Invicti DAST (formerly Netsparker) vs Escape DAST: 2026 Comparison
Explore why modern teams prefer Escape DAST over Invicti (formerly Netsparker DAST), weigh the advantages and disadvantages of both,and determine the best fit for you.

Invicti DAST (formerly Netsparker DAST) has established itself as a well-known security solution, primarily known for its capabilities in web application vulnerability scanning. They focused on helping organizations uncover common vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), and other web application flaws. However, while Invicti seems to be a good option for identifying vulnerabilities, they've been focusing heavily on scanning rather than comprehensive discovery, meaning its capabilities in asset and API discovery are somewhat limited. Also, while the Invicti tool identifies numerous issues, its findings are often not as actionable, leaving security teams with vulnerabilities that require considerable manual intervention to address effectively.
How can Escape create a better DAST & API security solution than Invicti DAST? We’ll let you decide if we’re better by comparing the value provided by the tool. In this article, we’ll explain why and what makes us different from Invicti.
Replace your legacy DAST
For teams that deploy modern apps and want deep business logic testing at scale
Below, you’ll find an in-depth comparison between Escape and Invicti across the entire security workflow - from building application inventory to scanning to remediation. We focused on key differences between those two tools. If you want to get a quick recap, jump to the last section.
We've built this comparison based on the following sources:
- Invicti's official website & product datasheets
- Invicti's documentation
- Invicti's publicly accessible demos on YouTube
- Feedback from security professionals
Recap: Invicti DAST (formerly Netsparker) vs Escape DAST
You can find side a side comparison between Escape DAST and Invicti below:

|

|
|
|---|---|---|
| Security Testing | Full API and web app scanning (internal & external) using proprietary AI-powered DAST with thousands of business-logic–aware attack scenarios. Supports multi-user testing and GraphQL natively. | Native DAST engine, with AI-enhanced fuzzing explored through experimental tools. Good support for web apps and basic support for APIs. |
| Authentication | Supports authentication mechanisms (OAuth, API keys, JWT, multi-factor auth, Playwright, custom auth workflows.. ). and its proprietary AI agent detects login fields and fills them in automatically, and pinpoints any failures during the process. | Supports authentication flows like OAuth 2.0, TOTP recording of a login sequence, and includes an automated mechanism that detects and handles standard login forms. No ability to debug and see where the authentication went wrong during scanning. |
| Testing in CI/CD | Easy native integration with multiple CI/CD pipelines | Integration with multiple CI/CD pipelines exists, but not always easy to implement (according to former customer feedback) |
| Testing via CLI | Open-source, single-binary CLI that enables managing app configs, integrations, scan locations, and running scans. Easy CI/CD integration. | CLI focused on enterprise-grade scanning automation with rich authentication, reporting, and customizable scan profiles. Integrations with major CI/CD tools. Windows-based CLI can be less flexible. | Application & API discovery | External discovery and internal discovery from code and through various connectors (Wiz, Akamai, AWS, Postman and others..) | Through network, existing cloud targets or integrations — dependent on existing documentation and visible endpoints. Multiple steps are required to achieve implementation. |
| Custom security tests, including from pentest results / incidents | Supports custom security tests that require no manual maintenance (support for both discovery and security testing) | Supports custom tests (require manual maintenance) |
| Triaging & Reporting | AI-based classification to reduce false positives, with severity scoring based on business context and exploitability. Advanced Jira integration, dashboards, reporting for compliance, available separately or in a unified view. | Offers customizable risk scoring and prioritization, but the single list of all critical alerts can be overwhelming. Provides rich reporting including executive summaries, compliance reports, and tight integration with ticketing systems. |
| Remediation Guidance | Delivers ready-to-merge code fixes tailored to each development framework | Provides generic recommendations on vulnerabilities |
Invicti
Pros:
- Supports various types of applications, including REST, SOAP, and GraphQL (to an extent) APIs, as well as traditional web applications.
- Part of the overall vulnerability scanning platform (ASPM) with SAST, IAST and SCA
- Supports various authentication options like OAuth 2.0, TOTP recording of a login sequence, and an automated mechanism that detects and handles standard login forms
- Includes custom security checks templates that help to customize security testing, but might require a lot of maintenance
Cons:
- Former users mentioned difficulties with CI/CD integration
- No ability to debug and see where the authentication went wrong during scanning
- Relies on existing API documentation, which limits the ability to discover undocumented or shadow APIs
- Limited number of security tests for business logic testing of modern application types and GraphQL, focused primarily on common vulnerabilities
- Doesn't have the ability to pinpoint code/application owners
- Does not provide dynamic feedback to adapt coverage automatically, relying more on manual review and configuration for improvements
Escape DAST
Pros:
- Full API and web app scanning (internal & external) using proprietary AI-powered DAST with thousands of business-logic–aware attack scenarios and support for multi-user testing
- In-depth GraphQL testing capabilities and lowest false-positive rate
- AI-powered exploit validation and generated remediation code snippets for developers that help you build better relationships with them
- Ability to prioritize the most critical applications by business context, data sensitivity, and exposure
- Supports even complex authentication scenarios and helps you to verify if they're set up correctly before launching the scans
- When complemented by the ASM feature, it provides an exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
Cons:
- Advanced feature sets like Custom Security Tests that may require specialized knowledge
- Number of integrations with some of the operational tools
Security Testing
The first point of comparison is the most important for DAST tools: the quality of security scans.
General overview
Invicti is strong when it comes to testing front-end apps and APIs, providing a good range of security checks for well-documented REST (and potentially SOAP or gRPC APIs, but it's hard to judge), such as injection flaws, authentication issues, and misconfigurations.
However, its capabilities are very limited for business logic security testing according to former users' feedback, meaning the exploitable complex risks might go unnoticed. It also lacks some flexibility when dealing with undocumented endpoints.
In contrast, Escape testing is more thorough, as it relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in SPAs and modern API types like GraphQL. Escape's algortihm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Both Invicti and Escape generate proof of exploit but their approaches differ.
Invicti's proof of exploit seems to be very limited to certain exploit types according to their documentation.
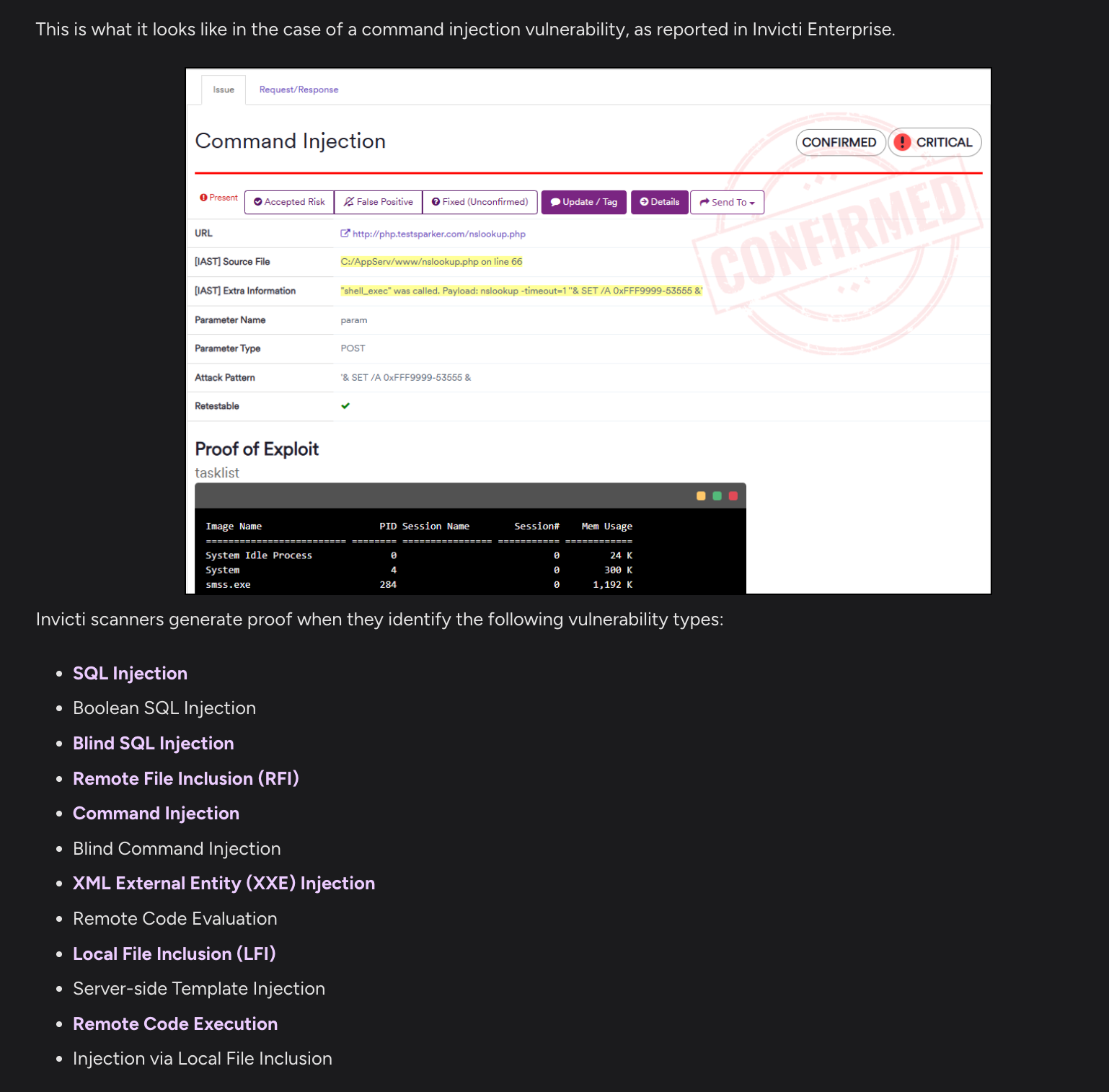
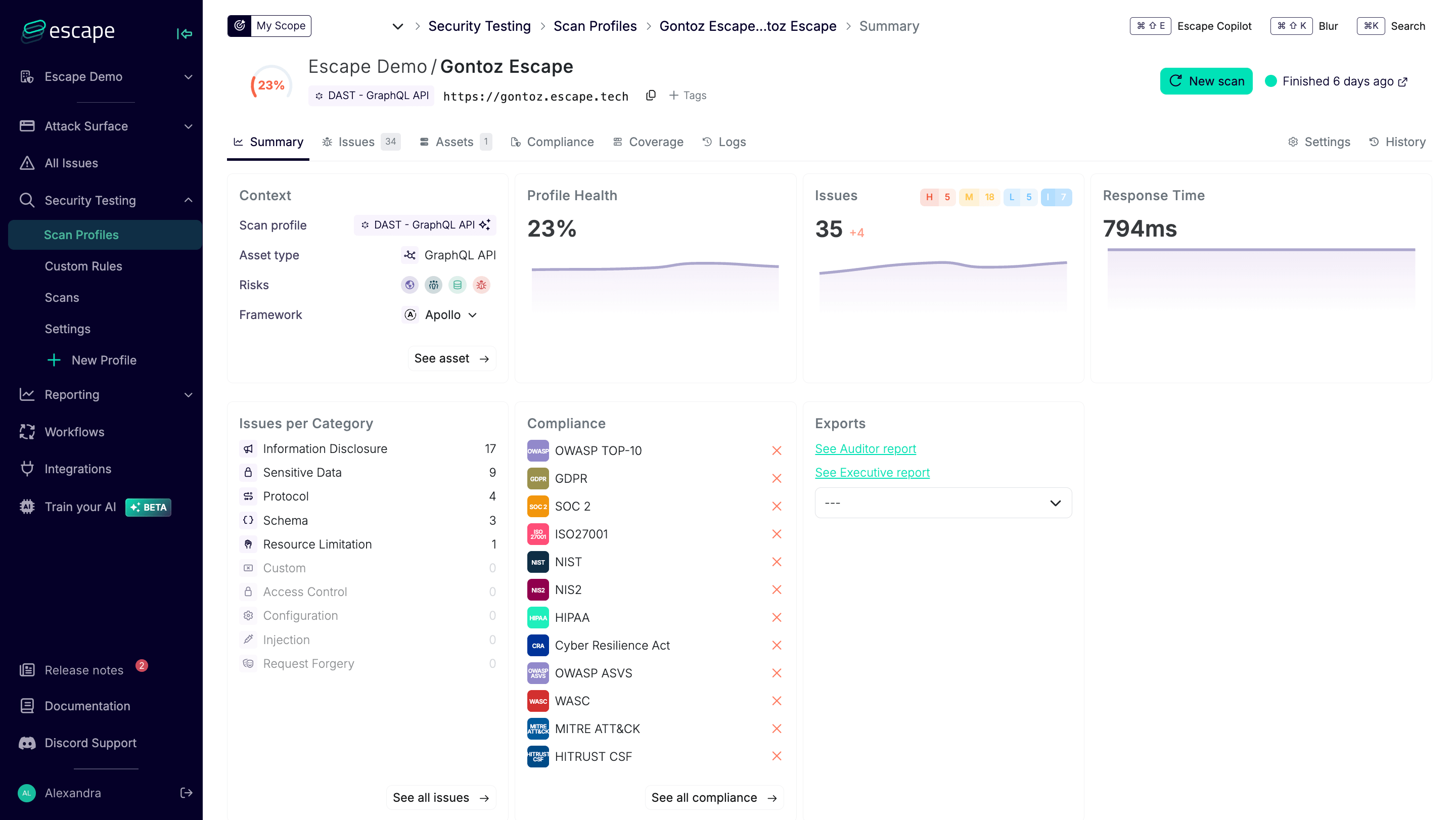
On contrast, Escape generates a very detailed proof of exploit without any limitations per vulnerability type, including and highlights whether the risks concern external facing asset, so altogether you can verify whether the surfaced vulnerabilities are actually exploitable.
Example for SSRF vulnerability triggered by the Referer header in a JavaScript (jQuery) environment
Schedule a time with Escape product expert to see for yourself how Escape DAST identifies even complex business logic vulnerabilities in your modern applications
Get a demoAuthentication
Escape supports a wide range of authentication mechanisms, including OAuth, API keys, JWT, multi-factor authentication, Playwright-based flows, and fully custom authentication workflows.
Its proprietary AI agent automatically detects login fields, fills them in during scans, and pinpoints exactly where authentication fails, making it easier to debug and fix issues. You can test the configuration before launching the scan, as you can see on the video below:
Test scan configuration in Escape
Invicti, on the other hand, supports common authentication flows such as OAuth 2.0 and TOTP by recording a login sequence and includes automation to detect and handle standard login forms. You have to set up an authentication profile separately and then add it during a new scan setup workflow, but it's not possible to follow one streamlined process from the start.
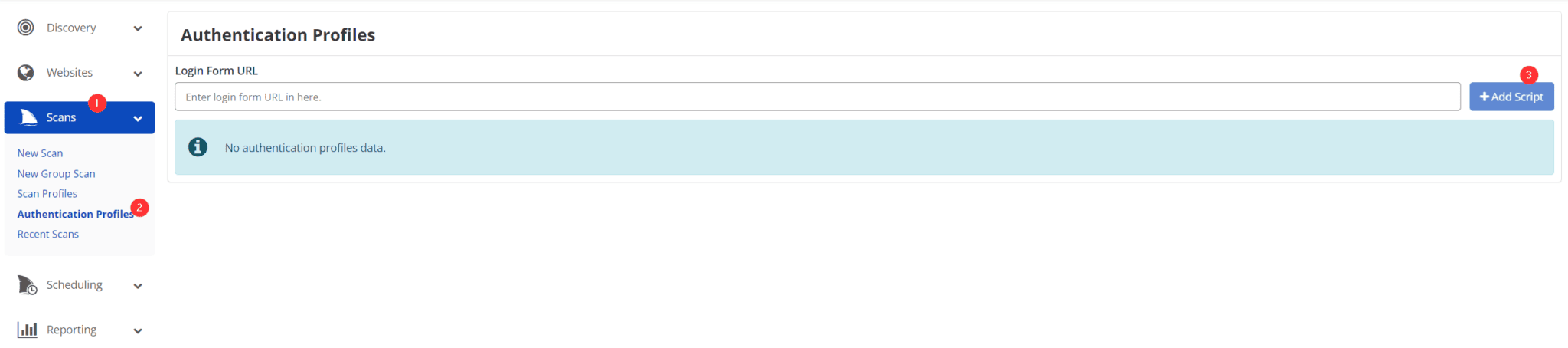
Invicit also does not provide visibility into where or why authentication fails during scanning, limiting troubleshooting capabilities.
GraphQL security
GraphQL, a query language for APIs, has gained significant traction in recent years due to its flexibility and efficiency.
Escape DAST has exceptional support for GraphQL Security Testing, integrating more than 100 GraphQL-specific tests, like aliasing and batching attacks, and even the most complicated access control issues.
Contrary to other scanners, Escape handles GraphQL natively and not as another HTTP API. Even better, our engine is capable of suggesting code fixes for all findings and all GraphQL engines to maximize developer productivity when fixing issues.
Escape r-elies on a powerful feedback-driven graph exploration algorithm that can explore and understand the business logic of your GraphQL API.
“Escape is an innovative tool, and its results and algorithms are truly impressive. It was able to find GraphQL vulnerabilities that their competitors haven't seen. It also provides me with extensive testing capabilities." - Pierre Charbel, Product Security Engineer, Lightspeed
On the other hand, according to their website, Invicti scans GraphQL for the following vulnerabilities:
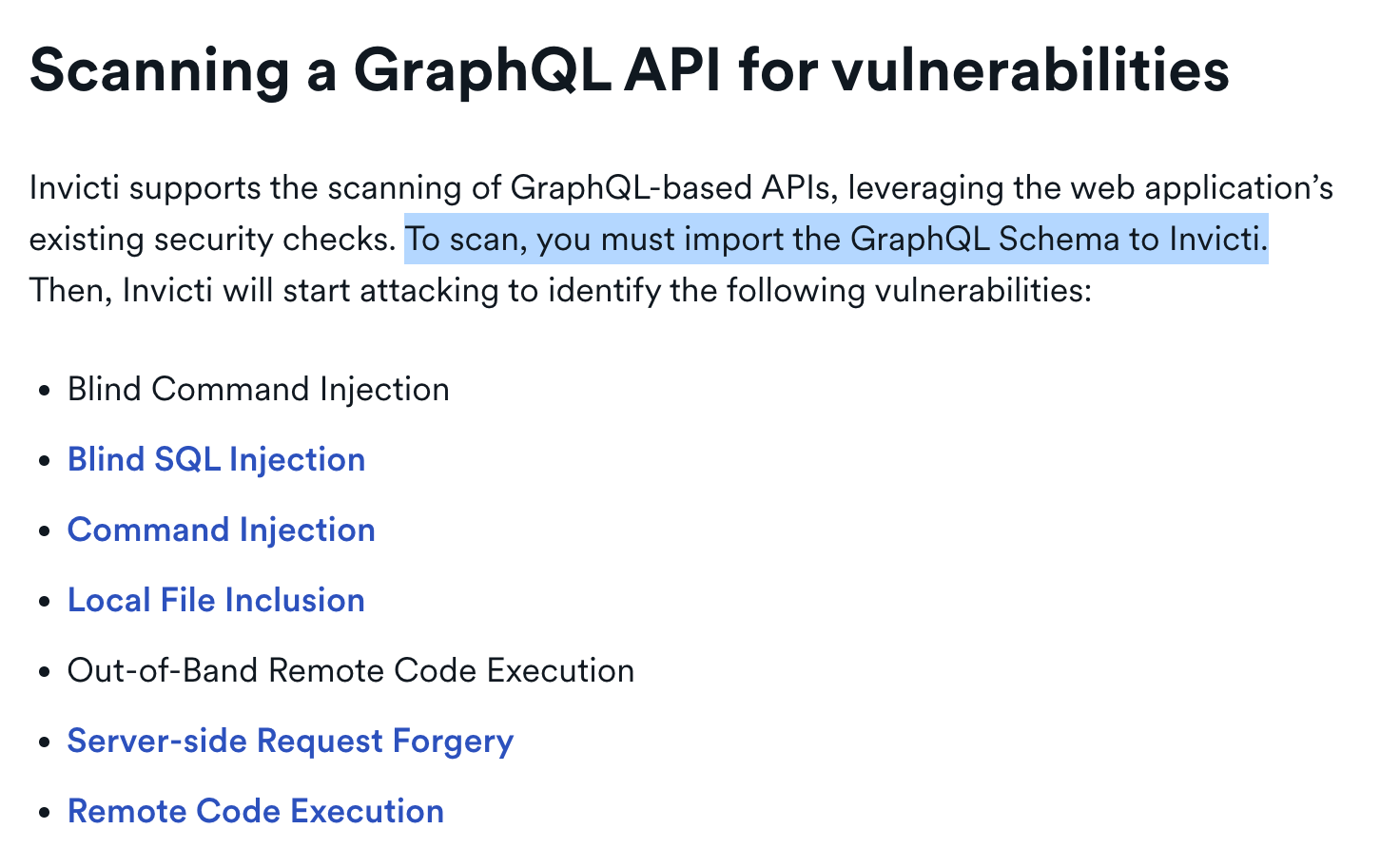
The number of checks available for GraphQL in Invicti is also constrained to the most common vulnerabilities like injections, which means its depth of testing does not cover all edge cases or advanced GraphQL-specific threats.
Coverage
Comprehensive coverage of DAST scanners is crucial because it ensures that all pages of a web app, endpoints of an API and data flows are thoroughly tested, reducing the risk of vulnerabilities being overlooked, which could lead to potential breaches.
Escape focuses on providing thorough and accurate coverage by leveraging its proprietary feedback-driven algorithms and detailed logs to support security teams in proving internally that the scanner actually crawled through a web app and API and found true positives that are actually exploitable (with even screenshots attached).
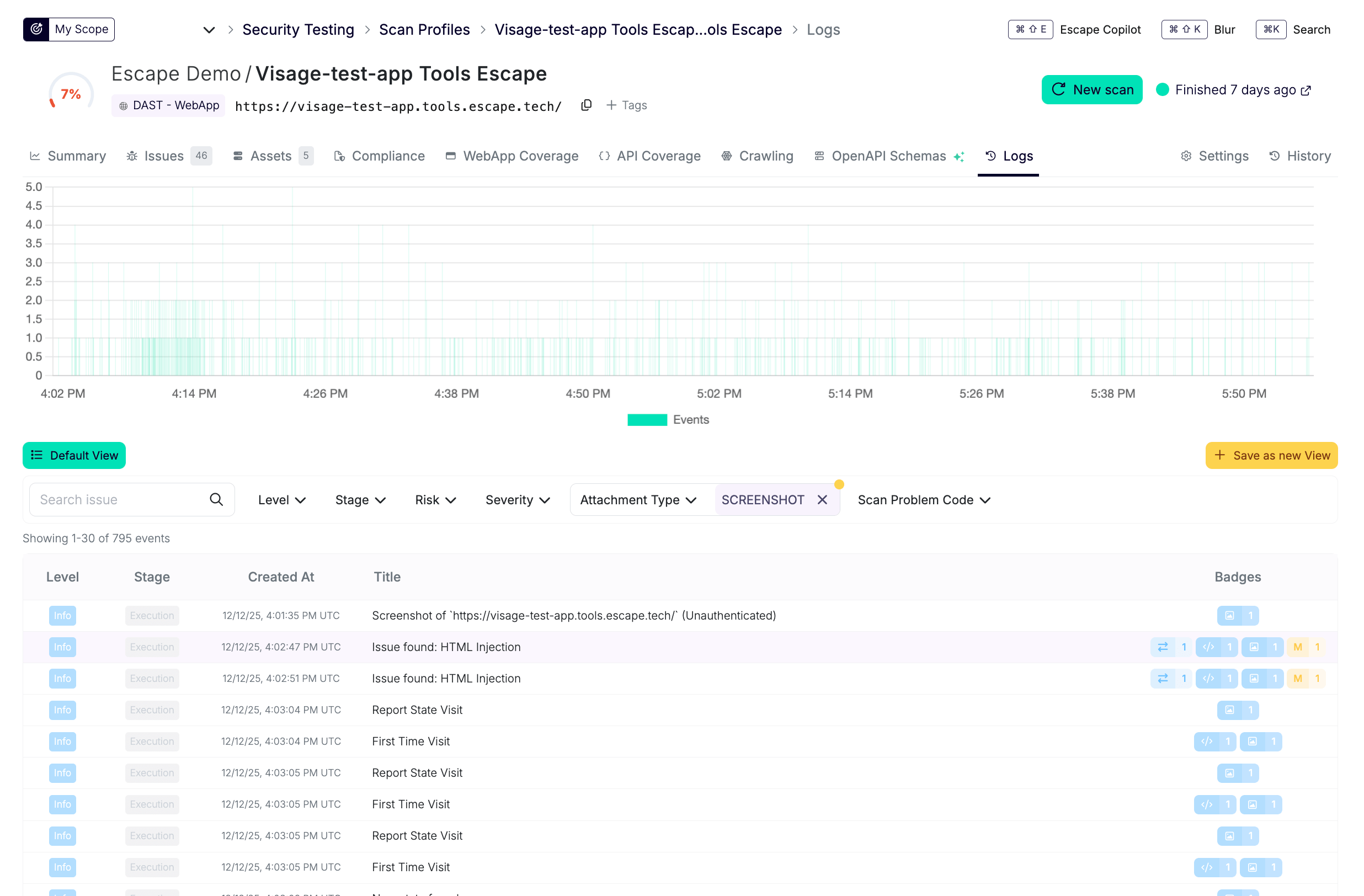
Escape's approach ensures that all potential attack surfaces are explored comprehensively, particularly in complex API types like GraphQL. Its logging and coverage mechanisms are designed to adapt dynamically, capturing detailed insights that are relevant and actionable for security teams.
If the app has associated APIs, API coverage is also included in the detailed logs of the web app.
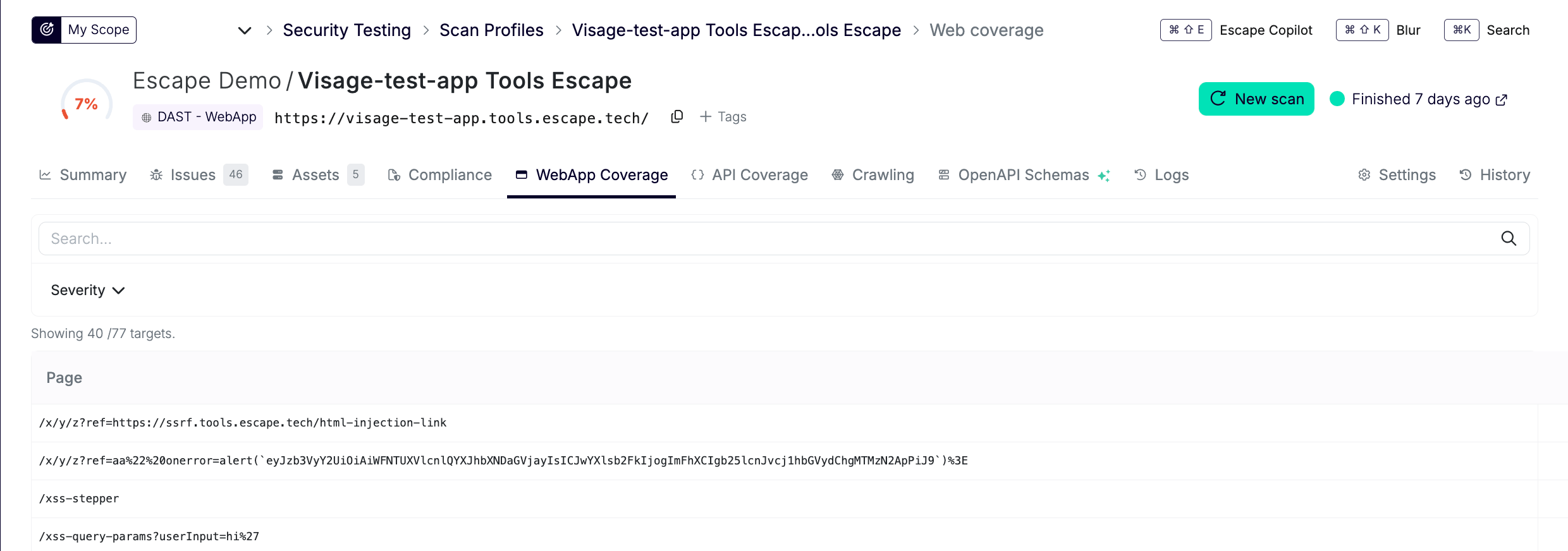
Going beyond, Escape provides step-by-step recommendations to configure scans properly and benefit from Escape’s full testing engine capabilities. You can find more information about Escape's coverage in the docs.
In comparison, Invicti provides coverage with a strong emphasis on detecting known vulnerabilities but relies on existing schemas and manual adjustments to optimize scan coverage. According to Invicti's documentation, there can be gaps in scan coverage, especially if critical configurations are missed or APIs are not well-documented. Invicti offers guidelines to address these gaps, but the effectiveness of its coverage is highly dependent on the accuracy and thoroughness of the provided API documentation and the correct use of scanning parameters.
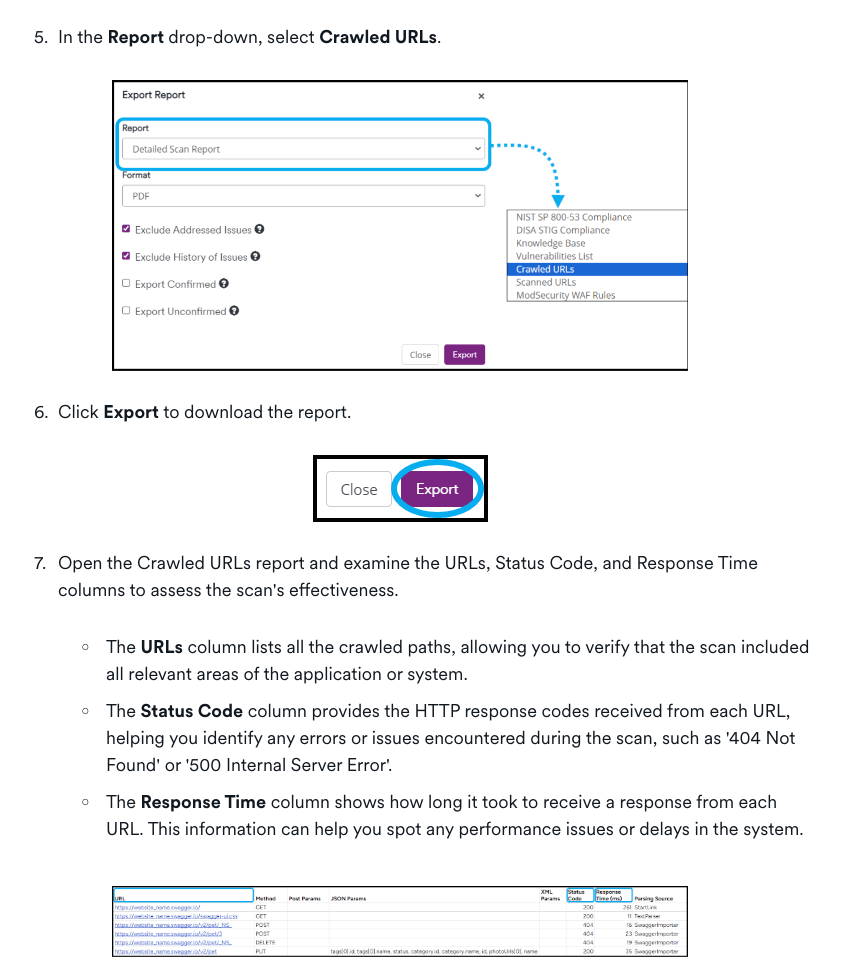
To check a scan’s coverage, you can examine the Crawled URLs Report or the Sitemap (these guidelines are general for all Invicti web scans). While these tools—Crawled URLs Report and Sitemap—are helpful for understanding what parts of the system were covered, they require manual review to effectively address gaps in coverage. This manual analysis can be time-consuming and may leave room for human error. The need to examine detailed reports and visualize structures introduces complexity, especially in larger environments with numerous endpoints and interactions.
In contrast, Escape's approach to coverage and logging is more automated and adaptive, focusing on minimizing noise while ensuring comprehensive scanning of all relevant endpoints.
Risk-scoring
Invicti relies on Invicti’s Predictive Risk Scoring to calculate risk scores using a dedicated in-house machine learning model. The Invicti risk score indicates how likely a website is to have vulnerabilities that make it susceptible to attacks before the scan, it's not linked to the fact how exploitable each vulnerability is or whether asset is exposed. Invicti also mentioned that Predictive Risk Scoring is also not as thorough as scanning each site, so it is important to note that you need to scan your sites to find vulnerabilities.
Without a clear system for ranking vulnerabilities based on their business impact (i.e. actual vulnerability criticality, its exposure and exploitability), organizations may find it challenging to determine which vulnerabilities to address first, leading to inefficient use of resources and potential oversight of critical issues.
Escape, however, offers a distinct advantage with its vulnerability prioritization funnel. This feature automatically identifies and prioritizes business-critical vulnerabilities (exposed and exploitable), ensuring that the most significant threats are addressed promptly. In addition, it clear shows each application's code owner.
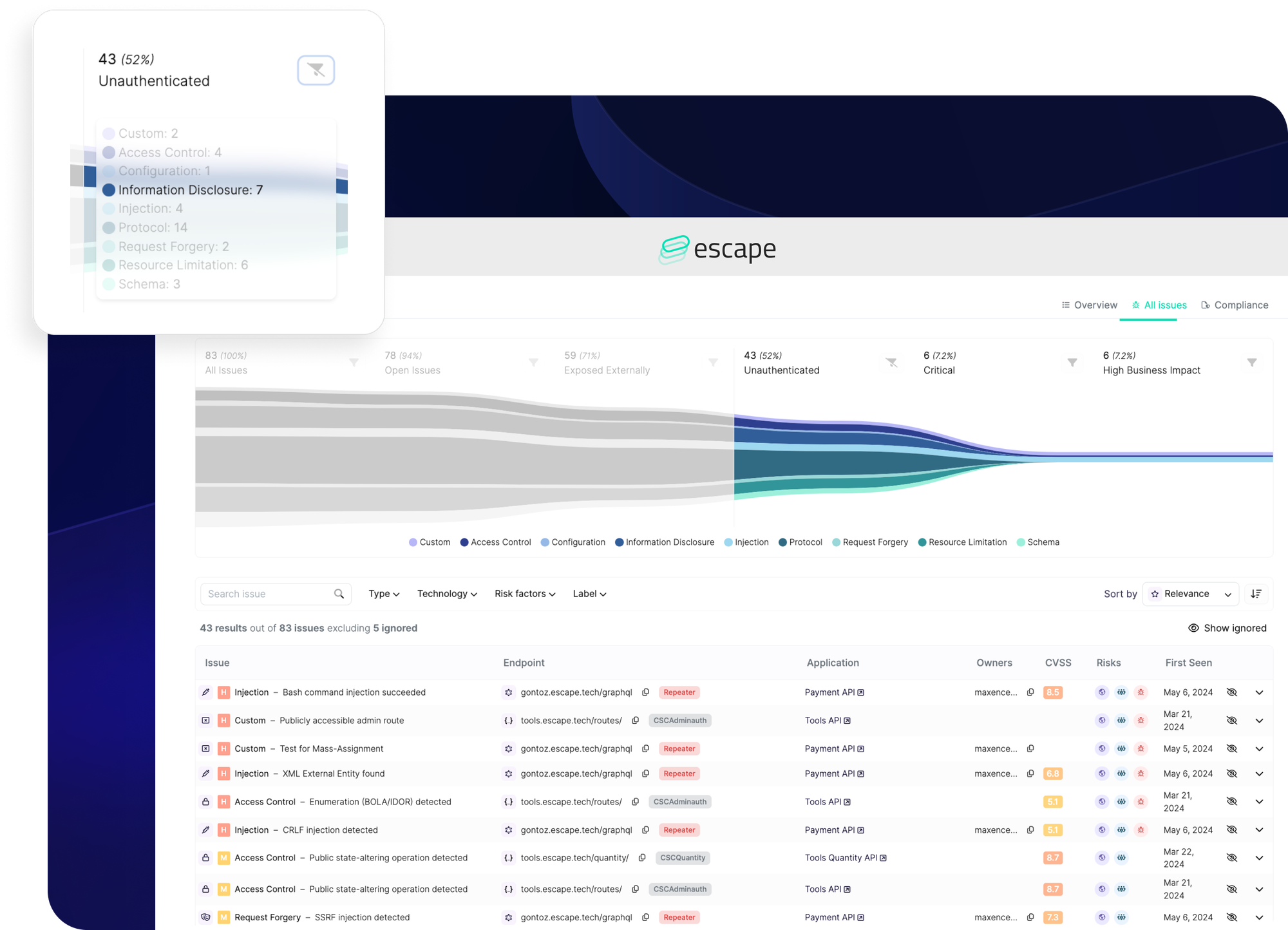
Since August 2024, Escape has been moving away from the traditional CVSS score-based system and adopting a new approach that highlights Escape Severity, including context related to API services. While CVSS scores provide a numerical risk measure, they don’t always capture the full picture. Escape Severity considers various factors such as the type of vulnerability, its exploitability, CVSS score, and other risk factors.
This comprehensive approach helps us better align issue prioritization with real-world risks and ensures you tackle the most critical issues more effectively.
By streamlining the prioritization process, Escape enables security teams to focus their efforts where they matter most, enhancing overall security and providing peace of mind that critical vulnerabilities are being effectively managed.
Remediation
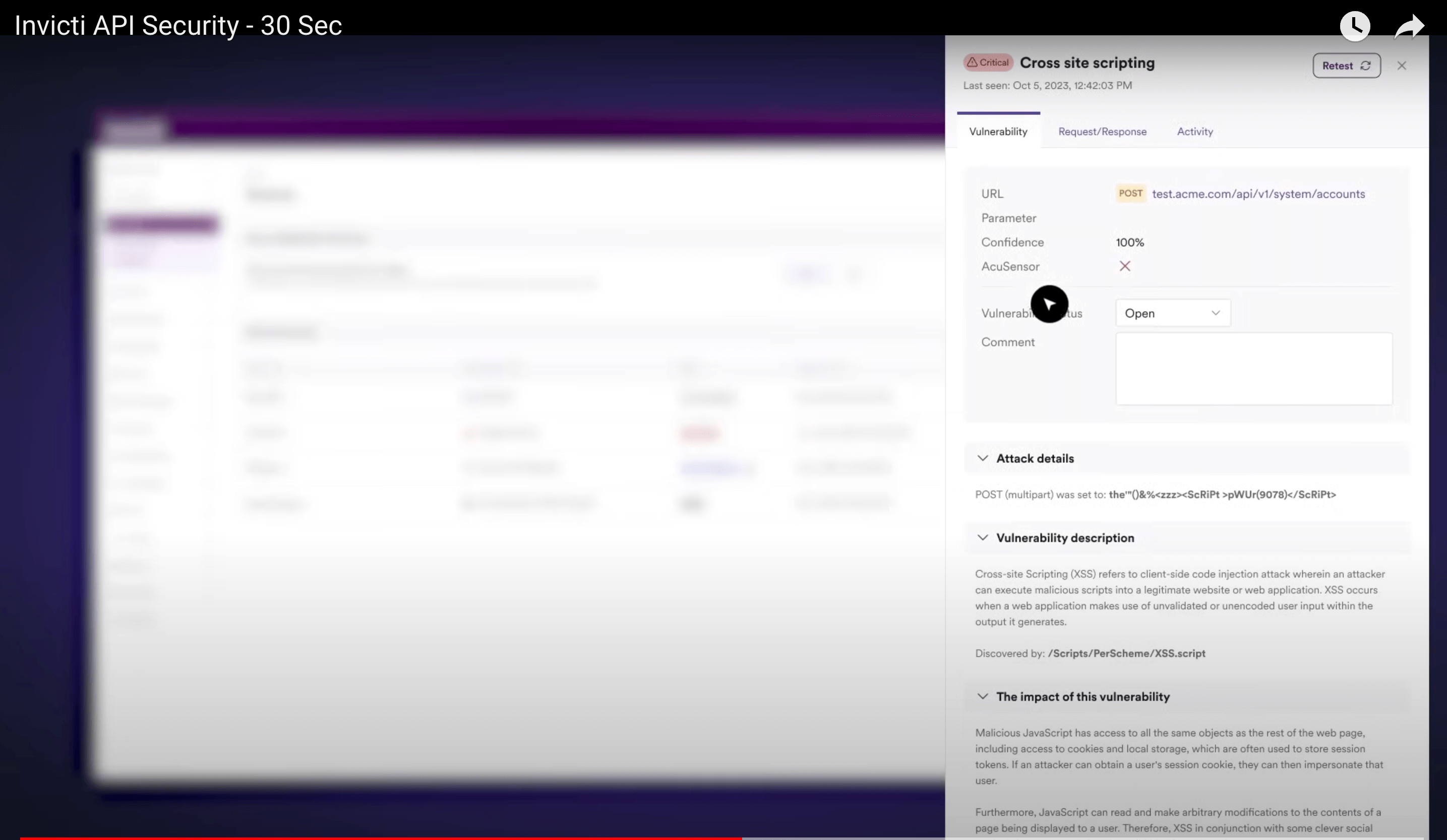
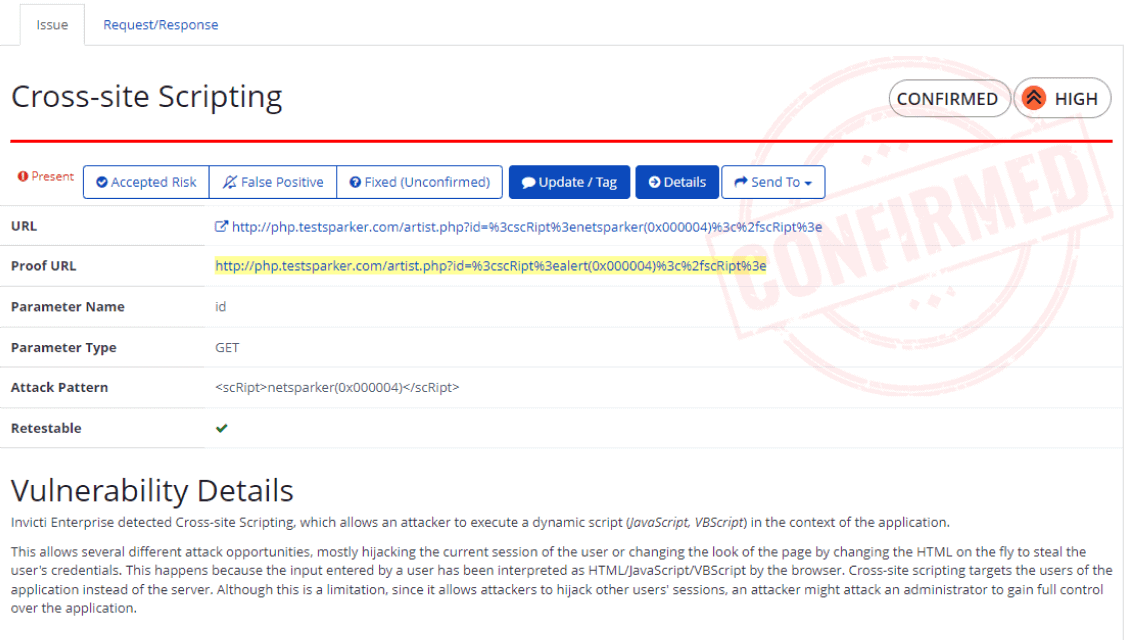
One of Invicti's key drawbacks is that its findings aren’t easily actionable.
Detecting vulnerabilities is only the first step; providing developers with actionable remediation guidance is equally important.
are
While Invicti can undoubtedly detect issues, its platform provides little direct support for developers to fix the identified vulnerabilities. The absence of code snippets or step-by-step remediation instructions means that security engineers need to manually translate alerts into fixes, which can be slow and error-prone.
Escape goes above and beyond by offering tailored remediations and code snippets to address identified vulnerabilities efficiently.
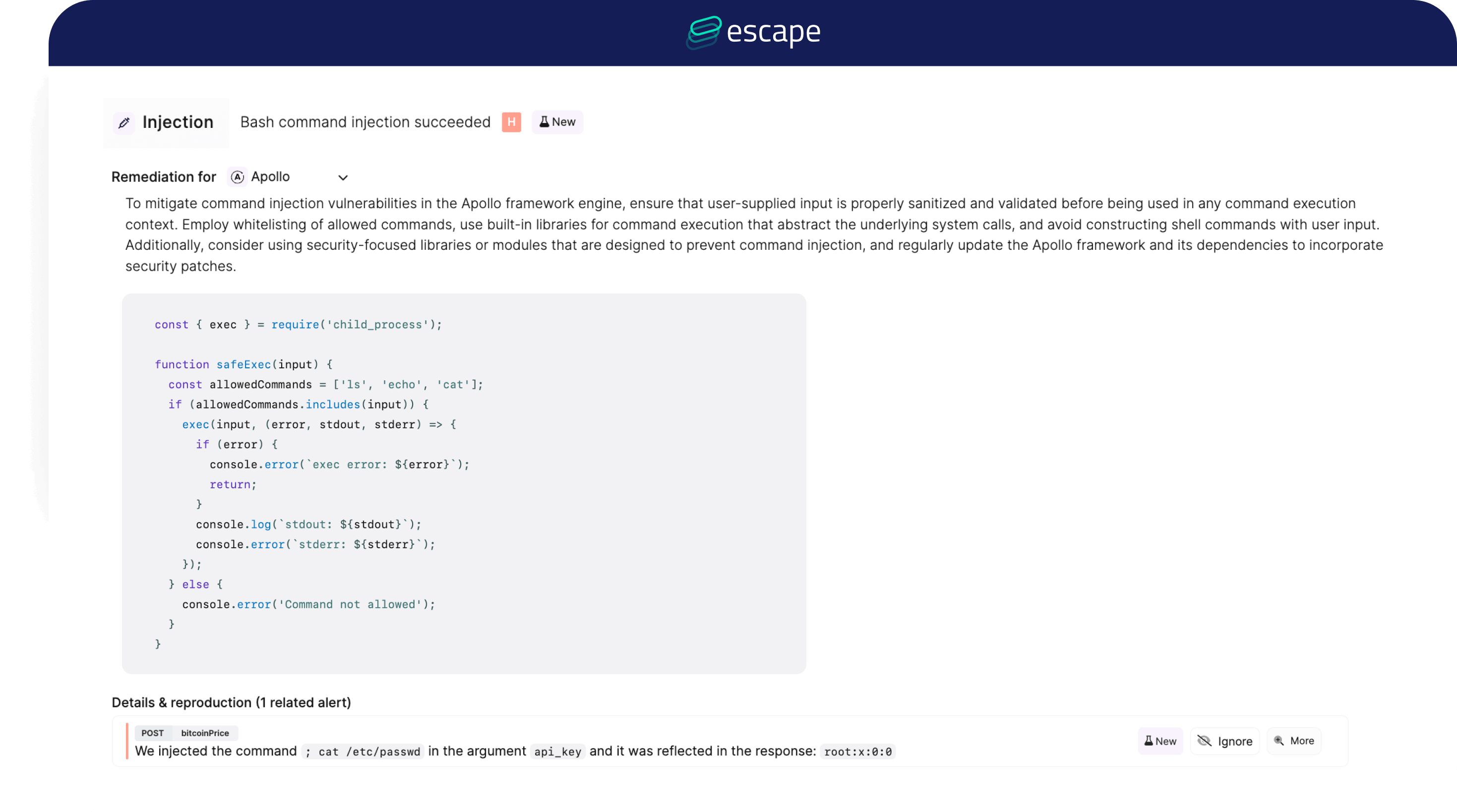
For each vulnerability, security teams can automatically share these code snippets with pre-filled remediation steps in Jira, saving time and ensuring faster resolution. Your developers can hit the ground running with the fix already in hand.

Extra Capabilities: Asset & API Discovery
You can't secure what you can't see, so the faster you get to see what applications are exposed on the internet, the more you reduce the risk of security breaches. And it all starts at the code level.
Escape is built to help you get the value out of it in the shortest time possible. It allows you to discover your web applications & APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This ensures that all web applications and APIs, including those not actively in use, are discovered and documented.
You can go further by integrating with code repositories (in Github, Gitlab..), or tools like Wiz to pinpoint exactly what assets exist all across your application landscape and who owns what.
According to their website, Invicti finds domains and applications through email matching, reverse API lookup, organization name matching, or AWS integration and APIs through zero-config testing, API management system integrations, and network API discovery.
These three methods can be combined to identify and fetch API endpoints:
- Network API Discovery: The Invicti Network Traffic Analyzer observes the traffic on your network to identify and then reconstruct REST API calls into OpenAPI3 specifications.
- API Management Integration: Invicti Enterprise integrates with API management systems to fetch and sync your known Swagger2 and OpenAPI3 specifications.
- Zero Configuration API Discovery: Scans your existing cloud targets for open ports and accessible paths to identify and retrieve Swagger2 and OpenAPI3 specifications.
This means Invicti is more dependent on existing documentation and visible endpoints, and it can struggle with discovering undocumented or shadow APIs, which are common in rapidly changing development environments. Essentially, Invicti can only detect APIs that are already somehow integrated into your system or already targeted, making its discovery approach more reactive than proactive.
Additionally, the amount of information displayed within the Invicti API Inventory doesn't appear to be very comprehensive:
Deploying Invicti for API discovery isn't also as straightforward. According to their documentation, setting up API discovery with Invicti involves multiple configuration steps, including linking it to existing network monitoring, or connecting it to specific cloud environments.
For example, when it comes to network monitoring, it is achieved by deploying the Invicti Network Traffic Analyzer (NTA) to your Kubernetes cluster. "The NTA includes a tap plugin that identifies API-specific unencrypted web traffic, which are converted to telemetry messages and sent to the NTA for reconstruction into OpenAPI3 specs. Those reconstructed OpenAPI3 specs are then pushed to your API Inventory in Invicti Enterprise."
With Escape, to get started all you need is to put in your main domain name, so you can build inventory without any intervention from the development team, which is not necessarily the case when you need to deploy traffic-based API discovery tool. Simplified deployment processes minimize the need for specialized knowledge and extensive internal resources.
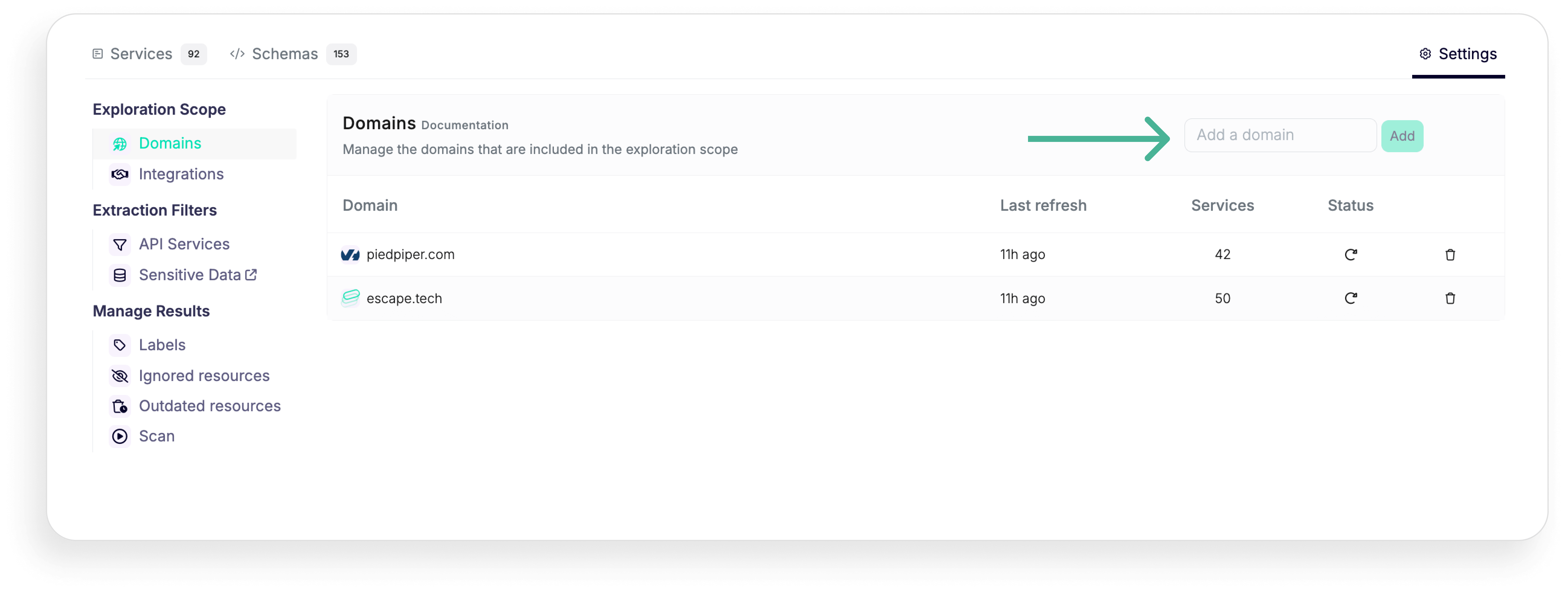
Once you've discovered all your exposed applications, you can enrich the data discovered and classified in asset inventory by connecting with your developer tools like Postman, GitHub, and GitLab, cloud platforms like AWS and Azure and gateways like Apigee, Axway, Kong Gateway and Kong Connect and Mulesoft. To scan internal applications behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
Despite making it easy to discover all applications, Escape doesn't fall short in the depth of the information it uncovers. You can see it for yourself 👇
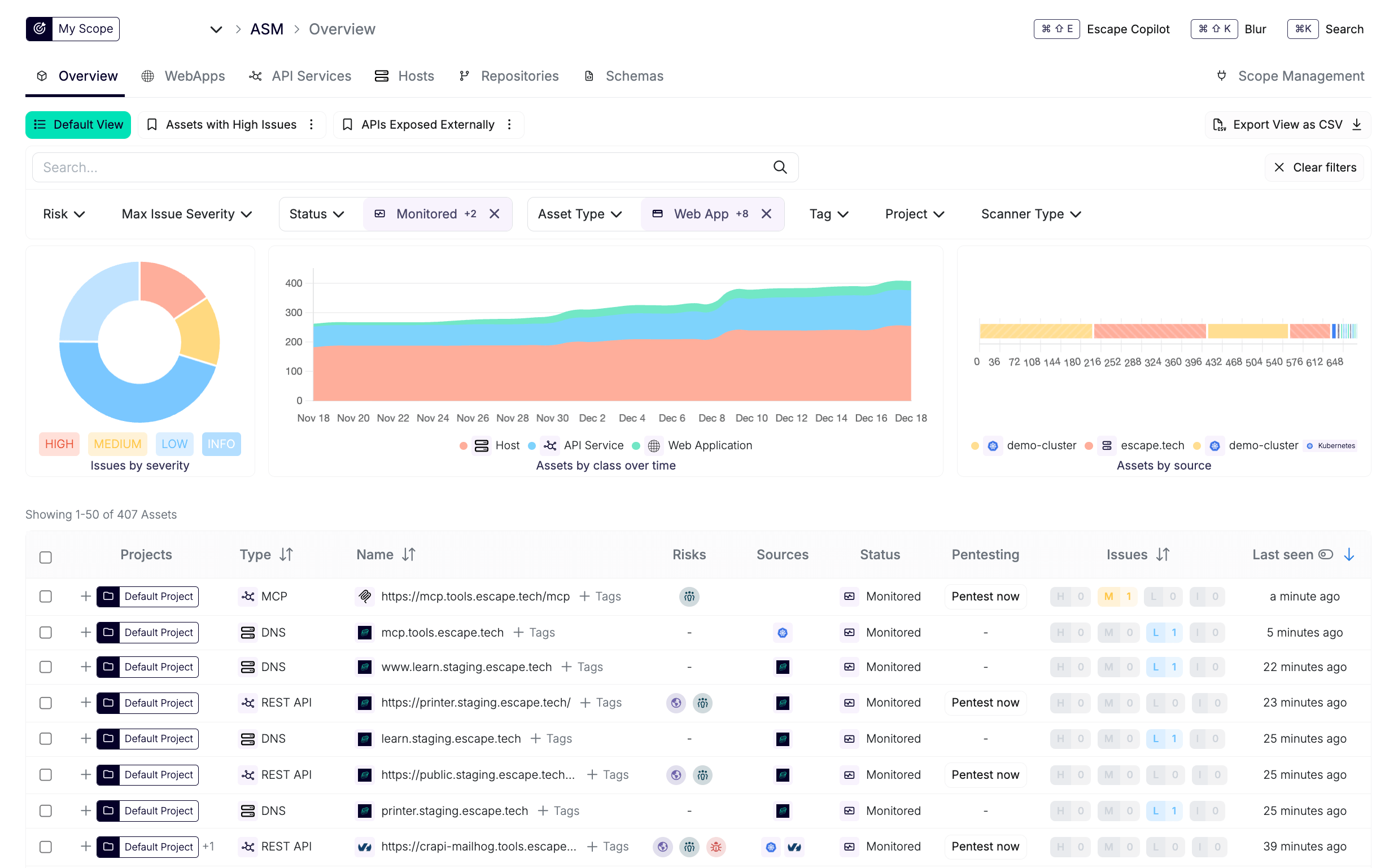
Conclusion
While Invicti offers a solid DAST application security scanning, it falls short in several key areas, such as business logic testing capabilities, support for complex authentication, and developer-ready remediation.
What sets Escape apart from traditional DAST tools like Netsparker DAST is its ability to detect business logic vulnerabilities. It’s the only DAST solution that uses a feedback-driven Business Logic Security Testing (BLST) engine. Special attention is given to real-world vulnerabilities like IDORs, BOLAs, and access control flaws. Each discovered vulnerability is supported by AI-Powered Exploit Validation.
If you still have doubts, take a moment to work with our team and see firsthand during a demo how Escape can replace your legacy DAST and help you secure your modern applications at scale.
Schedule a personalized 30-min demo with our product expert to see for yourself how Escape DAST identifies even complex business logic vulnerabilities in your modern applications
Get a demo💡 Want to learn more? Discover the following articles:
