Fortune 1000 at risk: How we discovered 30k exposed APIs & 100k API vulnerabilities in the world’s largest organizations

Hey there!
Next week, social media will be flooded with Thanksgiving feasts (and Black Friday deals). But before you dive into the holiday shopping madness, the Escape team has prepared a special treat for you—not a Black Friday deal on Escape, of course, but rather some impressive findings on API security risks among Fortune 1000 and CAC 40 organizations.
And trust us, the findings aren’t just “spicy” like your Thanksgiving stuffing—they’re quite scary...
Using a combination of advanced subdomain enumeration, AI-driven fingerprinting, and OSINT techniques, Escape’s security research team crawled the domains of Fortune 1000 and CAC 40 organizations. We discovered 30,784 exposed APIs (28,544 within Fortune 1000 companies). Next, we programmatically generated missing API specifications and began scanning exposed API services, revealing a staggering 107,368 vulnerabilities—2,038 of which (1,830 - among Fortune 1000, 240 - among CAC 40) were classified as highly critical due to broken authentication and security misconfigurations.
You can review the complete results in our comprehensive report. In this blog post, we’ll give you a sneak peek at the key findings in Fortune 1000 and share the methodology behind them. So, grab a cup of cider and settle in—you won’t want to miss this one!
Methodology
Data Gathering Strategy
In our comprehensive analysis, we aimed to examine API security measures across a broad spectrum of domains. We selected domains from two primary sources:
- Fortune 1000: A list of the 1000 largest public companies in the United States, ranked by revenue. We excluded several very large tech companies like Amazon, Google, and Meta to avoid skewing the results.
- CAC 40: A capitalization-weighted index of the 40 most significant stocks among the top 100 companies by market cap on Euronext Paris.
While this approach provided a substantial data set, we recognize potential biases. Larger domains with extensive resources may employ stronger security measures, potentially leading to fewer vulnerable APIs. However, our study focused on the largest American companies without specifically accounting for this bias.
Alternatively, with over 365 million domain names reported across the internet, our sample size becomes relatively small, potentially leading to greater volatility in the number of findings.
The data collection was a one-time process. During the collection, we encountered several limitations. To respect legal and ethical boundaries, we deliberately excluded certain types of domains. This decision ensured that our study aligned with ethical norms for web crawling and data collection practices, prioritizing responsible research standards.
In-Depth API Discovery Process
After finalizing our domain list, we gradually added these domains to initiate a comprehensive scan of exposed APIs. We examined not only the primary domains but also dived into the numerous subdomains associated with each. This approach enabled us to achieve a thorough and granular discovery process.
We used a sophisticated combination of techniques to identify and inventory APIs by scanning exposed source code implemented within the Escape platform:
Subdomain enumeration
First comes the subdomain enumeration. This process involves scanning for all subdomains associated with the main domain you previously entered into the platform. Subdomains often host APIs or services that may not be immediately apparent. By identifying these subdomains, we can uncover additional endpoints that might otherwise be missed. This initial step lays the foundation for a comprehensive discovery process.
AI-powered fingerprinting
Once subdomains are identified, we employed AI-powered fingerprinting to recognize and classify the APIs. Fingerprinting involves analyzing various characteristics of the APIs, such as their structure, endpoints, and response patterns. The AI algorithms that we also integrated in Escape can detect and categorize different API types (REST, GraphQL, gRPC) with high accuracy. This machine learning-based approach ensures that APIs are identified and classified correctly, even if they have unique or non-standard configurations.
OSINT techniques
We also leveraged Open Source Intelligence (OSINT) techniques. OSINT involves gathering and analyzing publicly available information to enhance the discovery process. By examining code repositories, documentation, and other public resources, we could identify additional API endpoints and services. This technique helps in discovering APIs that are not directly exposed but can still be found through public information.
Through this multi-layered process, we discovered 158,079 subdomains, allowing for extensive coverage and a highly detailed analysis. This broad scope provided a deep view into the exposure and security practices around APIs across various industries.
Automated API Documentation Generation
One of the most challenging aspects of our study was ensuring we had API specifications to effectively scan newly discovered exposed API services for vulnerabilities.
Having an OpenAPI Specification (OAS) is particularly beneficial as it provides a standardized, machine-readable format for documenting RESTful APIs, promoting clarity and consistency across services.
Through our initial scan, we located 4,547 exposed API specifications, so we had to generate most of the specifications ourselves. This process involved parsing the Abstract Syntax Tree (AST) from the code to create dynamically detailed and accurate API specifications.
Luckily, Large Language Models (LLMs) have recently become extremely good at analyzing and generating code. Moreover, they show great performance across a wide variety of code languages, frameworks, and coding styles, which is exactly what we want for framework and language-agnostic OAS generation software. Finally, LLMs can also leverage information in code comments, which the traditional static analysis approach cannot do.
In our current approach, integrated into Escape’s platform, we focused on two key areas:
- Semantic Analysis: We identify essential code fragments using custom rules (e.g., specific Semgrep patterns), optimizing the data sent to the LLM and enhancing prompt quality.
- Specification Generation: The LLM processes each identified fragment to generate precise OAS methods, with contextualization ensuring accuracy by resolving dependencies and references within the code.
This method enabled our platform to not only generate API documentation but also to continuously monitor and detect any changes or versions in the API documentation over time.
Final step - API Security Scanning
After the comprehensive specification generation process, the final step is API security scanning. Using Escape’s Dynamic Application Security Testing (DAST) security scanner, we conducted an in-depth analysis of each identified API endpoint to detect potential vulnerabilities and risks.
Escape’s DAST approach is specifically designed for API security. At the core of the tool is a proprietary algorithm that combines static and dynamic analysis to deliver precise, high-confidence results. The algorithm operates in multiple stages:
- Contextual Analysis: The algorithm first conducts a contextual analysis of each endpoint, identifying the API’s structure, parameters, and dependencies. This allows it to adapt its scanning approach to each specific API, ensuring relevance and reducing false positives.
- Fuzzing and Payload Injection: In the next stage, the algorithm uses fuzzing techniques to test each endpoint by sending random, unexpected, or malformed inputs. This helps identify weaknesses like input validation flaws, injection vulnerabilities, and misconfigurations. The algorithm adapts these payloads based on real-time feedback, simulating complex attacks more effectively than conventional static methods.
- Behavioral Monitoring: As it interacts with each endpoint, the algorithm monitors response patterns and behaviors to detect anomalies. By observing responses over multiple interactions, it can identify issues such as data exposure, error leakage, and misconfigured permissions, providing insights into the API’s security posture.
- Risk Prioritization: Escape’s DAST concludes with an analysis that ranks detected vulnerabilities based on risk and classifies them based on the metric named Escape severity.
Key findings - Fortune 1000
Here is what we discovered among Fortune 1000 companies:
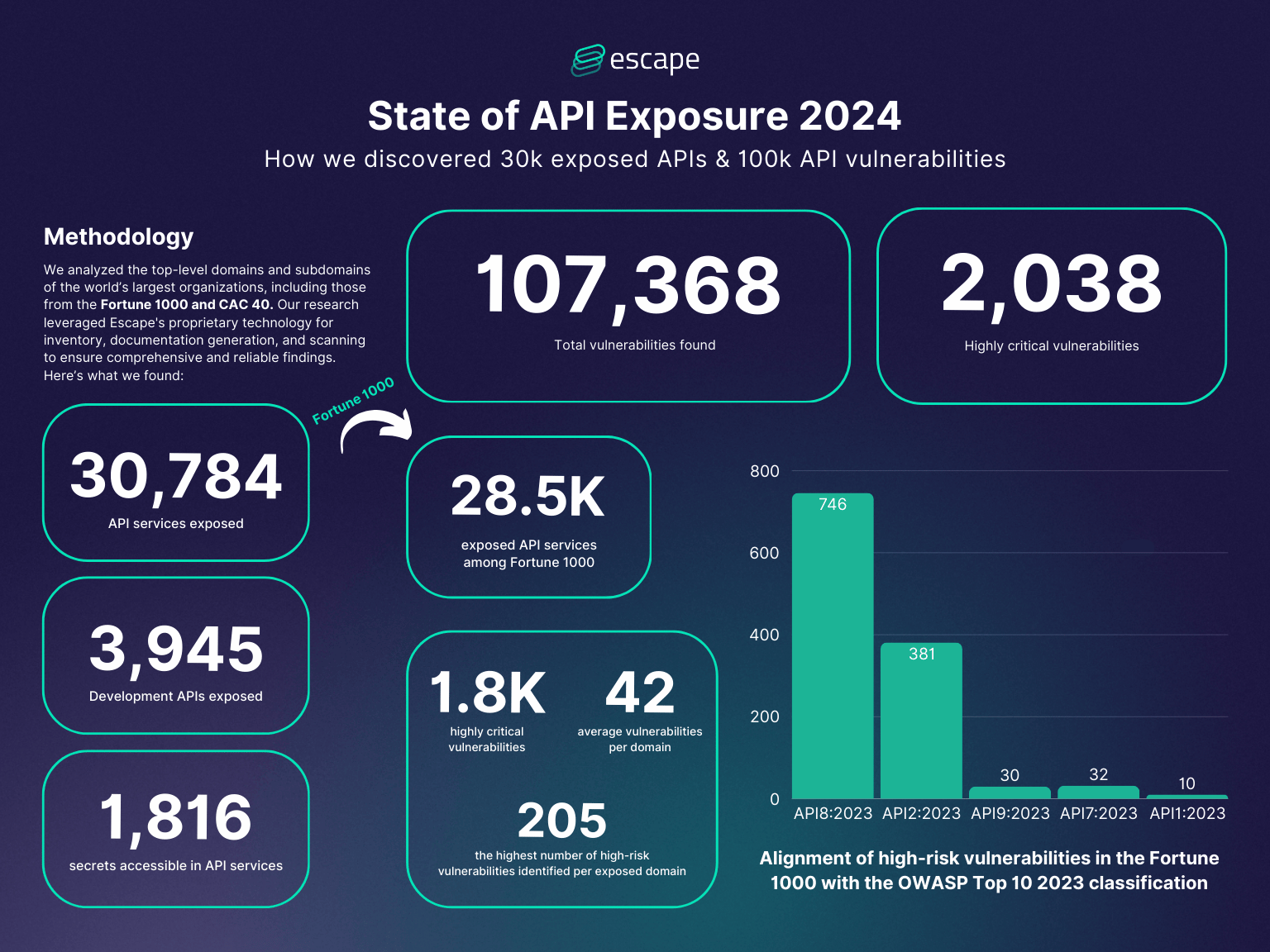
- Exposed APIs: Over 28,000 exposed APIs were identified across Fortune 1000, with some organizations revealing hundreds of vulnerable endpoints within a single domain.
- Critical Vulnerabilities: Fortune 1000 companies accounted for 1,830 highly critical vulnerabilities
- Development API Risks: Among Fortune 1000 companies, 3,650 development APIs were exposed. These APIs, which often bypass production-level security, present potential entry points for unauthorized access.
- Exposed API Secrets: More than 1,800 highly sensitive API secrets—including access tokens, API keys, and authentication credentials—were found exposed, significantly increasing the risk of unauthorized access and system compromise.
Conclusion
Securing all your APIs is hard. It’s even harder when you don’t know what you have to secure, want to ship (insecure) APIs too fast in the wild and have to monitor them at a large scale. Your organization is now not only prone to data breach risks but also to severe financial implications.
Our study reveals that over 100,000 vulnerabilities are present across Fortune 1000 and CAC 40 companies, with 1,800 classified as highly critical, directly impacting some of the largest organizations globally.
One of the most striking findings was the extensive exposure of vulnerable development APIs and the high level of overall vulnerability criticality. This highlights the real and present dangers for each organization and the necessity of thoroughly testing applications both before and after deployment.
Organizations must respond fast, adopting best practices for risk mitigation and integrating continuous, automated testing of their applications.
Not sure where to start? Conduct a comprehensive API audit, deactivate unused or duplicate APIs, recheck for exposed API secrets, and leverage automated testing tools like Escape. We've compiled a comprehensive list of recommendations in our report.
Need guidance tailored to your specific needs for securing APIs at scale?


