Escape vs Detectify: Top Rated Detectify Alternative in 2026 [Compared]
Looking for a Detectify alternative? Compare Escape vs Detectify on API and app security, pricing, G2 ratings, and key features. See why security teams choose this application security scanner for business logic testing and internal app scanning.
![Escape vs Detectify: Top Rated Detectify Alternative in 2026 [Compared]](/blog/content/images/size/w2000/2025/04/Escape-vs-Detectify--1-.png)
Detectify is a well-known dynamic application security testing (DAST) tool that helps identify vulnerabilities in Internet-facing applications. It simulates how attackers might exploit weaknesses in your web apps. The product offers two main components: Surface Monitoring, which continuously discovers and monitors your Internet-facing assets, and Application Scanning, designed to find and remediate critical issues before they reach production.
In 2026, more organizations are evaluating Detectify alternatives. The reasons vary: limited API security testing, rigid authentication handling, or the need for vulnerability assessment across cloud environments. The appsec industry has moved on. Security teams can no longer rely on traditional scanners that only catch common web flaws like SQL injection, but leave entire API architectures untested.
Detectify used to be a popular choice, but many businesses now look for alternatives. Escape DAST presents itself as a strong contender. It finds vulnerabilities, including business logic flaws, with a proprietary algorithm. It fits into modern technology stacks, supporting web frameworks, APIs, CI/CD pipelines, and Wiz. Escape also automatically discovers both external and internal applications from code, and it natively handles APIs.
Escape is rated 5.0/5 on G2. Detectify holds a 4.4/5 on Gartner Peer Insights. This product comparison covers key features, G2 ratings, pricing, and selection criteria so you can decide which tool fits your needs. It is written for application security leaders evaluating DAST vendors, security engineers looking for better vulnerability detection, and those requiring continuous monitoring across distributed cloud environments.
Detectify vs. Escape DAST: A Quick Comparison
We built this Detectify comparison based on feedback from former Detectify customers who evaluated Escape as an alternative. We also used the following sources:
- Detectify's official website and resources
- Detectify's technical documentation
- Detectify's publicly accessible demos
TL;DR
| Feature | Detectify | Escape |
|---|---|---|
| G2 / Analyst Rating | 4.5/5 on G2 | 5.0/5 on G2 |
| Best for | Web app surface monitoring, external assets | API-first teams, complex auth, internal + external apps |
| Pricing | From $70/month, 14-day free trial (Source: Capterra) | Custom - Enterprise (Source: Escape) |
| Application discovery | Continuously discovers and monitors all of your Internet-facing assets and domains available through connectors. No internal asset (ex. behind VPN), no API discovery | Agentless discovery, external and internal, from code and connectors (Wiz, Akamai, AWS, Postman, GitHub, GitLab). Full API + web app coverage |
| Testing Approach | DAST scanner using fuzzing techniques | DAST scanner with a proprietary business logic security testing algorithm |
| API Testing | No native API support | Native support for REST, GraphQL, SOAP APIs |
| Internal Asset Scanning | External only | Supported, through code repositories and via Private Locations / Repeater Proxy |
| Scanning Scope | Web apps via domains and connectors. No API coverage | Full API and web app inventory, internal and external (including shadow APIs, zombie APIs) |
| Authentication | Partial: Basic, session cookies, Chrome plugin. No complex auth flows | OAuth, API keys, JWT, MFA, Playwright, custom workflows + AI agent for automatic login |
| CI/CD Integration | Partial: via Zapier (GitHub, GitLab, Azure DevOps) | Native integration (how to implement DAST in CI/CD pipelines: GitHub Actions, GitLab CI/CD, Bitbucket, Jenkins, Azure DevOps, npm) |
| Continuous Monitoring | Surface monitoring, external only | Continuous monitoring, external + internal, across cloud environments |
| GraphQL Security | No native support | Native GraphQL security testing |
| Compliance and Reporting | Partial: PDF reports, no unified compliance view | Detailed compliance reports + Compliance matrix (SOC 2, ISO 27001, PCI DSS) |
| Vulnerability Detection | OWASP Top 10, security misconfigs. No API vulnerabilities | OWASP Top 10 + OWASP API Top 10, vulnerability categories covering business logic (BOLA, IDOR, Access Control)/td> |
| Custom Security Tests | Not supported | YAML-based custom security tests with custom policies and ability to integrate bug bounty results, discovery + security testing |
| False Positive Reduction | Users report challenges with noise | AI-based classification, severity based on business context + exploitability |
| Remediation Guidance | Generic recommendations that require developers to manually tailor them. | Developer-ready code snippets tailored to each framework |
What Users Say: Ratings and Reviews
Peer reviews and analyst ratings matter when evaluating a Detectify alternative. They come from real users in the industry, not from vendor marketing pages. Below is how Escape and Detectify compare across review platforms.
| Feature | Escape | Detectify |
|---|---|---|
| G2 | 5.0/5 on G2 | 4.5/5 on G2 |
| Gartner Peer Insights | Not listed yet | 4.4/5 |
What Users Say About Escape
Escape gets strong marks for API security testing accuracy and business logic vulnerability detection. Customers consistently mention these key features:
- Low false positive rate and actionable remediation guidance
- Strong integrations with modern development workflows and CI/CD pipelines
- Support for complex auth flows
- Business logic testing that competitors miss, including BOLA and IDOR detection
"The time-to-value ratio is just 100% there. While most DAST scanners on the market are built for Web Applications, Escape DAST is purpose-built to protect APIs on top of Web Applications." — Michael Bourgault, Sr. Security Architect
"Escape has an excellent modern approach to DAST testing making it easy to manage complex single-threaded scans. One of the nicest features is the screen capturing in scan logs allowing teams to quickly validate if authentication has occurred."— G2 review via AWS Marketplace
"Easy to integrate. Helped to quickly check and make sure our GraphQL endpoints were secure. Great customer support as well." — G2 review
"Escape's IDOR scanning and multi-tenant capabilities set it apart from other security testing solutions and allow us to test multiple scenarios. AI-based authentication and Project-scoped permissions facilitate the automation of team onboarding and significantly reduce the onboarding time and efforts. Support team is incredibly responsive to feedback and actually implements it." — Daniel Ilies, IT Security Engineer, Visma
What Users Say About Detectify
Detectify gets positive feedback for ease of setup and external surface monitoring. The platform relies on a global community of ethical hackers who contribute threat intelligence and vulnerability research.
Still, reviewers on Gartner Peer Insights point out recurring issues:
"The lack of issue tracking meant we had a lot of repeat issues popping up in reporting, including some false positives." — Gartner Peer Insights reviewer
"The product is slightly more expensive than the main competitor." — Gartner Peer Insights reviewer
Gartner places Detectify in the External Attack Surface Management (EASM) category. That is an essentially narrower scope than Attack Surface Management with full dynamic application security testing and agentic pentesting coverage offered by Escape.
Pros and Cons
Detectify
Gartner Peer Insights: 4.4/5 | Pricing: from $70/monthly | 14-day Detectify free trial for a surface scan available
Pros
- Solid web application vulnerability scanning that conducts automated scanning of your entire external attack surface
- According to the documentation, easy to set up and start testing. The tool can be configured quickly.
- Support for business-critical vulnerabilities in web applications, powered by a community of ethical hackers and researchers
Cons
- No native API support. No additional discovery options to provide business context related to the APIs (publicly exposed, whether they can be reproduced with or without authentication).
- No ability to scan internal applications (for example behind a VPN). The scanner only covers Internet-facing assets.
- Lacks handling of complex authentication flows. No visibility into Authentication Debug, so you cannot tell if the authentication worked or failed.
- The platform does not support multi-user testing in a single scan profile.
- Remediation suggestions are generic. According to former users, they lack specificity for different development frameworks. These are outdated methods compared to modern application security testing tools.
- Limited reporting and analytics features make it hard to prioritize business-relevant risks in a consolidated view.Escape
Escape
G2: 5.0/5 | Top rated Detectify alternative | PoC available | Contact Sales for enterprise pricing
Pros
- Proprietary business logic security testing algorithm that detects BOLA, IDOR, and Access Control issues that traditional scanners cannot discover. Native API security support for REST, GraphQL, and SOAP, with automated OpenAPI specification generation that continuously monitors API schema changes over time.
- Agentless discovery and scanning of both external and internal applications, including assets behind VPN or firewall via Private Locations. Clear distinction between APIs and web apps in the inventory.
- Advanced authentication handling for complex flows (OAuth, Cognito, SAML, Playwright, custom workflows). The platform's AI agent detects login fields and fills them automatically. Full visibility into authentication debug with step-by-step screenshots.
- Developer-ready remediation code snippets tailored to each development framework. Pre-filled Jira tickets speed up resolution.
- Prioritizes the most critical applications by exploitability, business context, data sensitivity, and exposure. This is true vulnerability prioritization, not just CVSS scores.
- Native CI/CD integrations for automated scanning on every pull request. Supports GitHub Actions, GitLab CI, Jenkins, Azure DevOps. Teams can implement DAST directly in their CI/CD pipelines.
- Integration with well-known cloud security platforms like Wiz
Cons
- Advanced feature sets require specialized knowledge. The product has a learning curve for some users, particularly around custom configurations.
- No IDE plugins (VS Code, JetBrains), unlike some other DAST tools in the industry, but can be addressed via Escape MCP
- Custom test configurations (YAML-based custom policies) require initial setup time. Once configured, maintenance is minimal. Note: business logic tests do not require custom configuration.
Find and remediate business-critical vulnerabilities in modern web apps and APIs
Discover how Escape DAST streamlines vulnerability detection and delivers tailored code snippets to quickly resolve business-critical issues—all while seamlessly integrating into your CI/CD pipeline.
Get a demoIn-Depth Comparison: Escape DAST as an alternative to Detectify
Attack surface
Detectify focuses on monitoring and securing internet-facing assets like websites and subdomains: "You can just provide the main domains, and it keeps scanning all those subdomains for like a basic header, related issues, SSL issues, and dangling DNS that comes under service monitoring." You can add connectors like AWS Route53, Azure, Google Cloud DNS, Cloudflare, IBM NS1, Alibaba Cloud, DigitalOcean, and GoDaddy. Domains stored in these connectors will be synced with your Detectify team on an ongoing basis.
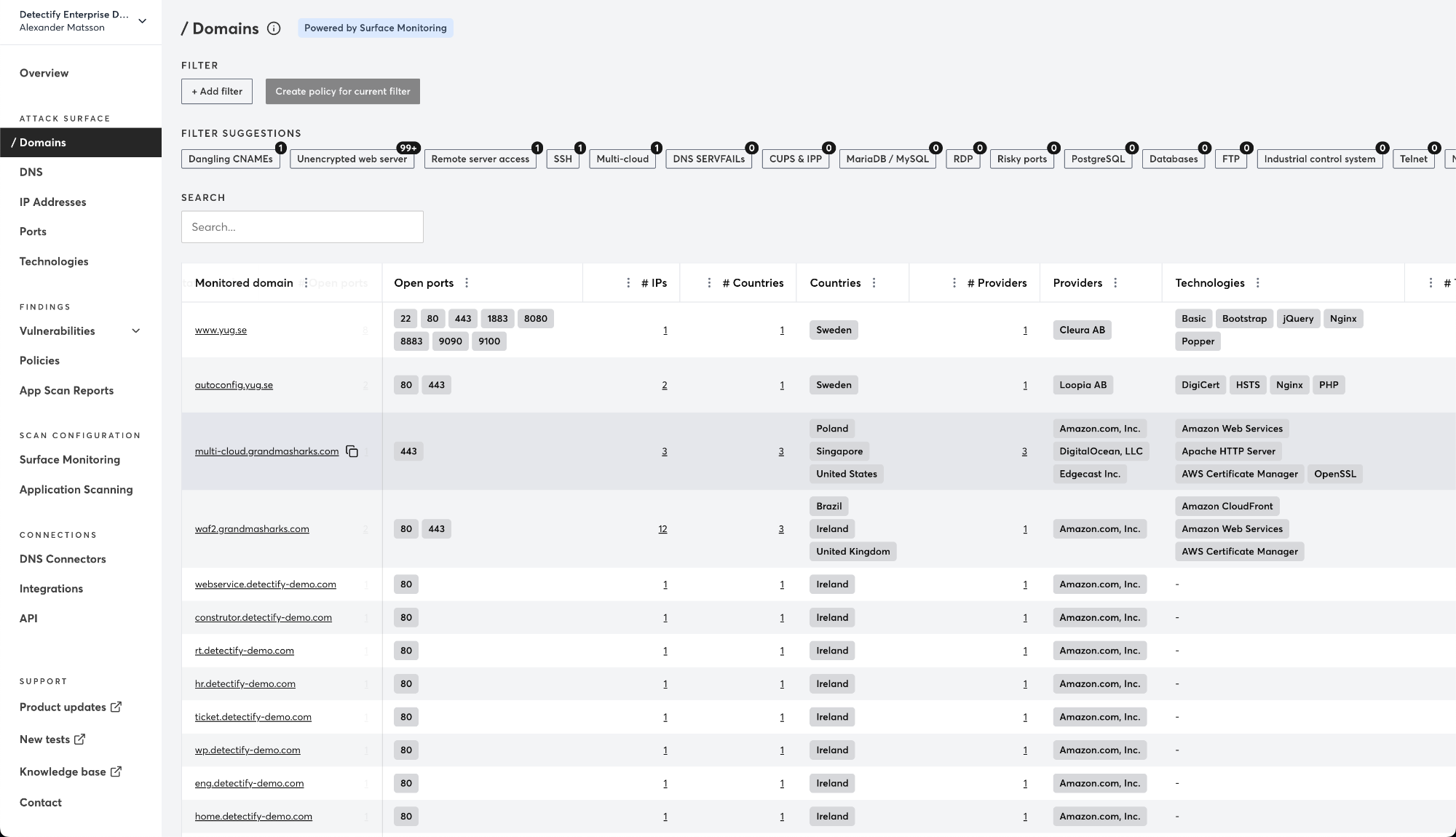
Detectify can discover vulnerabilities on external web applications and subdomains. But it lacks support for scanning internal assets, especially those behind VPNs or firewalls. The platform also offers no visibility into APIs. Detectify's crawler is designed for web applications and does not typically interact with API endpoints. It might incidentally detect some API endpoints during crawling and fuzzing, but it does not actively scan APIs for vulnerabilities. Understanding what API discovery is and how it works is essential when evaluating alternatives.
