Graphinder: lightweight and blazing fast GraphQL endpoint finder
Introducing Graphinder, a lightweight and blazing fast GraphQL endpoint finder, making penetration testing on GraphQL much faster ⚡️
Penetration Tests for GraphQL
Penetration tests are used to evaluate the security of infrastructures such as GraphQL APIs, by exploiting vulnerabilities in a safe environment.
A vaccine for your application if you will 💉
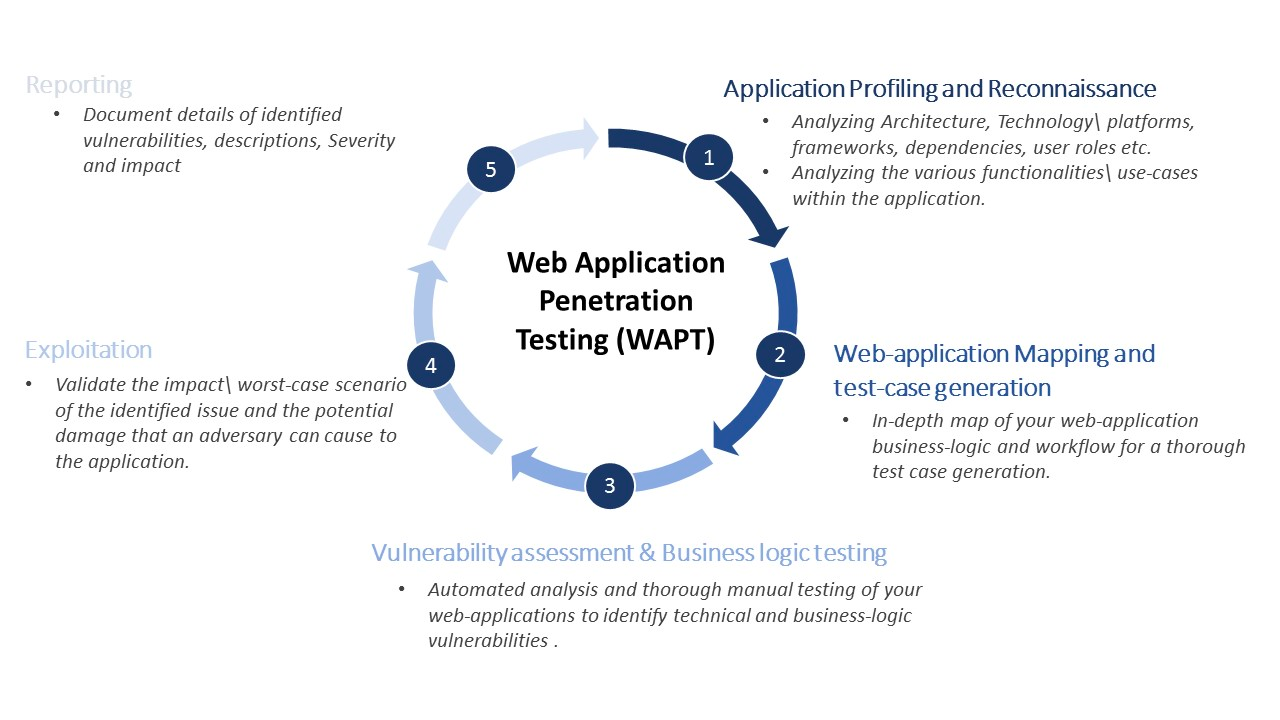
These tests are usually conducted on big infrastructures exposed to black hat hackers and could lose big in case of a vulnerability exploit. Because pentesting requires a very specific set of skills, they are most often delegated to external entities (cybersecurity experts) and follow a conventional routine.
Here’s what the process usually looks like:
- Planning: defining clear goals and scopes for the operation (eg. which environment do we test, staging or development?).
- Discovery: gathering information about the infrastructure - IP address, dependencies, API protocol, endpoints, etc.
- Penetration: trying different strategies based on the gathered information to find and exploit vulnerabilities.
- Analysis: creating a report on the discovered vulnerabilities and the strategies used to exploit them.
- Remediation: suggesting fixes for these security vulnerabilities.
At Escape, we’re building automated security scans for GraphQL APIs using smart fuzzing and complex graph algorithms. In essence, we are building GraphQL pentesting as a service.
But we are open-source lovers so we regularly contribute and make our work public during our dedicated open-source day.
So far, we’ve shared:
- graphql.security a free security quick scan for GraphQL APIs,
- mookme.org a git hook, language-agnostic utility for monorepos.
and we are super excited today to introduce Graphinder 🎉
Blazing Fast and Automated GraphQL Endpoint Discovery
The success of a penetration test relies on the success of the discovery phase.
In the context of a GraphQL API, finding every endpoint can be a tedious and extremely long task.
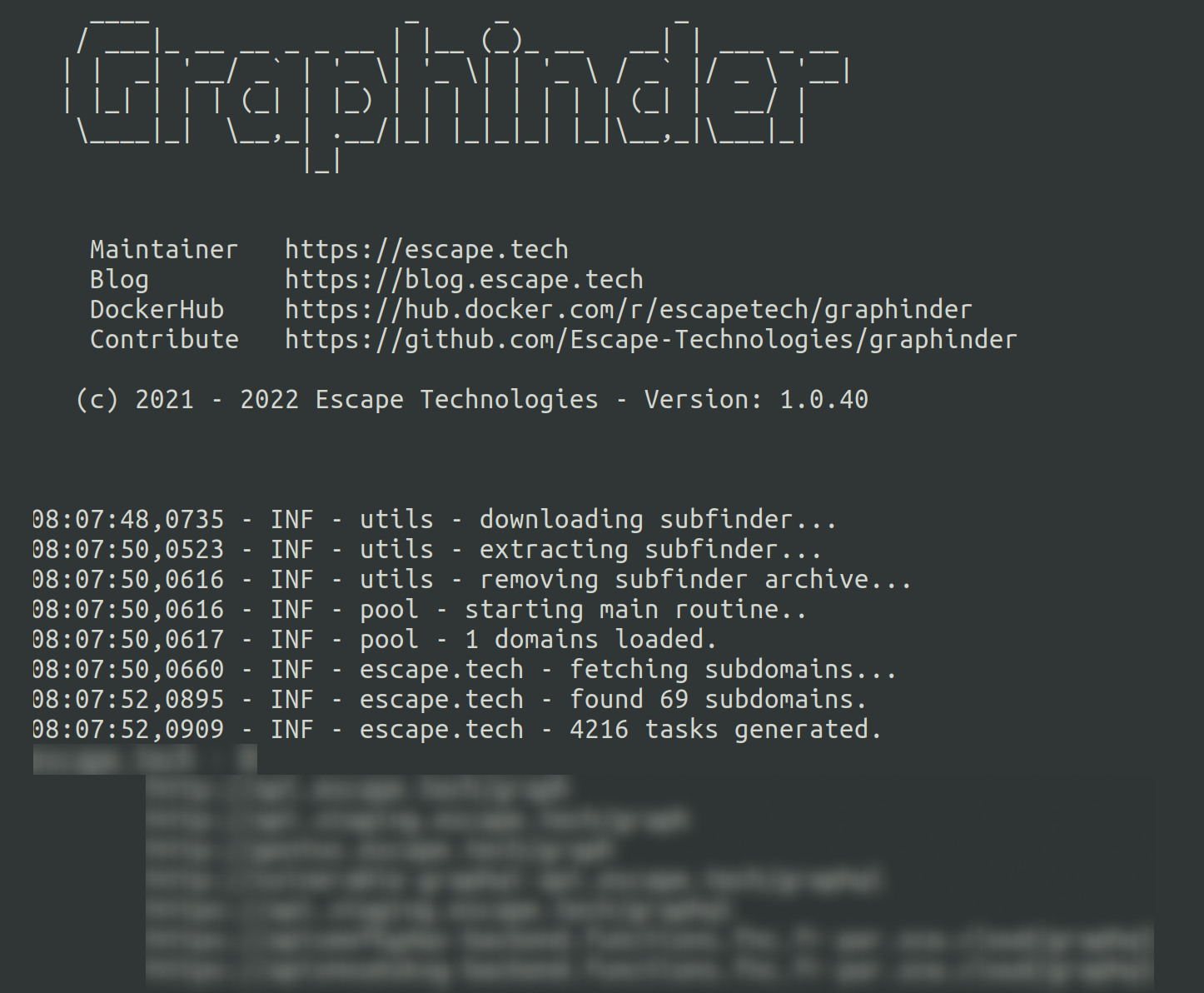
Graphinder uses subdomain enumeration, script analysis and brute-force techniques to find every GraphQL endpoint in minutes, not hours!
Not only that, the Docker image is only 23Mb 🪶
Combined with other open-source projects such as dolevf/graphwoof - a utility to identify the GraphQL engine used behind an endpoint - discovery is becoming more accessible for GraphQL pentesters!
Getting Started
It only takes 3 simple steps to get started with Graphinder.
1. Clone the repository on your local machine and run the installation script:
git clone <https://github.com/Escape-Technologies/graphinder.git>
cd Graphinder
./install-dev.sh
2. Start the virtual environment:
poetry shell
3. Enjoy!
graphinder -d example.com
Conclusion
We barely touched the surface of GraphQL Pentesting, but if you want to learn more tweet at us @EscapeTechHQ and we’ll do a dedicated post 😉
In the meantime, make sure to checkout Graphinder, leave us a star, and consider contributing!
Food for thoughts
Wanna know more about automated GraphQL security testing? Read our blog article "How to test your GraphQL API?".
