Escape vs Cequence Security
Discover why Escape is a better API security solution.

Today, attackers prioritize exploiting an application's business logic flaws and API vulnerabilities, which may result in the unauthorized extraction of sensitive data. Understanding an application's business logic is challenging and requires a security platform that understands an application's functionalities to address complex API attacks.
Cequence Security has been one of the major players in the API security market for the past couple of years. However, security professionals that we talked with voiced frustrations with their API discovery, requiring extensive tuning, outdated UI, and limited reporting and remediation guidance.
How can Escape create a better API security solution? We'll let you judge if we're better by comparing time to value. In this article, we'll show why and what makes us different than Cequence Security.
When it comes to API discovery and security, choosing the right tool can significantly impact your organization's efficiency and ability to protect its sensitive data.
Below you’ll find an in-depth comparison between Escape and Cequence Security across the entire API security workflow - from API discovery to remediation. We focused on key differences between those two tools.
We've built this comparison based on the following sources:
- Cequence Security official website, publically available documentation and product datasheets
- Cequence Security demos on YouTube
- Feedback from security professionals (whether Cequence's and Escape's current customers or not)
- Feedback from an independent industry analyst
TLDR: Pros and Cons - Cequence Security vs Escape
Side-by-side comparison table
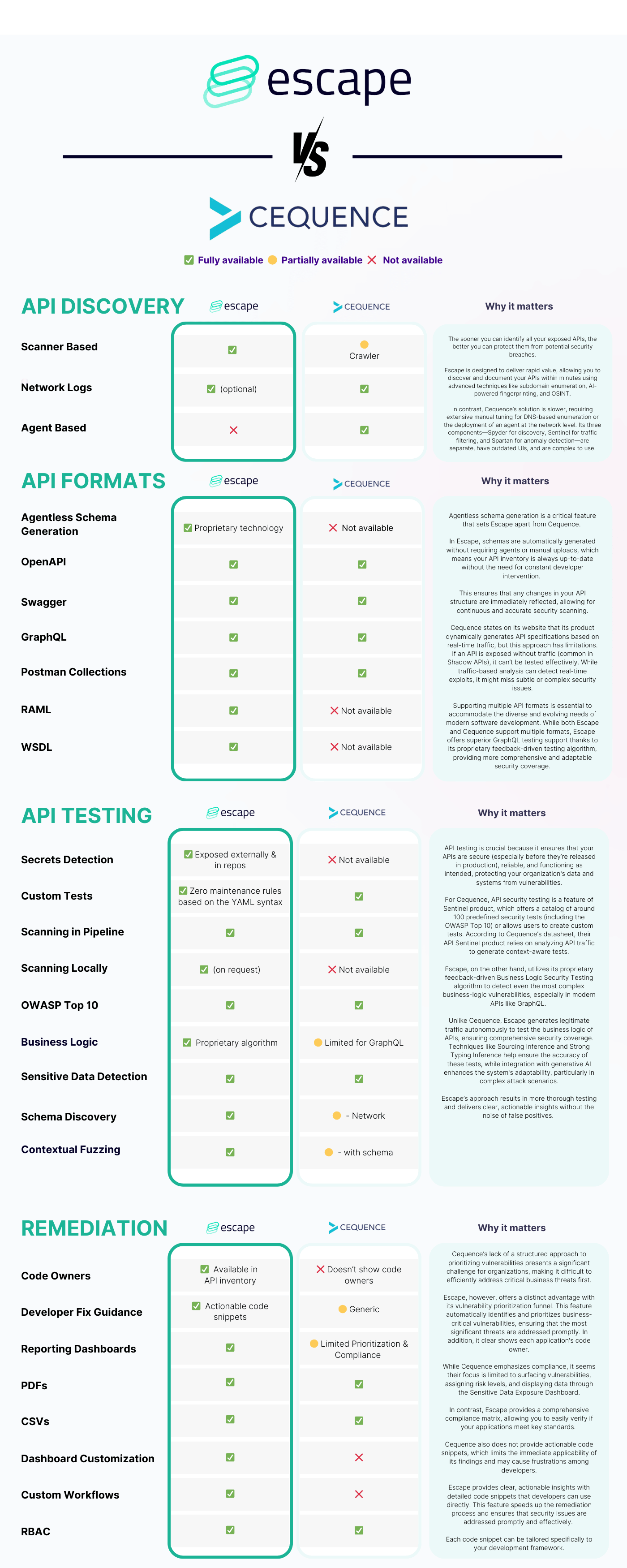
Cequence Security
Pros
- On the surface, Cequence mentions that they do API discovery, detection/posture, response, and anomaly detection - they wouldn't lose feature comparison to anyone. However, its ease of deployment, coverage & quality of the scanning (in the end, it's all about the speed and quality of the results), and user-friendliness need improvement.
- Integrations: Large number of integrations and use cases around those, but most seem to require deploying their container in some way for local log ingestion
- On-premise deployment options.
Cons
- Setup time:
- Spyder: Simple API discovery requires extensive tuning because it’s manually crawling DNS records and using other enumeration techniques. The customization process can be time-consuming, requiring more upfront investment in setup.
- Sentinel & Spartan: complex deployment & reliance on agent for traffic monitoring
- Spyder UI is treated as a separate product that only exists to crawl and try and discover APIs via DNS. It seems to mostly be looking for very basic public exposure and discovery, with very limited testing
- No business-prioritized vulnerability management: Cequence lacks features that prioritize vulnerabilities based on their business impact.
- Lack of actionable compliance insights: There’s limited guidance for teams to align with regulatory standards.
- Slow remediation process: Cequence doesn’t offer actionable code snippets for developers, slowing down vulnerability remediation.
Escape
Pros
- Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
- Automated schema generation that helps you to launch scans right away and reduces the need for maintenance
- In-depth GraphQL testing capabilities and lowest false-positive rate
- Ability to prioritize the most critical API by business context, data sensitivity, and exposure
- Business logic security testing with a proprietary AI-powered algorithm
- Actionable remediation code snippets for developers that help you build better relationships with them
- Effortless custom checks integration to automate security tests tailored to specific APIs
Cons
- Advanced feature sets may require specialized knowledge
- Number of integrations with some of the operational tools
Learn more about Escape
Schedule a time with our product expert to see for yourself how Escape simpliies API discovery and identifies even complex business logic vulnerabilities in your APIs
Get a demoIn-depth comparison: Cequence Security vs Escape
API Discovery
You can't secure what you can't see, so the faster you see the APIs exposed on the internet, the more you reduce the risk of API security breaches.
Cequence consists of three components: a basic DNS-based enumeration scanner for “discovery” (Cequence API Spyder), an agent that can either passively capture network logs, or be placed in line to do traffic filtering (Cequence API Sentinel), and their anomaly detection (Cequence Spartan - Bot management and Fraud Prevention).
API Spyder performs discovery crawls based on domains or IP addresses to discover API endpoints and associated hosting providers. Discovery requires extensive tuning because it’s manually crawling DNS records and using other enumeration techniques. While, obviously, fine-tuning can give you better results, you want to get the best results without spending a lot of time on configuration, right?
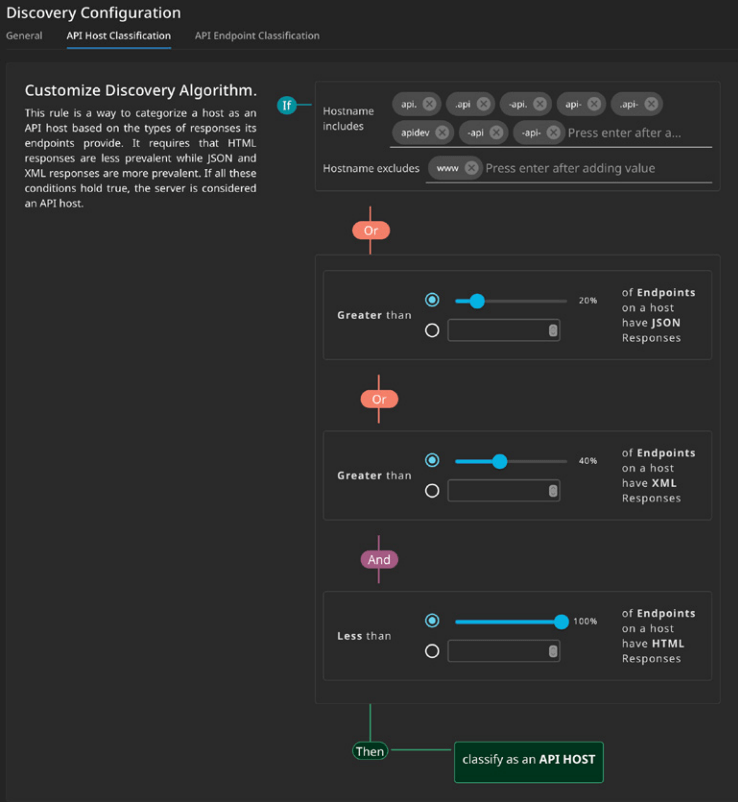
On the other hand, Cequence API Sentinel requires the "deployment of an agent at the network level" to perform API discovery - which immediately complexifies and increases the time to build your API inventory. This method can only detect APIs that are already part of your network traffic. This approach can miss dormant APIs or those not frequently accessed, for example, located outside of API gateways, WAFs or proxies, leading to incomplete visibility.
Escape is built to help you get the value out of it in the shortest time possible. It allows you to discover your APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This ensures that all APIs, including those not actively in use, are discovered and documented.
With Escape, to get started all you need is to put in your main domain name, so you can build inventory without any intervention from the development team. Simplified deployment processes minimize the need for specialized knowledge and extensive internal resources.
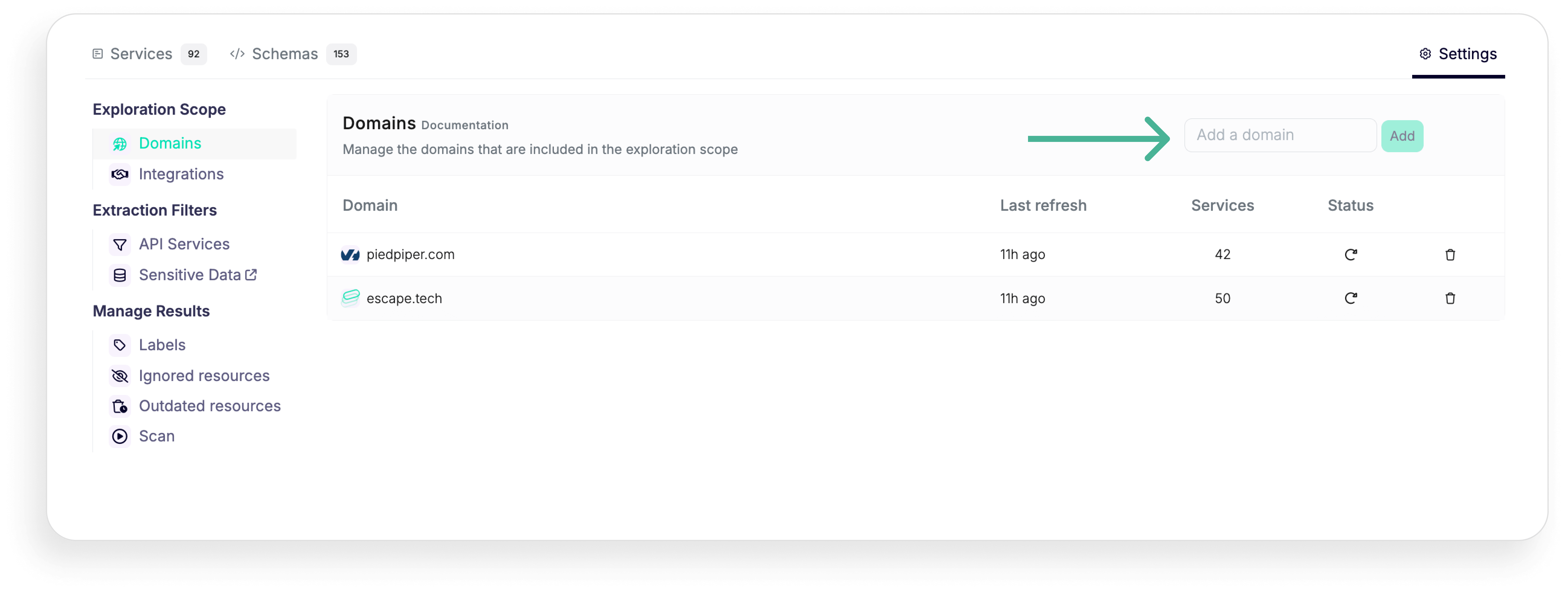
Once you've discovered all your exposed APIs, you can enrich the data discovered and classified in API inventory by connecting with your developer tools like Postman, GitHub, and GitLab, cloud platforms like AWS and Azure and gateways like Apigee, Axway, Kong Gateway and Kong Connect and Mulesoft. To scan internal APIs behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
More than that, Spyder UI is treated as a separate product that only exists to crawl and try to discover APIs via DNS, which is not practical when you want to know the risks associated with your discovered APIs:
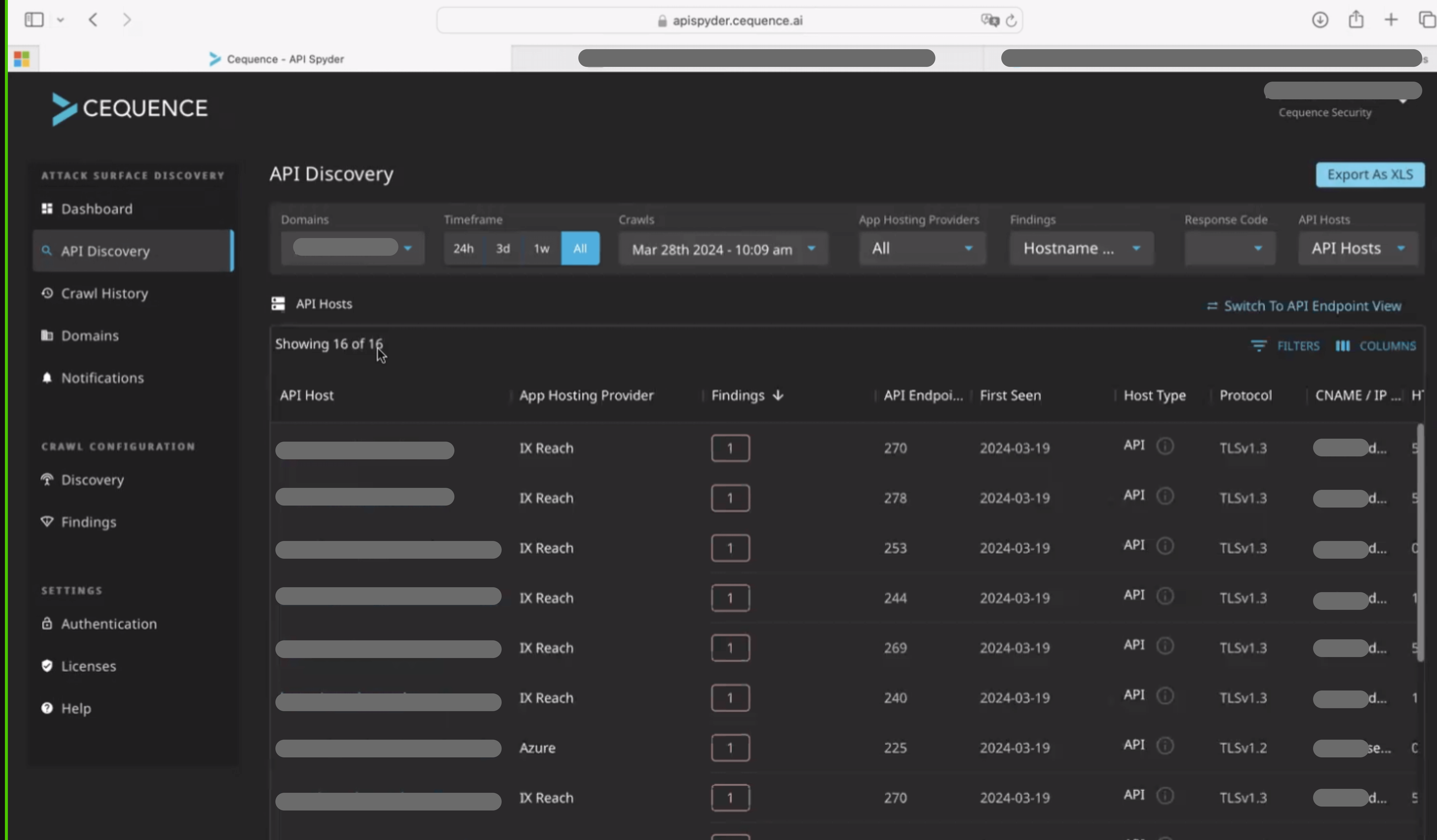
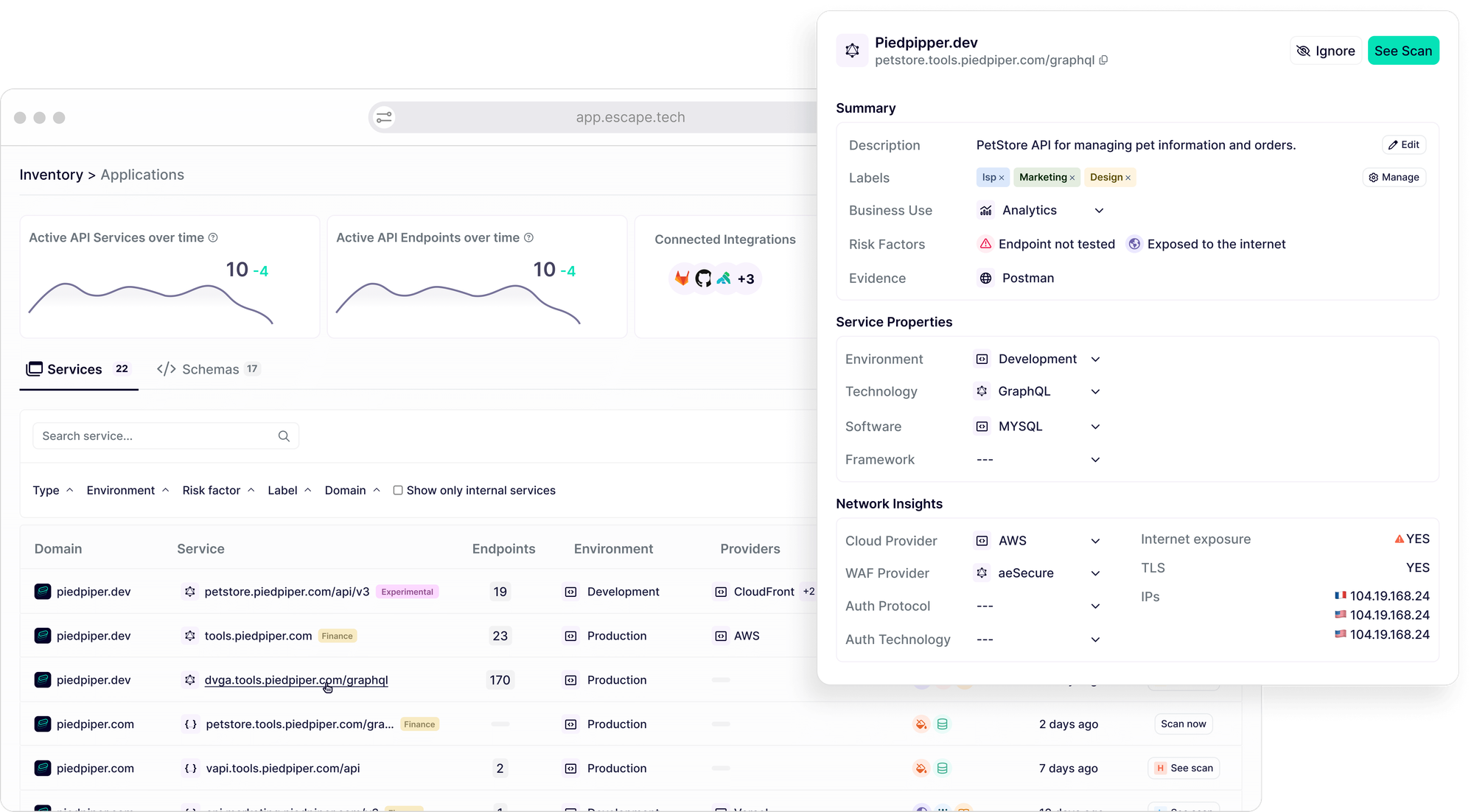
Cequence Security quick API Discovery via API Spyder Interface vs Escape quick API Discovery Interface
API Sentinel’s UI for API discovery is more advanced than API Spyder's. Cequence’s August 2024 update brought significant improvements over the previous version, but it's important to note that it still functions as a runtime inventory, meaning it relies on observed API traffic.
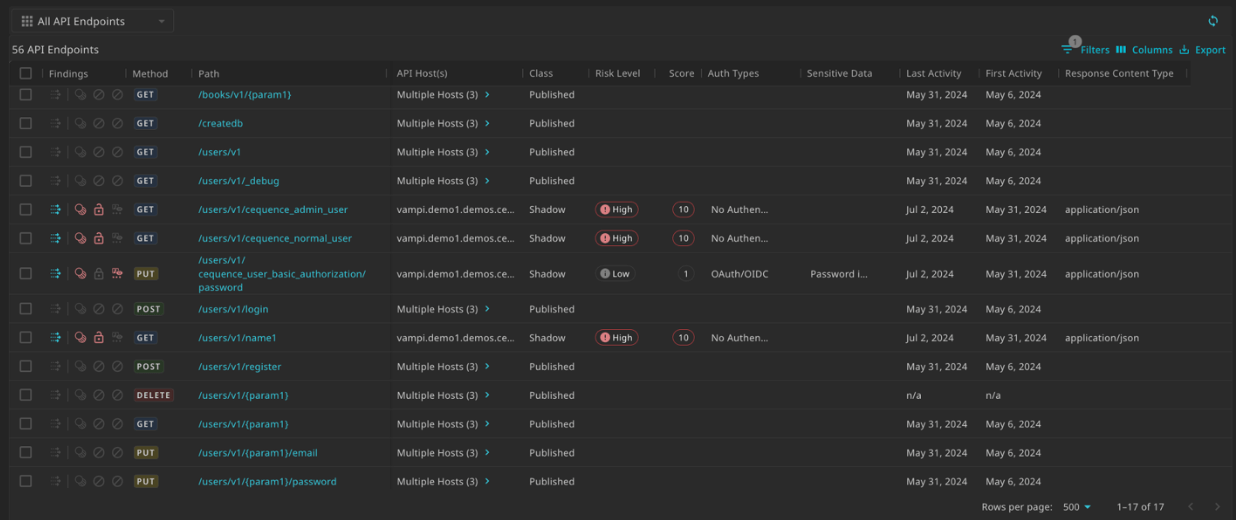
API Security
Once discovery is done, it comes down to API security testing.
For Cequence, API security testing is a feature of Sentinel product, which offers a catalog of around 100 predefined security tests (including the OWASP Top 10) or allows users to create custom tests. According to Cequence’s datasheet, their API Sentinel product relies on analyzing API traffic to generate context-aware tests.
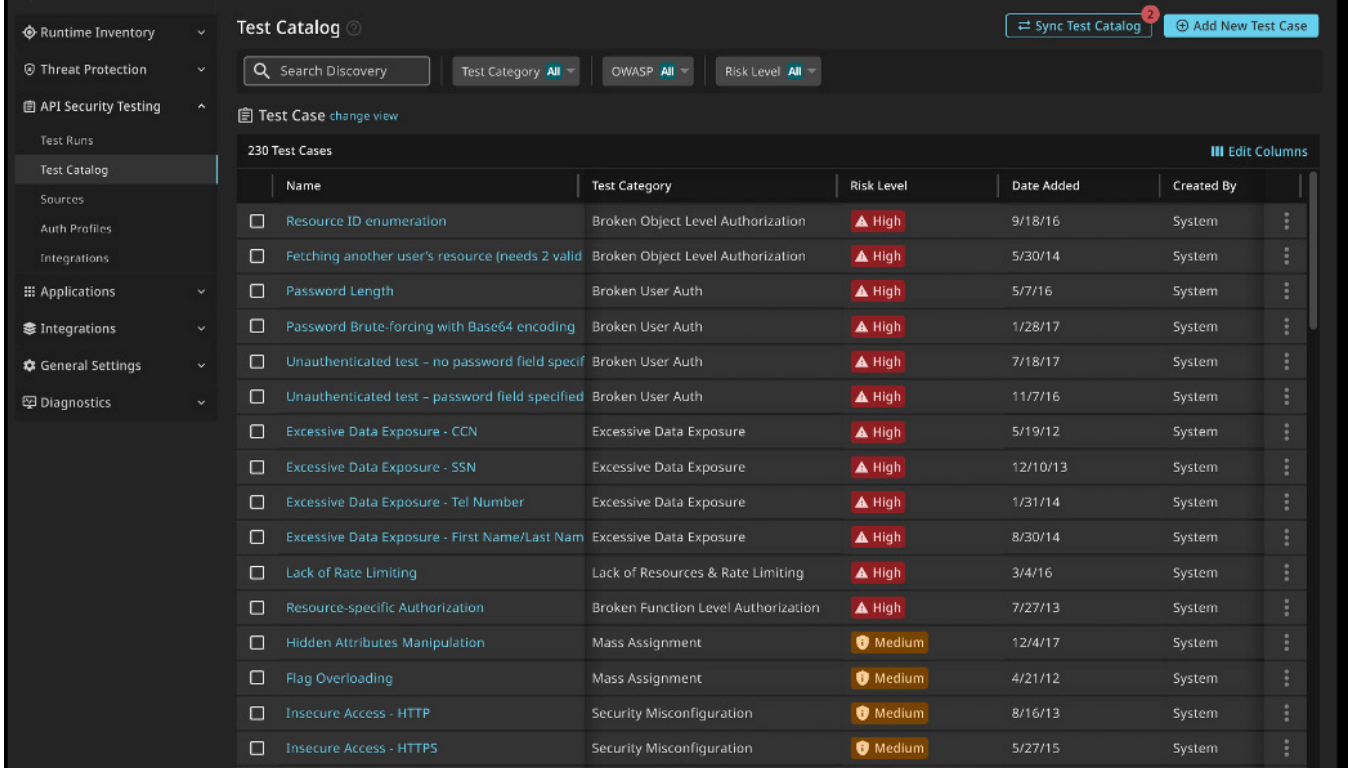
Cequence states on its website that its product dynamically generates API specifications based on real-time traffic, but this approach has limitations. If an API is exposed without traffic (common in Shadow APIs), it can’t be tested effectively. While traffic-based analysis can detect real-time exploits, it might miss subtle or complex security issues.
In contrast, Escape uses a proprietary machine learning algorithm to automatically reconstruct API schemas, enabling context-aware scanning that can be initiated right away without requiring API traffic.
For testing, Escape relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in modern API types like GraphQL. Escape's algortihm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Escape also offers custom security tests that users can implement on their own. They are based don't the YAML operators (detectors/transformations). Escape rules adapt to the evolution of your existing APIs and to your new APIs without the need to maintain them. This includes adapting to database fixtures in the development environment.

Response and Actionable Insights
One of the key drawbacks of Cequence Security is that its findings aren’t easily actionable. The product lacks the ability to provide developers with actionable code snippets for fixing vulnerabilities, limiting the immediate applicability of its insights. This can lead to frustration among developers and slow down the remediation process.
Escape provides clear, actionable insights with detailed code snippets that developers can use directly. This feature speeds up the remediation process and ensures that security issues are addressed promptly and effectively.
Each code snippet can be tailored specifically to your development framework. Don't you think your developers will appreciate more someone who speaks their language?

Another notable drawback of Cequence Security is its outdated UI , which lacks a structured, user-friendly approach to prioritize business-critical vulnerability remediation. Without a clear system for ranking vulnerabilities by business impact, organizations may struggle to identify which threats to address first, potentially leading to inefficient resource allocation, frustrations between security and development teams, and overlooking critical issues.
However, it’s worth acknowledging that the UI in Cequence’s Sentinel product has improved throughout 2024. Since August, it now offers a more comprehensive view of the API attack surface, enhancing overall usability.
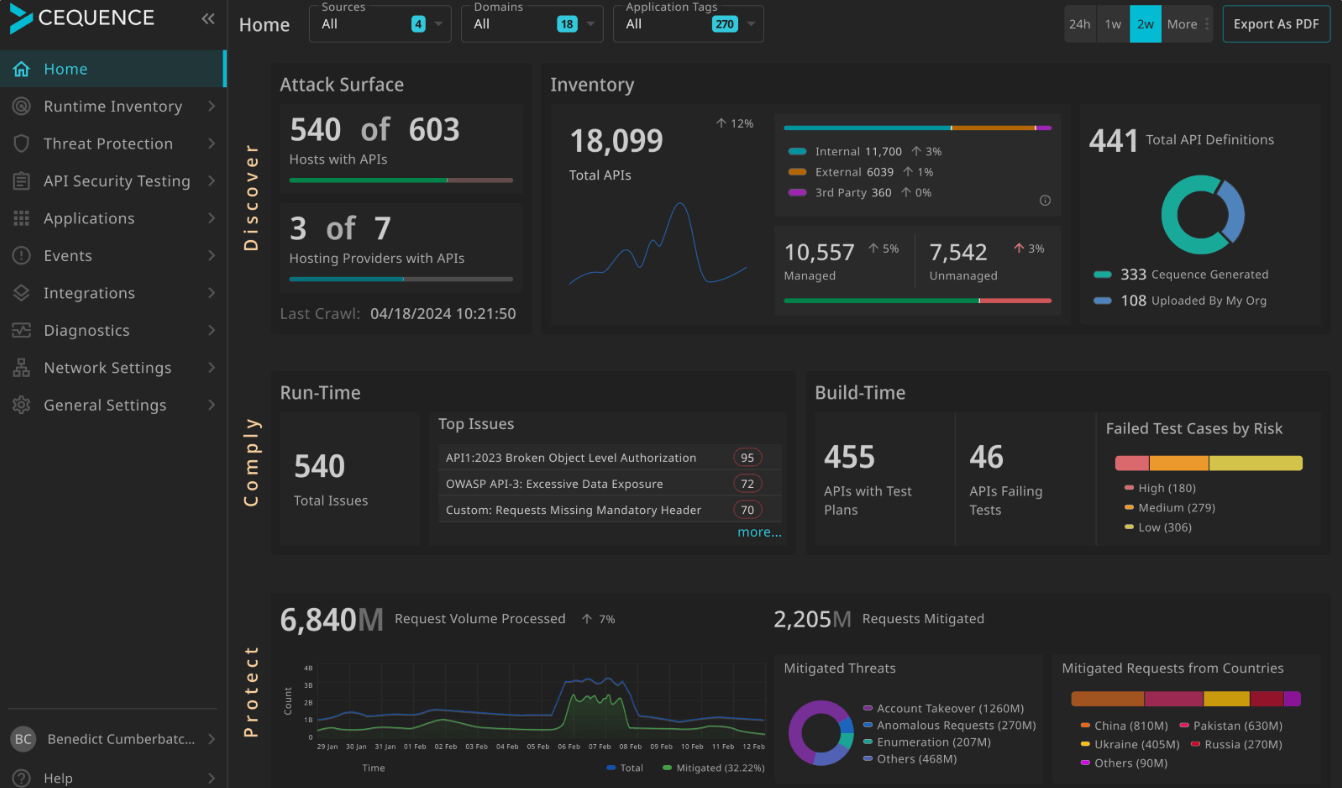
Escape, however, offers a distinct business advantage with its vulnerability prioritization funnel. This feature automatically identifies and prioritizes business-critical vulnerabilities, ensuring that the most significant threats are addressed promptly. In addition, it clear shows each application's code owner.
By streamlining the prioritization process, Escape enables security teams to focus their efforts where they matter most, enhancing overall security and providing peace of mind that critical vulnerabilities are being effectively managed.
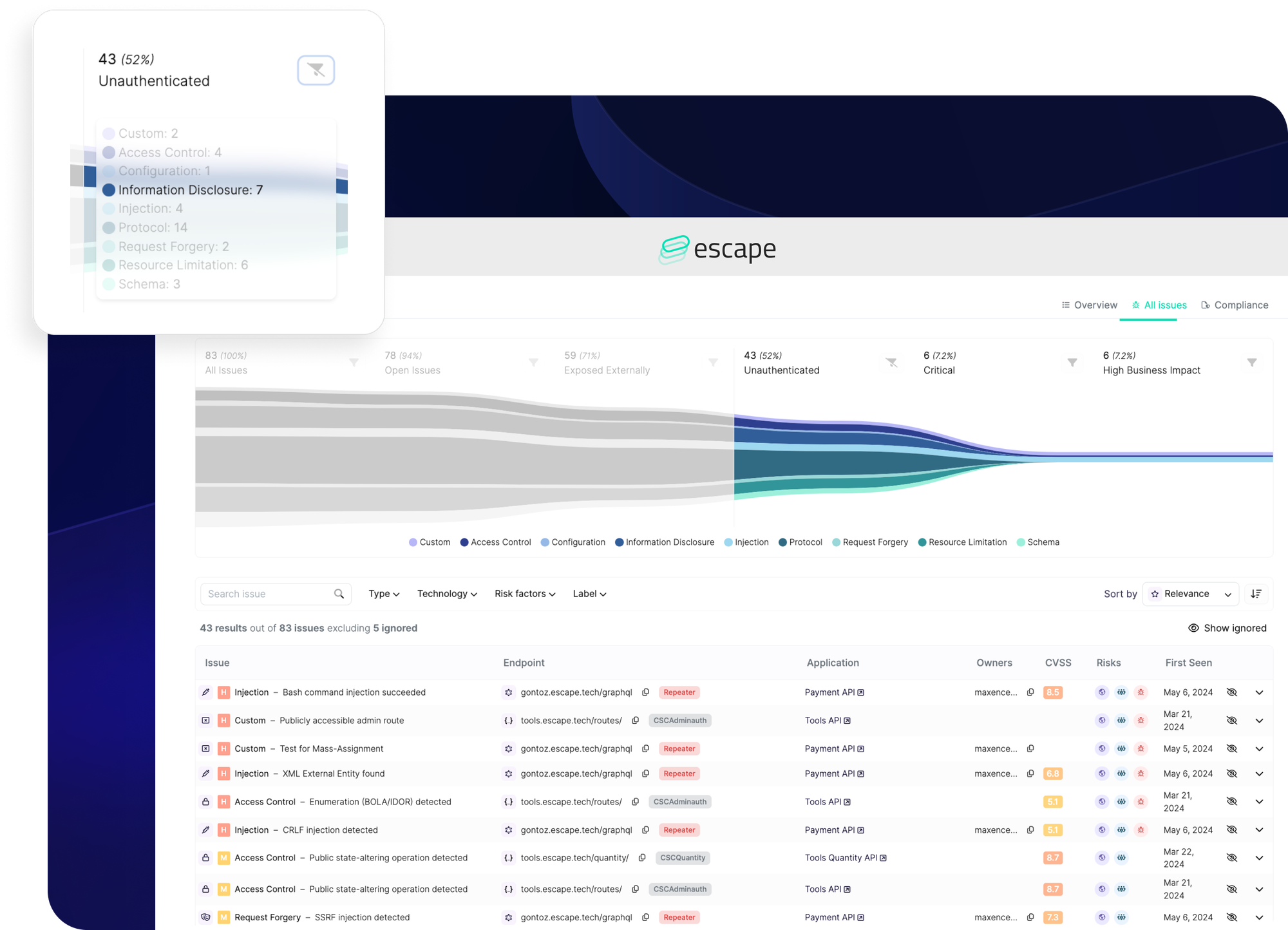
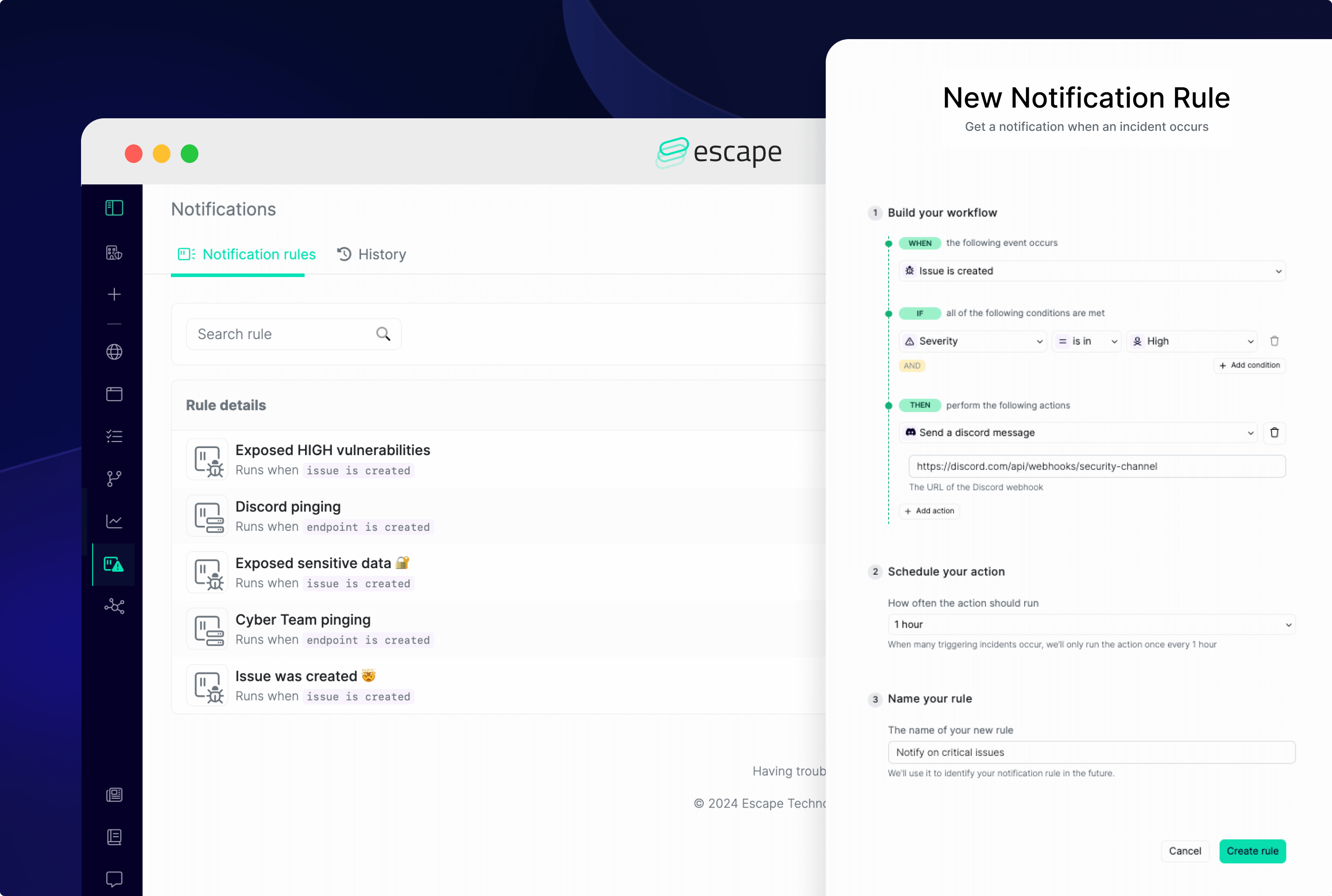
Additionally, Escape's notification rules feature helps you get notified about what really matters for you and your business with just a few easy steps.
Compliance
While Cequence emphasizes compliance, their website lacks clarity on how they help security teams visualize alignment with various regulations. It seems their focus is limited to surfacing vulnerabilities, assigning risk levels, and displaying data through the Sensitive Data Exposure Dashboard.
In contrast, Escape provides a comprehensive compliance matrix, allowing you to easily verify if your applications meet key standards such as OWASP Top 10, PCI-DSS, GDPR, SOC 2, PSD2, ISO 27001, NIST, and FedRamp. This unified view simplifies compliance management across multiple frameworks:
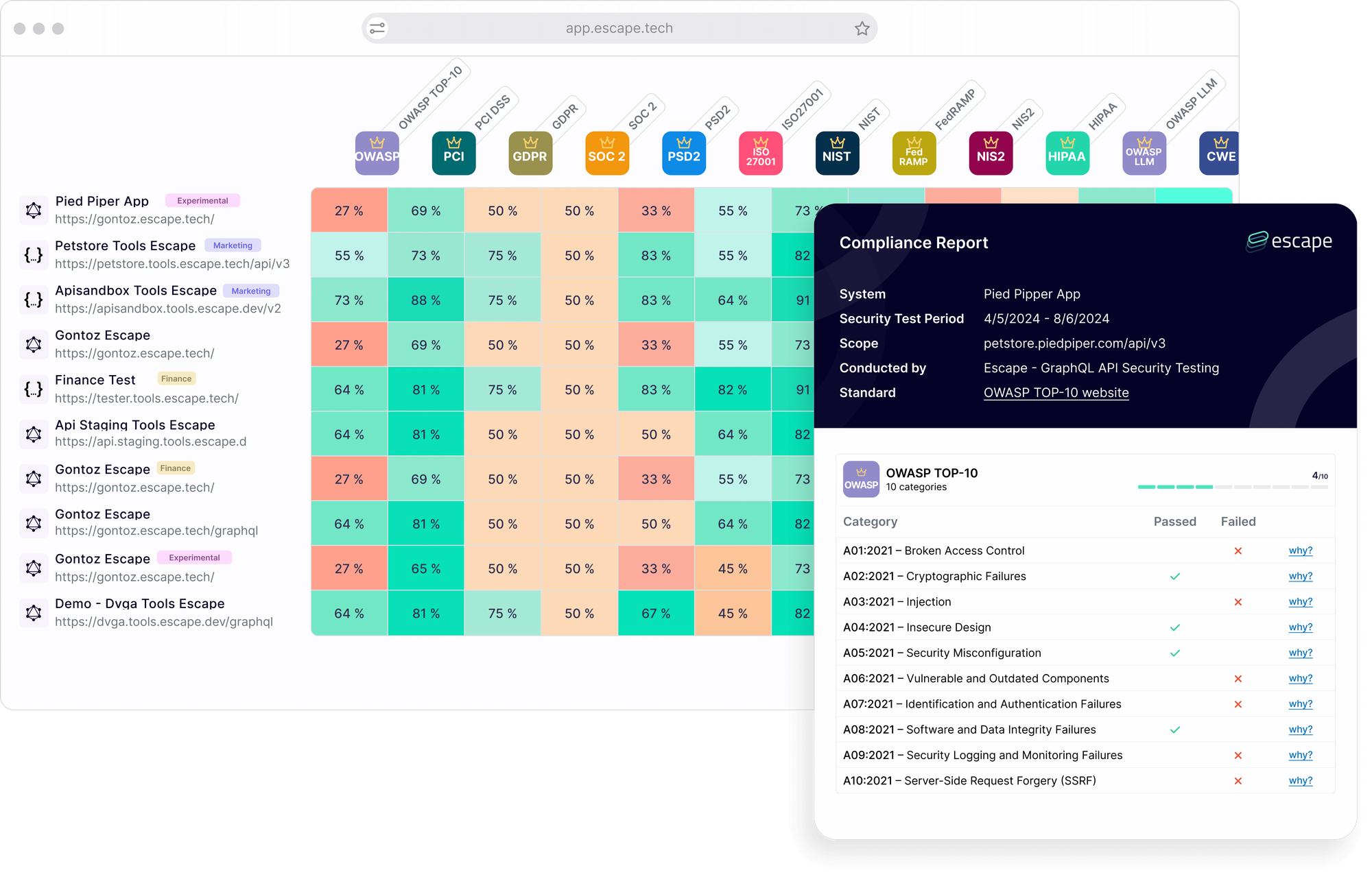
Conclusion
Cequence Security offers a broad range of features, including API discovery, posture assessment, and anomaly detection, positioning itself competitively in terms of surface-level capabilities. However, the platform faces challenges with ease of deployment, scanning speed and quality, and overall user-friendliness. While it supports a variety of integrations, many require complex setups, such as container deployment and agents for traffic monitoring.
Escape provides a more holistic and automated approach to API discovery and security. Its focus is on agentless API discovery, automated schema generation, advanced security testing, and actionable insights for developers.
If you still have doubts, take a moment with our team and see directly during a demo what APIs your organization left exposed.
Learn more about Escape
Schedule a time with our product expert to see for yourself how Escape simpliies API discovery and identifies even complex business logic vulnerabilities in your APIs
Get a demo💡Want to learn more? Discover the following articles:
- Reinventing API security: Why Escape is better than traditional traffic-based tools
- Escape vs Noname
- Escape vs Rapid7
- Escape vs Burp Suite Enterprise
- Escape vs Invicti
Discover your APIs in minutes
Get a complete inventory of your APIs and start fixing your vulnerabilities with detailed solutions for developers
Get started now