Escape DAST takes a different approach. It offers agentless discovery of both external and internal assets. Through integrations with Wiz, Akamai, AWS, Postman, GitHub, GitLab, and more (full list here), Escape continuously monitors and scans all of your applications. To scan internal applications behind your firewall or VPN, you can connect Escape's repeater proxy through Private Locations.
Escape provides continuous monitoring across your entire attack surface. This includes applications deployed in cloud environments (AWS, Azure, GCP) and internal assets behind VPN or firewall. It identifies shadow APIs and zombie APIs that traditional scanners miss entirely.
Detectify positions itself as an External Attack Surface Management (EASM) tool focused on public-facing assets. Escape covers both external and internal application scanning through its API discovery and security testing platform. This is a proactive approach to reducing the potential attack surface, and it gives security teams full visibility into their entire application portfolio.
Authentication
Detectify supports several authentication mechanisms: basic authentication, session cookies, and automated login via recorded sessions through a Chrome plugin. But it lacks support for complex authentication flows, multi-user support, custom workflows, and advanced session handling. Users often struggle to authenticate through sophisticated login systems or dynamic authentication processes. This creates gaps in scanning wherever complex authentication in DAST scans is needed.
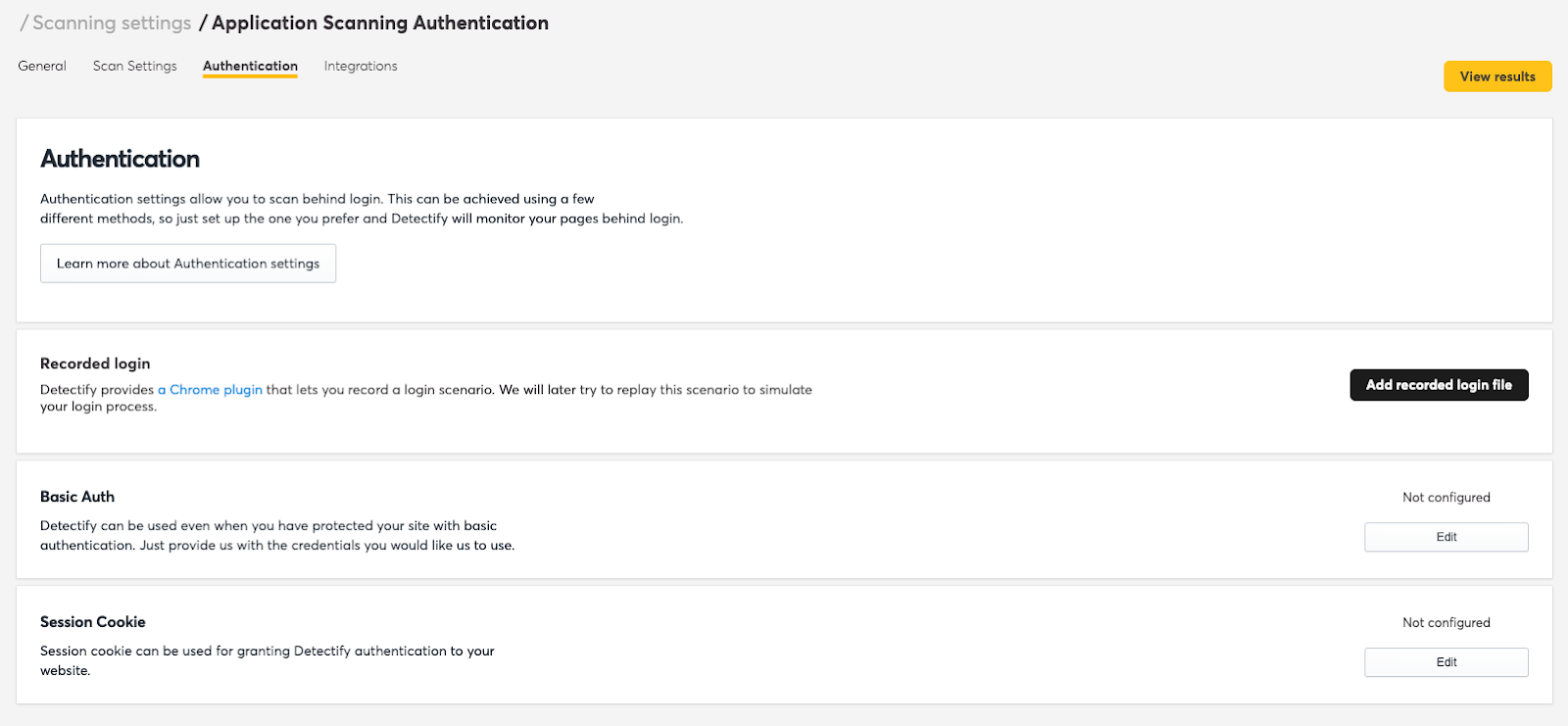
You also "can't know if the authentication worked or failed" when the scanning doesn't work.
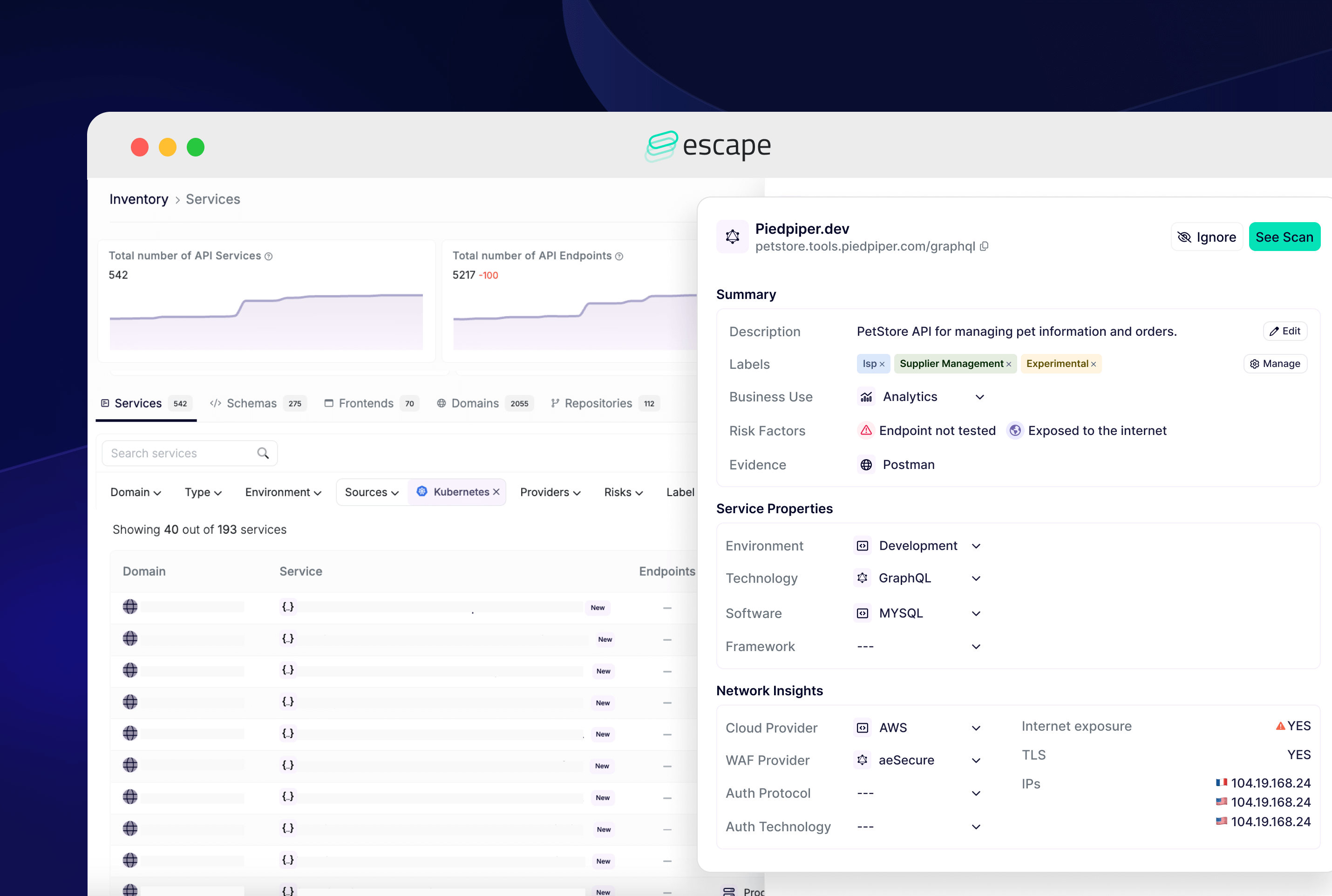
Escape handles this differently. For common authentication methods, it provides Standard Authentication Workflow Presets: Basic, REST, Digest, GraphQL, OAuth, AWS Cognito, Playwright, and others. For more complex needs, users can combine multiple workflows to build advanced authentication and access control procedures.
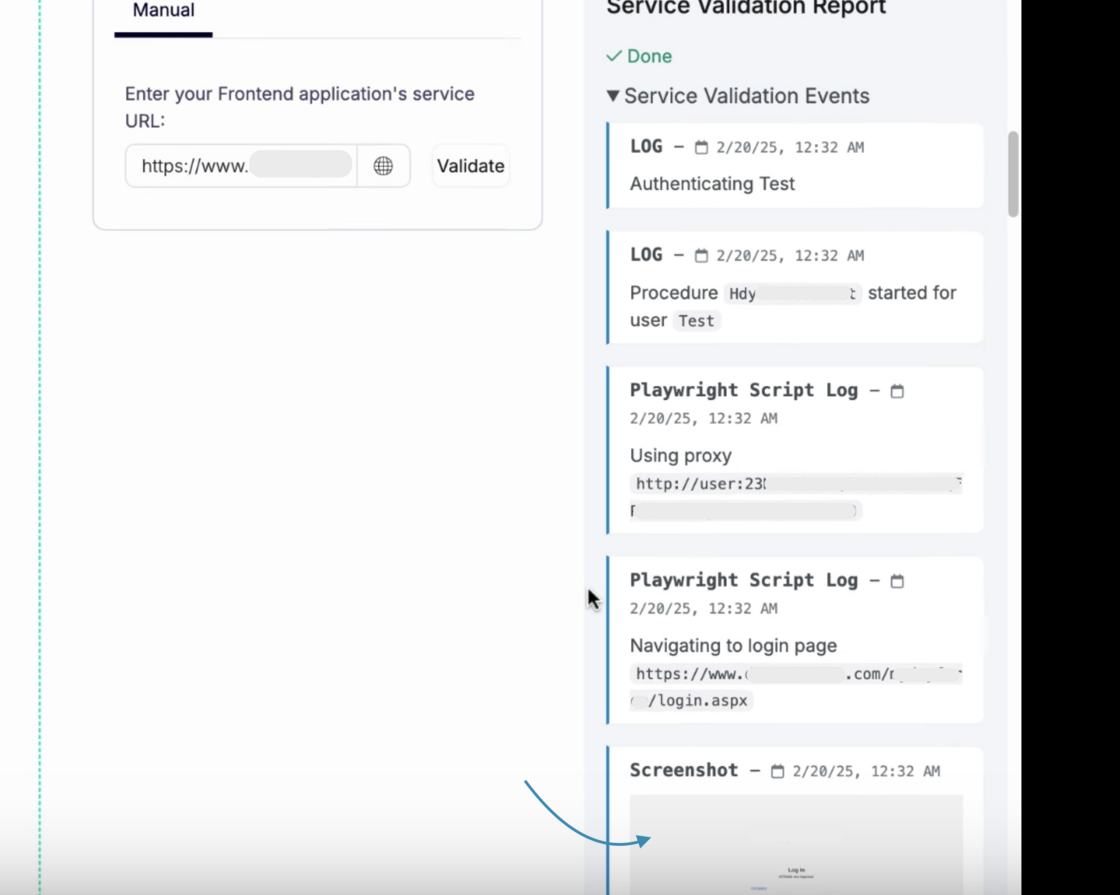
Escape goes further. When it encounters a login section, Escape's proprietary AI agent detects login fields and fills them in automatically. This approach also supports multi-user DAST testing across different roles and tenants.
Once logged in, you can view screenshots at each step. This helps you verify the authentication process or troubleshoot issues quickly.
Be certain — with this internal and secure technology, credentials are never sent to any external AI provider, ensuring complete privacy.
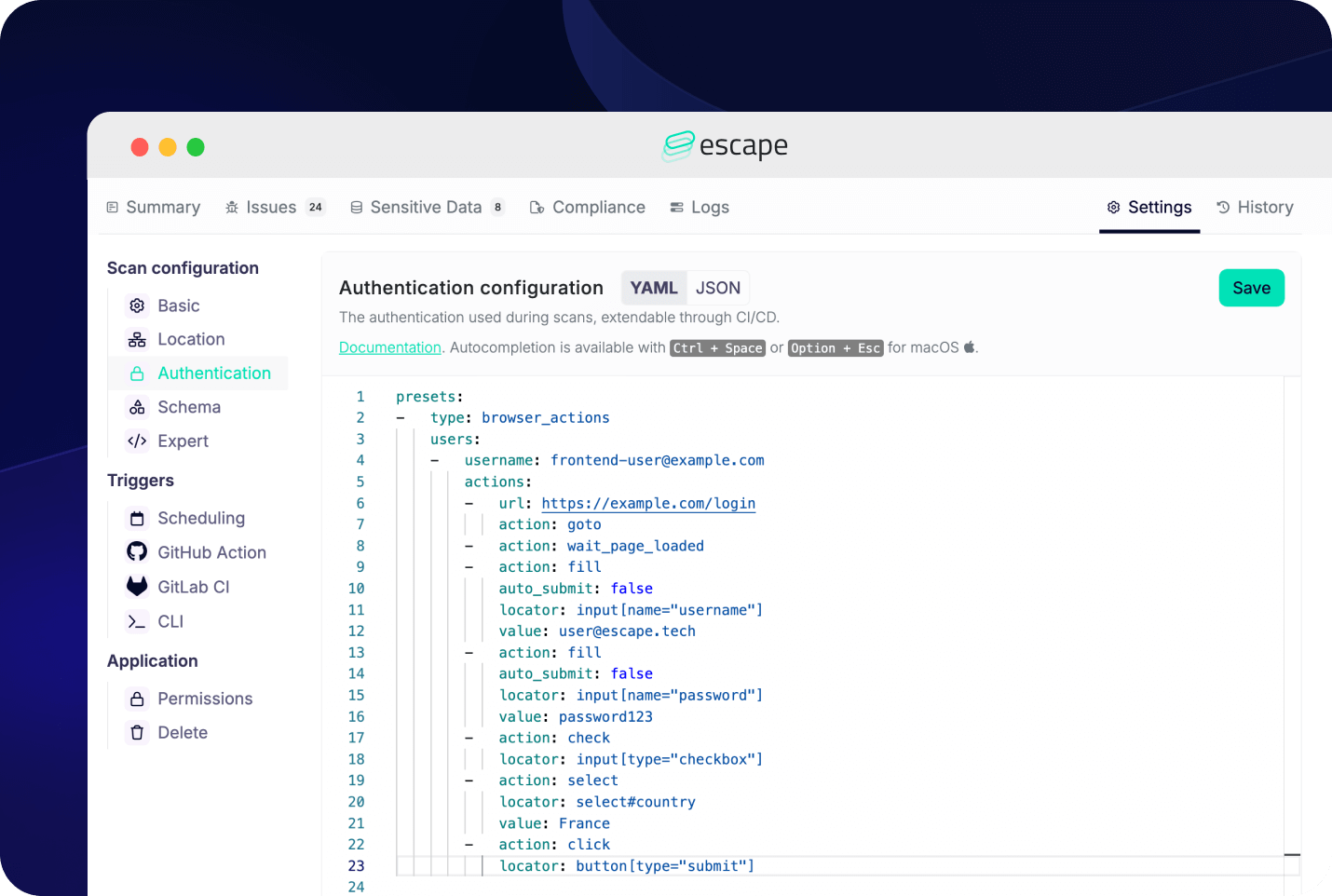
You can learn more about different authentication presets in Escape's documentation.
Security testing
Detectify finds vulnerabilities in web applications through fuzzing techniques. It can detect issues like XSS, SQL injection, and security misconfigurations. But it lacks native support for API testing and has limited ability to identify business logic vulnerabilities. This is a common limitation of traditional DAST scanners that rely on crawling methods rather than modern algorithmic approaches. As many AppSec engineers have noted, the current state of DAST has significant gaps.
Detectify's crawler is designed for web applications. It does not typically interact with API endpoints or gather the information needed for API testing. It might detect some API endpoints incidentally during crawling and fuzzing, but it is not actively scanning APIs.
One feature we're also lacking is like the able to scan the APIs because they're currently not in their scope...
Escape takes a fundamentally different approach. It uses a proprietary business logic security testing algorithm that detects complex vulnerabilities like Broken Object Level Authorization (BOLA) and Insecure Direct Object References (IDOR). It supports web applications and APIs, including GraphQL, and integrates with modern development tools and platforms for thorough application security testing across diverse environments.
“Escape is an innovative tool, and its results and algorithms are truly impressive. It was able to find GraphQL vulnerabilities that their competitors haven't seen. It also provides me with extensive testing capabilities." - Pierre Charbel, Product Security Engineer, Lightspeed
Escape's vulnerability scanning engine covers the OWASP Top 10 and OWASP API Security Top 10. It combines automated scanning with business logic penetration testing, a capability usually reserved for manual security assessments. Unlike traditional application security scanners and outdated DAST products that focus on known CVEs and misconfigurations, Escape conducts testing at the business logic level. It discovers vulnerabilities that real attackers would exploit in production, and it flags critical issues in real time. Benchmarks confirm these results: in DAST tools benchmark tests on VAmPI and DVGA,
Escape required significantly fewer requests than legacy scanners while detecting more business logic flaws.
Triaging issues & compliance
Detectify provides robust security testing for web apps. But the main reason users consider alternatives is the challenge with false positives. Former users report spending significant time filtering through noise and manually triaging findings. This makes vulnerability prioritization slow and frustrating for security teams. An effective vulnerability management lifecycle requires tools that reduce this noise, not amplify it.
Escape handles triaging differently. It automatically reduces false positives and prioritizes vulnerabilities based on exploitability and business context. The vulnerability prioritization funnel aligns issue severity with real-world risks.
We moved away from the traditional CVSS score-based system. Instead, Escape Severity considers multiple factors: the type of vulnerability, its exploitability, CVSS score, and other risk indicators. This makes sure you tackle the most critical issues first.
Scoring and categorization take into account:
- Whether the vulnerability can be reproduced with or without authentication
- Whether the endpoint is publicly exposed on the internet
- Whether the API schema is public
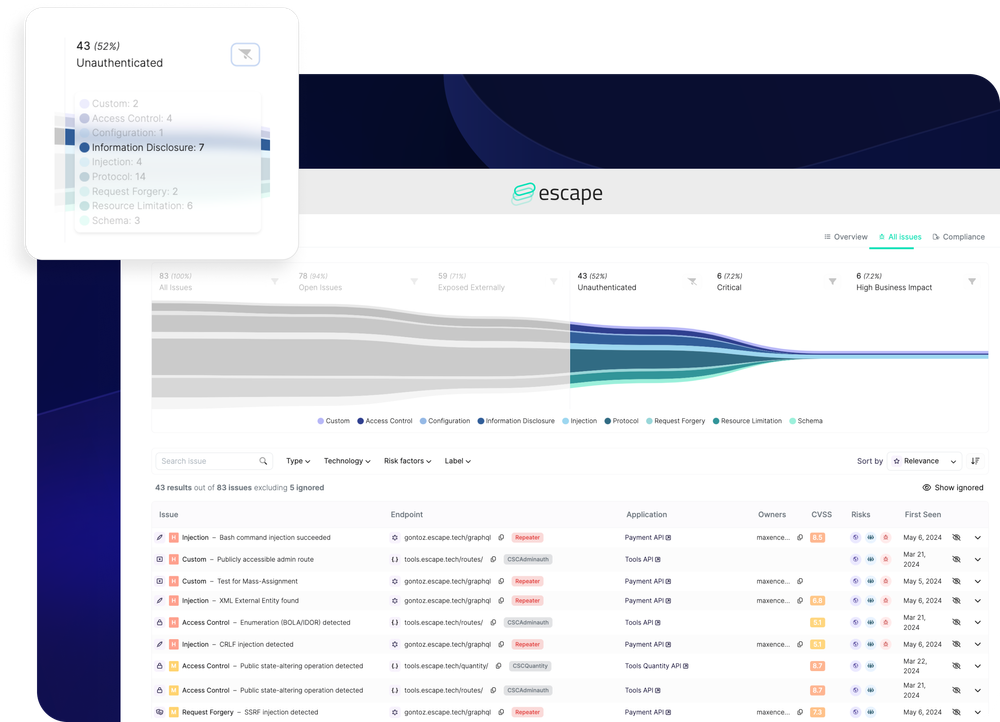
Compliance Framework Support
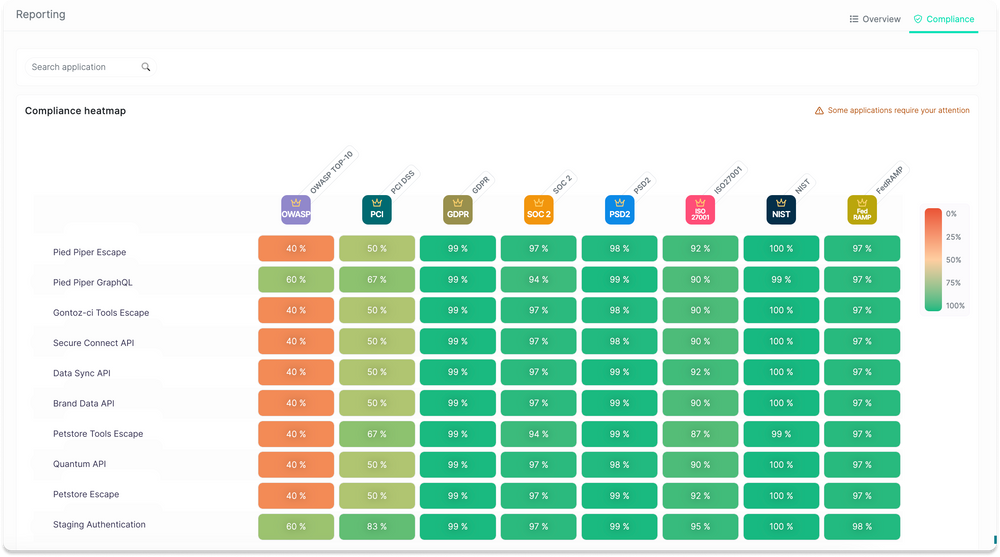
Compliance reporting is another key differentiator when selecting Detectify alternatives. Escape maps vulnerability findings directly to compliance frameworks through its Compliance Matrix feature. Security teams can then generate audit-ready reports for compliance reviews and regulatory submissions.
| Framework | Escape | Detectify |
|---|---|---|
| SOC 2 | Mapped (Escape is SOC 2 Type II compliant ) | Partial, PDF reports only |
| ISO 27001 | Mapped | Partial |
| PCI DSS | Mapped (how API security fits PCI compliance requirements | Limited |
| HIPAA | Mapped | Partial |
| GDPR | Mapped | Partial |
Escape's reporting and analytics go beyond basic PDF exports. The Compliance Matrix provides a unified view across all frameworks with real time tracking of your compliance posture. For companies in regulated sectors like financial services or healthcare, where audit cycles and regulatory data requirements drive the application security testing roadmap, this is a significant advantage.
Remediation guidance for developers
According to former Detectify users, the tool provides recommendations on how to fix vulnerabilities. But the feedback is clear: "it's very generic and not catered to exactly what the issue was found. And it's a very generic recommendation."
Here you can find an example from the Detectify documentation on what details look like:
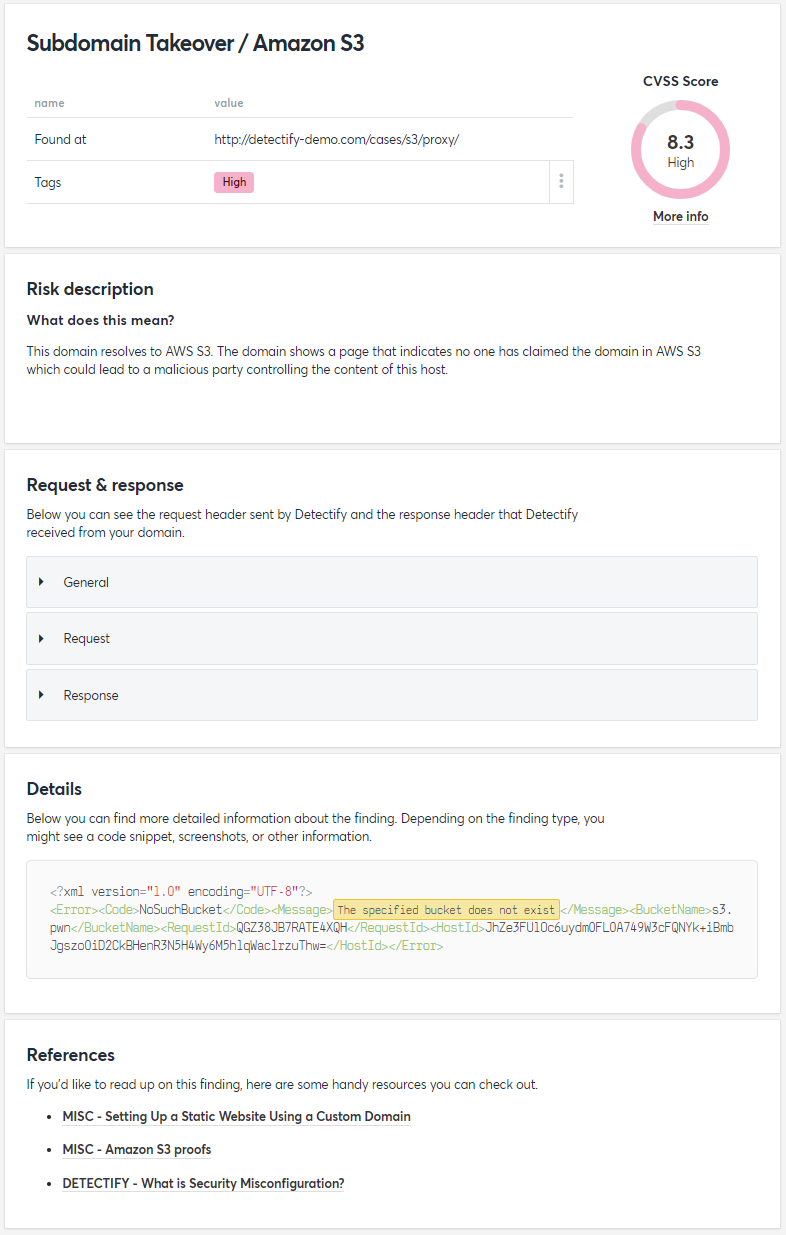
Escape takes a different approach. It provides detailed remediation code snippets tailored to each development framework, for APIs and front-end applications alike. The AI-powered exploit validation and remediation system generates framework-specific fixes that developers can apply immediately.
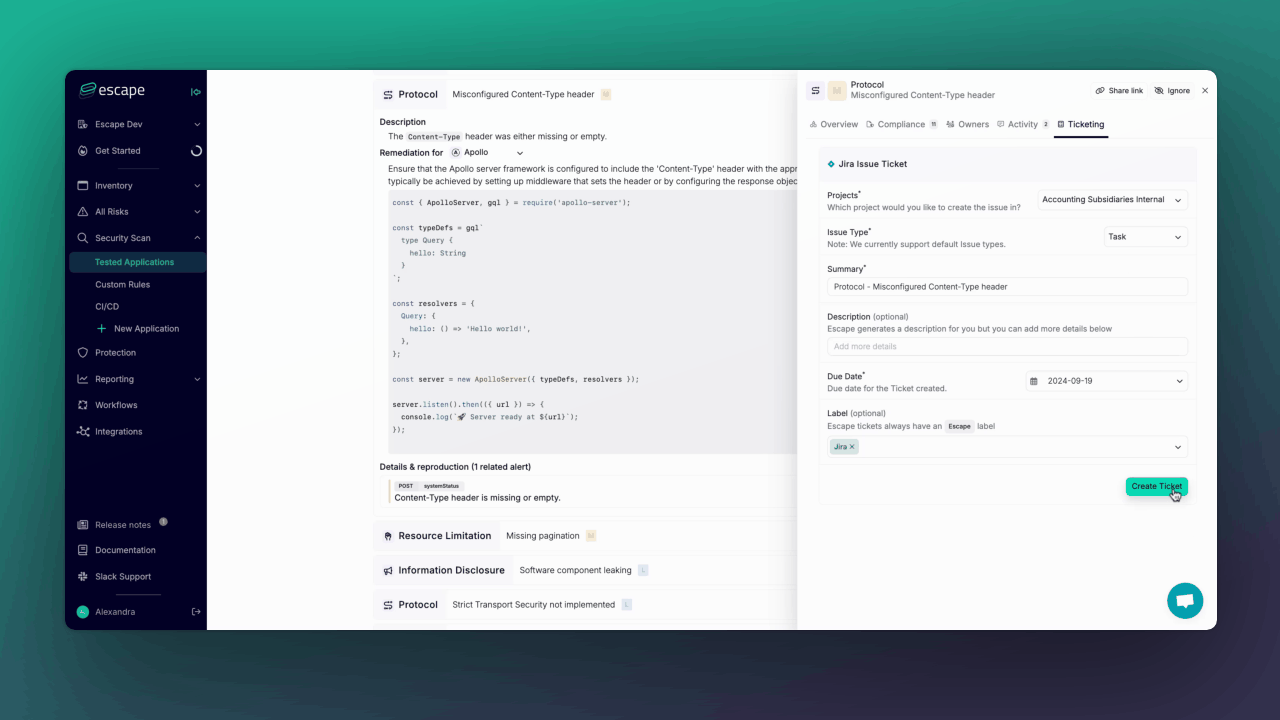
Security teams can automatically share these code snippets with engineers through pre-filled remediation steps in Jira. This saves time and speeds up resolution. Developers get the fix in hand before they even open the ticket.
CI/CD Integration and Enterprise Readiness
Native CI/CD integration matters when choosing the right alternative to Detectify. Escape integrates directly with GitHub Actions, GitLab CI/CD, Bitbucket Pipelines, Jenkins, Azure DevOps. It enables automated scanning on every pull request or scheduled deployment. Teams looking to implement DAST in their CI/CD pipelines can get started quickly: the tool can be configured in minutes and automatically triggers vulnerability assessment scans when code changes are discovered.
Enterprise security teams managing large application portfolios across cloud environments need more than scanning. The platform supports multi-tenant management, SSO/SAML, role-based access control, and full API access for automation across systems. These are key features that traditional DAST products often lack. They matter when evaluating a DAST tool for an entire organization. For teams building a business case for replacing their DAST tool, Escape's enterprise capabilities are a strong argument.
Detectify offers CI/CD integration through Zapier connectors (GitHub, GitLab, Azure DevOps). The configurability is more limited, there is no API testing in the pipeline, and enterprise governance features are fewer.
How to Choose the Right Detectify Alternative
Choosing the right alternative to Detectify depends on your security requirements, team profile, and technical environment. With several products on the market, selecting Detectify alternatives requires clear thinking. Below are the criteria for Detectify alternatives that every company should evaluate. For a broader perspective on how to conduct an application security audit, start with your coverage gaps.
Key Selection Criteria
1. Coverage type. Do you need web application scanning only, or also API security testing and internal asset scanning? If APIs matter, Escape provides native coverage that Detectify lacks. Traditional scanners that only test external web apps leave entire API structures and internal systems untested. Understanding the differences between SAST and DAST helps clarify where each tool fits.
2. Authentication complexity. Simple login forms work with most tools. But if your applications rely on complex OAuth, SAML, or multi-step authentication flows, you need a tool with advanced auth handling. Outdated DAST methods often fail on modern architectures that use authentication, authorization, and access control layers. Escape handles these flows natively.
3. Vulnerability detection depth. Surface-level automated scanning catches common vulnerabilities like SQL injection and XSS. Business logic testing (BOLA, IDOR, access control) catches the critical issues that actually lead to breaches. Escape's scanner conducts both. It goes beyond black box fuzzing.
4. Compliance and reporting. If your company needs audit-ready reports for SOC 2, ISO 27001, PCI DSS, HIPAA, or GDPR, check whether the tool maps findings to these frameworks. Escape provides a Compliance Matrix with real time tracking. Detectify offers PDF reports without a unified compliance view.
5. Cloud and scale. Multi-cloud environments (AWS, Azure, GCP) and large application portfolios require a platform that scales. Escape supports multi-tenant management, SSO, and RBAC for enterprise security teams managing data across complex architectures. The ROI calculator can help quantify the value for your organization.
6. Budget and pricing. The cost of Detectify alternatives varies. Detectify starts at $70/monthly for application scanning and $249/month for surface monitoring. A 14-day free trial is included. Escape offers a PoC with contact-sales pricing for Detectify alternatives at enterprise level. If you need affordable Detectify alternatives, open-source options like OWASP ZAP exist but lack enterprise features (see below). Request a demo to compare pricing before committing.
Choose Escape If... / Detectify May Suffice If...
This Detectify alternative selection guide summarizes how to choose based on your profile:
Conclusion: Is Escape DAST the Right Alternative to Detectify?
Escape is the strongest Detectify alternative in 2026, for three reasons:
- Native API security testing with proprietary business logic vulnerability detection (BOLA, IDOR, access control). Detectify explicitly does not support this.
- Full coverage of both external and internal applications, including assets behind VPNs and firewalls. It scans your entire attack surface.
Advanced authentication handling with OAuth, Cognito, Playwright, and AI-powered login detection. Detectify cannot match this.
Both Detectify and Escape DAST are powerful dynamic application security testing solutions designed for modern applications. Detectify is a solid tool for teams that need straightforward vulnerability scanning and surface monitoring for public-facing assets. But it has clear limitations in API testing, complex authentication flows, and internal asset scanning. These gaps make it insufficient for modern application architectures.
Escape DAST fills those gaps. Its proprietary business logic security testing algorithm, native API security support, and agentless application discovery give it a broader security posture for organizations with complex, modern infrastructures. If you need in-depth API security, native integration into modern tech stacks, or the ability to scan both internal and external assets, Escape DAST is the better choice.
Rated 5.0/5 on G2 by security professionals, Escape is trusted by companies and security teams that need more than basic vulnerability scanning. From API-first startups to enterprise organizations managing complex cloud environments across their entire infrastructure.
Ready to see how Escape performs on your own applications? Book a demo for a guided walkthrough.
Find and remediate business-critical vulnerabilities for modern web apps and APIs, internal and external
Integrating seamlessly into your modern stack
Book a demo with our product expertFrequently Asked Questions
What are the best Detectify alternatives in 2026?
The top-rated Detectify alternatives include Escape (best for API security and business logic testing), Intruder (best for startups and SMBs), Invicti (best for full ASPM), and HostedScan (most affordable). Escape is the strongest application security scanner of the group, with native API support, business logic vulnerability detection (BOLA, IDOR), and internal asset scanning. These are three areas where Detectify has significant limitations.
Is Escape a good alternative to Detectify?
Yes. Escape is rated 5.0/5 on G2 and is the top rated Detectify alternative for organizations that need API security testing, business logic vulnerability detection, and internal asset scanning. The platform also provides advanced authentication handling, native CI/CD integrations, and compliance-ready reporting. Detectify either lacks or only partially supports these capabilities.
Are there free alternatives to Detectify?
Yes. Free Detectify alternatives include OWASP ZAP and Nuclei for basic vulnerability scanning. But free tools lack enterprise features like compliance reporting, SSO, business logic testing, and dedicated support. Escape offers a free trial with full platform access and no credit card required.
Does Detectify support API security testing?
No. Detectify explicitly states in its documentation that it does not encourage users to scan API endpoints. Its crawler cannot interact with API-only applications. Escape provides native API security testing for REST, GraphQL, and SOAP APIs. It includes automated API schema generation and business logic vulnerability detection. These are critical capabilities for modern API-first architectures.
Can Escape scan internal applications behind a VPN?
Yes. Escape's Private Locations feature uses a repeater proxy to scan internal applications behind firewalls or VPNs. No agents on your infrastructure are required. This proactive approach to application security testing covers your entire attack surface. Detectify only scans publicly exposed, internet-facing assets.
What compliance frameworks does Escape support?
Escape maps vulnerability findings to SOC 2, ISO 27001, PCI DSS, HIPAA, and GDPR through its Compliance Matrix feature. It generates audit-ready reporting for security teams. The platform provides real time tracking of your compliance posture. Detectify provides PDF reports but lacks a unified compliance view.
How does Escape compare to Detectify for CI/CD integration?
Escape integrates natively with GitHub Actions, GitLab CI/CD, Bitbucket Pipelines, Jenkins, Azure DevOps. It enables automated scanning on every pull request. Teams can follow the guide to implementing DAST in CI/CD pipelines for step-by-step setup. The tool can be configured quickly and automatically triggers scans when code changes are deployed. Detectify offers CI/CD integration through Zapier connectors. This adds complexity and limits configurability.
💡 Want to learn more? Discover the following articles:
