability is known to be high risk and/or is part of a critical system or asset in your organization. Patch or upgrade the asset before it becomes an entry point for an attack.
When approaching vulnerability remediation for your applications, make sure that you choose tools that can provide your development team with actionable fixes, tailored to your specific backend framework, and not only a basic description of the vulnerabilities. The faster you get your team on board to fix all threats, the less will be a security risk for your organization.
More than that, make sure your software is always up to date with the latest versions where potential vulnerabilities may have already been addressed by their providers.
People delay enhancements because they are unaware that they resolve security issues. Malware and other hazards can penetrate vulnerabilities that are not addressed. Installing updates promptly may prevent vendor-resolved software issues. Regular updates enhance the user experience and system security by enhancing system functionality and performance. Whenever possible, configure software to update automatically to avoid delays. - Andre Slonopas, Cybersecurity Department Chair at American Public University System
Step 4: Validation and monitoring
After you've sorted your vulnerabilities and laid out action plans based on exposure levels, the next crucial step is to double-check your work. Reassessing your strategy lets you gauge the effectiveness of your actions and spot any new concerns related to the same assets. This step isn't just about ticking off resolved issues; it’s also about discovering and addressing new ones as needed. Plus, this reassessment phase is a great opportunity to compile and present the progress and impact of your team’s efforts to the upper management, highlighting the value of your cybersecurity efforts.
The significance of continuous monitoring in vulnerability management
We understand that to remain one step ahead, continuous monitoring is a must. Continuous monitoring acts as the backbone of an effective vulnerability management strategy. It involves regular scanning and analysis to detect new vulnerabilities, assess the effectiveness of implemented security measures, and identify any changes that could introduce risks. This proactive approach not only helps in the early detection of potential threats but also ensures that your security posture is always aligned with the current threat environment. Here are 4 potential monitoring tools you can use:
| Monitoring Tool | Function | Contribution to Security |
|---|---|---|
| Security Information and Event Management (SIEM) | Real-time visibility across the IT landscape | Centralizes monitoring and alerts for faster response |
| Intrusion Detection Systems (IDS) | Inspects incoming traffic for patterns of attack | Identifies potential external threats quickly |
| User and Entity Behavior Analytics (UEBA) | Profiles standard user conduct to spot deviations | Detects potential inside threats from atypical behavior |
| Vulnerability Scanners | Scans systems for known weaknesses | Helps prioritize remediation efforts by highlighting critical vulnerabilities |
One of the possibilities to ensure continuous monitoring of your applications is to integrate dynamic vulnerability scanners in your CI/CD process. Vulnerabilities will be detected automatically and early in the development before they even reach production.
Continuous monitoring offers invaluable insights for strategic decision-making in cybersecurity. By constantly evaluating the security status of your network, you can adapt your vulnerability management tactics to address emerging threats more effectively. This not only enhances your ability to prevent security breaches but also ensures compliance with evolving regulatory standards.
Step 5: Reporting and improvement
This is the final stage of the vulnerability management cycle. The best vulnerability management programs follow the principle of consistent improvement. Consistently strive to enhance your existing processes and SLAs, ensuring you demonstrate value by establishing accurate metrics to monitor the impact of your ongoing security efforts. By taking a hard, regular look at your entire vulnerability management process and seeking ways to refine and advance it, you place yourself in a proactive stance.
Best practices for enhancing your vulnerability management lifecycle
To improve your cybersecurity defenses, we recognize the importance of following best practices throughout our vulnerability management lifecycle. These practices are not just recommendations; they are vital to the effective protection of your data. Let’s explore some key strategies that, when adopted, minimize your risk profile and reinforce your security posture.
Continuously discover and test all your applications
A key best practice in enhancing your vulnerability management lifecycle is the continuous discovery and testing of all your applications. This ongoing process involves not just a one-time identification but a persistent effort to uncover and scrutinize every application used in your organization.
Regular testing ensures that any newly introduced or previously overlooked vulnerabilities are promptly identified. This approach not only helps in keeping your application security up-to-date with the latest threat intelligence but also aligns with a proactive defense strategy, reducing the window of opportunity for attackers to exploit any weaknesses in your systems.
Implementing a policy of least privilege
The least privilege policy security principle dictates that users are granted the minimum levels of access—or permissions—needed to perform their job functions. Through meticulous access controls and privilege management, you can effectively lower the risk of insider threats and minimize the potential impact of breaches.
- Inventory access points: Begin with identifying all access points within systems and applications.
- Assess user roles: Determine the needs of each user group, ensuring the right level of access is aligned with job responsibilities.
- Implement access limits: Set up access controls that reflect the principle of least privilege across our digital environment.
- Regular audits: Conduct periodic reviews to ensure privileges remain appropriate and modify as necessary.
Ensuring compliance with industry standards
Aligning your practices with established cybersecurity compliance standards is not only a proactive measure against threats but also a legal and ethical mandate. Through adherence to robust security and regulatory frameworks, you can avoid penalties and foster trust among stakeholders and customers alike.
Below, you can find information on some compliance frameworks that your organization might need to adhere to strictly:
| Standard/Framework | Purpose | Benefits |
|---|---|---|
| ISO/IEC 27001 | Establishing, maintaining, and continually improving an information security management system (ISMS) | Global recognition for best-practice information security approaches |
| PCI DSS | Protecting cardholder data for all types of card payments | Essential for entities that handle credit card transactions |
| NIST Cybersecurity Framework | Providing a policy framework of computer security guidance for organizations | Enables comprehensive risk management strategies |
| GDPR | Regulating data protection and privacy for individuals within the European Union and the European Economic Area | Ensuring strong data protection standards internationally |
Regularly update and educate your team
An informed team is our first line of defense against cyber threats. All internal teams require ongoing security training and cybersecurity awareness. By promoting a culture of knowledge and vigilance, your team becomes proactive participants in your security ecosystem.
You can implement one of the following practices:
- Monthly security updates: Provide written updates on new threats and security trends.
- Quarterly workshops: Organize interactive training sessions to engage and test your team's response to simulated security incidents.
- Annual security training: Mandate comprehensive security training refreshers to stay updated on the latest cybersecurity developments.
Conclusion
An effective vulnerability management lifecycle is not just a summary of tactics; it's a call to action. Evolving beyond mere compliance, we understand that the goal is a resilient, proactive defense mechanism—a thriving organism capable of adapting to and repelling sophisticated cyber attacks. Organizations following these principles will not only navigate the challenges of the digital world successfully but also become leaders in cybersecurity.
Take a moment to think about how you can tailor these best practices to refine your organization’s security strategy. Remember, the only constant in cybersecurity is change.
💡 Want to learn more? Discover the following articles:
