Introducing Kubernetes Integration: Discover APIs in Kubernetes
Identify undocumented and potentially vulnerable APIs in your Kubernetes clusters with ease.
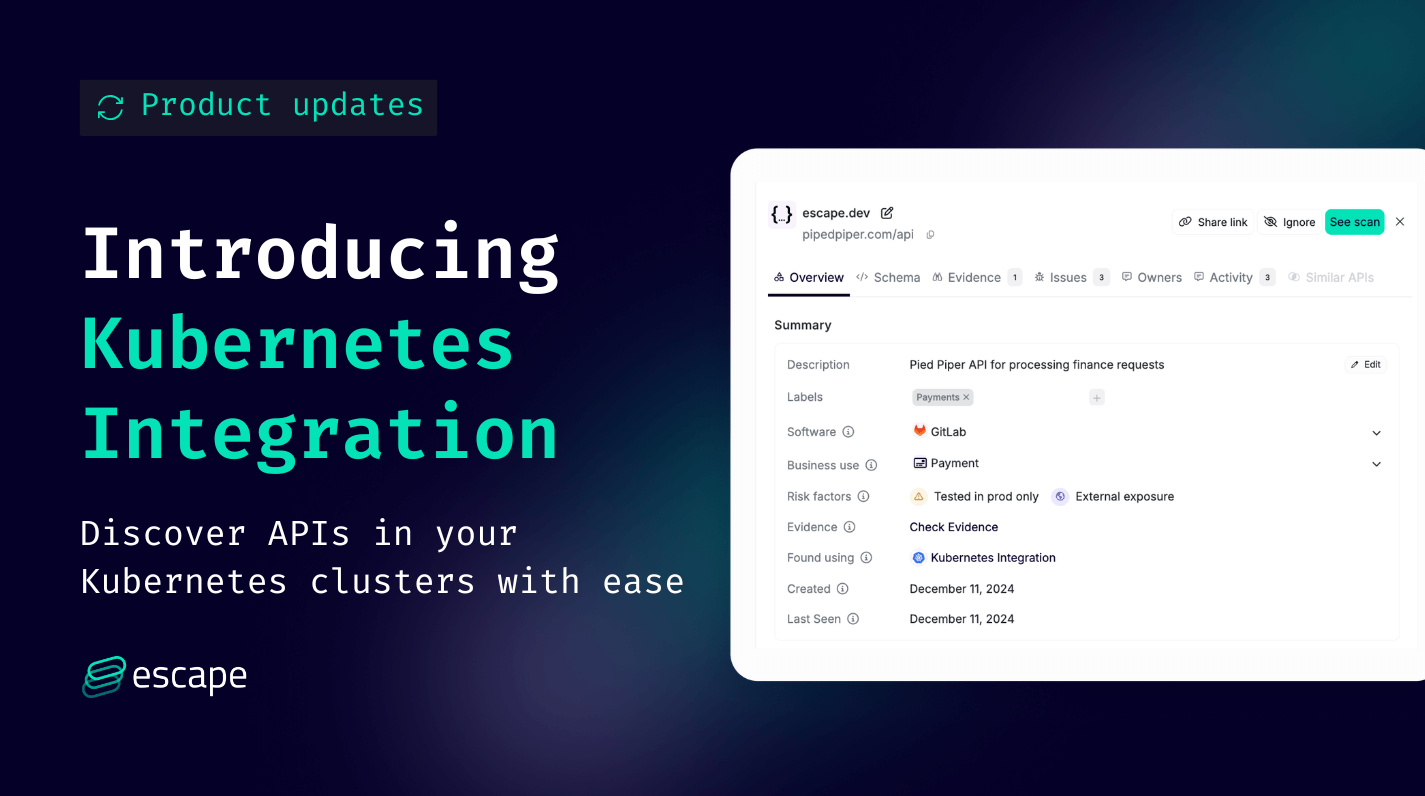
As organizations scale their Kubernetes deployments, the number of services and APIs grows rapidly. Maintaining visibility into these resources is critical for securing the API attack surface and ensuring compliance.
Escape now supports Kubernetes integration, enabling users to discover services running in their Kubernetes clusters.
This integration simplifies the process of discovering both documented and shadow APIs within your clusters, reducing operational risks and improving API governance.
How it works?
Escape will read the services and ingresses defined in your cluster.
These resources will be tested to determine if these are APIs. If that's the case, you can see them in the All Services section of the Escape's Inventory.
Importance of API Visibility in Kubernetes
Kubernetes is the backbone of modern cloud-native applications, orchestrating microservices at scale. However, the dynamic nature of Kubernetes makes it challenging to maintain an up-to-date inventory of exposed API services.
"As an industry, we're in a quest for agility and ability for developers to deliver value to the company as fast as possible. Kubernetes helps that be very, very fast. We now have the ability where we can go from a code repository to a deployed application within seconds. In this quest for efficiency, I think there is also the blind spot of assumption that Kubernetes is safe by default. And I think that is a very problematic assumption because Kubernetes is not safe by default. Kubernetes is very open spec by default. " - Raunaq Aurora, Lead Application Security Engineer at Chipotle
With Escape’s Kubernetes integration, you can:
- Gain frequent visibility into APIs in your Kubernetes clusters
- Identify undocumented and potentially vulnerable APIs
- Reduce risks associated with them
By enabling visibility, organizations can address API sprawl and reduce security blind spots.
Getting started
Step 1: Set Up a Private Location
You need to configure a Private Location as a Kubernetes deployment for Escape to interact with your cluster.
Step 2: Create Service Account and ClusterRoleBinding
To allow this deployment to access resources in your Kubernetes cluster, you need to create a Service Account and a ClusterRoleBinding.
You can use the sample YAML below to create these authorizations (replace default with the right namespace if needed).
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: escape-repeater
namespace: default
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: escape-repeater
rules:
- apiGroups: [""]
resources: ["namespaces"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["services"]
verbs: ["get", "list"]
- apiGroups: ["networking.k8s.io"]
resources: ["ingresses"]
verbs: ["get", "list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: escape-repeater
subjects:
- kind: ServiceAccount
name: escape-repeater
namespace: default # the namespace where the ServiceAccount is created
roleRef:
kind: ClusterRole
name: escape-repeater
apiGroup: rbac.authorization.k8s.ioStep 3: Bind the Service Account
Add the following line to the spec section of your deployment YAML to bind the Service Account to the pod: serviceAccountName: escape-repeater
Step 4: Monitor Discovered APIs
Once the integration is enabled, Escape will automatically identify and display APIs in the services section of your inventory, allowing you to take further actions like securing, auditing, or analyzing them.
For more details and step-by-step guidance, check out our Kubernetes Integration documentation.
With these new updates, you should be able to discover your APIs in your Kubernetes clusters with ease. Try it out for yourself, and let us know what you think in our Slack community!
