Escape DAST vs Snyk DAST (Probely): Complete Comparison 2025
Discover the differences between these tools for Application Discovery and DAST.

Finding the right tools for your AppSec team can be a daunting task. Especially, when it comes to testing modern applications like SPAs, APIs, and Microservices.
Both Escape and Probely DAST (acquired by Snyk — now considered as Snyk DAST ) offer solutions tailored to application discovery and DAST (Dynamic Application Security Testing) scanning workflows, but their approaches differ significantly. This comparison aims to help you navigate these differences, highlighting how each tool supports your journey from application discovery to remediation.
Dive right in!
Head-to-head comparison: Escape vs Probely (Snyk DAST)
Escape and Probely (Snyk DAST) cater to different needs, whether you're managing multiple brands, scaling across large teams, or simply looking for simple DAST capabilities. Both are designed to support modern applications with varying depth. Escape focuses on deep application discovery and advanced testing with developer-centric remediation, Probely is a simple DAST tool that comes, however, with multiple integrations with DevSecOps workflows. Understanding these distinctions is crucial for making an informed decision that aligns with your organization's priorities.
We've built this comparison based on the following sources:
- Official websites
- Demos on YouTube and official documentation
- Feedback from security professionals (whether Probely's and Escape's current customers or not)
TLDR
Probely (Snyk DAST)
Best if you want a simple DAST solution with basic discovery capabilities
Pros
- Straightforward classic DAST scanning
- Backed by Snyk’s ecosystem
- Complete integrations with ticketing systems and platforms like Defect Dojo
- Provides remediation explanations that are more detailed compared to some DAST competitors
Cons
- Limited asset discovery capabilities (focused on external domain discovery; only connections with Cloudflare & AWS, no in-depth discovery from code)
- API specifications must be uploaded manually to start security testing
- No possibility to implement custom security tests
- No support for business logic testing
- Lack of code owner identification
- Offers detailed remediation guidance but no code-level fix suggestions
Escape
Best if you need advanced discovery, scalability, and business logic testing—ideal for managing workflows across multiple teams in complex or technical security environments
Pros
- In-depth application discovery, including internal API discovery from code
- Automated API documentation generation that helps you to launch scans right away and reduces the need for maintenance of scans
- Custom security tests that do not require maintenance
- Business logic testing: finds IDORs, SSRFs and Access control issues in modern web applications
- Actionable remediation code snippets for developers
- Integrations with advanced tools like Wiz
Cons
- Fewer integrations with ticketing & DevSecOps systems compared to Probely
- Advanced feature sets require specialized knowledge
In-depth feature comparison
Application Discovery
Probely: Focuses on external asset discovery from a domain perspective. While it includes limited integrations for asset discovery, it does not support discovery from source code or API specification generation.
Probely supports 3 options for discovery:
- Simple discovery from a domain name
- By connecting to Cloudflare
- Via AWS Route 53 connection
Escape: provides in-depth application discovery from multiple sources:
- Agentless discovery of externally exposed applications through a combination of different techniques
- API discovery from source code
- Escape Inventory also ingests data from various types of integrations to enhance the quality of the results like API gateways (Apigee, Kong Gateway, Kong Konnect) or Developer tools like Postman (a complete list can be found here)
Escape uses AI-powered fingerprinting to also classify applications by analyzing various characteristics, including structure, endpoints, and response patterns. This AI-based approach enables high-accuracy detection and categorization of various application types, even for unique or non-standard configurations.
Additionally, Escape reconstructs API schemas by parsing the Abstract Syntax Tree (AST) of both frontend and backend source code.
Security Testing
Complexity of scan setup
Probely: Manual scan setup for APIs: Users need to upload API specs manually for scanning (How to configure and scan an API). If you're sure that your API specs are always up to date, then set up is quite simple.
Escape: Automates scan setup with API spec generation. Once generated, API schemas are seamlessly integrated into the DAST process, reducing manual effort. Users can initiate dynamic application security testing with a simple click, employing the latest schema versions to ensure thorough and accurate testing coverage.
Depth of algorithm findings
- Probely: Focuses on detecting common vulnerabilities (Types of vulnerabilities). It is enough if you're looking for surface scans and don't need to go more in-depth.
- Escape: Advanced detection algorithms identify a broader range of vulnerabilities, including complex business logic flaws like IDORs, SSRFs, and Access control issues in modern web applications. For all modern applications, Escape handles testing them natively. You can learn more about Escape's proprietary business logic testing algorithm here.
Scale your business logic security testing quickly with Escape DAST
And see how it compares to Probely
Get a demo with our product expertCustom security tests
Probely: Does not offer custom security tests
Escape: If you need to add specific security testing scenarios, you can do it with Escape. Escape Rules allow users to create custom security tests in YAML syntax -both for discovery and for security testing. These rules adapt to API changes without extra maintenance, enabling detection at scale and supporting development-specific configurations, such as database fixtures.
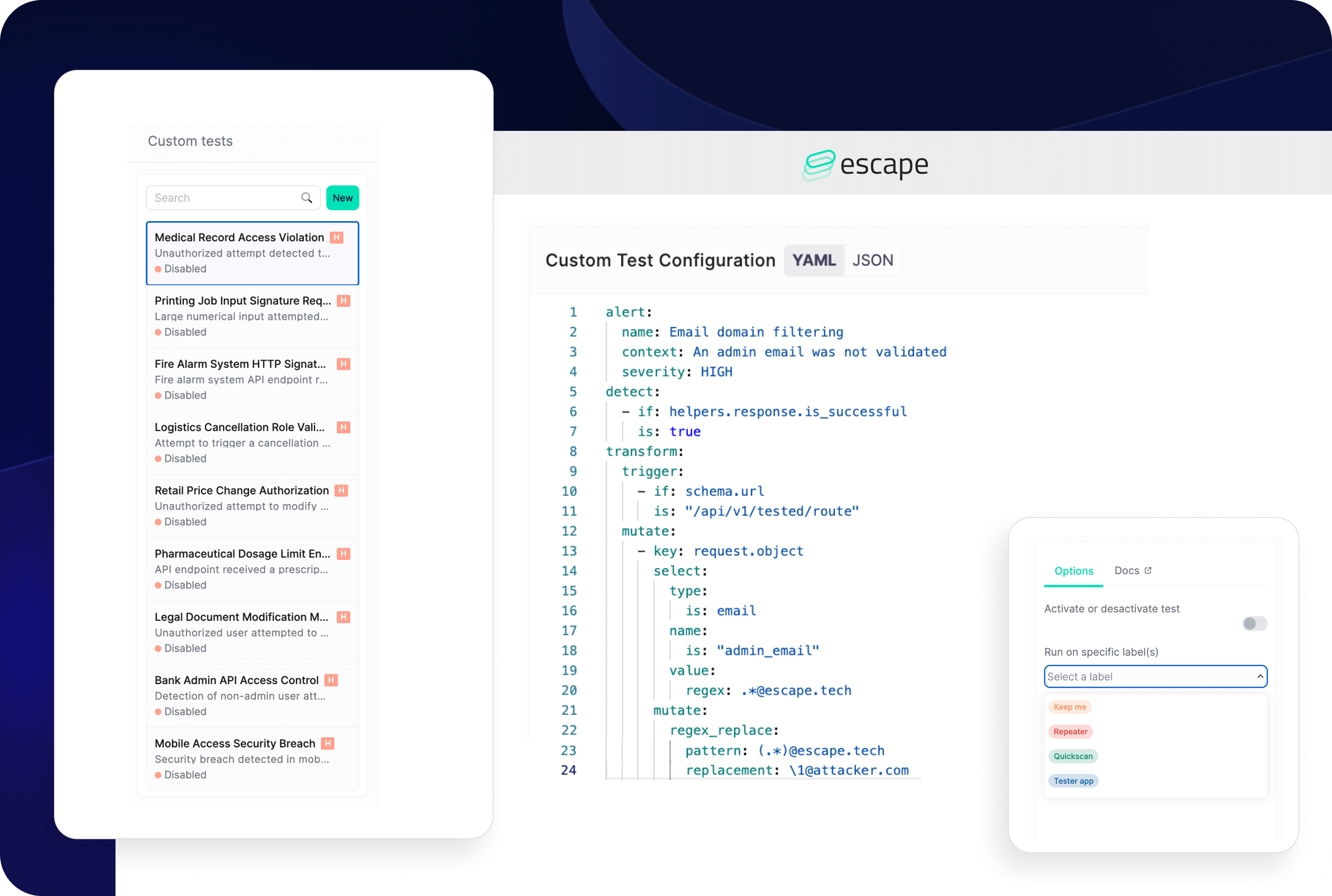
Most of what pentest or a bug bounty program can find can be quickly implemented as an Escape rule for easy detection at scale, including the detection of business logic flaws.
Remediations
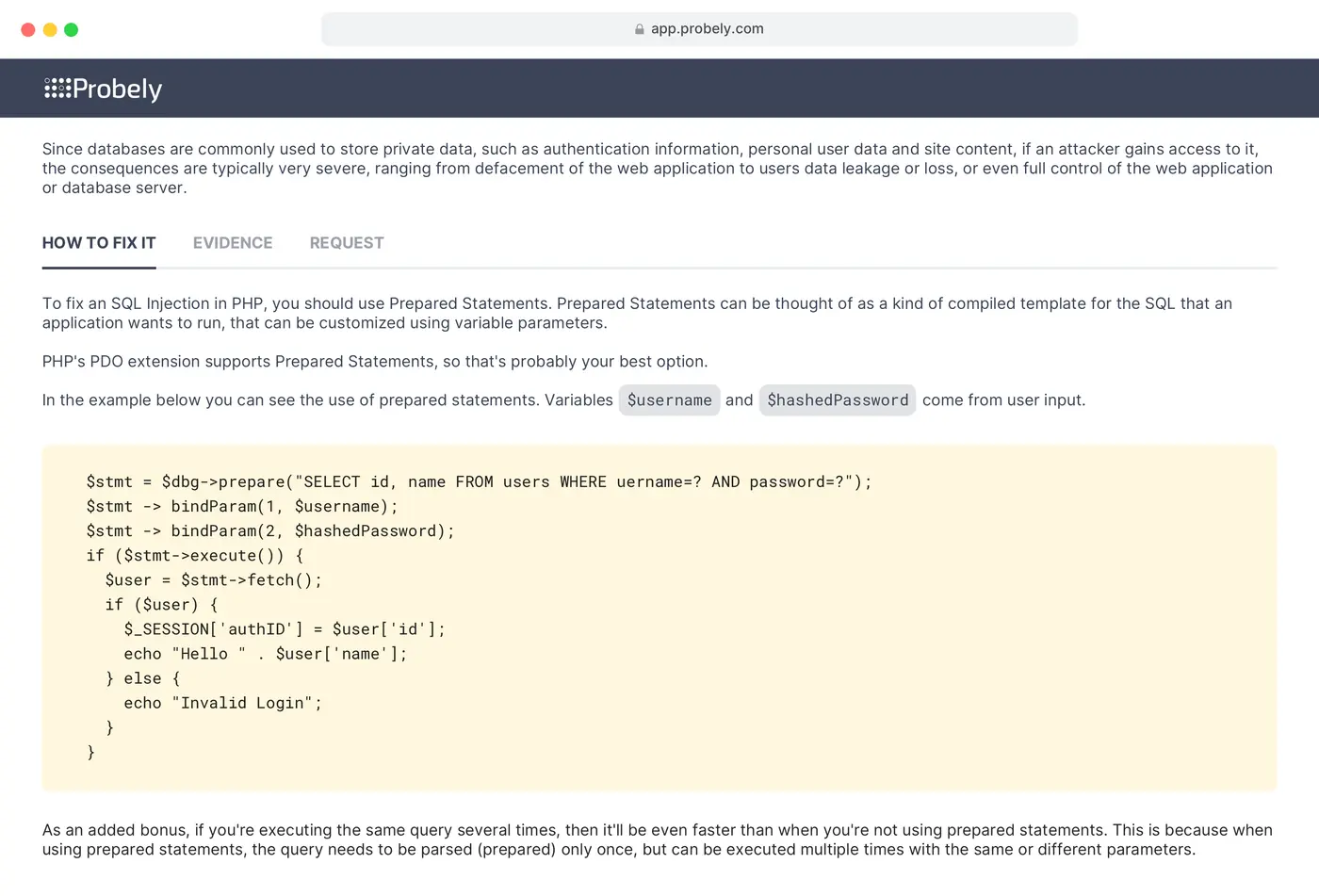
- Probely: Offers detailed remediation explanations, though they are not tailored to specific frameworks. Guidance focuses on interpreting scan results and understanding vulnerabilities:
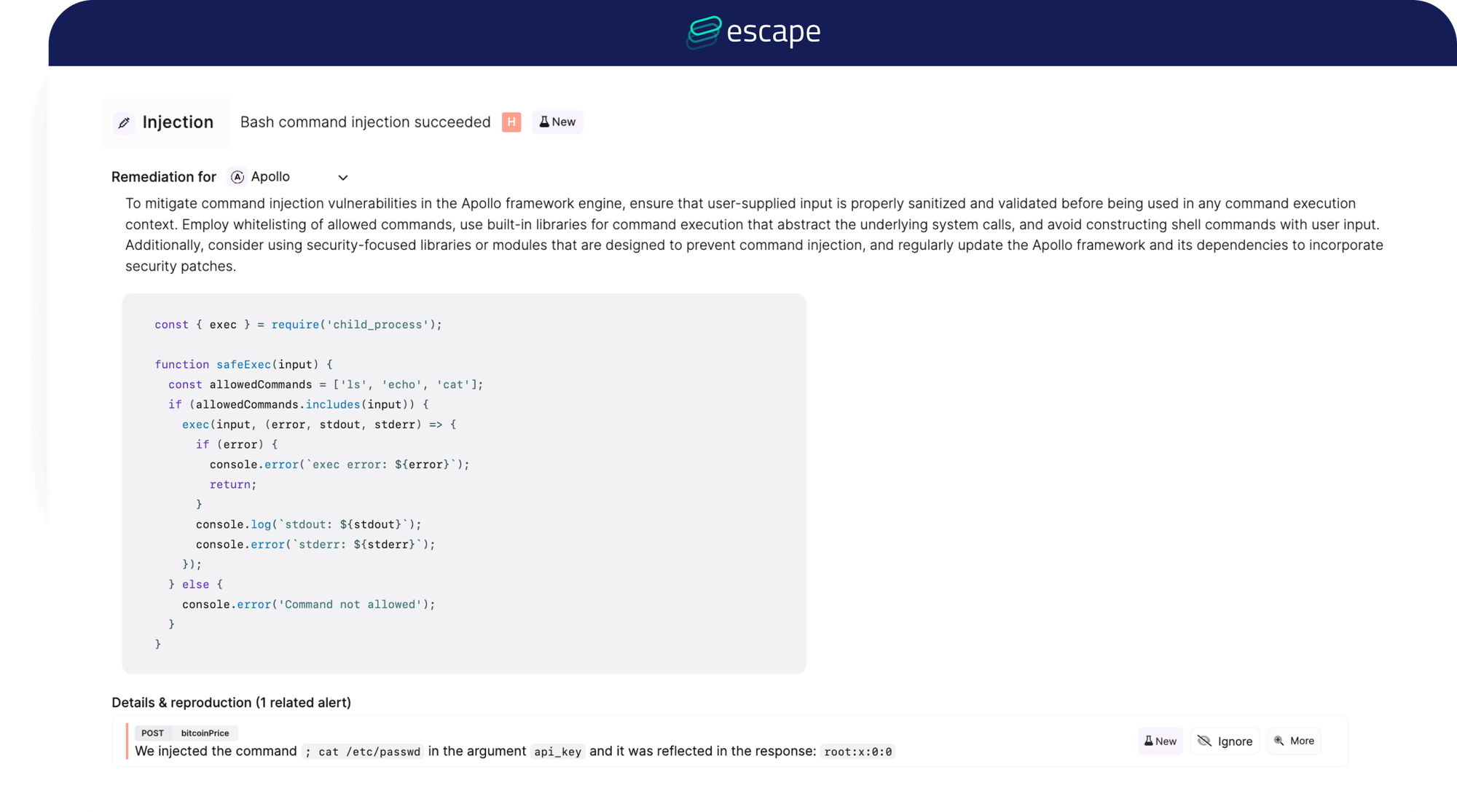
- Escape: Goes further by providing actionable remediation code snippets, helping developers fix issues directly in the code.
Integrations
- Probely: Stronger integrations with developer-centric tools, ticketing systems and DevSecOps tools like DefectDojo
- Escape: While less comprehensive in ticketing integrations, Escape’s partnership with advanced platforms like Wiz offers a strategic advantage for teams prioritizing scalability and security
Conclusion: Is Escape a viable alternative to Snyk DAST (Probely)?
In conclusion, both Escape and Probely (Snyk DAST) offer valuable solutions for dynamic security testing. Choosing between them depends on your priorities:
- If you need a straightforward tool for DAST scanning with surface discovery capabilities, Probely might be the right fit, especially for smaller teams looking for simplicity and diverse ticketing integrations
- If your focus is on advanced discovery, scalability, and custom testing capabilities, Escape stands out as a powerful option. Its automated workflows, business logic testing, and actionable remediation guidance make it a strong choice for complex environments and large-scale operations
Both tools have their strengths, but Escape definitely emerges as the superior choice for organizations that need to automate many processes of their rapidly scaling engineering teams, and those who are looking for in-depth application and security capabilities (especially for their modern applications like SPAs, APIs, and microservices).
Scale your business logic security testing quickly with Escape DAST
And see how it compares to Probely (a Snyk DAST)
Get a demo with our product expert💡 Want to learn more? Discover the following articles:
