The Russo-Ukrainian War: How the Fight for Democracy translates into Web API Security
In Ukraine, web APIs have demonstrated their value to achieve democratic progress through e-governance. Nonetheless, API security has revealed its vital nature in light of the cyberattacks launched by Russian state-sponsored hackers.
Introduction
“Signal: Cyber prep. Since early December, there has been a dramatic increase in cyber intrusions on Ukraine government and civilian networks from Russia” warned Dmitri Alperovitch as soon as the 21st of December 2021 (1). Co-founder of CrowdStrike, the Russian-born American cybersecurity expert hence predicted Russia’s invasion of Ukraine that would unfold two months later, almost to the day.
Signal:
— Dmitri Alperovitch (@DAlperovitch) December 21, 2021
Cyber prep. Since early December, there has been a dramatic increase in cyber intrusions on Ukraine government and civilian networks from Russia
Since then, Russia has launched several cyberattacks tracked by the Cyber Peace Institute (2). Among them figure the “WhisperGate” Wiper Attacks, the Defacement of Government Websites, DDoS attacks or the “Hermetic Wiper” Malware Attack, just to mention a few. As Europeans realise that sounds of bombings on their continent are not echoes from a distant nightmare, Anonymous launched a cyber war against Russia, while Ukraine’s Volunteer IT Army and local NGOs, such as UISGCON or the Ukrainian Cyber Alliance, are mobilised to counterattack Russian state-sponsored hackers.
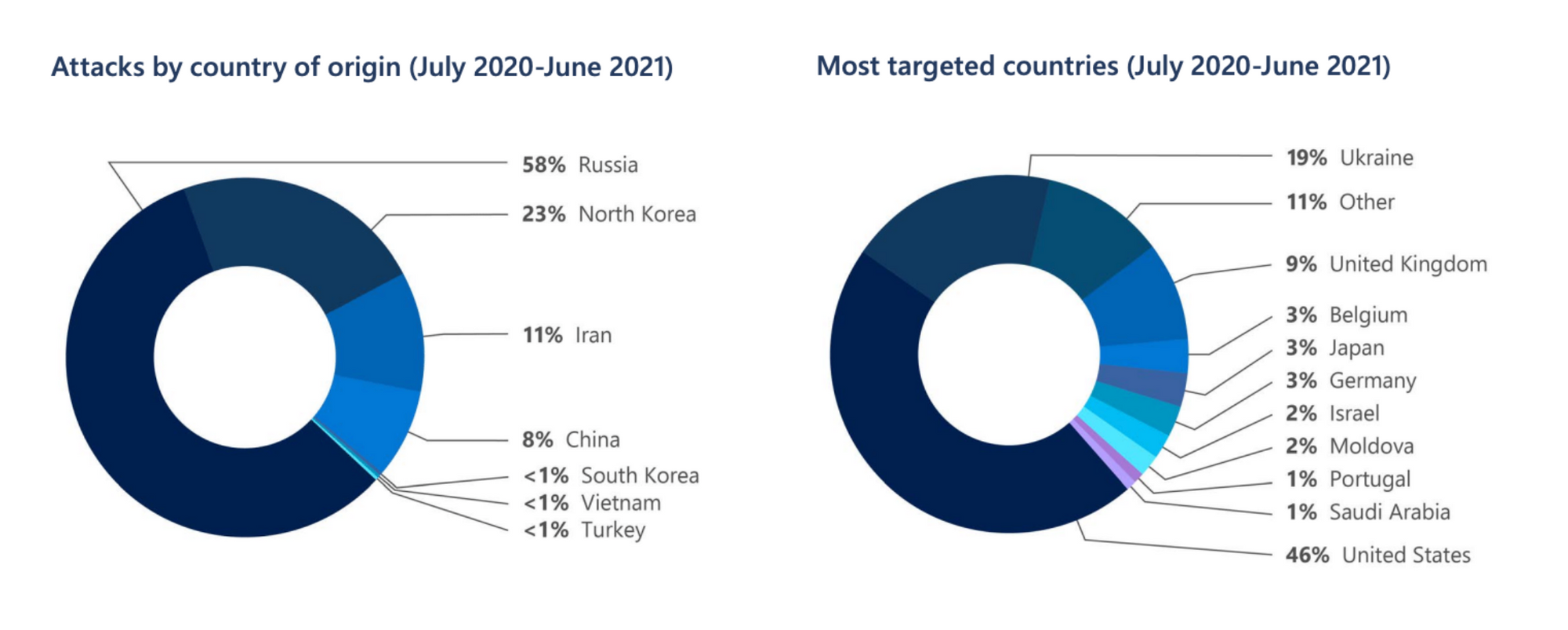
Enshrined in the 21st century, the Russo-Ukrainian War reflects the rivalries in the cyberspace. In October 2021, the Microsoft Digital Defense Report revealed that Ukraine had been the second most targeted countries by cyberattacks in the world (19%), behind the United States (46%), and in front of the United Kingdom (9%), between June 2020 and June 2021 (3). During the same time period, Russia ranked first in countries from which attacks came from (58%), far from the second runner up, North Korea (23%) (4).
Working at escape.tech, a cybersecurity company securing web application programming interfaces (API), I wondered to what extent have the vulnerabilities of web APIs fostered cyberattacks in the Russo-Ukrainian War. I discovered that web APIs have been a crucial technology for the development of an e-democracy in Ukraine in the aftermath of the 2014 Revolution of Dignity, enhancing trust between citizens and state institutions (Part I). Yet, APIs’ vulnerabilities have been exploited by Russian hacker groups to weaken Ukraine throughout the Russo-Ukrainian War (Part II). Let’s dive deeper into how the fight for democracy in Ukraine translated into web API security.
I- Central in e-governance projects, web APIs contribute to enhance democracy in Ukraine.
I.A. Prozorro, an e-procurement platform embodying Ukraine’s anti-corruption endeavors.
In 2013, the Euromaïdan grassroots movement began in Ukraine. It was spurred by the decision of Viktor Ianoukovytch, the pro-Russian president at the time, to not ratify an association agreement between the European Union and Ukraine. Filling the Maidan Square in Kyiv’s downtown, the protest gradually addressed larger issues, most notably the widespread corruption in the country. In 2014, a vicious circle of violence was set in train as protesters were killed by police forces. Euromaïdan then became the so-called Revolution of Dignity which ultimately led to the overthrow of President Ianoukovytch.
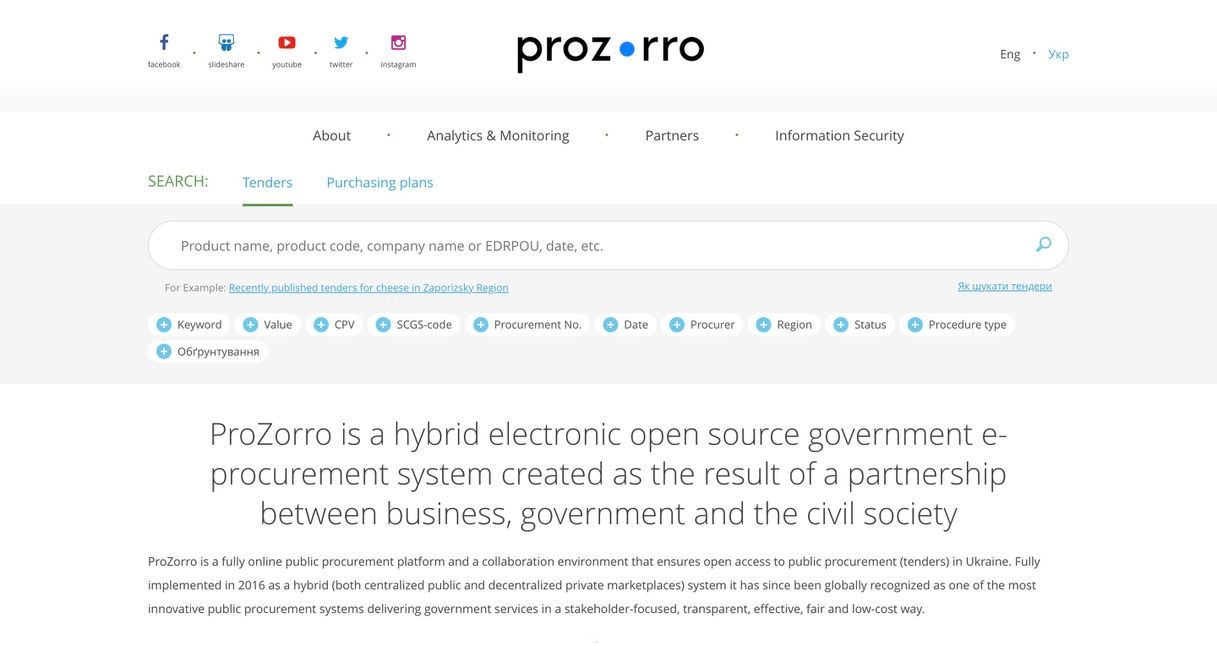
Following Ianoukovytch’s fall, Petro Poroshenko was elected president of Ukraine. His victory was achieved as a result of his anti-corruption platform, echoing the calls of Euromaïdan protesters. Nevertheless, efforts for more transparency in Ukraine’s politics were also fostered by civilian movements. For instance, Euromaïdan’s supporters were wondering how to make public procurement more transparent. Their reflection gave birth to an online platform, Prozorro, built by Ukrainian students, Poroshenko’s government and Transparency International, an anti-corruption NGO. It is now officially integrated within the Ukrainian Ministry for Development of Economy and Trade. In 2016, the Verkhovna Rada, the Ukrainian Parliament, adopted a law making the use of Prozorro compulsory for any transaction between the State and private entities.
I.B. Web API, a crucial technology for the development of Prozorro.
Through Prozorro, contractors can submit bids and citizens can freely access information related to contracts between the Ukrainian state and businesses. This information includes the name of the company, the amount of the transaction and even the reasons that led to choose one tender bid winner and not another. Data is stored in a central database and shared with users through an API. As described by the Organisation for Economic Co-operation and Development (OECD), API is “the functionality that connects systems, people and things without facilitating direct access. These tools are what enable mobile and web-based applications to function, whether reading the news, booking tickets, paying bills or chatting to friends” (5).
More precisely, the United States Agency for International Development (USAID), which supported the project, reveals that Prozorro “is designed in accordance with service-oriented architecture (SOA) based on methods of interaction Representational State Transfer (REST). This solution provides a multi-platform approach, which includes two main components: a CDB and several service platforms that allow the user to interact with the CDB via an Application Programming Interface (API)” (6).
Ukraine has not been flogging a dead horse with Prozorro. The effort to achieve democracy through e-governance has been a long-term and sustained effort. Elected in 2019, the current President, Volodymyr Zelensky, is a strong advocate of this vision. He coined the "state in a smartphone" motto and created the country's first Ministry of Digital Transformation at the head of which he appointed Mykhailo Fedorov (7). The dogs of war having befallen on Ukraine, Zelensky and Federov now have to set aside their promising projects to take on the responsibility of commander in chief, for Zelensky, and cyberwarfare leader, for Federov.

II- Web APIs' security vulnerabilities have been exploited throughout the Russo-Ukrainian War.
II.A. Cyberspace, a full-fledged combat zone in the Russo-Ukrainian War.
If web APIs have then been a prominent tool to improve e-governance and e-democracy in Ukraine, it is not without security risk. On the 17th of January 2022, the day Russian troops were deployed at the Ukrainian border and in Belarus, Prozorro’s Infobox forum was defaced, allegedly by Russian state-sponsored groups. A defacement is a cyber incident through which the attacker inject code into a website as to display a message instead of the original content of the webpage. It can be described as an act of electronic “vandalism” (8). A threat addressed to Ukrainians was thus published on Infobox’s page. Since the forum is separated from the main platform, Prozorro’s activities were not compromised. Nevertheless, it sheds light on the fact that Prozorro is a target of Russian authorities because it is a symbol of hope for democratic progress in Ukraine.
Indeed, Moscow has been hostile to the pro-European Ukrainian authorities in place in Kyiv since the 2014 Revolution. It has annexed Crimea and supported pro-Russian separatists in Donbas. In February 2022, Russia launched a military invasion of Ukraine. The Kremlin justified this enterprise by arguing that Ukraine was going to join the North Atlantic Treaty Organization (NATO), thus adopting a threatening stance against Russia. Yet, if Ukraine applied to join NATO as soon as 2008, its membership had not been put on the table of the Atlantic Alliance, notably because of the opposition of major powers such as France, Germany and even the United States (9).
Therefore, the drivers of Russia’s action might be elsewhere. Published in July 2021, the essay written by the Russian president, Vladimir Putin, “On the Historical Unity of Russians and Ukrainians” puts forward that the recent military operations are enshrined in his nationalist vision. Moreover, the democratic progress accomplished by Ukraine in the past years threaten to set a precedent in Russia’s sphere of influence. The Kremlin’s autocratic regime might fear that such accomplishments would demonstrate to Russian citizens that democracy would not be impossible and inefficient in their own country.
Prozorro’s team are aware of these threats. The journalist Daryna Antoniuk disclosed that Prozorro “was one of the first public companies to launch a bug bounty program in 2020” (10). According to Vasyl Zadovnyy, the platform’s CEO, “within one-and-a-half years, eight bug hunters found 80 vulnerabilities in ProZorro’s system and won $4,200 USD” (11). As early as in 2015, USAID advised Prozorro to guarantee the security of its API through integration testing, an approach that we have been developing at escape.tech for several years.

II.B. Juggling vulnerabilities, a critical exploit in API requests used against Ukrainian websites.
The attacks launched in January 2022 did not target only Prozorro. Russian hackers defaced more than seventy Ukrainian governmental websites. How did they manage to do so ? Ukraine’s Computer Emergency Response Team (CERT-UA) suspects that a vulnerability inside October CMS’ API was used by the attackers. A content management system (CMS) is a program offering an interface to its users so that they can create a website without having to write its code. Being an open source project, October CMS relies on its team of developers and its community of users to detect and fix the program’s vulnerabilities.
Registered as CVE-2021-32648 on CVdetails.com database, one of the security vulnerabilities which was exploited to target Ukrainian institutions enabled attackers to “request an account password reset and then gain access to the account using a specially crafted request” (12).
In other words, hackers exploited a vulnerability in the API request that enabled users to reset their password. This type of breach is thus referred to as an authentication bypass.
Provided on GitHub, the patch, in other words the bug fix, reveals that the exploit came from a juggling vulnerability in the PHP script (12). For instance, let’s take Vladimir, the hacker, targeting Volodymyr, October CMS’ user. Vladimir managed to get Volodymyr’s username. Vladimir requests to reset Volodymyr’s password. Volodymyr then receives an email with a code to create a new password. If it was a legitimate request, Volodymyr would go back to the website and paste the code he just received. October CMS’ software would then use the following function, checkResetPasswordCode, to compare the reset code entered by Volodymyr ($resetCode) and the one that October CMS (reset_password_code) had set up (14).
To do so, the application had to choose between two paths. First, it could adopt a loose equality operator ==. Second, it could rather enforce a strict equality operator ===. Having chosen the first option, October CMS unintentionally allowed Vladimir to enter a value that would be accepted by the software as Volodymyr’s reset password code.
return ($this->reset_password_code == $resetCode);
Indeed, a loose equality operator, == , evaluates the equality between two variables even if they are of different natures: a sequence of characters (string), an integer number (int), a floating number (float), or a boolean (True or False). For example, 5 == "5" is true because the loose equality operator establishes a connection between the int, 5, and the string, “5”, since the value of both variables is the same. Yet, 5 === "5" is false since 5 and “5” are of different nature.
Hence, Vladimir exploited the loose equality operator by writing true instead of the $resetCode received by Volodymyr. Since reset_password_code is the value generated by the function, it will always be evaluated as true. Therefore, reset_password_code == true amounts to true == true, which ultimately obtains a true result. Thereby, Vladimir’s request to change Volodymyr’s password was approved. He finally logged into the compromised October CMS account and defaced the targeted website.
This breach consequently sheds light on the necessity to adopt a strict equality operator, === , rather than a loose equality one, == , when building authentication processes.
return ($this->reset_password_code === $resetCode);
Following the attack, October CMS disclosed that it had pushed a commit, meaning that they updated the program’s code, fixing this vulnerability as early as in March 2021. They consequently stressed that “keeping software installations current is an essential measure in maintaining server security” (15).
Conclusion
“All real wars bring into conflict collectivities which are united in expressing one will. In this regard, they are all psychological wars”, wrote Raymond Aron in Peace and War (1962) (16). The aforementioned cyberattack launched via a web API did not have major lasting consequences physically. Having defaced Ukrainian governmental websites, their purpose was to undermine the population's trust in their state. They are therefore enshrined in the trial of wills described by Aron.
Even if they are unsophisticated, the psychological impact of cyber disruptions should not be underestimated. “Cyber disruptions are a low-cost, low-payoff form of cyber strategy designed to shape the larger bargaining context. These cheap signals likely do not achieve sufficient leverage to compel a target. Rather, they seek to probe an adversary: testing their resolve, signaling escalation risk, and supporting larger propaganda efforts” underscore Benjamin Jensen, Brandon Valeriano and Ryan Maness (17).
Such an information warfare doctrine is not new as highlights Sandor Fabian’s depiction of Moscow’s cyberattacks during the 2008 Russo-Georgian War: “On 8 August 2008 at the same time when Russian military forces started their offensive operations, multiple cyber-attacks were also launched against high visibility Georgian targets including the websites of the Georgian Parliament, the President, the Ministry of Defence, the Ministry of Foreign Affairs, the National Bank, and the major news outlets in Georgia” (18).
Notwithstanding this tried-and-tested approach, Kyiv has managed to get the upper hand in the information war launched by Moscow (19). Pictures and videos of Ukrainian cities being torn apart, of women and children seeking refuge in neighbouring countries and of ordinary citizens taking up arms and banners to confront Russian soldiers have won the compassion of the international community. Ukrainian hackers managed to take offline Russia’s majority state-owned bank, Sberbank, during 24 hours. This attack undermined the untouchable image of the Kremlin and of its cyber capabilities.
Facing a strong Ukrainian resistance and sporadic discontent at home, Putin might thus step up his cyber-offensive for two possible reasons. In a first hypothesis, it could help his army to complete the occupation of Ukraine, a perilous goal however when one remembers the fatal Soviet occupation of Afghanistan between 1979 and 1989 (20). In a second and more modest hypothesis, it could strengthen his position at the negotiating table. At the time of writing, Russian cyber operations still consist of limited nuisance disturbance (21). Moscow could then target critical infrastructure, as it did in 2015 when Unit 74455, the advanced persistent threat (APT) group of the GRU, took down the Ukrainian power grid.
In Ukraine, web APIs have demonstrated their value to achieve democratic progress through e-governance. Nonetheless, API security has revealed its vital nature in light of the cyberattacks launched by Russian state-sponsored hackers. Convinced that the cyberspace can be a safer place, we, at escape.tech, have developed an automated API vulnerability scanner to protect data and servers from malicious hackers. Web APIs are a great gift that ought to be preserved.
Wanna know more about Security? Check out our blog post "9 GraphQL Security Best Practices" and learn how to build safe GraphQL APIs.
Bibliography
(1) Alperovitch, Dmitri [@DAlperovitch]. “Signal: Cyber prep. Since early December, there has been a dramatic increase in cyber intrusions on Ukraine government and civilian networks from Russia.” Twitter, posted on December 21, 2022, https://twitter.com/DAlperovitch/status/1473363114427133967.
(2) “UKRAINE: Timeline of Cyberattacks on critical infrastructure and civilian objects.” Cyber Peace Institute, March 1, 2022, https://cyberpeaceinstitute.org/ukraine-timeline-of-cyberattacks/.
(3) “Microsoft Digital Defense Report.” Microsoft, October 2021, https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWMFIi.
(4) ibid.
(5) “Unlocking the Digital Economy – A Guide to Implementing Application Programming Interfaces in Government.” OECD, 2019, https://www.oecd.org/tax/forum-on-tax-administration/publications-and-products/unlocking-the-digital-economy-guide-to-implementing-application-programming-interfaces-in-government.pdf.
(6) “Technical Assistance for the E-Tender Initiative in Kyiv, Ukraine (Phase One).” USAID, May 29, 2015, https://pdf.usaid.gov/pdf_docs/PA00KQ6K.pdf.
(7) "I dream about a state in a smartphone - Volodymyr Zelenskyy." President of Ukraine, May 23, 2019, https://www.president.gov.ua/en/news/ya-mriyu-pro-derzhavu-u-smartfoni-volodimir-zelenskij-55585.
(8) Maness, Ryan C & Brandon Valeriano. “The Impact of Cyber Conflict on International Relations.” Armed Forces & Society, 2016, vol. 42(2), pp.301-323.
(9) Wong, Edward & Lara Jakes. “NATO Won’t Let Ukraine Join Soon. Here’s Why.” New York Times, January 13, 2022, https://www.nytimes.com/2022/01/13/us/politics/nato-ukraine.html.
(10) Antoniuk, Daryna. “Ukraine reconsiders bug bounties after latest cyberattacks. but are they enough?” The Record, February 3, 2022, https://therecord.media/ukraine-reconsiders-bug-bounties-after-latest-cyberattacks-but-are-they-enough/.
(11) ibid.
(12) “Vulnerability Details : CVE-2021-32648.” CVE Details, August 28, 2021, https://www.cvedetails.com/cve/CVE-2021-32648/.
(13) daftspunk. “Backport code audit from 1.2.” GitHub, committed on April 1, 2021, https://github.com/octobercms/library/commit/016a297b1bec55d2e53bc889458ed2cb5c3e9374.
(14) bennothommo. “octobercms / library.” GitHub, latest commit on September 27, 2019, https://github.com/octobercms/library/blob/v1.0.471/src/Auth/Models/User.php.
(15) “On the Importance of Keeping Your Server Up to Date.” October CMS, January 15 2022, https://octobercms.com/blog/post/importance-keeping-your-server-updated.
(16) Aron, Raymond. Peace and War : a Theory of International Relations. Transaction Publishers, 2003.
(17) Jensen, Benjamin, Brandon Valeriano & Ryan Maness. “Fancy bears and digital trolls: Cyber strategy with a Russian twist.” Journal of Strategic Studies, 2019, 42:2, pp.212-234.
(18) Fabian, Sandor. “The Russian hybrid warfare strategy - neither Russian nor strategy.” Defense & Security Analysis, 2019, 35:3, pp.308-325.
(19) Thornhill, John. “Ukraine is winning the information war against Russia.” Financial Times, March 3, 2022, https://www.ft.com/content/2a11a507-80a3-4da5-9eee-4dafa4a7ee6e.
(20) Riedel, Bruce. “Could Ukraine be Putin’s Afghanistan?” Brookings, February 24, 2022, https://www.brookings.edu/blog/order-from-chaos/2022/02/24/could-ukraine-be-putins-afghanistan/.
(21) Menn, Joseph & Craig Timberg. “The dire predictions about a Russian cyber onslaught haven’t come true in Ukraine. At least not yet;” The Washington Post, February 28, 2022, https://www.washingtonpost.com/technology/2022/02/28/internet-war-cyber-russia-ukraine/.
