Escape vs Noname Security (Akamai): Complete 2025 Comparison
Discover how Escape helps implementing API Security faster and with lower overhead than traffic-based solutions like Noname Security.

Noname (recently acquired by Akamai) has been a major player in the API security market for the past couple of years. However, security professionals have voiced their frustrations with the solution for several reasons:
- Complicated and slow to deploy. Noname security requires capturing traffic by integrating all production environments, like gateways, reverse proxies, and CDNs. This requires having an accurate inventory of exposed API environments in the first place, which almost no organization has. Integrating anything in production also often requires multiple layers of approval from different teams. This step alone can take months to years in large organizations.
- False positive rate. Noname security attempts to detect attacks in real-time by identifying outliers from legitimate API traffic. In practice, most outliers are not cyberattacks, which leads to a high number of false positives.
- Lack of Security by Design capabilities. Noname security has been designed with network security engineers in mind, not with developers. Thus, the solution has only basic capabilities to shift API security left and doesn't help organizations implement Secure by Design principles for API Security.
We at Escape attempted to create an alternative that would overcome those limitations and empower Application Security teams to have the visibility and security they deserve for their APIs. To overcome those limitations, we invented an entirely new approach that is not based on the observation of API traffic.
- Effortless setup: discover all your APIs literally in minutes. Thanks to Escape's in-house API discovery intelligence engine, based on source code analysis and network discovery rather than traffic analysis, Escape can provide an accurate inventory of all your internal and external APIs in minutes and with near-zero integration effort.
- See what is relevant and strip noise. We designed the first Feedback-Driven API Exploration engine to detect API vulnerabilities with an extra low false positive rate. We correlate results with your API inventory to prioritize risks and show you only what matters in an actionable format.
- Empower your developers to adopt API security by design at an unprecedented scale. Escape has been built with Security Engineers and Developers in mind. All issues come with remediation code fixes that are compatible with your technology stack. Both CI/CD integrations and pipelineless security options are available. The whole platform is customizable and automatable.
When it comes to API discovery and security, choosing the right tool can significantly impact your organization's ability to protect its sensitive data.
Below you’ll find an in-depth comparison between Escape and Noname Security across the entire API security workflow - from API discovery to remediation. We focused on key differences between those two tools. If you want to get a quick recap and an infographic that you can download and share with others, jump to the last section.
As Noname doesn't have publically accessible documentation, we've built this comparison based on the following sources:
- Noname official website
- Noname publically accessible demos on YouTube
- Feedback from security professionals (whether Noname's and Escape's current customers or not)
- Feedback from an independent industry analyst
TLDR: Noname Security vs Escape
Side-by-side comparison table
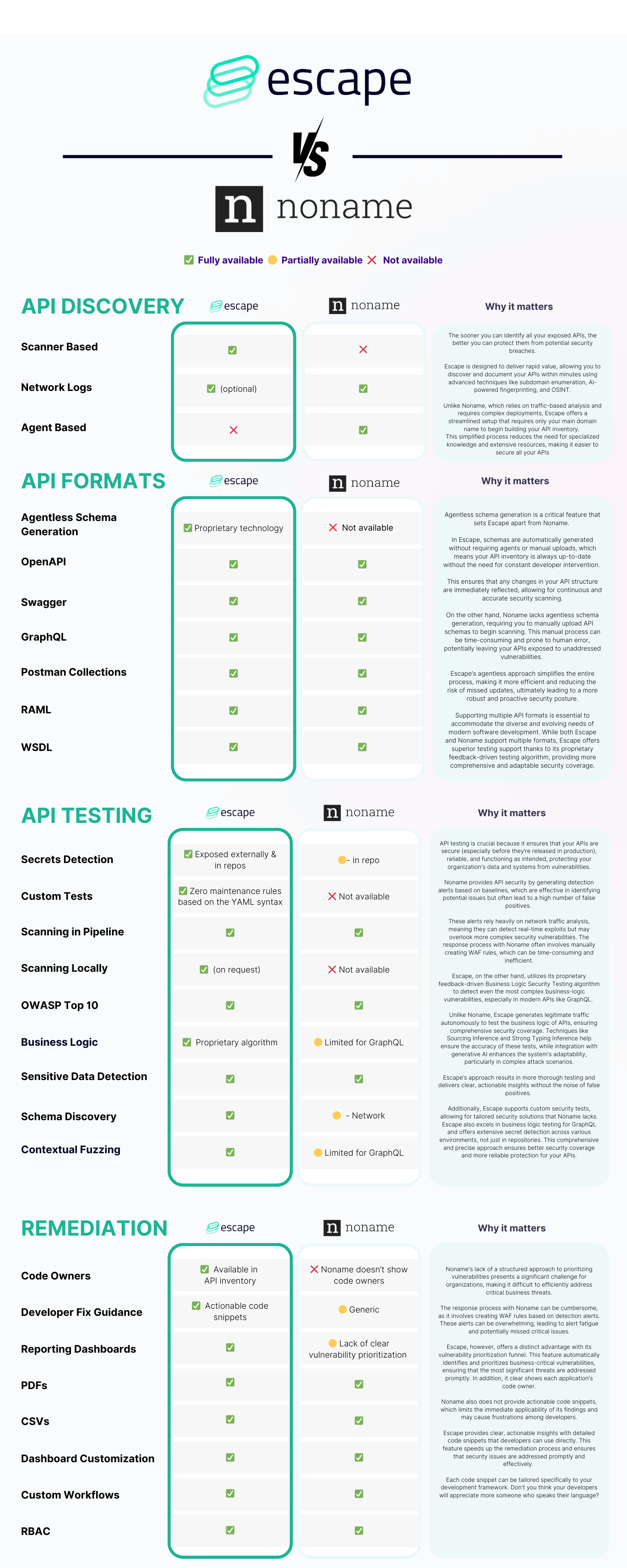
Noname Security
Pros
- Easy to understand for network engineers (though the learning curve might be steeper for security engineers with other backgrounds)
- Focuses strongly on helping to ensure regulatory compliance.
- Since they’re looking at API traffic, they’re able to detect exploits in runtime, but it only helps to adapt a reactive approach.
- The findings from Noname may appear to be real detection events, but they are often quite basic, such as merely checking if an authentication header is present.
- Noname covers a broad range of API types.
Cons
- Setup time: The customization process can be time-consuming, requiring more upfront investment in setup. Testing requires full application deployment first, as well as ingesting logs from your staging or lower environments.
- If your primary concern is detecting APIs, being reliant on network logs doesn’t really solve your problem, as it requires them to be behind your normal network flows in the first place! This is because network logs can only capture traffic that is actively passing through your network. Therefore, they can only detect APIs that are already being used and generating traffic. You're at risk of missing exposed and vulnerable Shadow APIs.
- Detection alerts are heavily based on baselines, which makes them very noisy and full of false positives.
- Testing requires manually uploading schemas when they change - it doesn’t automatically detect them.
- Response actions are incredibly cumbersome - you get drowned in these alerts and then respond by building WAF rules.
- You can't accelerate the remediation process because of the lack of actionable remediation code snippets for developers.
Escape
Pros
- Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
- Automated schema generation that helps you to launch scans right away and reduces the need for maintenance
- In-depth GraphQL testing capabilities and lowest false-positive rate
- Ability to prioritize the most critical API by business context, data sensitivity, and exposure.
- Actionable remediation code snippets for developers that help you build better relationships with them
- Effortless custom checks integration to automate security tests tailored to specific APIs
Cons
- Advanced feature sets may require specialized knowledge
- Number of integrations with some of the operational tools
Learn more about Escape
Schedule a time with our product expert to see for yourself how Escape simpliies API discovery and identifies even complex business logic vulnerabilities in your APIs
Get a demoIn-depth comparison: Noname Security vs Escape
API Discovery
You can't secure what you can't see, so the faster you get to see what are the APIs exposed on the internet, the more you reduce the risk of API security breaches.
Escape is built to help you get the value out of it in the shortest time possible. It allows you to discover your APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This ensures that all APIs, including those not actively in use, are discovered and documented.
Noname relies heavily on traffic-based analysis for API discovery. This method examines network logs to identify APIs, which means it can only detect APIs that are already part of your network traffic. This approach can miss dormant APIs or those not frequently accessed, for example, located outside of API gateways, WAFs or proxies, leading to incomplete visibility.
And it's not that easy to deploy. To be able to start discovering APIs with Noname, you need to deploy Integrated Engine and potentially Remote Engine that can inspect API traffic. Noname has a large ecosystem of integrations, but you don't want to wait till you can plug the ones you need.
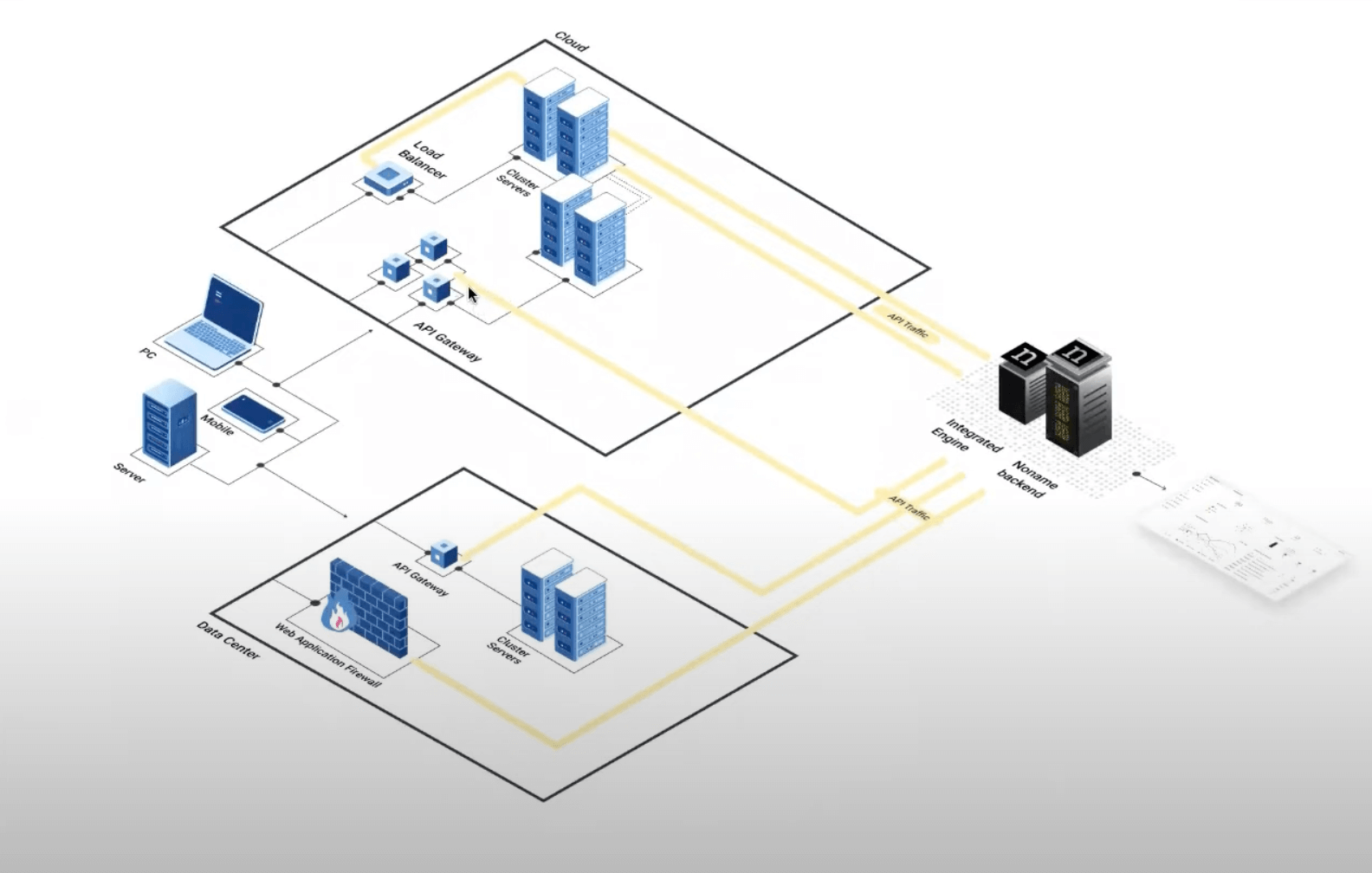
With Escape, to get started all you need is to put in your main domain name, so you can build inventory without any intervention from the development team, which is not necessarily the case when you need to deploy traffic-based API discovery tool. Simplified deployment processes minimize the need for specialized knowledge and extensive internal resources.
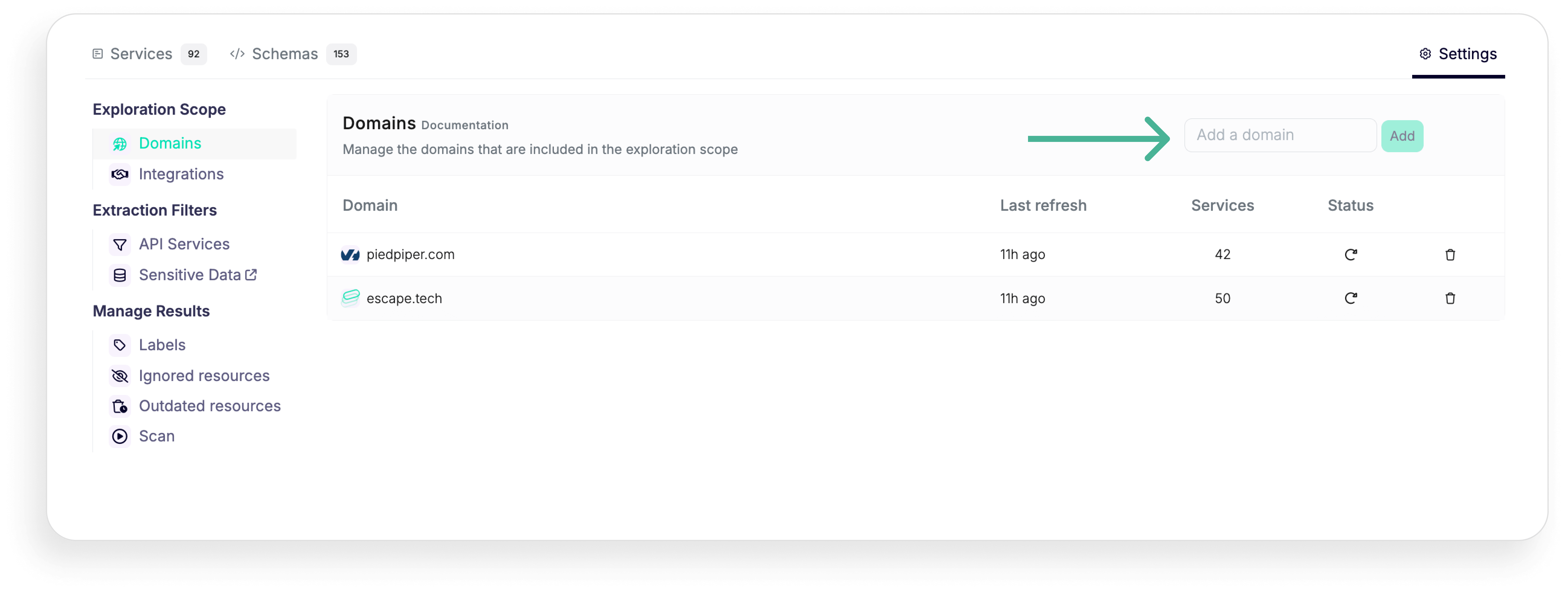
Once you've discovered all your exposed APIs, you can enrich the data discovered and classified in API inventory by connecting with your developer tools like Postman, GitHub, and GitLab, cloud platforms like AWS and Azure and gateways like Apigee, Axway, Kong Gateway and Kong Connect and Mulesoft. To scan internal APIs behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
Discover your APIs in minutes
Establish API governance with Escape: ongoing discovery, inventory, and security of your most critical APIs.
Get a demoAPI Security
Once discovery is done, it comes down to API security testing.
Noname requires manual upload of API schemas to start scans as they precise in this demo, as it doesn't automatically generate schemas. In contrast, Escape uses a proprietary machine learning algorithm to automatically reconstruct API schemas, enabling context-aware scanning that can be initiated right away.
Noname provides API security by generating detection alerts based on baselines. These alerts can be effective in demonstrating potential issues but often result in a high number of false positives. The alerts are primarily based on network traffic analysis, which means they can detect exploits in real-time but might miss more nuanced security issues. Response actions often involve manual WAF rule creation, which can be time-consuming and inefficient.
Escape relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in modern API types like GraphQL. Escape's algortihm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Escape’s testing is more thorough and provides clear, actionable insights without the noise of false positives.
Testing Capabilities
Noname’s testing capabilities are limited and often require full application deployment. It does not support custom security tests, which can be a drawback for organizations needing tailored security solutions.
Additionally, its business logic testing for GraphQL is limited, and secret detection is only available in repositories.
Escape offers extensive testing capabilities, including custom security tests. These features allow for more detailed and specific security assessments, tailored to your unique needs.

Escape’s business logic testing for GraphQL is robust, and it includes comprehensive secret detection across various environments, not just repositories. Here is the full list of secrets that can be detected by Escape.
This thorough approach ensures better security coverage and more reliable protection.
Response and Actionable Insights
One significant issue with Noname is its lack of a structured approach to prioritizing vulnerabilities.
Without a clear system for ranking vulnerabilities based on their business impact, organizations may find it challenging to determine which threats to address first, leading to inefficient use of resources and potential oversight of critical issues. The response process with Noname can be cumbersome, as it involves creating WAF rules based on detection alerts. These alerts can be overwhelming, leading to alert fatigue and potentially missed critical issues.
Escape, however, offers a distinct advantage with its vulnerability prioritization funnel. This feature automatically identifies and prioritizes business-critical vulnerabilities, ensuring that the most significant threats are addressed promptly. In addition, it clear shows each application's code owner.
By streamlining the prioritization process, Escape enables security teams to focus their efforts where they matter most, enhancing overall security and providing peace of mind that critical vulnerabilities are being effectively managed.
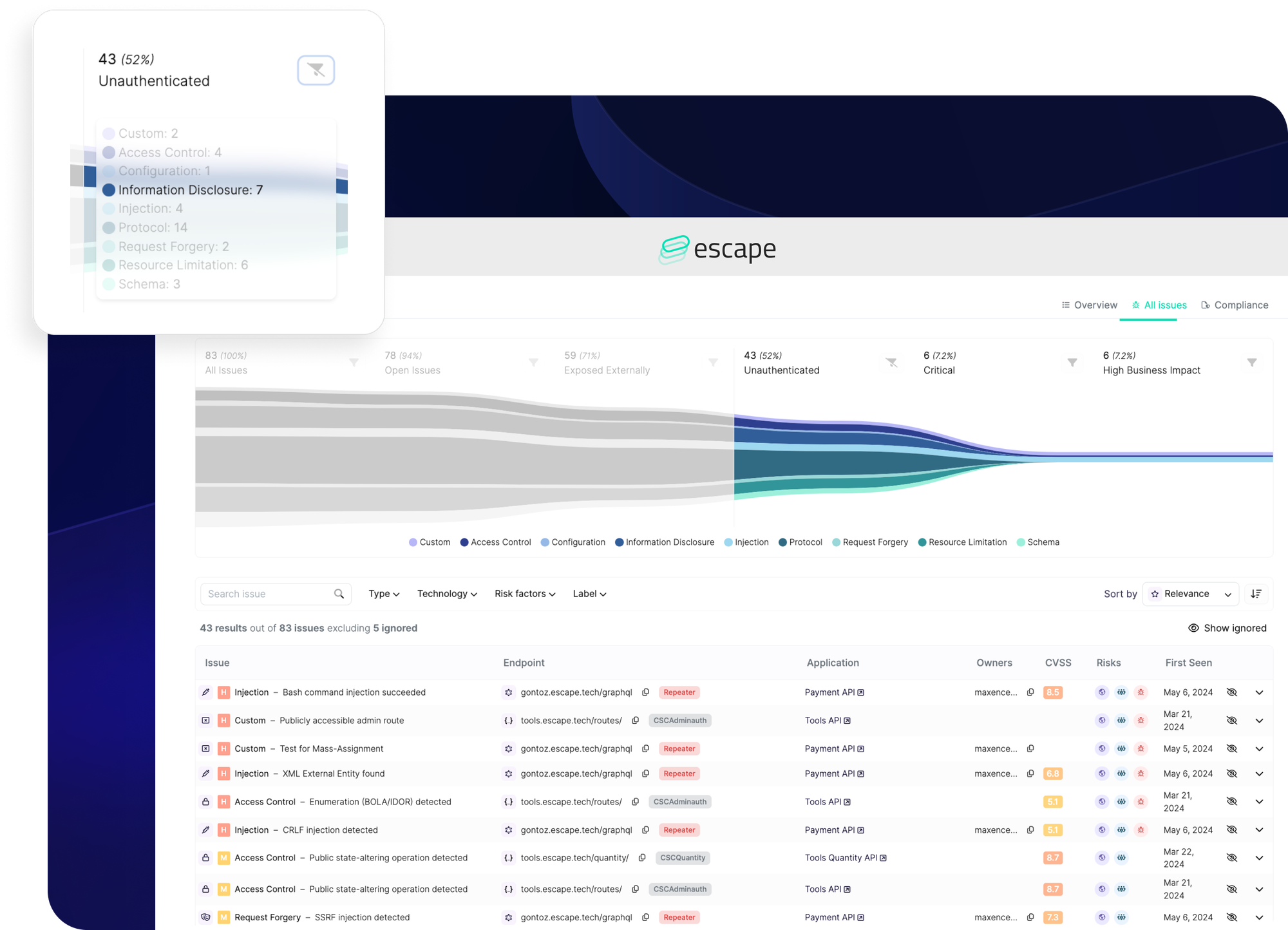
Noname also does not provide actionable code snippets, which limits the immediate applicability of its findings and may cause frustrations among developers.
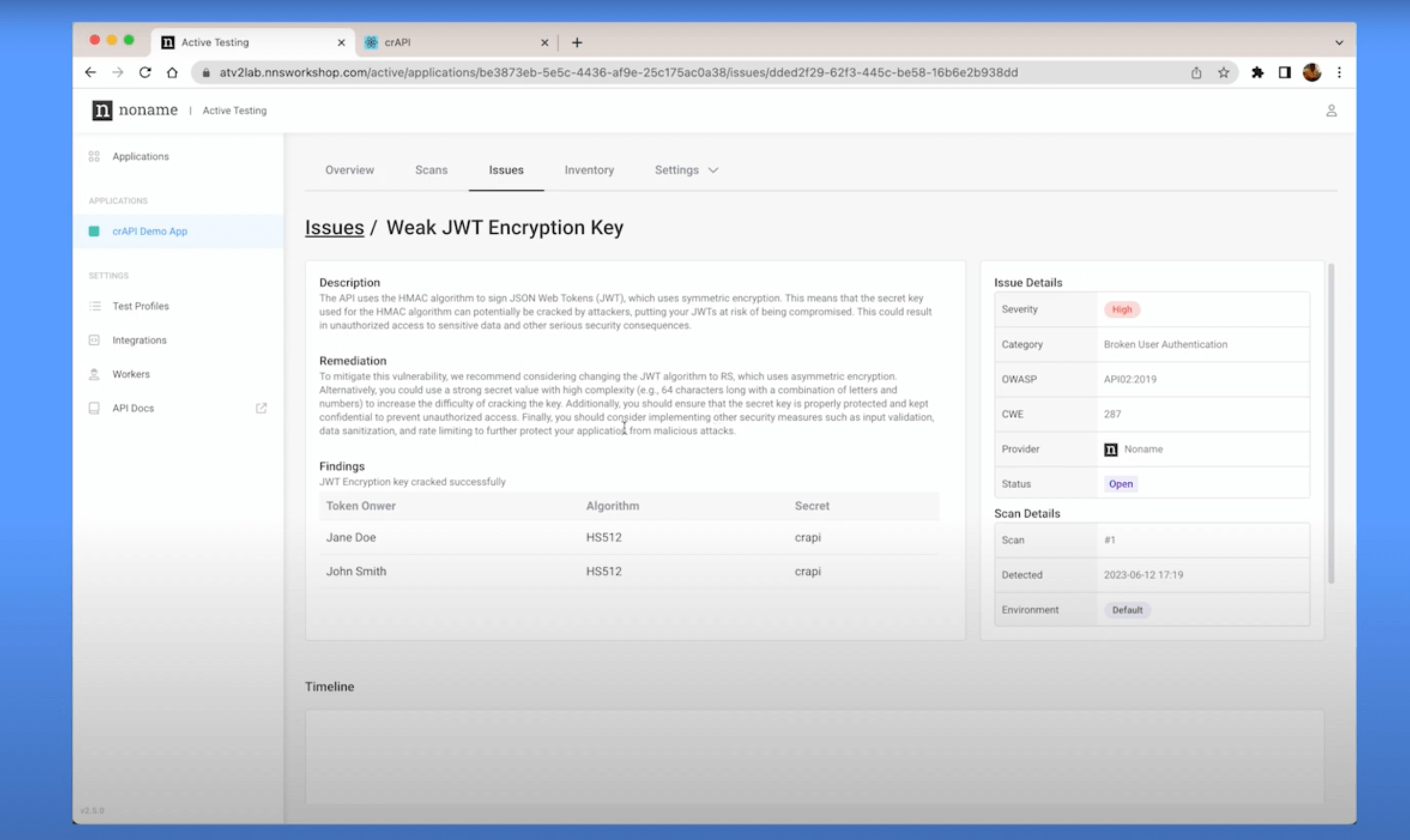
Escape provides clear, actionable insights with detailed code snippets that developers can use directly. This feature speeds up the remediation process and ensures that security issues are addressed promptly and effectively.
Each code snippet can be tailored specifically to your development framework. Don't you think your developers will appreciate more someone who speaks their language?

Ease of Use and Integration
It's important, of course, that once deployed, it's easy to use the tool.
Noname’s system is straightforward for network engineers to understand and implement. However, it requires a complete application deployment and manual log ingestion from staging environments. Changes in schemas need to be manually uploaded, adding to the administrative burden. The tool also lacks features like actionable code snippets, which can limit its usability and integration with modern development workflows. So, even in the long run, combination of all of this manual work can lead to a lot of frustrations.
Escape stands out with its user-friendly interface and automated processes. It does not require manual schema uploads or extensive setup procedures. The tool integrates seamlessly with existing workflows, providing continuous and automatic updates to schemas and security tests. Escape’s agentless schema generation and actionable remediation code snippets make it a more efficient and effective tool for maintaining API security.
Conclusion
While Noname offers a solid traffic-based API discovery and security solution, it falls short in several key areas such as comprehensive API discovery, detailed testing capabilities, and actionable remediation.
The Akamai acquisition makes total sense because it’s bolstering their API WAF capabilities; however, their testing was already very manual and unusable, and being acquired has never made anyone work faster. Most companies using something like Noname Security still buy something like Escape as an addition because the testing and discovery capabilities are so weak. Thus, you can avoid this by simply integrating Escape right away into your API security program.
Escape provides a more holistic and automated approach to API discovery and security. Its focus is on agentless API discovery, automated schema generation, advanced security testing, and actionable insights for developers.
If you still have doubts, take a moment with our team and see directly during a demo what APIs your organization left exposed.
Learn more about Escape
Schedule a time with our product expert to see for yourself how Escape simpliies API discovery and identifies even complex business logic vulnerabilities in your APIs
Get a demo💡Want to learn more? Discover the following articles:
