Top Vulnerability Scanning tools 2025

In 2025, vulnerability scanning tools are essential for modern security teams, but running a scan is rarely the hard part anymore. The real challenge is automating it at scale: across thousands of assets, spanning APIs, web applications, and cloud services, in environments that can change by the hour.
Security engineers are voicing this exact frustration. You can find it in multiple Reddit threads, like the one below,
where a user asked how others automate vulnerability management in their org - from scanning to remediation. The replies make it clear: automation isn’t solved yet, and teams are still figuring out how to keep up.
One rushed deployment, a misconfigured endpoint, or an overlooked microservice or API can silently expand the attack surface.
In this guide, we focus on application and API scanners, the kind used by AppSec engineers, DevSecOps teams, and security leads to find real, exploitable flaws in production-like environments.
The best scanners don’t just give you a backlog of vulnerabilities. They pinpoint what’s exposed, unauthenticated, and truly exploitable - then provide the technical context needed to act fast. At scale, that means mapping complex applications, tracking new assets in real time, integrating with CI/CD pipelines, and delivering results that security engineers can triage quickly and pass to developers with clear, actionable remediation guidance.
For most large-scale organizations, you scan more than just one app per month. Engineering pushes updates daily across multiple domains, and often AppSec teams need continuous, context-driven detection that keeps pace with engineering velocity - without leaving blind spots or overwhelming the teams responsible for fixing what matters most.
The Modern Vulnerability Scanning Tools: Checklist That Actually Matters
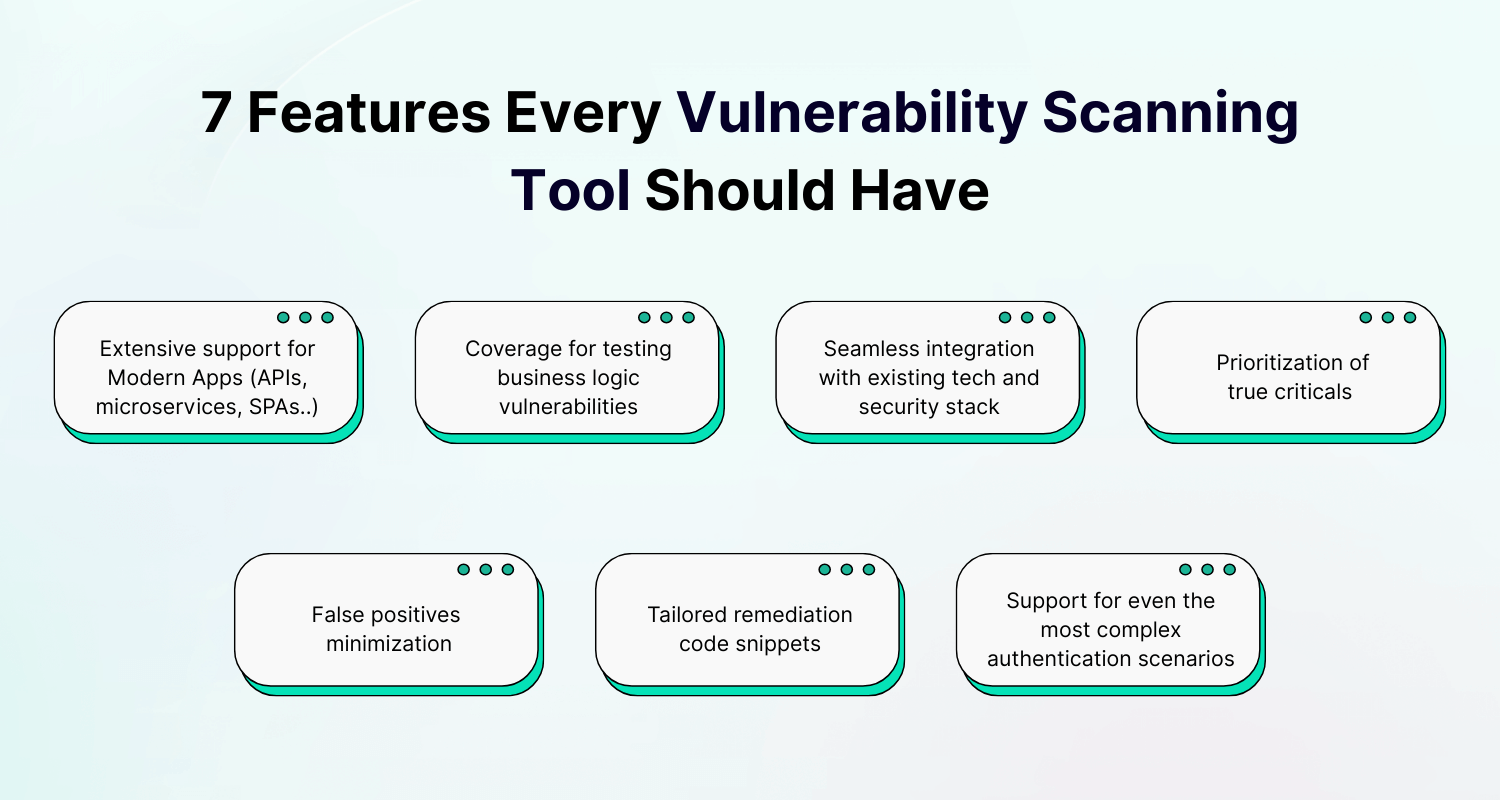
Not all vulnerability scanning tools are built for the realities of today’s software environments. Modern AppSec teams work in fast-moving pipelines, deal with API-first architectures, and secure applications that may only exist for hours before being replaced. Most of the legacy scanners will either miss critical flaws or flood your backlog with false positives. The modern scanner should meet these requirements:
1. Extensive Coverage for Modern Applications
Goes beyond traditional web apps to test APIs (REST, GraphQL), SPAs, and microservices. Without deep API coverage and SPA crawling, huge parts of your attack surface stay invisible.
2. Advanced Business Logic Testing
Business logic flaws are some of the hardest vulnerabilities to uncover. The best scanners rely on adaptive algorithms, powered by AI, that mimic user behavior - enabling deep logic testing with little to no human in the loop.
3. Accurate, Relevant Findings
High-confidence results with minimal false positives. Quality scanners focus on vulnerabilities that are actually truly critical and exploitable, so engineers trust the alerts and act fast.
4. Seamless Integration With Tech & Security Stack & Automation
Scanning should integrate seamlessly into existing developer workflows (GitHub or GitLab CI...) and help to surface triaged findings directly in ticketing systems like Jira. At the same time, it should provide robust API access and scalable automation to run continuously without slowing down releases.
5. Prioritization That Cuts the Noise
You can't secure everything at once. To help you prioritize criticals, well-executed scanner groups issues by root cause and filters out low-risk items through the prioritization dashboard. Once implemented, you'll see the impact on MTTR.
6. Actionable Remediation
Provides framework-specific code snippets or config changes so developers can patch immediately, not go hunting for fixes.
7. Realistic Authentication Support
Handles multiple authentication flows and methods: TOTP MFA, CAPTCHA, token-based logins, multiple users, and reauthentication to simulate real user (or attacker) behaviour.
Top 5 vulnerability scanning tools at glance
10 Vulnerability Scanning Tools Worth Evaluating in 2025
With so many tools available, the challenge isn’t finding a scanner, it’s finding one that actually fits your team’s maturity, tech stack, and scale.
Escape
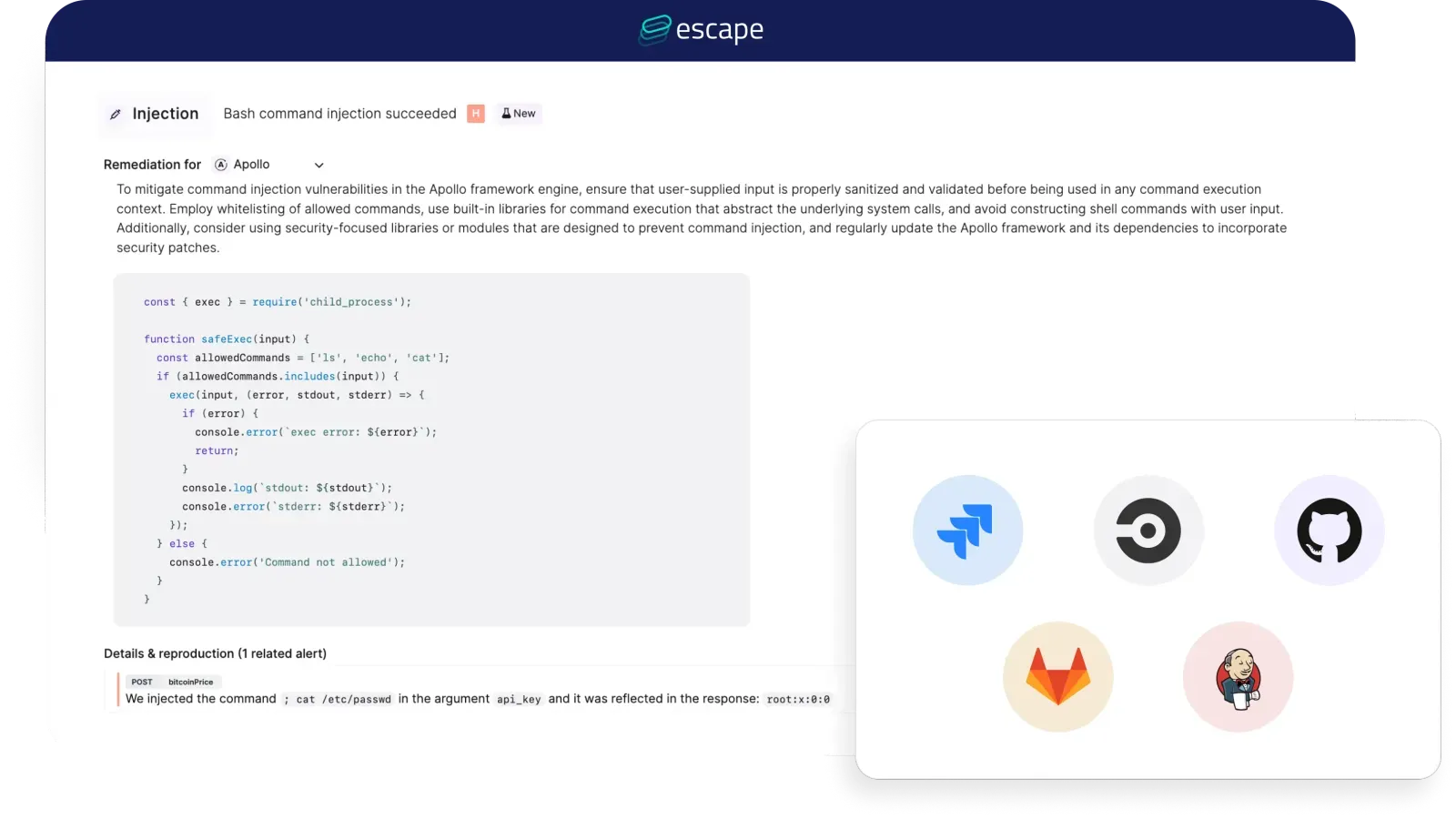
Escape is built for lean Application Security (AppSec) teams working in fast-moving, engineering-driven organizations. When developers ship new apps and features daily, the attack surface changes constantly, and Escape’s adaptive engine is designed to test them with the depth and precision of modern business-logic security.
Traditional vulnerability scanners rely on static testing patterns, flagging everything they find and leaving security teams to understand what is actually critical for their business. Escape separates the problem into two layers: agentless API and web app discovery to ensure complete coverage, and an agentic testing engine that adapts its path based on what it uncovers - similar to how a skilled tester would probe business logic. This combination removes much of the repetitive recon and mapping work, freeing human experts to focus on complex, novel attack scenarios.
The result is more than detection. Escape identifies and prioritizes exploitable vulnerabilities, especially in business logic and API-specific flaws, then delivers framework-specific remediation snippets that developers can use immediately. This reduces mean time to remediate (MTTR) and keeps security and engineering in sync.
Key Features:
- Agentic DAST → Goes beyond payload spraying by adapting tests dynamically across modern applications (APIs, SPAs, microservices) to uncover business logic flaws and sensitive data exposure
- Faster Vulnerability Discovery → What used to take pentesters days to find in newly deployed applications can now be surfaced in hours, enabling earlier remediation at scale.
- Real-World Authentication Handling → Supports complex authentication flows, MFA, text-based CAPTCHA and others authentication scenarios for easily scalable testing.
- Remediation-Focused Workflow → Provides actionable, framework-specific code fixes to speed resolution.
- Seamless CI/CD & Issue Tracking → Easy integration with major CI/CD tools (GitHub Actions, GitLab, Jenkins, CircleCI, Bitbucket, Azure DevOps) via CLI & API, plus Jira integration for streamlined issue tracking.
- Escape + Wiz Integration → Extends Escape’s agentic app-layer testing with Wiz’s cloud context, allowing joint customers to correlate risks, assign ownership instantly, and accelerate remediation with a unified view.
Pros:
✅ Purpose-built for modern applications (APIs, SPAs, microservices) with Advance business logic detection
✅ Agentic scanning replaces time-intensive manual pentests - accelerating coverage and reducing cost
✅ Validated findings with clear exploits and minimal false positives.
✅ Handles complex authentication flows without breaking automation
✅ Seamless CI/CD integration for continuous testing
Cons:
⚠️ Advanced features may require security expertise to configure and interpret optimally
⚠️ Integration coverage is narrower for some operational tools
Customer Review
Positive
”Escape shines … coming up with thousands, if not several thousands of unique test cases to put forth against your application endpoints, and be able to get wider coverage and visibility.” - Seth Kirschner, DoubleVerify
Negative
The updates to the platform, while ensuring we always have access to the latest features and security enhancements, can sometimes require a bit of adjustment on our part. Nevertheless, the benefits of the tool far outweigh this minor inconvenience, and we look forward to seeing how the platform evolves.
Burp Suite DAST
Burp Suite DAST (formerly Burp Suite Enterprise) is one of the most widely recognized vulnerability scanning tools in the security community, valued for its deep customization and hybrid approach to testing. It combines automated scanning with its DAST with powerful manual testing capabilities, making it a strong choice for experienced security professionals who need precision and control.
Unlike lightweight scanners that aim for fast, hands-off results, Burp allows AppSec engineers and pentesters to directly manipulate requests, customize payloads, and chain exploits ideal for identifying vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) in dynamic web environments. The trade-off is that it demands significant expertise to use effectively, and it’s not designed for fully automated testing for complex vulnerabilities in CI/CD - you need a lot of tweaking to get the results out of the tool.
Key Features:
- Customizable Workflows → Fine-tune scans and payloads for application-specific testing.
- Extensible Plugin System → Supports free and premium extensions for enhanced detection and reporting.
- Advanced Authentication Support → Handles Basic Auth, JWT, session cookies, and recorded login workflows.
- In addition to automated testing, it provides manual testing toolkit → Includes Intruder, Repeater, and Sequencer for in-depth, hands-on security testing.
- Performs automated DAST scans to detect common web vulnerabilities like SQL injection, XSS, and CSRF.
Pros:
✅ Highly customizable for advanced security practitioners
✅ Supports a broad range of authentication workflows
✅ Strong community and plugin ecosystem for extended capabilities
Cons:
⚠️ Requires manual testing expertise to unlock full potential
⚠️ No native support for automated GraphQL or modern API scanning
⚠️ Limited detection of business logic vulnerabilities
⚠️ Can be resource-intensive during large-scale scans
Customer Review
Positive
Negative
ZAP ( by Checkmarx )
ZAP (Zed Attack Proxy) is the world’s most widely used open-source vulnerability scanning tool, trusted by both newcomers to security testing and seasoned penetration testers. Its API-first design and zero licensing cost make it an attractive option for DevOps and AppSec teams who want to integrate dynamic application security testing (DAST) tools into their CI/CD pipelines without incurring commercial tool expenses.
ZAP can run headless in a Docker container for continuous security testing, triggering scans with every deployment. Its extensibility through the ZAP Marketplace allows teams to add custom rules, integrations, and specialized capabilities. However, while ZAP is powerful for smaller environments or teams with strong in-house expertise, it lacks the scalability, modern API specialization, and advanced automation features required for complex enterprise environments. Out-of-the-box scans can also be noisy, requiring manual tuning to avoid false positives.
Key Features:
- Powerful API & Automation → Fully API-driven for DevSecOps workflows and CI/CD integration.
- ZAP Marketplace → Large library of extensions for rules, integrations, and custom scans.
- Multiple Modes → Safe (non-destructive) and Attack (aggressive) modes for flexible testing.
- Active & Passive Scanning → Supports non-intrusive checks and deeper vulnerability detection (e.g., SQL injection, XSS).
Pros:
✅ Free and open-source with no licensing costs
✅ API-driven for seamless automation in CI/CD
✅ Highly extensible through a large community of add-ons
Cons:
⚠️ Requires significant time and expertise to tune and automate effectively
⚠️ Noisy default scans can lead to false positives
⚠️ Limited specialization for modern APIs like GraphQL compared to dedicated API security tools
Customer Review
Positive
Negative
Nuclei
Nuclei, developed by ProjectDiscovery, is a high-performance open-source vulnerability scanning tool designed for automation and rapid detection. Its template-based scanning engine allows security teams to quickly identify vulnerabilities, misconfigurations, and exposed services across large target sets making it a favorite for attack surface assessments and incident response.
Built in Go, Nuclei supports high-concurrency scanning, making it exceptionally fast for reconnaissance at scale. Its strength lies in its community-driven template library, which is regularly updated by security researchers to cover new CVEs, misconfigurations, and takeover risks. However, Nuclei has no graphical user interface (GUI), built-in reporting, or remediation tracking. This means results require manual triage, and noise can be an issue if templates aren’t targeted carefully.
Best suited for technical teams comfortable with CLI tools and customization, Nuclei works seamlessly with other ProjectDiscovery utilities like subfinder and httpx, enabling end-to-end reconnaissance pipelines.
Key Features:
- Community-Powered Templates → Large library of YAML templates for vulnerabilities, misconfigurations, and exposure detection.
- High-Concurrency Scanning → Written in Go for parallel execution across large targets.
- Workflow Integration → Works with CLI tools like subfinder and httpx for reconnaissance and scanning pipelines.
- Custom Template Support → Create organization-specific templates for internal or emerging threats.
Pros:
✅ Extremely fast scanning, ideal for reconnaissance and enumeration
✅ Continuously updated community-driven templates
✅ Highly customizable for command-line automation and scripting
Cons:
⚠️ No GUI, reporting, or remediation tracking
⚠️ Requires manual triage and prioritization of findings
⚠️ Can generate noise if templates are not carefully selected
Customer Review
Positive
Negative
Snyk
Snyk, widely recognized for its developer-first SCA (Software Composition Analysis) and SAST (Static Application Security Testing) tools, expanded into DAST testing in late 2024 by acquiring Probely. This led to Snyk API & Web, adding basic DAST functionality to the broader Snyk ecosystem.
The DAST module is designed for fast setup and works well for scanning publicly accessible web applications, integrating directly into developer workflows like IDEs, pull requests, and CI pipelines. However, compared to dedicated API-native scanners, its scope is limited when it comes to API testing with its DAST, there’s no automated API discovery, no business logic testing, and API scans require manual specification uploads. It also cannot test internal or VPN-restricted assets, making it less suitable for complex enterprise environments.
For teams already embedded in Snyk’s platform, this integration offers convenience and unified reporting across SAST, SCA, IaC, and container scanning. For organizations prioritizing deep API and business logic coverage, it may need to be paired with a more specialized DAST solution.
Key Features:
- Part of the Snyk Ecosystem → Integrates with Snyk’s broader developer security tools.
- Lightweight DevSecOps Integration → Connects to CI/CD and ticketing tools for vulnerability tracking.
- Manual API Scan Setup → Requires manual upload of API specifications; no automated schema generation.
- Basic External Asset Discovery → Identifies exposed domains via AWS Route 53 and Cloudflare, without deep code-based or internal discovery.
- Automated Basic Web Vulnerability Scanning → Detects common flaws like XSS, SQL injection, and misconfigurations.
Pros:
✅ Simple setup for public-facing web app scans
✅ Strong IDE, PR, and CI/CD integrations for developer adoption
✅ Unified reporting across Snyk’s full security platform
Cons:
⚠️ No native API discovery or business logic testing
⚠️ Requires manual API uploads for scanning
⚠️ Cannot test internal or restricted-network assets
⚠️ Remediation lacks framework-specific code snippets
Customer Review
Positive
Negative
Too much unnecessary false positives, policy overrides, hard and complex to manage and track alerts
Invicti
Invicti (formerly Netsparker DAST) is an enterprise-grade vulnerability scanning tool built for large organizations that need reliable, automated testing across extensive web application portfolios. It excels at detecting well-known vulnerability classes such as SQL injection, cross-site scripting (XSS), and common misconfigurations, across many sites with consistent accuracy.
Invicti’s Proof-Based Scanning™ feature helps reduce false positives by safely validating certain vulnerabilities with proof-of-exploit evidence. While useful, similar validation methods are available in other enterprise tools, and it doesn’t eliminate all noise.
Its scanning engine handles well-documented REST APIs and traditional web apps effectively, but struggles with undocumented or shadow APIs. Automated API discovery is limited, and broader network-based discovery requires additional manual configuration, such as deploying traffic analyzers. API testing depends heavily on existing specifications or integrations with API management tools, making it less flexible for fast-changing, undocumented environments.
Key Features:
- DAST with Optional IAST → Combines dynamic and interactive testing for improved accuracy and code-level insight.
- Validated Vulnerability Reporting → Proof-of-exploit confirmation for certain issues to improve triage confidence.
- Enterprise Asset Management → Large-scale scan scheduling, role-based access control (RBAC), and compliance reporting.
- Broad Protocol Support → Tests REST, SOAP, and limited GraphQL APIs alongside traditional web applications.
Pros:
✅ Reliable detection of common web vulnerabilities at enterprise scale
✅ Supports REST, SOAP, and limited GraphQL API testing
✅ Detailed reports with optional code-level context
✅ Integrates with CI/CD pipelines, issue trackers, and WAFs
Cons:
⚠️ Limited GraphQL coverage and no advanced business logic testing
⚠️ No automated API specification generation
⚠️ Relies heavily on existing documentation for API testing and discovery
⚠️ Higher cost of entry compared to smaller-scale DAST tools
Customer Review
Positive
Negative
Not much helpful for scanning API endpoints.
No proper support for 2FA or MFA web applications
Intruder
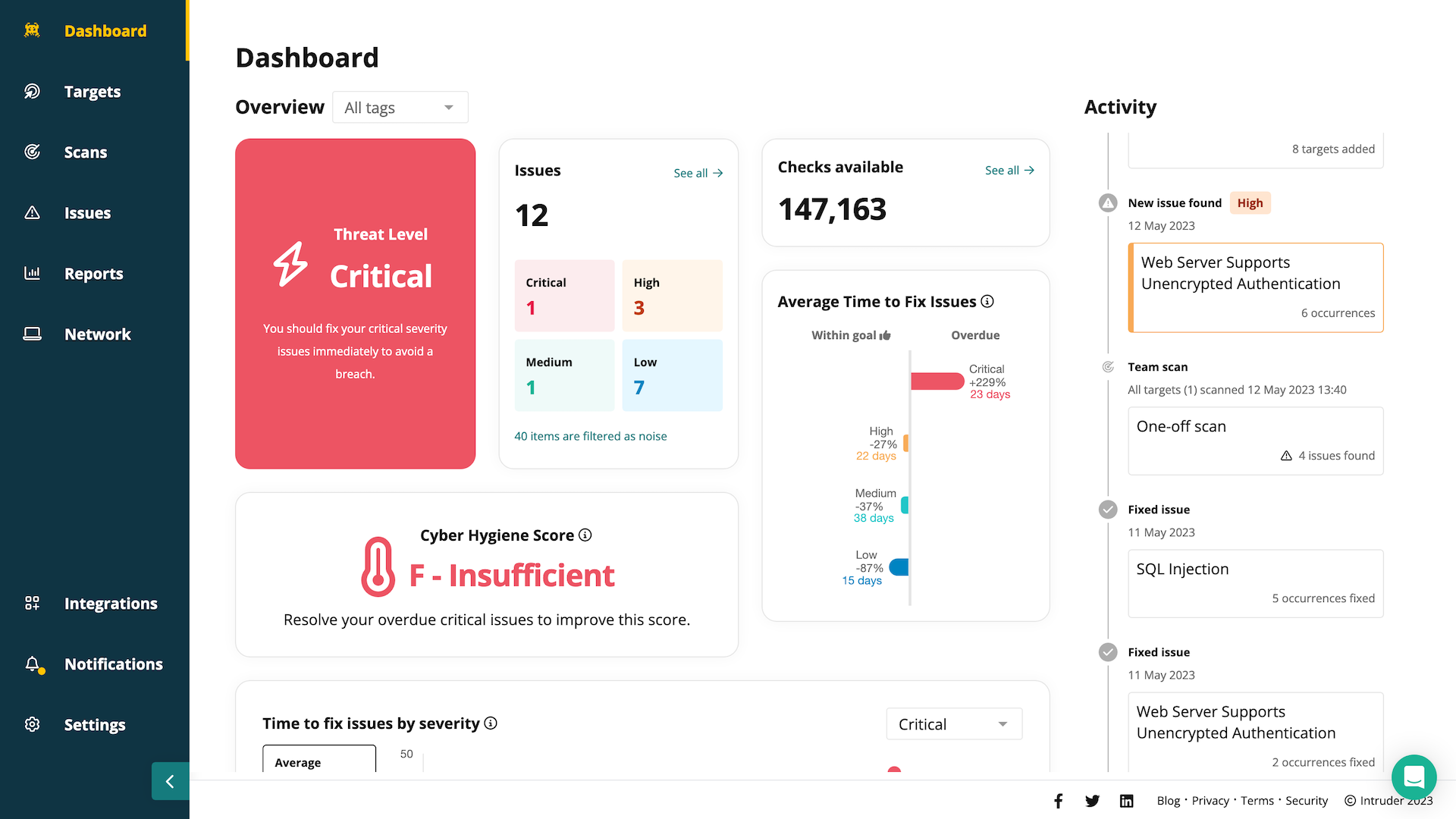
Intruder is a vulnerability management platform built for SMBs, startups, and lean technical teams that need strong security coverage without hiring a dedicated AppSec function. It’s often adopted by Heads of Engineering, DevOps leads, and IT managers who want a single platform for tracking vulnerabilities, monitoring attack surfaces, and preparing for compliance audits.
Rather than building its own scanning engine, Intruder integrates ZAP for web application scanning and OpenVAS for infrastructure scanning. This gives it broad detection coverage but also means it inherits some of the noise and false positives associated with those tools. Where Intruder stands out is in simplifying security for non-specialist, automating scans, consolidating reports, and surfacing clear priorities for remediation.
Key Features:
- Continuous Attack Surface Monitoring → Automatically detects new or changed assets (e.g., new services or domains) and triggers scans.
- Cyber Hygiene Score → Tracks security posture over time for compliance frameworks like ISO 27001, SOC 2, and Cyber Essentials.
- SMB-Friendly Integrations → Works with AWS, Azure, Google Cloud, Jira, GitHub, GitLab, and Cloudflare.
- Proactive Threat Checks → Runs targeted scans when new vulnerabilities are disclosed.
Pros
✅ Easy to deploy and manage, even without dedicated security staff
✅ Combines web and infrastructure scanning in one tool
✅ Compliance-ready reports for audits and certifications
Cons
⚠️ Relies on third-party scanning engines (ZAP, OpenVAS)
⚠️ Can produce noise and false positives without tuning
⚠️ No advanced API, Kubernetes, or business logic testing
Customer Review
Positive
Negative
- Can have a number of false positives - but these can be easily tagged as noise.
- Generating reports for specific resources isn't intuitive. Additionally, updating targets requires deletion and re-adding, likely due to licensing constraints, necessitating reliance on external DNS configuration
Nmap
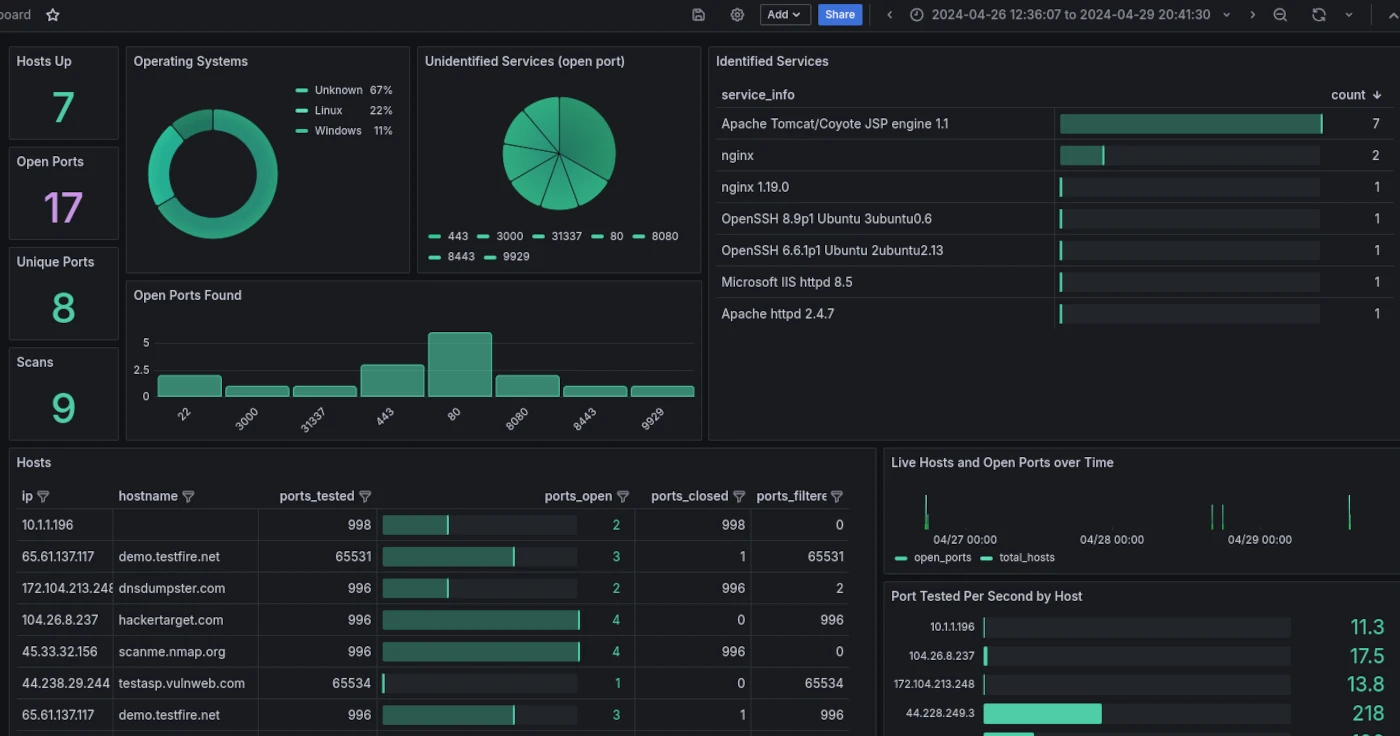
Nmap is a foundational tool in network and security assessments, widely used to map an organization’s digital perimeter before vulnerability testing begins. It’s capable of far more than basic port scans identifying live hosts, enumerating open/filtered ports, detecting running services, and fingerprinting operating systems.
The Nmap Scripting Engine (NSE) extends its capabilities with thousands of community-maintained scripts, enabling checks for specific vulnerabilities, insecure configurations, and compliance gaps. This makes Nmap a go-to for attack surface enumeration in both offensive and defensive security workflows.
While Nmap offers unmatched flexibility, it’s not a vulnerability management tool. It focuses on discovery rather than remediation, and accuracy depends heavily on the quality and maintenance of NSE scripts. Aggressive scans can be resource-intensive and easily detected by intrusion detection systems, sometimes leading to IP blocking.
Key Features:
- Comprehensive Host & Port Discovery → Identifies active hosts, open TCP/UDP ports, and firewall filtering rules.
- Service & Version Fingerprinting → Gathers detailed service banners and OS information for targeted testing.
- Extensible Scripting Engine (NSE) → Enables automation, vulnerability checks, and integration with other security tools.
Pros:
✅ Industry standard for network mapping and reconnaissance
✅ Highly flexible and extensible through NSE scripts
✅ Completely free and open-source
Cons:
⚠️ Aggressive scans can trigger security alerts or blocks
⚠️ Resource-heavy for large environments
⚠️ Focused on discovery - no built-in remediation
Customer Review(G2)
Positive
Negative
OpenVAS
OpenVAS, part of the Greenbone Vulnerability Management (GVM) framework, is one of the most established free and open-source network vulnerability scanners. It’s built for security teams with strong technical skills who can handle the configuration, tuning, and ongoing maintenance required for optimal results.
Powered by the Greenbone Community Feed a library of over 80,000 vulnerability tests updated daily, OpenVAS can identify CVEs, misconfigurations, and compliance issues across servers, endpoints, firewalls, and other networked devices.
Its biggest strength is delivering enterprise-grade detection without licensing costs, but this comes with trade-offs: setup is complex, scan speeds can lag in large environments, and results often require significant manual triage to filter false positives.
Key Features:
- Greenbone Community Feed → Continuously updated with 80K+ vulnerability tests for broad network coverage.
- Credentialed Scanning → Authenticated scans for deeper visibility into patch levels and local misconfigurations.
- Integrated Management → Part of GVM, offering scheduling, reporting, and asset management in a single interface.
Pros:
✅ Completely free and open-source
✅ Highly customizable scan configurations
✅ Comprehensive, regularly updated vulnerability database
Cons:
⚠️ Steep learning curve with complex setup
⚠️ Slower performance at enterprise scale
⚠️ Detection coverage can lag behind premium tools
Customer Review(G2)
Positive
Detectify
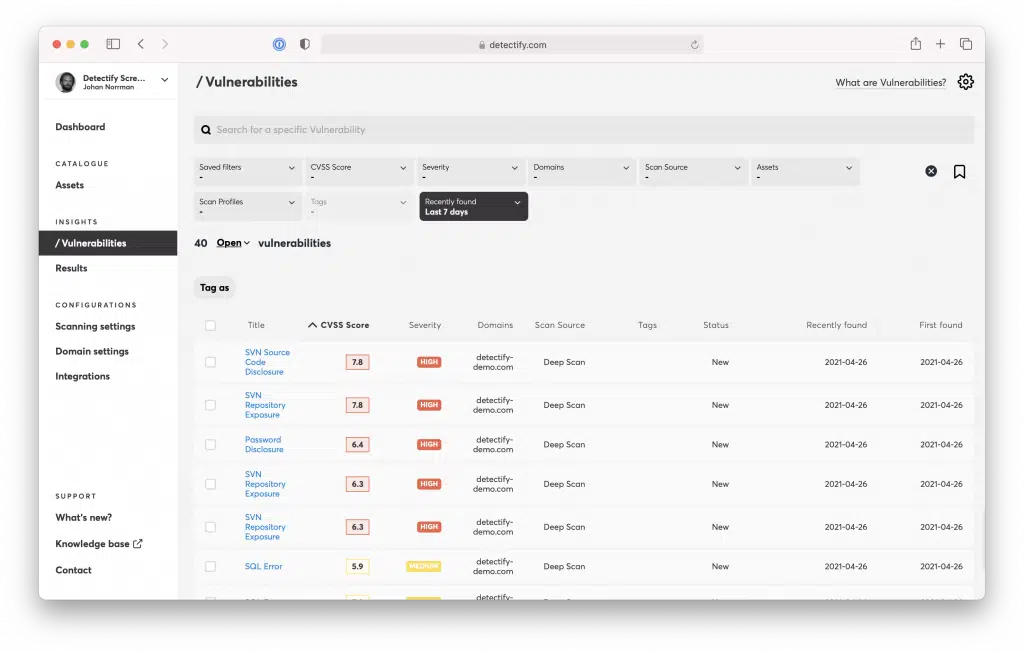
Detectify is a cloud-based vulnerability scanner designed for security teams that need continuous visibility into publicly exposed web assets. It combines surface monitoring with automated DAST scanning to detect common vulnerabilities such as SQL injection, XSS, and insecure configurations.
The platform integrates directly with major DNS providers including AWS Route 53, Azure, Cloudflare, and Google Cloud DNS to automatically discover new subdomains and exposed assets. Its scanning engine relies on fuzzing techniques to identify known issues but lacks native API, GraphQL, or complex authentication support, making it less suited for API-heavy or internal application environments.
Key Features:
- Fast, Lightweight Setup → Minimal configuration required for onboarding.
- Change Detection Alerts → Notifies when new assets appear or configurations change.
- Fuzzing-Based DAST → Finds common vulnerabilities like XSS, SQL injection, and misconfigured headers.
- Continuous Surface Monitoring → Automatic asset discovery through DNS integrations.
Pros:
✅ Quick setup for continuous external monitoring
✅ Detects widely known vulnerabilities with minimal effort
✅ Seamless DNS integration for automated asset discovery
Cons:
⚠️ No native API or GraphQL testing
⚠️ Limited authentication support
⚠️ No internal or restricted-network scanning
⚠️ Minimal remediation guidance
Customer Review
Positive
Negative
Scanning Isn’t the Endgame - Fixing Is
Running scans is easy. The real bottleneck begins after the results.
A new version ships, the pipeline runs, and hundreds of findings drop in—often from multiple tools. Many are false positives, duplicates, or too low-risk. Security teams spend hours triaging and figuring out ownership. Developers then get Jira tickets with vague details and little guidance, forcing them to dig through code to find and fix the issue.
The result?
- Security wastes time on triage instead of real risks.
- Developers waste time on unclear tickets.
- Critical issues get patched, but root causes reappear in the next release.
High-performing AppSec teams flip the process:
- Root-cause grouping → fix once, clear dozens of duplicates.
- Exploit-driven prioritization → act on issues with real attack paths.
- Developer-ready remediation → framework-specific fixes delivered straight into Jira or PRs.
This isn’t just about scanning - it’s about building a workflow that actually keeps pace with CI/CD. The outcome: fewer regressions, faster fixes, and less friction between security and engineering.
👉 Escape’s AI-powered DAST takes it further - exposing business logic flaws other tools miss, showing how they can be exploited, and delivering precise fixes that slot directly into developer workflows.
See how Escape replaces weeks of triage with actionable fixes.
💡 Want to learn more? Discover the following articles:
- 2025 Best DAST tools
- Best automated pentesting tools
- Tools for AI pentesting
- Escape Research: Escape's proprietary Business Logic Security Testing algorithm
- Escape Research: How to automate API Specifications for Continuous Security Testing (CT)
- DAST is dead, why Business Logic Security Testing takes center stage

