How Gorillas's GraphQL API was leaking data from 10000 customers

German on-demand online grocery delivery company Gorillas took the industry by storm, guaranteeing delivery in under 10 minutes and gaining massive popularity throughout the pandemic.
Founded in May 2020, Gorillas rapidly spread to dozens of European cities and America. After only three funding rounds, the last of which was in October 2021, the startup was valued at 1 billion dollars, making it the fastest German startup to reach unicorn status (after only nine months).
But in our eyes, this was too fast. Nine months of development for a product of that scale is the recipe for a vulnerable application: security is the first thing to be overlooked when compromising for speed of development.
Around May 2021, just after it reached unicorn status, a vulnerability report was dropped on Gorillas, which we'll be covering in this article.
You can find the full article about the report here.
Report Content
The report uncovered that Gorillas' system was built by Eddress, a company based in Pakistan and Lebanon that offers white-label courier software. A small search led to an admin portal for Gorillas/Eddress: portal.gorillas.io
Like any other admin portal, the visitor will be presented with a login page, but what was different about this one was that JavaScript loaded in the login page, disclosing the GraphQL endpoint.

Introspection was directly fetched, and revealed the following queries:
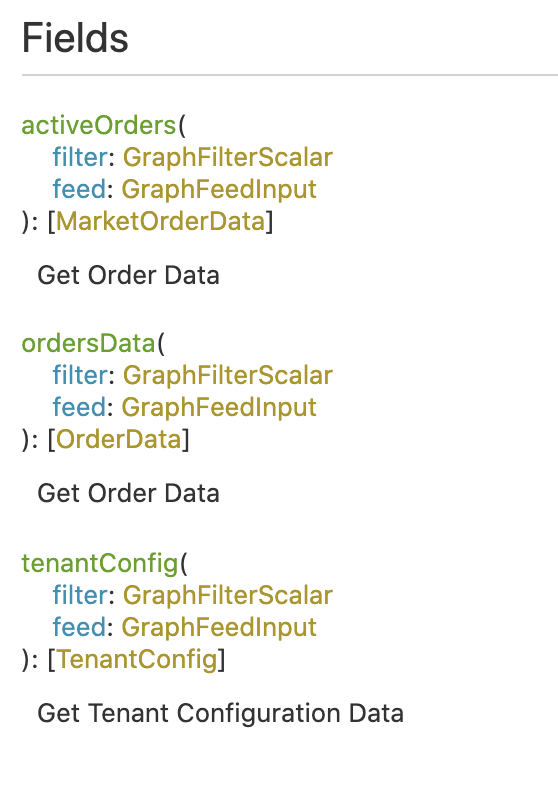
All of the queries had been correctly secured except tenantConfig, which anyone can access without any restrictions, and that was very... informative :)
Data in the tenantConfig query included API keys and URLs for various services used by the Gorillas/Eddress infrastructure. Some examples include the slack webhook URL and the API keys for Sendgrid.
Slack URLs allow posting messages to specific Gorillas Slack channels: “Everybody gets a raise!”
While this may seem like a manageable threat, Sendgrid API keys, on the other hand, reach a whole new level of risk. They allow anyone possessing them to send emails on behalf of Gorillas, and I'll leave the wide variety of phishing possibilities to your imagination.
But there's still more to come. Going back to the GraphQL endpoint, it turns out that any authenticated user (or anybody who signs up, for that matter) has access to all the data.
This resulted in an alarming amount of leaked data: 1,000,000 orders, the associated 200,000 customers, and information about the employees related to these orders. This data included everything that one would expect from the customer's address and phone number to some payment details, and went as far as a link to photos of the front door/bell plate, causing further commotion.
Conclusion
Applications are being developed at an increasingly fast pace, but security seems to be lagging behind. To make up for this, we've been working on GraphQL endpoints protection for the past years in hopes that security issues won't hinder any more startups in their quest to reaching unicorn status.
Escape.tech offers blazing fast security for endpoints along with algorithms and checks specifically designed to prevent this type of incident from reoccurring, all with a click of a button.
Wanna know more about Security? Check out our blog post "9 GraphQL Security Best Practices" and learn how to build safe GraphQL APIs.
