Top 10 DAST tools in 2026: APIs, CI/CD & business logic
Discover the top 10 DAST tools for 2026, reviewed for APIs, SPAs, and CI/CD pipelines. Compare strengths, weaknesses, and key features that matter to AppSec and DevSecOps teams.

With global cybercrime costs projected to reach $10.5 trillion annually by 2025 and 30,000 websites compromised daily worldwide, the best DAST tools have become essential for identifying vulnerabilities in applications and APIs. According to Gartner's 2025 forecast, global information security spending will reach $213 billion this year—driven largely by the rising urgency around application security. These cybersecurity solutions detect security flaws by scanning for weaknesses and simulating real-world attacks against running applications.
Modern DAST goes more than surface-level checks. It finds business logic flaws, broken authentication, and authorization vulnerabilities. These security issues only appear when you actually interact with an application's interfaces and workflows. By testing how attackers could exploit intended functionality, modern DAST reduces false positives and adds critical security coverage for teams adopting CI/CD pipelines and developer-first security programs.
Legacy solutions like Qualys DAST and Rapid7 have become outdated. They burden teams with false positives, manual setups, and limited remediation guidance. Modern DAST tools solve these problems. They reduce workloads, minimize false positives, and integrate seamlessly into CI/CD pipelines.
"DAST is not dead, legacy DASTs are. Modern DASTs are changing the industry." - Swan Beaujard, Security Engineer at Escape, at the Elephant in AppSec Conference
The top DAST tools stand out through adaptability and automation. They provide real-time feedback. Security teams can focus on strategic priorities instead of manual tasks. DAST tools are essential for any organization serious about application security.
This article covers the top DAST tools for DevSecOps. You will find their pros and cons, and practical guidance on how they can secure your applications. Whether you are a developer, a security team lead, or evaluating tools for enterprise deployment, this guide will help you make the right choice.
TL;DR: Quick comparison of the top 10 DAST tools
Here is a comprehensive comparison of all ten DAST tools covered in this guide. Use this table to quickly identify which solution matches your requirements and improves your security.
| DAST Tool | G2 rating | Best for | API support | CI/CD integration | Pricing model |
|---|---|---|---|---|---|
| Escape | 4.8/5 | Modern AppSec teams with APIs & SPAs, support for complex authentication & business logic testing | REST, GraphQL, SOAP (external scans) | Native (GitHub, GitLab, Jenkins) | Per application/Enterprise |
| StackHawk | 4.5/5 | Developer-first DevSecOps teams | REST, GraphQL, SOAP, gRPC (limited API security detection, built around ZAP) | Excellent | Per-application, Free tier |
| Invicti | 4.6/5 | Best for enterprise security and audit-ready reports | REST, SOAP, GraphQL (limited) | Yes, but not easy to implement & lacks detailed debugging | Per-seat / Enterprise |
| Bright Security | 4.4/5 | Mid-sized teams with predefined apps | REST, SOAP, GraphQL (limited) | Yes | Per-scan |
| Snyk (Probely) | 4.3/5 | Teams in Snyk ecosystem | REST (manual upload) | Basic | Per-target |
| Burp | 4.7/5 | Pentesters | REST, limited API support | Basic | Per-seat, Free community |
| Intruder | 4.5/5 | SMBs seeking simplicity | REST | Yes | Flat-rate tiers |
| Checkmarx | 4.2/5 | Enterprises wanting SAST+DAST combo | REST, SOAP, gRPC | Yes | Enterprise custom |
| Fortify WebInspect | 4.1/5 | Best reporting for regulated industries | REST, SOAP, GraphQL, gRPC (limited, no business logic support) | Limited | Enterprise custom |
| Detectify | 4.3/5 | Best for small–medium businesses seeking quick, lightweight vulnerability scanning (no complex auth support or business logic) | Web apps only | Basic | Per-domain |
Key takeaway: For comprehensive vulnerability detection and native API support, we recommend Escape and StackHawk. For enterprise compliance reporting, Invicti and Checkmarx offer stronger audit features. Teams on a budget should look at open-source alternatives like OWASP ZAP.
For a detailed breakdown of performance on the vulnerable applications, see our DAST tools comparison.
How to choose a DAST tool: selection framework
Selecting the right DAST tool requires more than comparing feature lists. A structured evaluation framework helps you choose a security platform that fits your technical environment, team capabilities, and security objectives.
Key evaluation criteria
Prioritize these ten criteria when evaluating DAST tools:
1. Business logic vulnerability detection
The ability to detect BOLA and IDOR vulnerabilities separates modern DAST from legacy scanners. Tools that only find OWASP Top 10 basics miss the vulnerabilities attackers actually exploit. Check if the tool can test multi-step workflows and user permission boundaries.
2. False positive rate
High false positive rates waste developer time and erode trust. Look for tools with proof-based scanning that validates findings before reporting. Ask vendors for their documented false positive rate. Industry leaders achieve under 5%.
3. API protocol support
Modern applications rely on diverse API architectures. Make sure the tool natively supports REST, GraphQL, gRPC, and SOAP. Native support means the tool understands protocol-specific vulnerabilities, not just generic injection tests. The tool should also detect exposed secrets and API keys.
4. CI/CD integration depth
Surface-level CI/CD integration differs from native pipeline support. Check if the tool provides pre-built CI/CD integrations. DAST tools automate security tests when properly integrated. They should support incremental scanning and fail builds based on severity thresholds.
5. Authentication handling
Complex authentication flows break many DAST scanners. Test the tool's ability to handle complex authentication flows including MFA, SSO, OAuth, and SAML. Tools that fail when authentication changes create security blind spots and leave applications vulnerable to attacks.
6. Remediation guidance quality
Identifying vulnerabilities is half the challenge. The best tools provide stack-specific code fixes, not generic OWASP references. Check if remediation guidance matches your development frameworks and follows security best practices.
7. Scalability
A tool that works for 10 applications may struggle with 100 or 1,000. Check if the solution scales horizontally without requiring proportional team growth. Consider scan parallelization and enterprise deployment options.
8. Compliance reporting
Regulated industries need audit-ready outputs. Look for pre-built templates covering PCI DSS, SOC 2, HIPAA, ISO 27001, and GDPR requirements.
9. Total cost of ownership
Licensing fees represent only part of the cost. Include implementation time, training requirements, ongoing maintenance, and integration development in your comparison.
10. Asset discovery
You cannot secure what you cannot see. If you want a comprehensive solution, Cceck whether the DAST tool offers additional API discovery capabilities or/and shadow API detection. Tools with agentless discovery reduce manual inventory maintenance and improve your overall security posture.
Quick selection checklist
Use this checklist during vendor evaluations:
- Does the tool detect business logic vulnerabilities (BOLA, IDOR, broken access control)?
- What is the documented false positive rate?
- Does it support your API protocols natively?
- Can it integrate into your specific CI/CD platform with pre-built actions?
- Can it handle your authentication method without manual intervention?
- Does remediation guidance match your tech stack?
- Can it scale to your projected application count?
- Does it discover APIs automatically?
- Does it generate reports for your compliance requirements?
- What is the total first-year cost including implementation?
Total cost of ownership considerations
Licensing models vary significantly across DAST vendors. Per-application pricing works well for organizations with stable application counts. Per-seat pricing benefits small teams scanning many applications. Flat-rate enterprise licensing provides predictability.
Hidden costs to evaluate:
- Implementation and onboarding: Some tools require weeks of professional services
- Training requirements: Complex tools demand ongoing education investment
- Integration development: Custom integrations consume engineering resources
- Maintenance overhead: Outdated legacy tools often require dedicated administrators
For a deeper dive into evaluation criteria, read our guide on building a business case for DAST.
Best DAST tools by use case
Best DAST for API security
Modern applications are API-first. Dedicated API security testing is essential for identifying vulnerabilities in your interfaces. These tools excel at securing REST, GraphQL, and gRPC endpoints.
| Tool | API strengths | Limitations |
|---|---|---|
| Escape | REST & Native GraphQL, business logic testing, tailored remediations per framework |
Advanced features need configuration |
| StackHawk | REST, GraphQL, SOAP, gRPC support,developer-friendly |
Limited business logic detection |
| Invicti | Full REST and SOAP coverage, enterprise reporting |
GraphQL support is basic |
Recommendation: For GraphQL APIs, complex API architectures, or business logic testing, we recommend Escape for the deepest native support. StackHawk offers breadth across multiple protocols at a lower price point.
For comprehensive API security strategies, explore our best API security tools guide.
Best DAST for enterprise security
Enterprise deployments require scalability, compliance features, and integration with existing security infrastructure. These AppSec tools meet large organization requirements.
| Tool | API strengths | Limitations |
|---|---|---|
| Escape | Scales to thousands of apps, Wiz integration, business logic testing |
Number of external integrations is limited |
| Invicti | Mature security platform, rich compliance reporting, ASPM capabilities |
Higher cost, limited GraphQL support |
| Checkmarx | Combined SAST+DAST+SCA, broad ecosystem |
Complex setup, higher false positives |
Recommendation: Enterprises prioritizing modern API security and business logic testing should evaluate Escape. Those needing comprehensive reporting and audit trails may prefer Invicti's mature compliance features.
Best DAST for startups
Startups need fast implementation, reasonable pricing, and minimal operational overhead. These tools provide automated scanning for vulnerabilities without requiring dedicated security teams.
| Tool | API strengths | Limitations |
|---|---|---|
| StackHawk | Free tier available, developer-focused, fast setup |
Limited enterprise features |
| Intruder | Simple interface, affordable pricing, good coverage |
Less customization |
| Detectify | Quick external scanning, easy onboarding for external scans |
No API testing, basic features |
Recommendation: Start with StackHawk's free tier for CI/CD-integrated testing. As security needs mature, evaluate whether Intruder's simplicity or Escape's depth better matches your growth.
For foundational security guidance, see our SaaS startup security guide.
Best DAST for DevSecOps and CI/CD integration
DevSecOps teams need seamless pipeline integration and developer-friendly workflows. These tools follow best practices to prevent threats early in the development cycle.
| Tool | API strengths | Limitations |
|---|---|---|
| Escape | Native CI/CD integration, detailed Jira tickets, remediation code, IDE integration via MCP |
Learning curve for advanced features |
| StackHawk | Built for CI/CD, parallel scanning, developer experience focus |
Limited business logic testing & remediation guidelines |
| Bright Security | IDE integration, early-stage testing, major CI platform support |
Manual API schema uploads, limited authentication support |
Recommendation: Teams prioritizing deeper vulnerability detection will benefit from Escape's business logic testing and seamless integration via Escape MCP. Those focused on supporting developers in their environment should evaluate StackHawk.
Best overall open source DAST tool
Budget constraints should not prevent security testing. Open-source tools provide foundational DAST capabilities for teams building security programs incrementally.
| Tool | API strengths | Limitations |
|---|---|---|
| OWASP ZAP | Best overall open source DAST tool, active community, extensible |
Requires expertise, manual setup |
| Nikto | Fast web server scanning, lightweight | Limited modern app support |
| Wapiti | Good coverage, active development | Less documentation |
Recommendation: OWASP ZAP remains the main standard for free DAST. It requires security expertise to configure effectively. Organizations outgrowing ZAP should evaluate commercial vulnerability scanners offering automation and reduced operational overhead.
Best DAST for GraphQL APIs
GraphQL's unique architecture requires specialized security testing. Most legacy DAST tools fail to test GraphQL effectively, leaving applications vulnerable to GraphQL-specific attacks.
| Tool | API strengths | Limitations |
|---|---|---|
| Escape | Purpose-built GraphQL testing, introspection analysis, 100+GraphQl-focused tests |
- |
| StackHawk | Basic GraphQL support, query testing | Limited depth |
| Bright Security | Basic vulnerability types only | Not GraphQL native |
Recommendation: For production GraphQL APIs, we recommend Escape as the clear leader. Organizations with minimal GraphQL usage may find StackHawk's basic support sufficient.
DAST vs SAST vs IAST: understanding the differences
Choosing between application security testing approaches requires understanding what each method finds and when to apply it. DAST, SAST tools, and IAST serve complementary roles in a comprehensive cybersecurity program.
| Aspect | DAST | SAST | IAST |
|---|---|---|---|
| Testing approach | Black-box (external) | White-box (source code) | Hybrid (instrumented) |
| When it runs | Against running applications | During development/build | During testing/QA |
| What it finds | Real-world vulnerabilities, business logic flaws, authentication issues |
Code-level bugs, insecure patterns, hardcoded secrets | Runtime issues with code context |
| False positive rate | Lower (tests real behavior) | Higher (lacks runtime context) | Medium |
| Setup complexity | Moderate | Lower | Higher (requires agents) |
DAST excels at finding security issues that only appear in running applications. Business logic flaws, authentication bypass, and authorization issues are its strength. SAST tools catch problems earlier but generate more false positives because they cannot observe actual application behavior.
Most mature security programs combine DAST and SAST. SAST catches security flaws during development. DAST validates security in staging and production environments. Some organizations also add Software Composition Analysis (SCA) tools like Endor Labs to identify supply chain vulnerabilities in third-party dependencies.
For a complete comparison, read our SAST vs DAST guide.
DAST for compliance: meeting regulatory requirements
Regulatory frameworks increasingly mandate dynamic security testing as part of compliance programs. DAST tools help organizations meet these requirements while generating audit-ready documentation and improving their security posture.
| Standard | Key requirement | How DAST helps |
|---|---|---|
| PCI DSS | Req. 6.5 & 11.3: Address coding vulnerabilities, regular penetration testing | Tests for injection, XSS, authentication flaws; provides continuous testing evidence |
| SOC 2 | CC6.1 & CC7.1: Vulnerability identification and security testing | Documents security testing processes for auditors |
| HIPAA | Section 164.308(a)(8): Periodic technical evaluations | Validates ePHI applications resist common attacks |
| ISO 27001 | A.14.2.8 & A.12.6.1: Security testing and vulnerability management | Provides testing evidence for application security controls |
| GDPR | Article 32: Appropriate technical security measures | Identifies vulnerabilities that could lead to data breaches |
| DORA | ICT risk management including security testing | Documents testing of application security controls for financial institutions |
Not all DAST tools generate equally useful compliance documentation. Escape, Invicti, Checkmarx, and Fortify offer comprehensive compliance reporting with customizable templates. Escape also provides the compliance matrix to help you evaluate posture at glance. StackHawk provides limited compliance templates but supports custom reports.
For specific guidance, see our articles on PCI compliance, HIPAA compliance, and DORA compliance.
Why legacy DAST tools don't work for DevSecOps
Legacy DAST tools fall short for modern application security needs. They create challenges that hinder effective vulnerability detection and remediation. Many have become outdated and cannot keep pace with modern development practices.
False Positives Overload
Endless false positives waste valuable time. Critical vulnerabilities get overlooked. Applications remain vulnerable and exposed. Security teams spend more time triaging noise than addressing real risks.
Manual Configurations
These tools demand time-consuming manual setups. They struggle to integrate with CI/CD pipelines. They are unsuitable for scalable, modern development workflows. Every application requires individual configuration instead of automated discovery.
Developer Frustration
A lack of actionable remediation guidance creates friction with engineering teams, forcing developers to spend excessive time diagnosing and resolving issues instead of building features.
A lack of actionable remediation guidance creates friction with engineering teams. Developers spend excessive time diagnosing and resolving security issues instead of building features. Generic OWASP references do not help developers fix specific code.
Modern applications are built around Single-Page Apps (SPAs) and APIs. They bring flexibility but also new challenges. Security threats now include Insecure Direct Object References (IDORs), Server-Side Request Forgery (SSRF), and Access Control vulnerabilities. Security needs to be efficient and scalable.
Security teams can no longer work in isolation or reactively. They must automate security processes and integrate them into a DevSecOps pipeline. Security becomes a continuous, proactive part of development following industry best practices.
The top DAST tools excel here. They reduce manual workload, minimize false positives, and offer seamless CI/CD integration.
For deeper analysis, see our examination of problems with current DAST and feedback from AppSec engineers.
Top 10 DAST tools: in-depth reviews
This section provides detailed analysis of each DAST tool. Each review covers capabilities, strengths, limitations, and ideal use cases. These tools can detect a wide range of vulnerabilities across your applications. According to the 2025 Verizon DBIR, 88% of basic web application breaches involve stolen credentials, and 42% of exploited vulnerabilities target web applications—making robust DAST testing more critical than ever.
Escape DAST

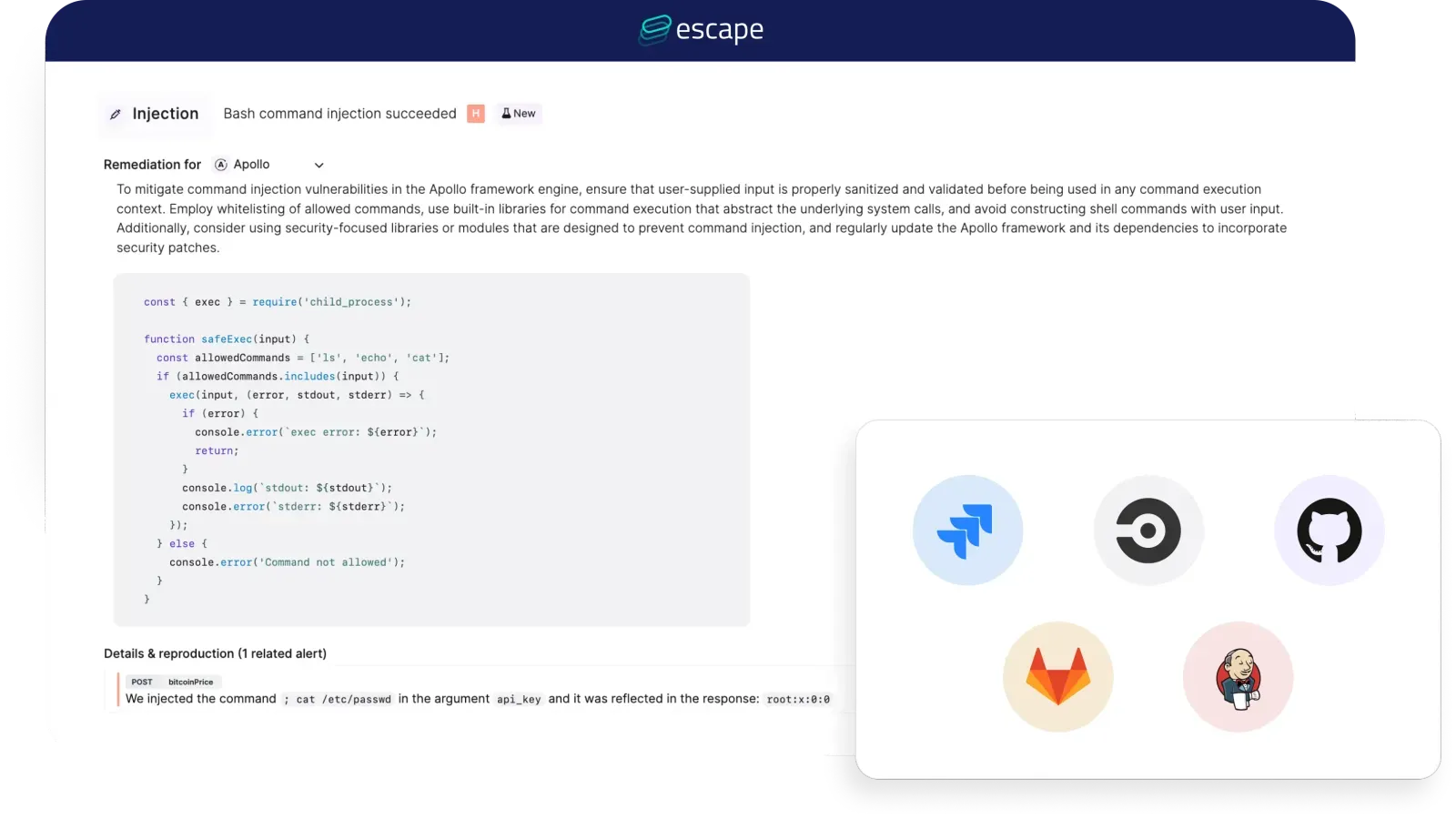
Overview:
Escape DAST Escape DAST is one of the most advanced Dynamic Application Security Testing (DAST) tools in 2026, built specifically for modern tech stacks and complex authentication workflows. It’s ideal for security and AppSec teams looking to scale vulnerability detection with minimal effort and high accuracy.
What sets Escape apart from traditional DAST tools is its ability to detect business logic vulnerabilities.
It’s the only DAST solution that uses a feedback-driven Business Logic Security Testing (BLST) engine. This enables deeper testing tailored to your unique app context, identifying vulnerabilities other scanners often miss. Special attention is given to real-world vulnerabilities like IDORs, BOLAs, and access control flaws. Each discovered vulnerability is supported by AI-Powered Exploit Validation.
In addition to security testing, Escape combines Attack Surface Management and agentless API discovery, and is the best DAST to handle complex authentication scenarios and multi-user testing with natural language rules.Escape is built to support Single Page Applications (SPAs), APIs natively, and to easily integrate in CI/CD pipelines.
🔍 Features
● In-depth Detection for Business Logic Flaws: Escape’s proprietary Business Logic Security Testing engine identifies deep business logic threats like BOLAs, IDORs, and others that often require human in the loop
● GraphQL-Native Security Testing: Escape is purpose-built for GraphQL, sending context-aware queries that reflect real application logic, uncovering vulnerabilities that legacy DAST tools miss.
● Complex authentication handling: Set up advanced authentication configurations, including multi-step auth flows or text-based CAPTCHA
● CI/CD-Ready Custom Tests: Define security rules that evolve with your web apps and APIs and run automatically in your CI/CD pipelines with no manual upkeep. See Escape Rules.
● Automated Asset Discovery, including agentless API discovery: Escape automatically detects external, internal and third-party web apps and APIs by scanning source code with no traffic capture or agents required. It also generates and maintains up-to-date API schemas without manual uploads.
● Risk-Based Vulnerability Prioritization: Escape ranks findings by business impact and exploitability, enabling focused remediation. Explore Prioritization Funnel.
● Developer-Centric Remediation: Escape auto-generates Jira tickets with remediation code tailored to your stack, helping developers fix vulnerabilities faster and reduce MTTR with less back and forth.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Ability to handle complex business logic vulnerabilities. Highly accurate request generation, enhanced by in-house generative AI for smarter vulnerability detection. ✅ Less than 3.7% false positive rate, reducing noise for security teams. ✅ Actionable remediation code snippets, accelerating patching and improving developer efficiency. ✅ Prioritizes critical applications by business context, data sensitivity, and external exposure risk. ✅ Support for complex authentication ✅ Seamless integration with modern DevSecOps tools and CI/CD pipelines for scalable security workflows. |
❌ Advanced features require security expertise or training for optimal use. ❌ Integration coverage for some operational tools is still being expanded. |
Invicti DAST (formerly Netsparker DAST)

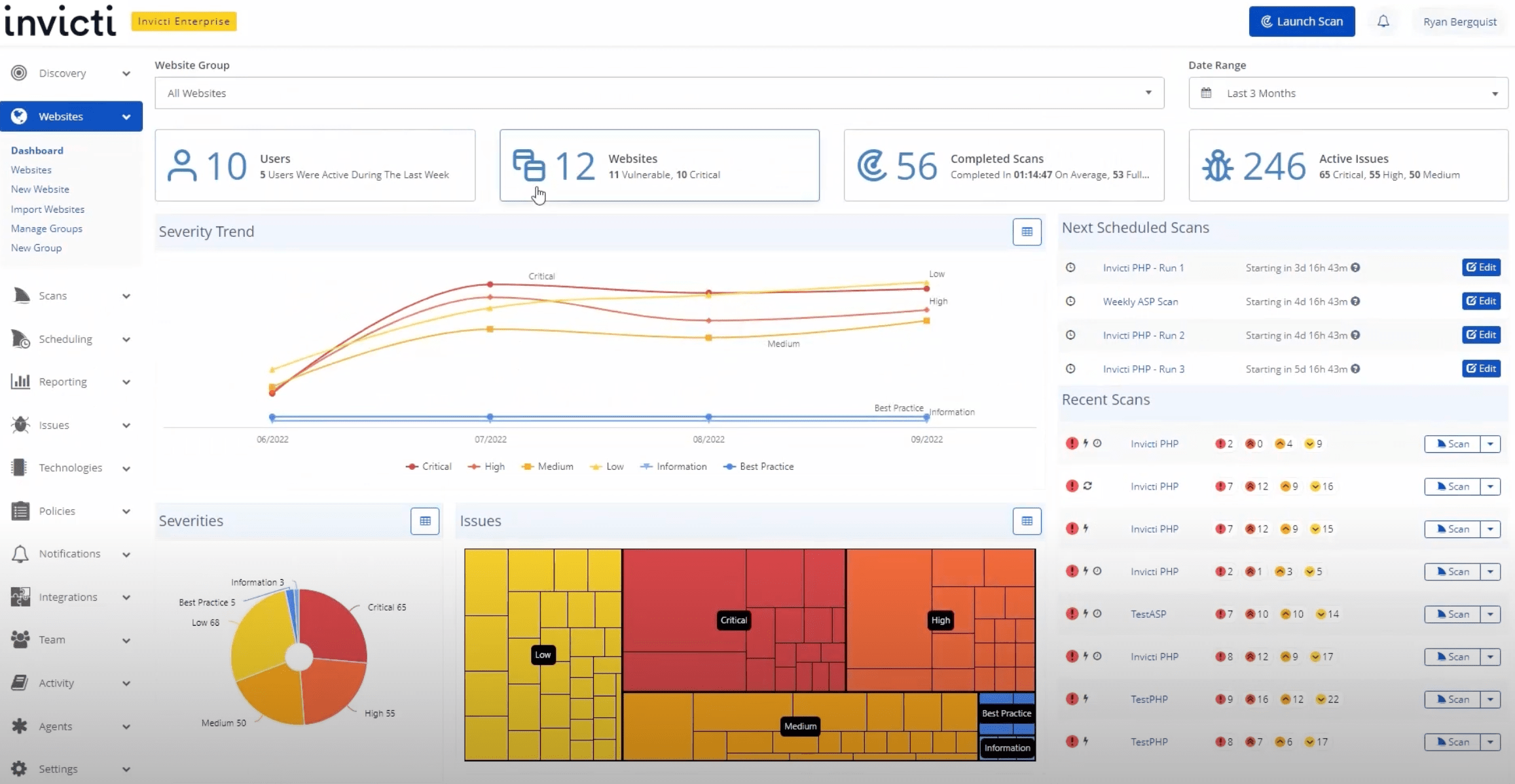
Overview:
Second in our list of the best DAST tools for 2026 is Invicti DAST, (formerly Netsparker DAST), a security solution built for scalable and automated vulnerability detection. Invicti combines Dynamic Application Security Testing (DAST) with Interactive Application Security Testing (IAST), making it capable of identifying a wide range of threats including SQL injection, XSS, misconfigurations, exposed databases, and out-of-band vulnerabilities.
Its automated crawler is designed to scan modern web technologies like HTML5, JavaScript-heavy applications, and Single Page Applications (SPAs). Invicti streamlines the process for development teams by automating crawling and vulnerability detection across complex web environments. While this DAST tool is best suited for large scale enterprises, Invicti also offers Acunetix a simplified version geared toward smaller organizations.
🔍 Features
● Fast vulnerability scans with live access to reports even before completion
● Highlights specific lines of code that require remediation
● Seamless integration with CI/CD pipelines, issue trackers, and Web Application Firewalls (WAFs)
● Basic scans can be completed within minutes for quick feedback cycles
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Supports REST, SOAP, and GraphQL APIs (limited GraphQL coverage) along with traditional web applications. ✅ Generates detailed vulnerability reports for faster triage. ✅ Offers customizable security check templates to tailor DAST scans. ✅ Part of a broader security platform that includes IAST and Software Composition Analysis (SCA). |
❌ GraphQL testing is limited to basic vulnerability types. ❌ Primarily focused on web applications, with less coverage for modern cloud-native environments. ❌ Does not support automatic API specification generation, requiring manual uploads. ❌ Higher entry-level cost compared to other DAST tools in the market. |
StackHawk

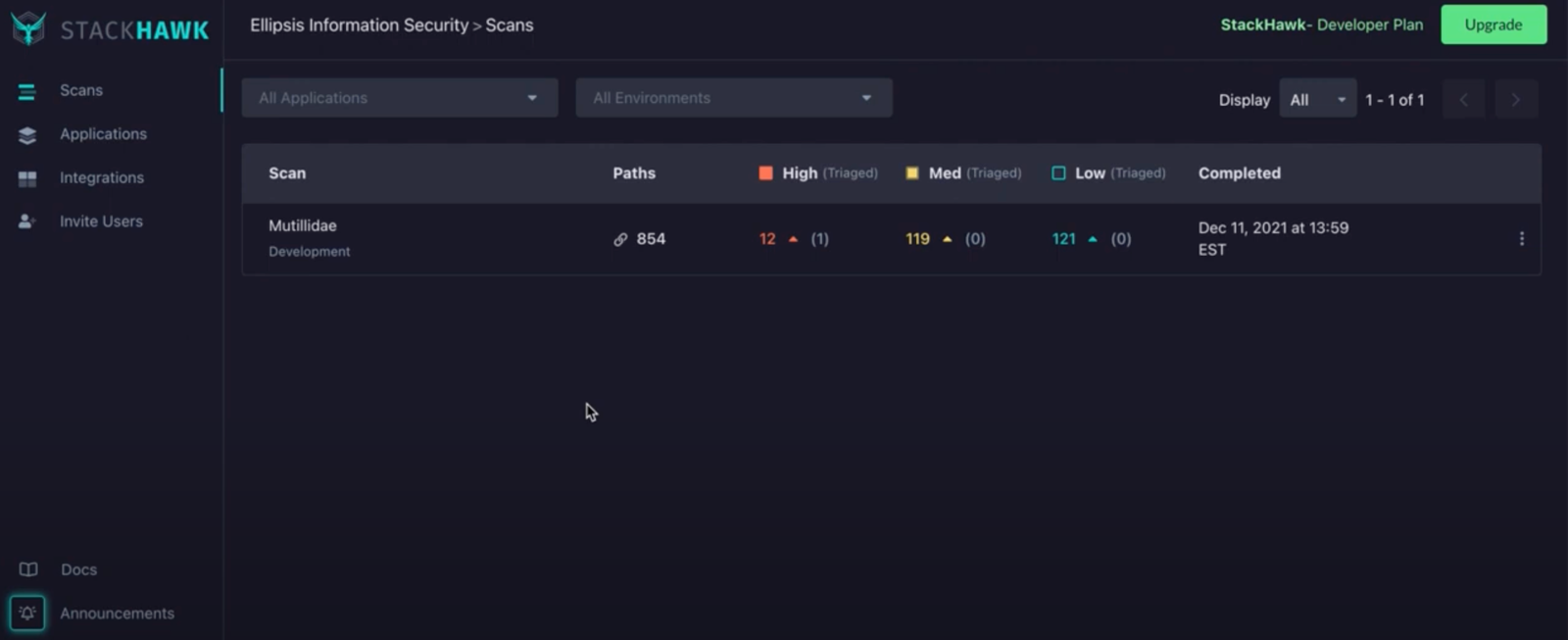
Overview:
StackHawk is a modern Dynamic Application Security Testing (DAST) tool built with developers in mind. It emphasizes catching security vulnerabilities early in the development lifecycle before code hits production. Designed for technical teams, StackHawk helps developers integrate security testing into continuous delivery pipelines with minimal disruption.
Its vulnerability prioritization follows the OWASP Risk Rating Methodology, focusing on impact and exploitability. StackHawk supports a wide range of API formats, including REST, GraphQL, SOAP, and gRPC, making it a solid DAST option for microservices-driven environments.
🔍 Features
● Enables developers to write custom test scripts for security scenarios not covered by default scans (built on the ZAP library)
● Supports parallel scanning across environments local dev, CI/CD pipelines, Kubernetes, or remote servers
● Offers automated and authenticated scans to detect vulnerabilities that appear only after login or session handling
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Built for developers, with strong CI/CD integration ✅ Customizable attack templates to tailor security tests to business logic ✅ Flexible pricing tiers, ideal for startups and fast-growing teams |
❌ Built on ZAP, with limited support for detecting business logic vulnerabilities ❌ API schema uploads and configuration may require manual setup in complex apps ❌ Lacks deep remediation guidance for developers ❌ May not meet the scalability or feature depth needed by large enterprise teams |
Bright Security

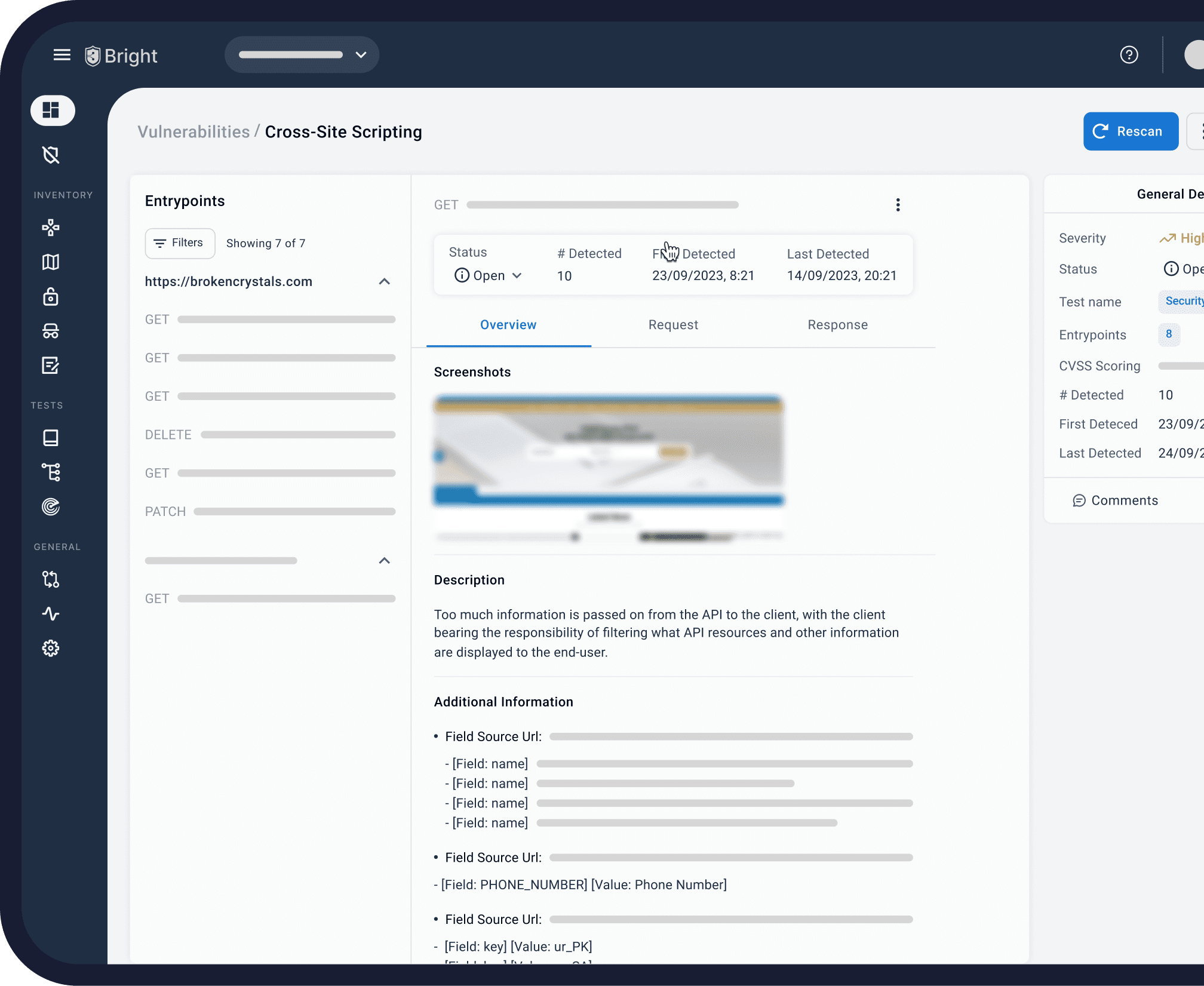
Overview:
Bright Security stands out among modern DAST tools by embedding security testing directly into developer workflows. Its early stage testing capability starting within the IDE helps teams catch vulnerabilities before code ever reaches staging or production. This proactive approach enables faster, more secure releases without adding friction to development.
As one of the few developer first DAST tools, Bright integrates natively with popular CI/CD platforms like GitHub, GitLab, Jenkins, CircleCI, and JFrog. It detects critical web application vulnerabilities such as SQL injection, cross-site scripting (XSS), CSRF, and XXE, offering efficient, automated testing during every stage of delivery. While its coverage of business logic flaws is limited, Bright provides strong foundational testing with minimal configuration.
🔍 Features
● IDE-Based Security Testing: Run real-time attack simulations directly in the IDE to validate code and catch vulnerabilities early.
● CI/CD Pipeline Integration: Supports automated security testing across GitHub, GitLab, Jenkins, CircleCI, and TravisCI.
● Interactive Vulnerability Detection: Detects SQLi, CSRF, XSS, and XXE with limited business logic flaw coverage.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Quick setup and easy onboarding for engineering teams ✅ Developer-focused, with IDE-level security simulations ✅ Seamless CI/CD integration across major platforms |
❌ Requires manual API schema uploads before scans ❌ Remediation advice lacks depth across varied tech stacks ❌ Limited reporting capabilities for business-critical vulnerability prioritization |
Snyk(Probely)

Overview:
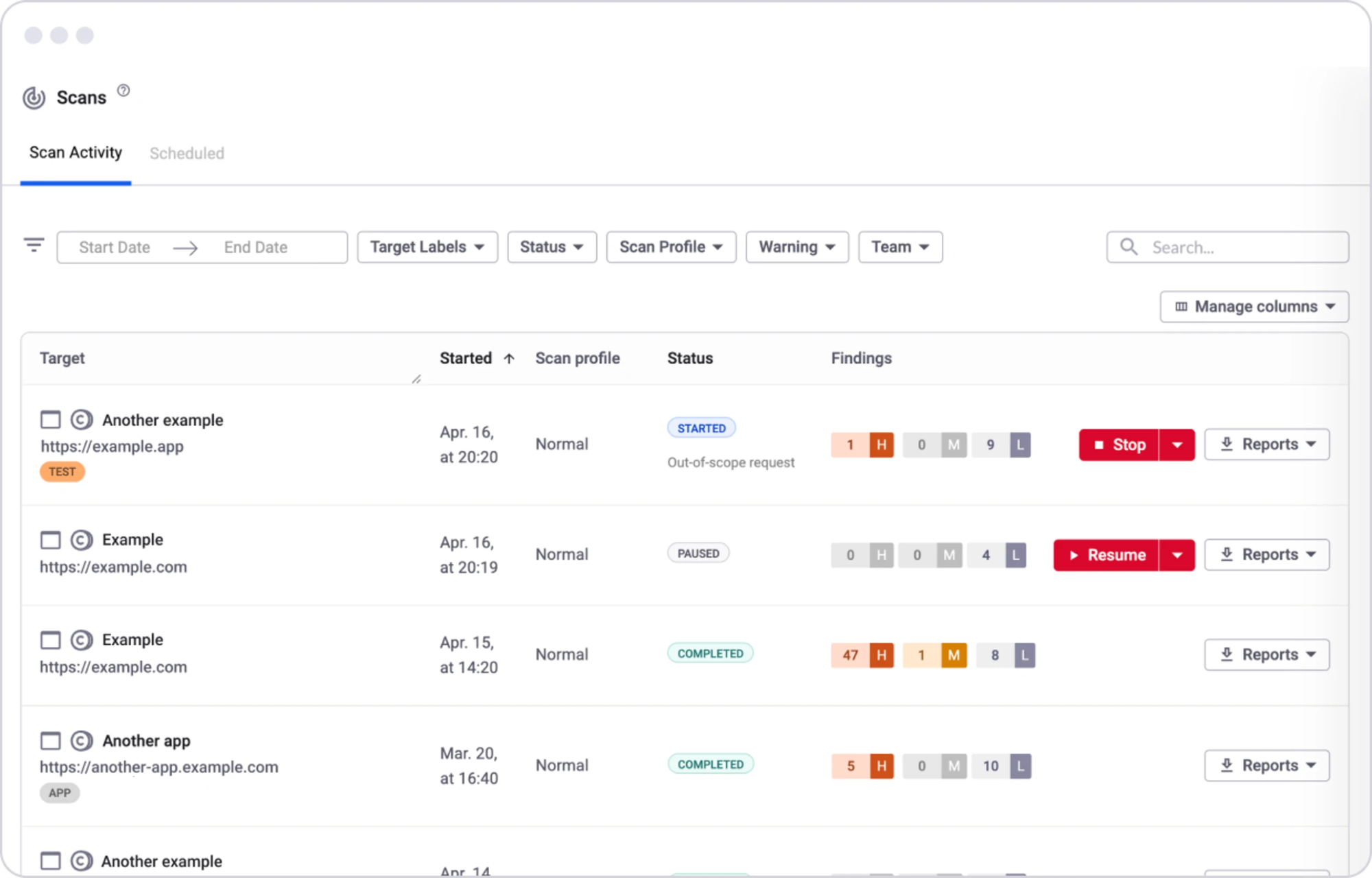
Snyk DAST (formerly Probely) is a cloud-based DAST tool geared toward straightforward application discovery and vulnerability scanning. It suits teams needing basic support for publicly accessible web apps without complex setup or deep security testing.
Snyk DAST performs standard DAST scans to identify common web vulnerabilities like XSS, SQL injection, and misconfigurations. Discovery relies on domain and DNS connectors (AWS Route 53, Cloudflare), but lacks source‑code or API schema automation. Testing APIs requires manual uploads, with no support for business logic flaws or internal assets. While the tool integrates with ticketing systems (e.g., DefectDojo), and offers remediation guidance, it doesn’t include framework‑specific fixes, code‑level remediation, or advanced findings.
Compare technical strengths of Escape vs Snyk DAST
🔍 Features
● Automated DAST Scanning: Performs classic dynamic application security testing (DAST) to identify common vulnerabilities like XSS, SQL injection, and misconfigurations in web applications.
● External Asset Discovery: Supports limited asset discovery via domain connections and DNS providers like AWS Route53 and Cloudflare, but lacks deep discovery from source code or internal environments.
● Manual API Testing Setup: Requires manual upload of API specifications to initiate scans, with no support for automated API discovery or modern API testing workflows.
● Basic DevSecOps Integration: Includes integration with popular CI/CD and ticketing tools, but lacks features like custom security rules, internal API scanning, or developer-focused remediation guidance.
● Backed by Snyk Ecosystem: Benefits from the broader Snyk platform, integrating DAST tools into a more comprehensive developer security solution.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Simple DAST setup for standard web app vulnerabilities ✅ Quickly integrates with ticketing and CI/CD systems ✅ Backed by Snyk’s wider security ecosystem |
❌ No native API discovery or automated schema generation ❌ Unable to test internal or VPN‑protected assets ❌ Does not detect business logic flaws or custom rules ❌ Requires manual API uploads for scanning ❌ Remediation lacks code‑level specificity and framework focus |
Burp Suite


Overview:
Burp Suite DAST is one of the more widely used DAST tools designed to test the security of modern web applications through both automated and manual methods. Known for its deep customization and flexibility, it enables technical teams to identify vulnerabilities such as SQL injection, XSS, and CSRF in dynamic environments.
Unlike simpler tools, Burp Suite DAST offers manual testing components alongside automated scans, making it a strong option for users with security expertise. While setup may be more involved, it remains a well-established dynamic application security testing (DAST) solution for teams needing both extensibility and precision.
🔍 Features
● Performs automated DAST scans to detect common web vulnerabilities like SQL injection, XSS, and CSRF.
● Allows manual security testing for complex scenarios, ideal for experienced security professionals.
● Supports advanced authentication workflows, including Basic Auth, JWT, session cookies, and login recording.
● Offers a flexible plugin system with both free and premium extensions for enhanced vulnerability detection and reporting.
● Includes manual testing tools like Burp Intruder, Repeater, and Sequencer for deep dynamic analysis and edge case testing.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Highly customizable, ideal for advanced users needing fine-tuned DAST testing capabilities ✅ Supports a wide range of authentication methods for complex login workflows ✅ Part of the Burp Suite ecosystem with a large user and plugin community |
❌ Requires manual testing expertise and tuning to deliver optimal results ❌ Lacks built-in support for automated GraphQL or modern API scanning ❌ Limited detection of business logic vulnerabilities ❌ Can be resource-heavy during extensive scans |
Intruder

Overview:
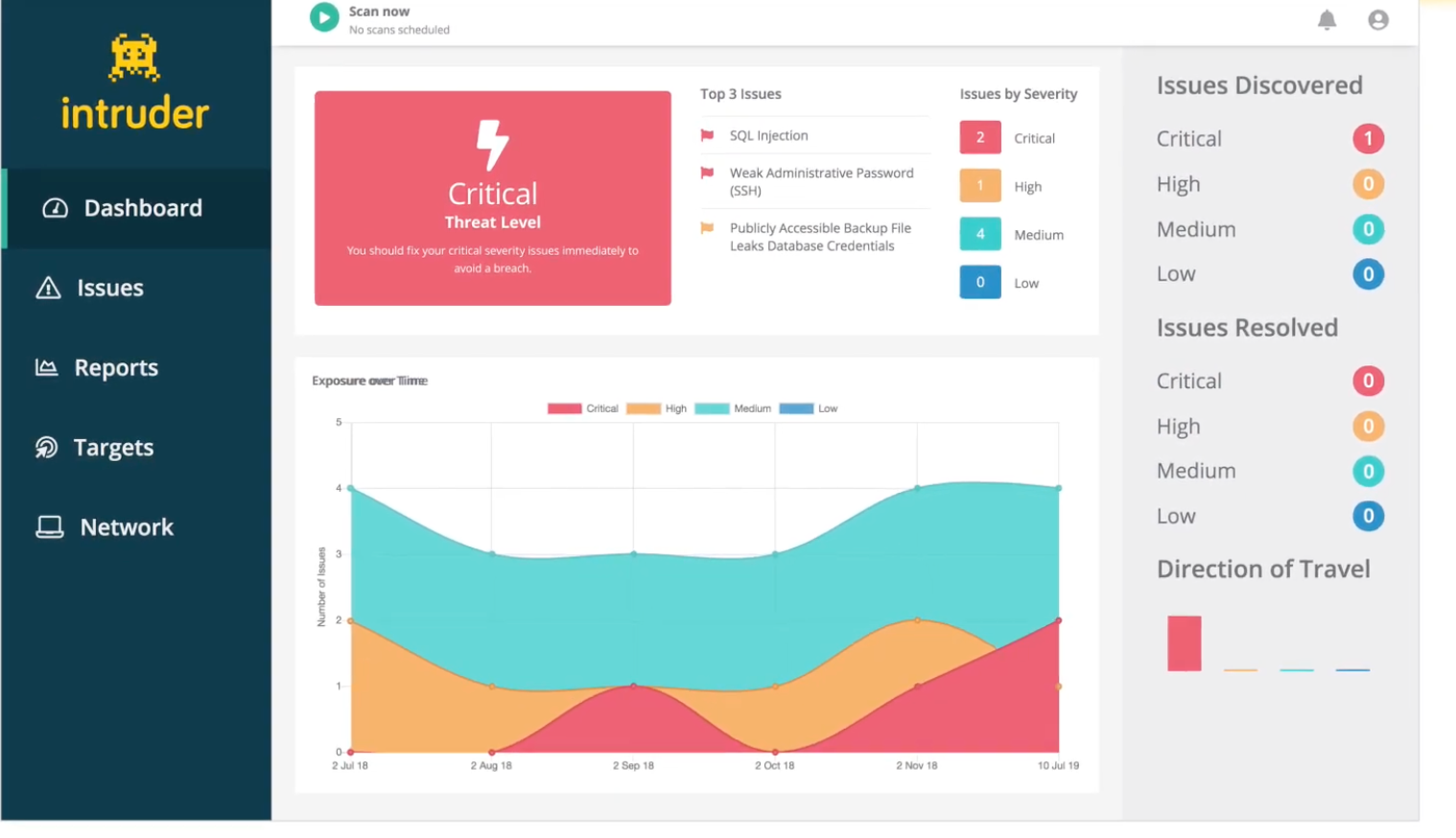
Intruder is a cloud-based DAST tool designed for simplicity and wide-ranging coverage across web applications, APIs, and infrastructure. It excels in identifying exposed systems, misconfigurations, and known vulnerabilities with minimal configuration, making it a strong fit for SMBs and security aware development teams.
Unlike traditional enterprise tools, Intruder provides fast, automated security testing for both internal and external assets. It also includes manual black-box testing capabilities to support deeper assessments when needed.
🔍 Features
● Cyber Hygiene Score: Reflects an organization’s security posture by scoring how effectively vulnerabilities are managed useful for compliance and risk tracking.
● Extensive Integration Options: Supports tools like AWS, Azure, Google Cloud, Cloudflare, Jira, GitHub, GitLab, Teams, and Vanta, streamlining workflows across DevOps pipelines.
● Real-Time Vulnerability Alerts: Provides instant alerts when critical issues are detected, enabling fast response and reduced exposure.
● Audit-Ready Reports: Delivers compliance friendly reports for internal reviews, audits, and regulatory requirements.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Easy integration into CI/CD pipelines to align with DevOps practices ✅ Cost-effective DAST solution for individual users or growing teams ✅ Offers continuous vulnerability scanning and cloud security insights |
❌ Manual testing features may require expert involvement for full value ❌ Does not extend scanning to Kubernetes or advanced code-level analysis ❌ Lack of scan customization may reduce efficiency in complex environments |
Checkmarx

Overview:
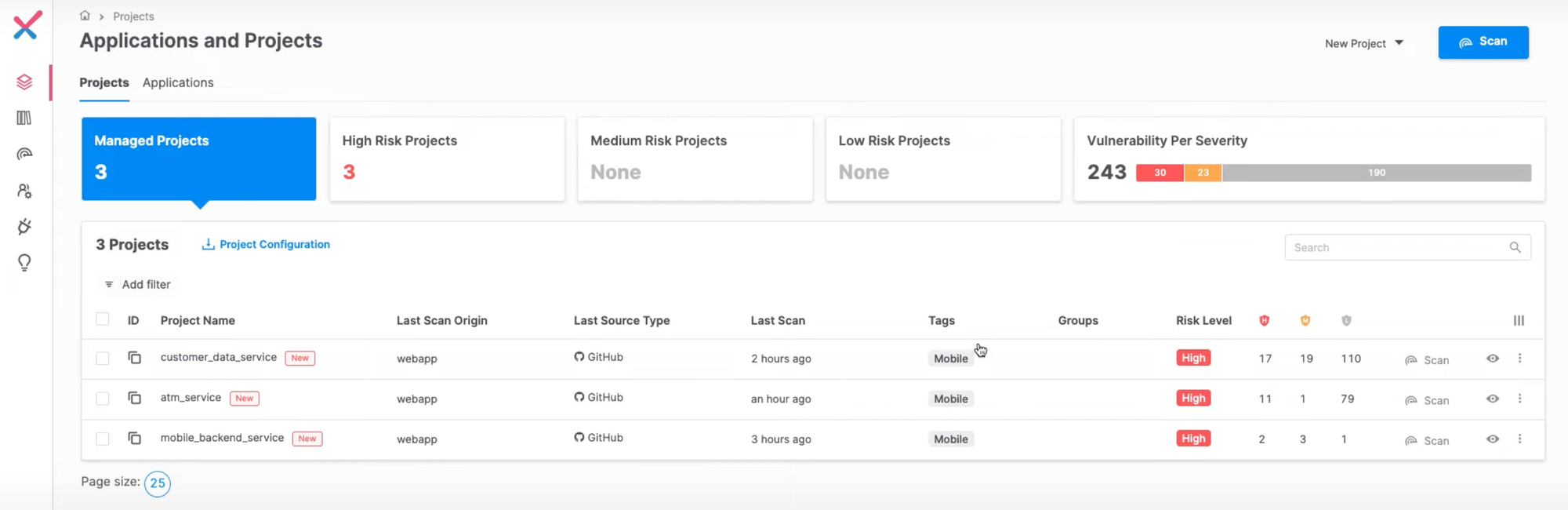
Checkmarx is a security platform that combines Static and Dynamic Application Security Testing (SAST and DAST), offering a holistic solution for identifying vulnerabilities across the software development lifecycle. It performs DAST scans against live applications to uncover runtime risks, while also using SAST to detect issues in source code before deployment. This combined approach helps larger enterprises manage security at scale.Learn more about SAST vs DAST.
It supports the analysis of APIs, including REST, SOAP, and gRPC, making it suitable for complex applications with diverse architectures. While it’s powerful, Checkmarx requires a deeper investment in setup and resources, which aligns it more with larger organizations.
🔍 Features
● Performs SAST and DAST together for complete visibility across development and runtime environments.
● Integrates into CI/CD pipelines to automate testing before deployment stages.
● Supports automated testing of APIs and endpoints in live production environments.
● Correlates security findings across multiple layers: source code, APIs, open-source components, and infrastructure as code.
● Provides educational resources to help developers write secure code.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Combines multiple security testing methods (SAST, DAST, and SCA) into one platform ✅ Scalable architecture and flexible configurations for large enterprise environments ✅ Supports integration with common CI/CD tools and developer workflows |
❌ Requires considerable expertise and setup time for effective implementation ❌ Limited support for GraphQL API security testing ❌ Complex user interface may pose challenges for usability ❌ Higher potential for false positives compared to specialized DAST tools ❌ Custom rule configuration can be difficult to manage |
Fortify

Overview:
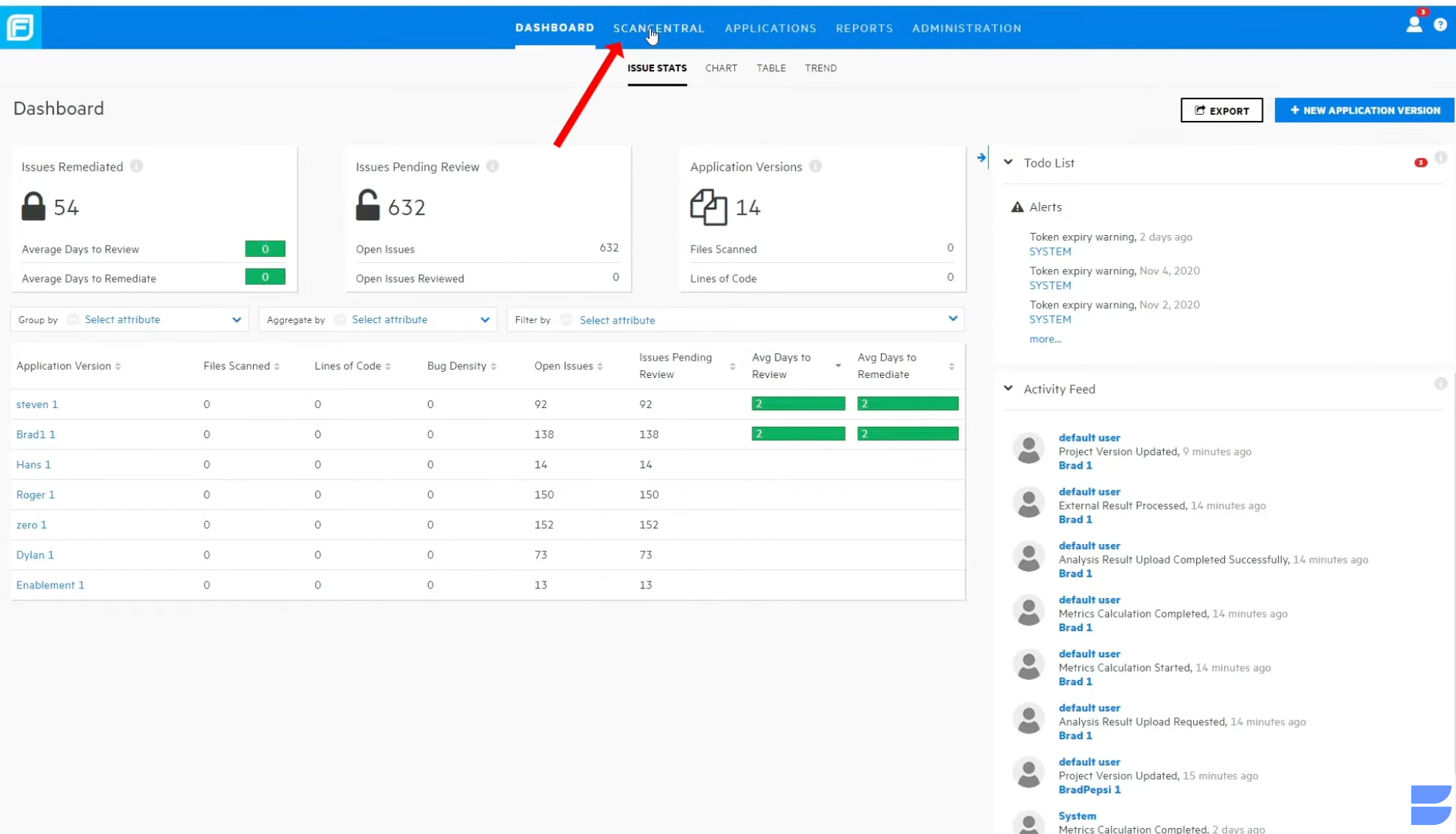
Fortify WebInspect by OpenText is a dynamic application security testing (DAST) tool designed to detect vulnerabilities that traditional IAST tools might miss. It leverages functional security testing to enhance web application protection and supports horizontal scaling using Kubernetes to boost JavaScript scanning speeds.
The platform offers flexible deployment models, including on-premise, SaaS, and AppSec-as-a-Service, making it suitable for various enterprise environments. With built-in compliance templates and integrations, WebInspect is ideal for security teams needing robust, customizable application security assessments.
🔍 Features
● Detects redundant and duplicate pages to optimize scanning workflows
● Automatically generates macros to streamline test coverage
● Offers containerized delivery for modern infrastructure compatibility
● Scans multiple API protocols including REST, SOAP, OpenAPI, Swagger, Postman, GraphQL, and gRPC
● Integrates with OpenText tools such as Application Lifecycle Management and Quality Center for centralized control
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Simultaneous crawling and auditing for faster vulnerability detection ✅ Customizable reporting for compliance and executive visibility ✅ Flexible deployment across cloud, hybrid, and on-prem environments |
❌ Requires technical expertise for effective configuration and use ❌ Steep learning curve to maximize platform efficiency ❌ Limited CI/CD integration may slow adoption in fast-paced DevOps environments |
Detectify

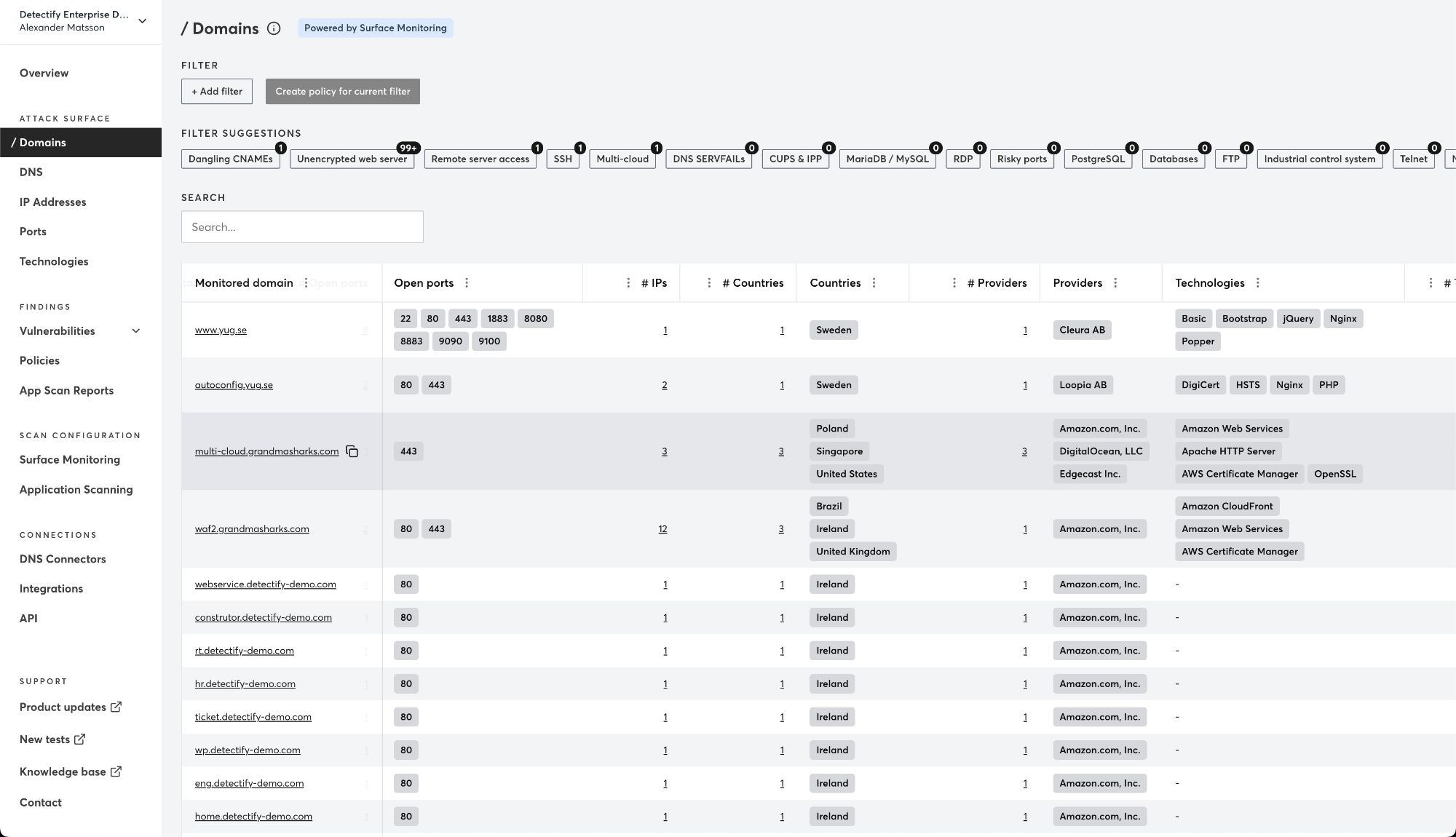
Overview:
Detectify is a cloud-based DAST tool designed to uncover vulnerabilities in publicly exposed web applications. It combines Surface Monitoring to detect changes and risks across subdomains and DNS assets with Application Scanning, which uses fuzzing techniques to find known web security flaws like SQL injection, XSS, and misconfigurations.
As one of the more lightweight DAST tools, Detectify is easy to set up and geared towards monitoring external-facing assets. However, it lacks native support for internal application scanning, complex authentication, and API security testing—making it less suitable for organizations with broader or more modern security requirements. To explore a more advanced approach to dynamic application security, see this detailed comparison of Detectify and modern DAST alternatives.
🔍 Features
● Continuously monitors domains and subdomains via DNS integrations such as AWS Route53, Azure, Cloudflare, and Google Cloud DNS.
● Uses fuzzing-based DAST scanning to identify common vulnerabilities like XSS, SQL injection, and insecure headers.
● Supports basic authentication and session cookies, but lacks advanced login handling or multi-factor workflows.
● Focused on external attack surface monitoring; does not support internal app or behind-the-firewall scanning.
● No native support for API security testing, GraphQL scanning, or automatic API schema handling.
📊 Pros & Cons
| 📈 Pros | 📉 Cons |
|---|---|
|
✅ Simple setup and fast onboarding for external web application scanning ✅ Continuous monitoring of public-facing domains for exposure ✅ Detects widely known vulnerabilities using automated DAST scanning |
❌ No native API testing or support for scanning internal applications ❌ Limited handling of complex authentication flows ❌ Generic remediation advice, not tailored to specific development frameworks ❌ Minimal reporting capabilities, lacking detailed compliance views ❌ Not ideal for scaling in larger or more complex security environments |
Preparing a list of DAST tools to evaluate on your modern applications?
Learn how Escape DAST can help you meet your compliance mandates quickly, reduce the load on your developers, and remediate vulnerabilities more effectively than ever
Legacy DAST tools
Some legacy solutions remain in use at organizations with established security programs. They offer broad functionality but struggle with modern application architectures and DevSecOps workflows. Many have become outdated compared to modern alternatives.
Qualys Web Application Scanning: Cloud-based with REST and SOAP support, TruRisk scoring system for risk prioritization. See Escape vs Qualys.
Rapid7 InsightAppSec: Scans applications on closed networks with optional on-premise engine, Attack Replay for vulnerability validation. See Escape vs Rapid7.
Veracode: Combines SAST, DAST, SCA and manual penetration testing with scheduled scans and remediation guidance.
What is a DAST tool?
Dynamic Application Security Testing is a black-box testing approach that simulates real-world attacks on running APIs, SPAs, and web applications. It detects security flaws without needing source code access. DAST tools are essential for any comprehensive cybersecurity program.
Modern AI-powered DAST solutions use intelligent crawling, behavior analysis, and risk prioritization. They reduce false positives and improve accuracy. They secure web apps, APIs, and microservices in CI/CD pipelines through continuous, scalable testing.
How DAST works
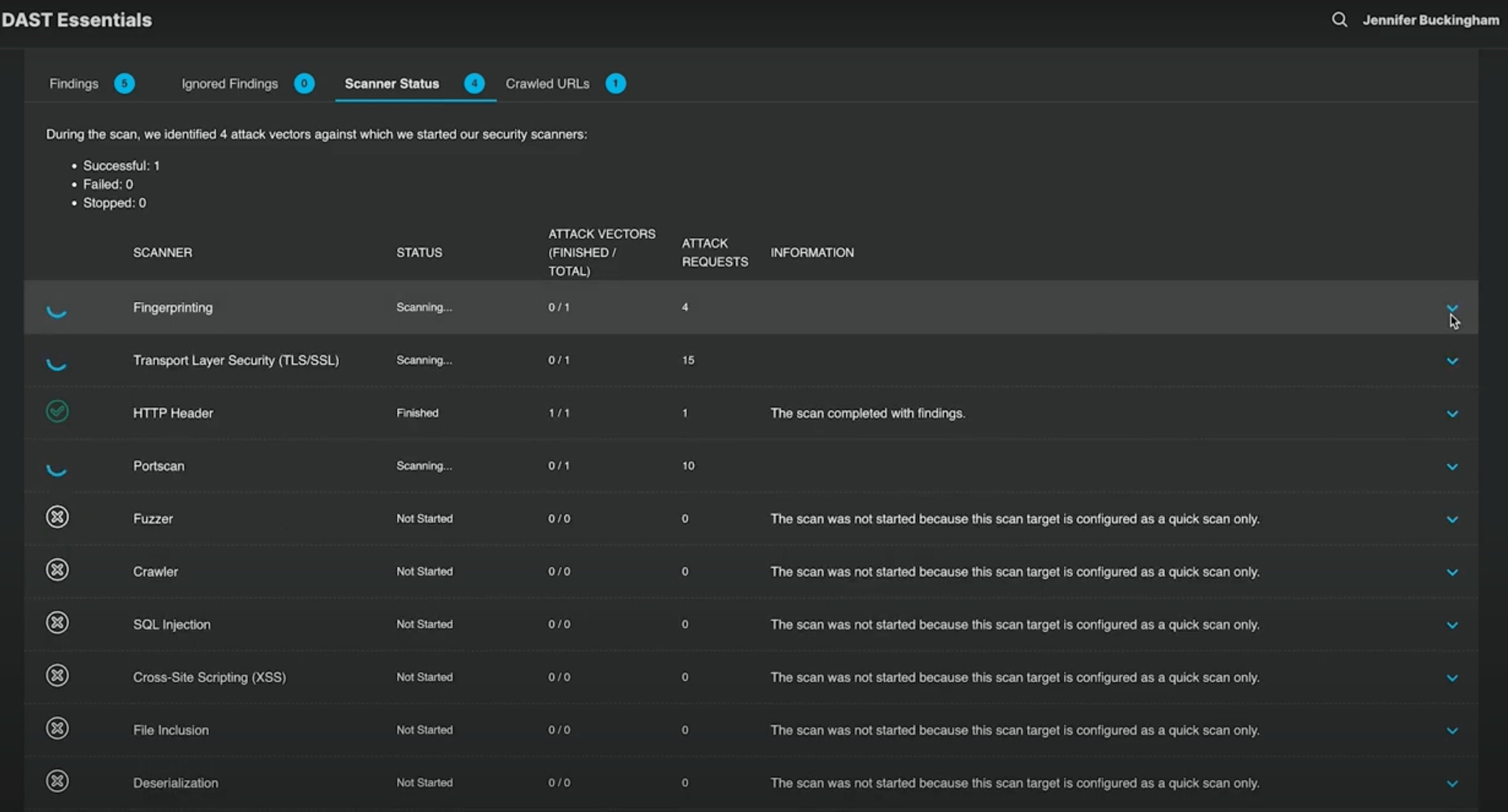
DAST tools interact with applications as an attacker would - through external interfaces. Understanding this process helps teams evaluate tool capabilities.
Discovery and crawling: The tool first maps the attack surface. It crawls pages, identifies endpoints, and discovers API routes. Advanced tools do this automatically. Outdated legacy tools often require manual configuration.
Attack simulation: Once mapped, the tool sends malicious payloads designed to trigger vulnerabilities. These include injection attacks, authentication bypass attempts, and business logic manipulation. DAST tools automate security tests by following best practices in attack methodology.
Response analysis: The tool analyzes responses to determine if attacks succeeded. Proof-based scanning validates findings by confirming actual exploitation rather than pattern matching.
Feedback loop: Modern DAST tools use responses to inform subsequent test generation. They adapt attacks based on observed behavior. This feedback-driven approach finds security issues that static analysis misses.
Why you need a DAST tool
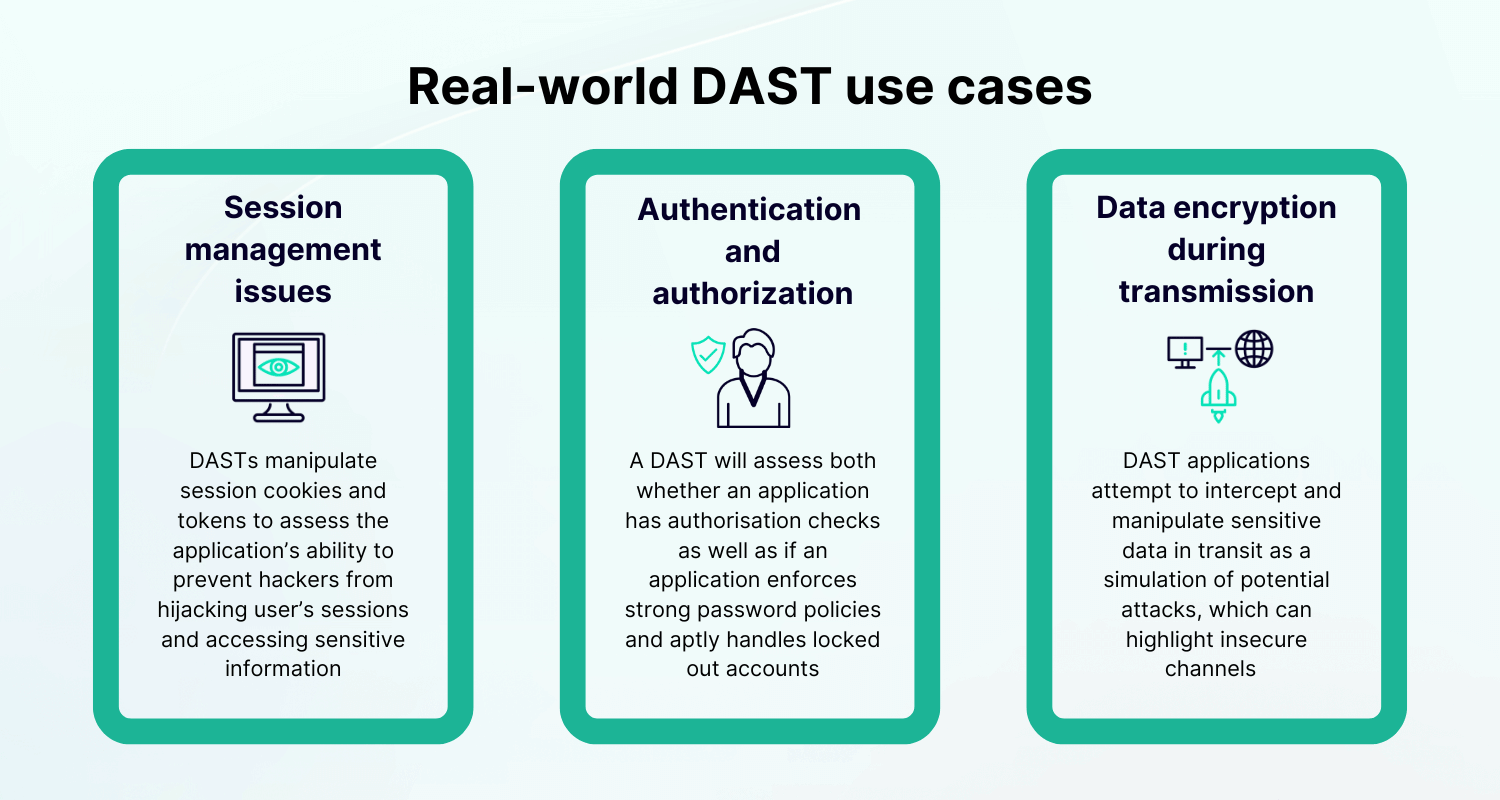
DAST tools are essential for identifying vulnerabilities from an "outside-in" perspective. DAST combines with SAST tools and SCA for comprehensive vulnerability detection across the SDLC.
Vulnerabilities can be remediated before an application goes live. This lowers breach risk and makes fixes cheaper. DAST also helps with end-user experience issues and facilitates regulatory compliance. We recommend integrating DAST into your security program early.
Real-world use cases where DAST delivers value:
- Security testing in CI/CD pipelines
- API security testing
- Business logic vulnerability detection
- Compliance and audit readiness
DAST limitations: what DAST cannot do
No security tool provides complete coverage. Understanding DAST limitations helps teams build comprehensive security programs.
Source code blindness: DAST tests running applications without source code access. It cannot identify insecure coding patterns, or vulnerabilities in unexercised code paths. SAST tools address this gap.
Running application requirement: DAST requires applications to be deployed and accessible. Integrate DAST into staging environments to test pre-production or add a private location proxy to test internal applications before they’re deployed externally.
Coverage limitations: Some security issues are difficult for DAST to detect. Race conditions, certain cryptographic weaknesses, and timing-dependent vulnerabilities are examples. Penetration testing complements DAST here.
Authentication complexity: Modern DAST tools handle complex authentication better than outdated legacy solutions. Highly customized authentication schemes may still require manual configuration.
The solution is defense in depth. Combine DAST with SAST tools, SCA, and periodic penetration testing. No single tool replaces a layered security approach. Follow best practices to prevent threats by using multiple testing methods.
For deeper insights, see our webinar on combining SAST and DAST.
Getting started: implementing DAST in your organization
Selecting a DAST tool is only the first step. Successful implementation requires thoughtful rollout and process integration. Follow these best practices for effective deployment.
5 steps to your first DAST scan
Step 1: Identify critical applications Begin with applications handling sensitive data or exposed to the internet. Do not scan everything immediately. Prioritize based on risk to improve your security posture.
Step 2: Configure authentication Most meaningful vulnerabilities hide behind authentication. Set up login credentials, session handling, and MFA requirements before scanning.
Step 3: Define scan scope Specify which endpoints and functionality to test. Exclude logout endpoints, data deletion functions, and production-impacting operations during initial testing.
Step 4: Run an initial scan Execute your first scan against a staging or pre-production environment. Review results for false positives. Tune configuration based on findings.
Step 5: Integrate into workflows Add DAST to CI/CD pipelines. Establish remediation workflows. Define severity thresholds for blocking deployments versus creating tickets.
CI/CD integration examples
GitHub Actions
---
name: Escape
on:
push:
branches:
- main
jobs:
Escape:
runs-on: ubuntu-latest
steps:
- name: Escape Scan
uses: Escape-Technologies/action@v0
with:
# application_id is deprecated, use profile_id instead
profile_id: ${{ secrets.ESCAPE_PROFILE_ID }}
api_key: ${{ secrets.ESCAPE_API_KEY }}
watch: "true" # to wait for scan completionJenkins:
pipeline {
agent { label 'alpine/curl:8.12.1' } // Use an alpine container
environment {
ESCAPE_APPLICATION_ID = credentials('ESCAPE_APPLICATION_ID')
ESCAPE_API_KEY = credentials('ESCAPE_API_KEY')
}
stages {
stage('Checkout') {
steps {
checkout scm // Checkout the codebase from the SCM provider
}
}
stage('Post-Deploy') {
when {
branch 'staging' // Only run on the 'staging' branch
}
steps {
script {
// Install the Escape CLI tool
sh 'curl -sf https://raw.githubusercontent.com/Escape-Technologies/cli/refs/heads/main/scripts/install.sh | sh'
// Show the installed Escape CLI version
sh 'escape-cli version'
// Run Escape action
sh 'escape-cli scan start ${ESCAPE_APPLICATION_ID} --watch'
}
}
post {
always {
// Configuration to allow failure
}
}
}
}
}For comprehensive guidance, see our complete guide to implementing DAST in CI/CD pipelines.
Common mistakes to avoid
Scanning production without safeguards: DAST tools send attack payloads. Configure exclusions for destructive operations. Prefer staging environments for initial testing.
Ignoring authentication setup: Unauthenticated scans miss most vulnerabilities. Invest time in proper authentication configuration before evaluating results.
Treating all findings equally: Not every vulnerability requires immediate attention. Prioritize by exploitability and business impact. Focus on security flaws that pose real risk.
Scanning without developer buy-in: Security tools developers resist do not get used. Involve engineering teams in tool selection to ensure adoption. Follow best practices to prevent threats through collaboration.
Success metrics
Measure DAST program effectiveness:
- Mean Time to Remediation: How quickly vulnerabilities get fixed
- Vulnerability Escape Rate: Security issues found in production that DAST should have caught
- False Positive Rate: Time wasted investigating non-issues
- Scan Coverage: Percentage of applications with active DAST scanning
- Developer Adoption: Percentage of teams using DAST in pipelines
For automation strategies, explore our guide on automating penetration testing.
The future of DAST: 2026 trends
DAST continues evolving to address emerging threats and modern development practices. The cybersecurity landscape demands continuous adaptation.
AI-powered scanning: Machine learning enhances vulnerability detection. AI generates context-aware attack payloads and reduces false positives. Tools adapt testing strategies based on observed behavior.
Agentic pentesting: Autonomous agents chain vulnerabilities, maintain state across interactions, and think like human attackers. This approach finds complex security flaws requiring multi-step exploitation.
API-first architectures: Applications become collections of microservices. DAST tools must natively understand API protocols beyond REST. GraphQL, gRPC, and event-driven architectures require specialized testing.
Shift-left integration: DAST moves earlier in development lifecycles. IDE plugins and pre-commit scanning become standard. The goal is finding vulnerable code before it reaches shared environments.
Choosing the right DAST tool for 2026
For modern stacks - especially APIs, SPAs, and CI/CD-native workflows - your priorities are clear: low false positives, business logic flaw coverage, and seamless developer integration.
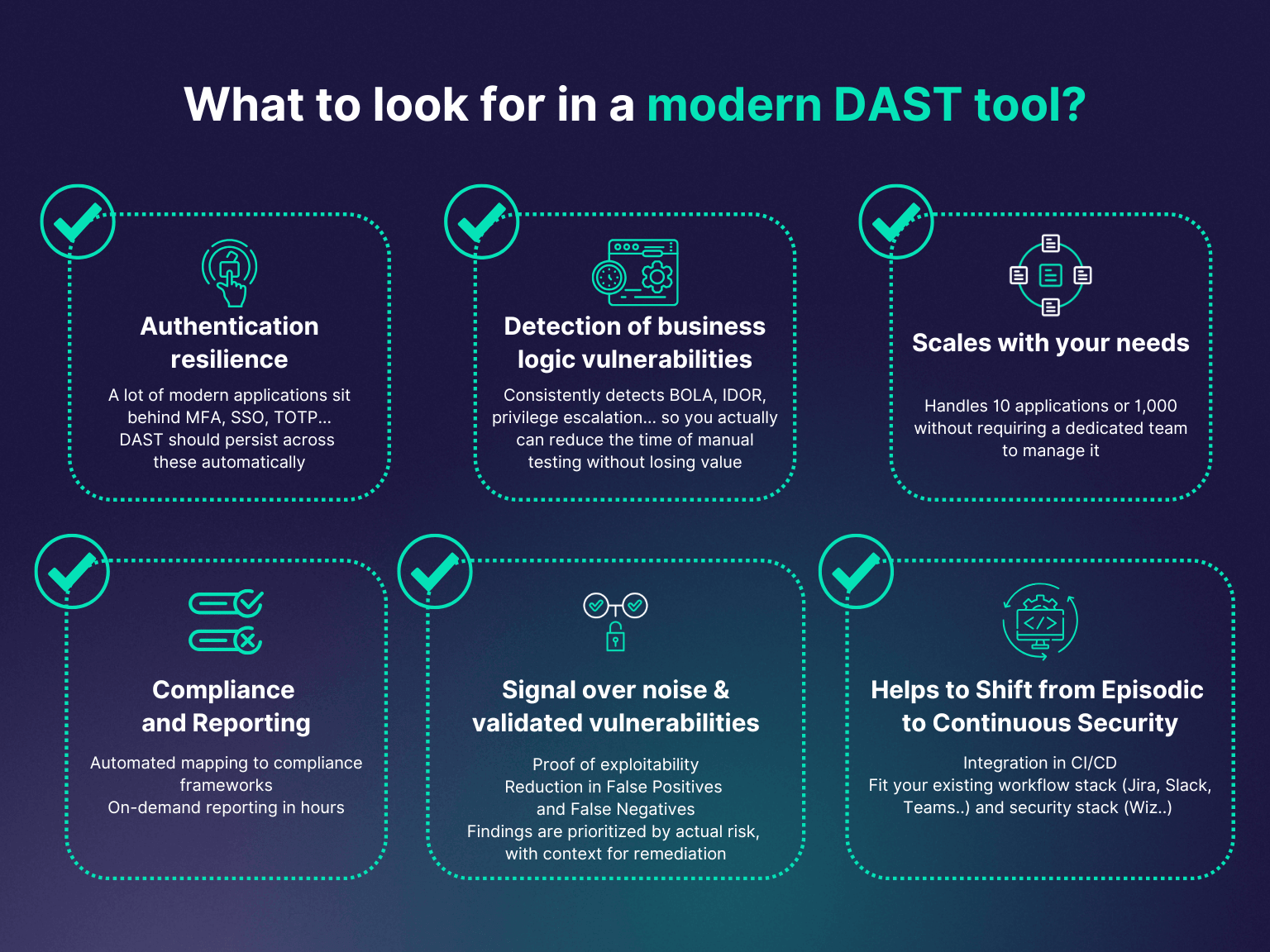
Legacy DAST scanners fall short. Tools like Escape are built for today's AppSec challenges. They offer comprehensive vulnerability detection, instant CI/CD feedback, and testing that matches how attackers operate.
The right choice depends on your context: team size, application architecture, compliance requirements, and existing toolchain. Use the selection framework and use-case recommendations in this guide to narrow options. Then conduct hands-on evaluations with your actual applications.
Security is an ongoing capability. Choose a DAST tool that grows with your organization and strengthens your security posture against emerging threats. With Gartner projecting security spending to reach $240 billion by 2026, and the Verizon 2025 DBIR showing that third-party breaches have doubled year-over-year to 30% of all incidents, investing in robust application security testing is no longer optional—it's a business imperative. According to IBM's 2025 Cost of a Data Breach Report, organizations using security AI and automation save nearly $1.9 million per breach on average. We recommend starting your evaluation today.
See how Escape DAST compares to traditional DAST tools - book a live demo with a product expert who understands your architecture and security needs
Get a demoFAQ
💡 Want to discover more about DAST? Check out the following links:
- DAST is dead, why Business Logic Security Testing takes center stage
- We benchmarked DAST products, and this is what we learned
- The Elephant in AppSec Podcast⎥ Lack of effective DAST tools⎥ Aleksandr Krasnov (Meta, Thinkific, Dropbox)
- Reinventing API security: Why Escape is better than traditional DAST tools
- Escape DAST - Your Detectify Alternative

