The Elephant in AppSec Talks Highlight: Reinventing API Security
Highlights from Escape's talks at The Elephant in AppSec Conference on the challenges of API security and how Escape is overcoming these

APIs are everywhere. Breaches happen weekly. Attacks grow exponentially. Everyone knows about it, and yet companies are extremely slow to adopt the existing API security solutions. - Tristan Kalos, CEO and Co-Founder of Escape
With 83% of global web traffic flowing through APIs but only 11% of companies adopting API security, we need to step it up now more than ever. But when legacy DASTs are inefficient and no enterprise team has visibility on all of their APIs, how do we move forward?
The answer lies in two talks from the Elephant in AppSec Conference on November 7. Swan Beaujard, Security Engineer at Escape, and Tristan Kalos, CEO and Co-Founder of Escape, dive into why DASTs aren't enough, how companies struggle to secure APIs at scale and what we can do about it. This article takes you through the key highlights from their talks, which you can also rewatch in full now.
The API Security Conundrum
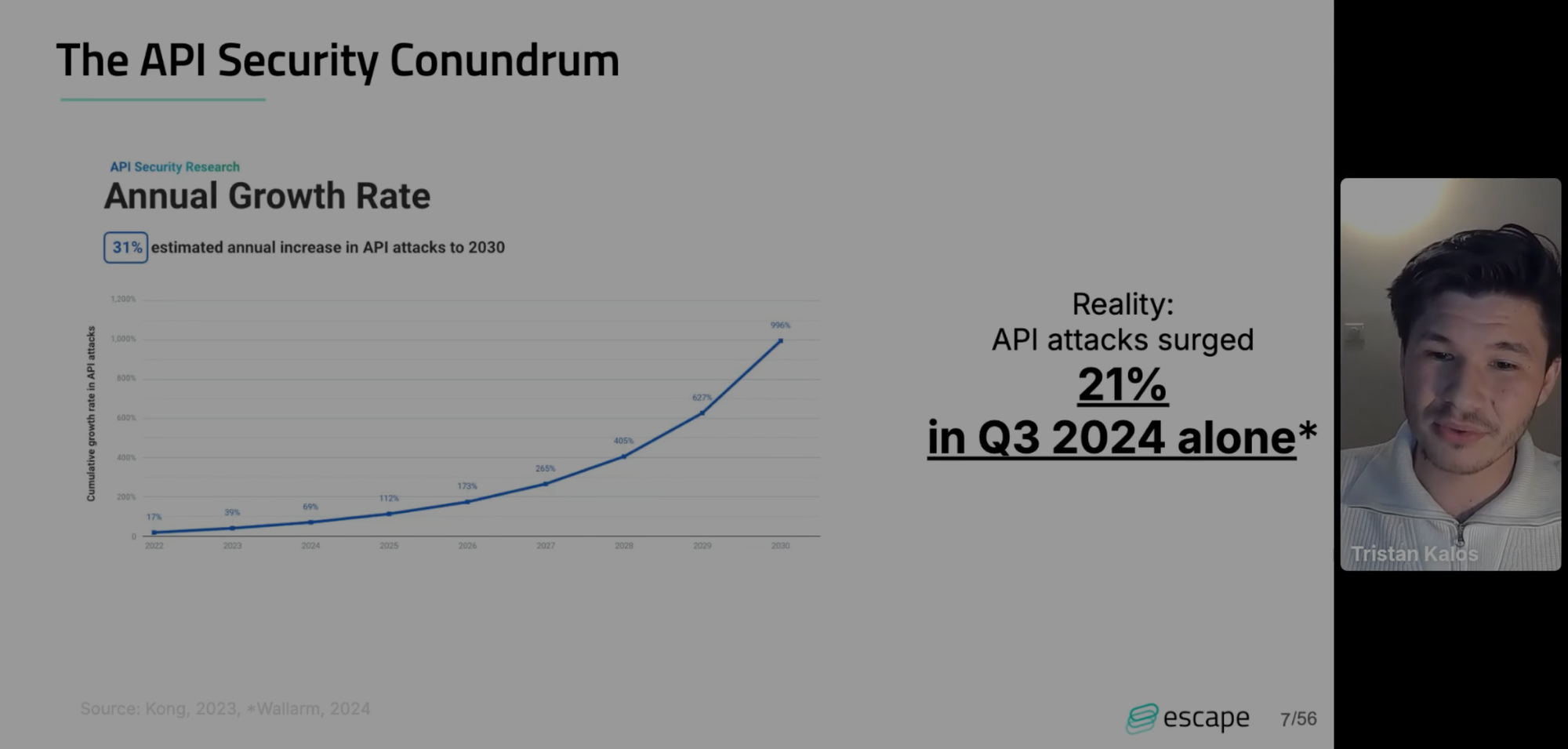
APIs are integral to modern web applications, powering mobile apps, single-page applications, B2B systems, and more. We are seeing significant companies experiencing API security breaches increasingly often, from attackers stealing 30 million Authy users' phone numbers this March to just this month DocuSign's API being hacked to send out fake invoices. Yet the complexity and inefficiency of current API security solutions has led to the critically low implementation of API security across these companies.
So what are the challenges exactly?
Challenges in API Security
API Security Testing
API security testing is the API version of the classic Dynamic Application Security Testing (DAST). Although you've probably heard that DAST is dead, rightly so. As Swan explores in his talk, existing DASTs are "unable to adapt to new threats" and often "too complex to integrate into." These tools can also just give securities alert fatigue with the sheer volume of alerts they generate, to the point where security teams may become overwhelmed and start ignoring some key vulnerabilities.
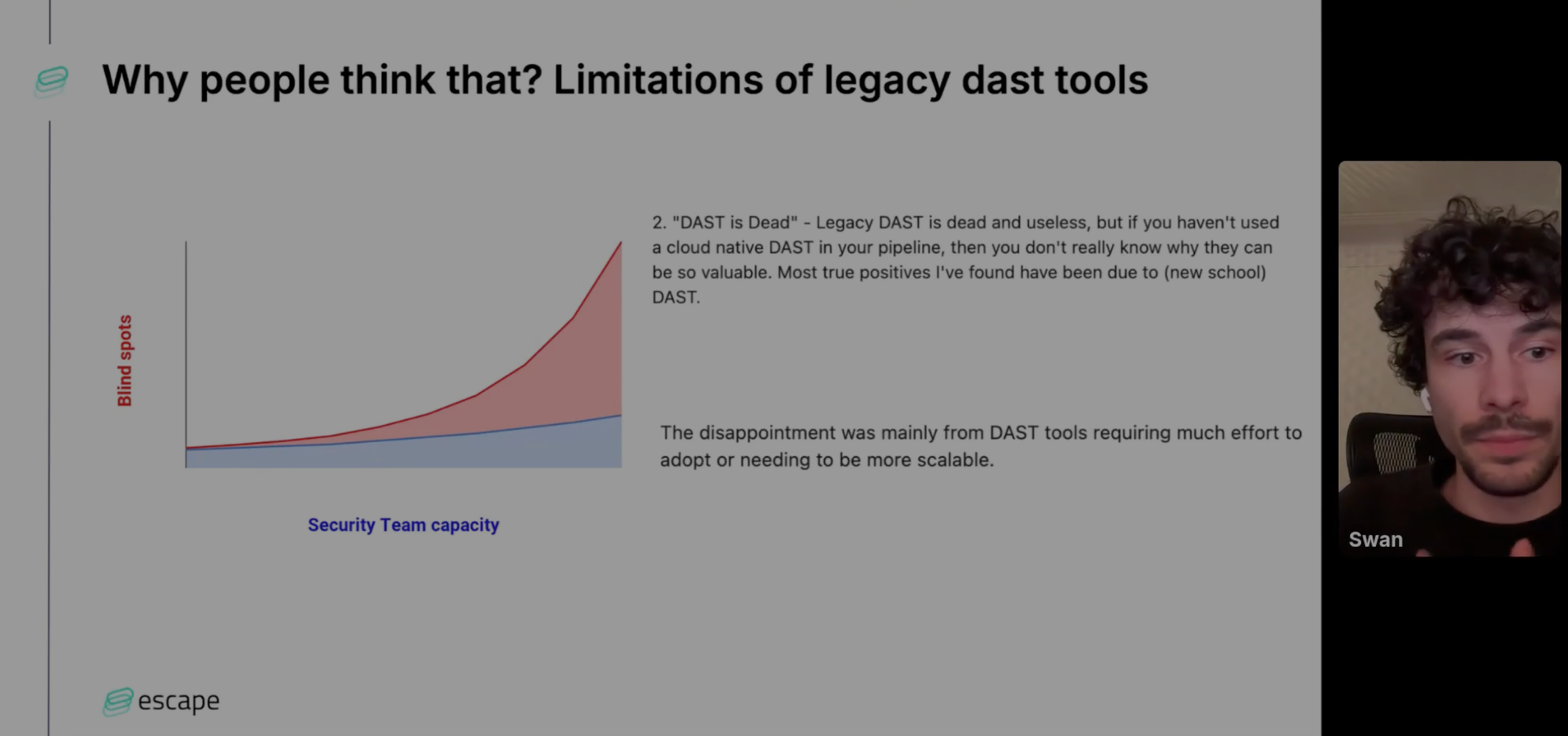
As Tristan explores, regarding APIs, DAST is often done with wrappers of open source tools that have been tuned to suit APIs but this requires days of back-and-forth with developers per API service for results that end up not even being worth it. And, of course, enterprises have thousands of APIs, so you can imagine the difficulty of this process at scale. With only a few security engineers being left to secure hundreds of applications made by thousands of developers, they just cannot get the documentation from all of these developers.
API Runtime Protection
Runtime protection is the recent development in API security. By monitoring API traffic in real-time, this strategy attempts to detect outliers and eventually block attacks. However, at scale, it doesn't work that easily. Since most of the outliers in API traffic are just outliers, not actually attacks, runtime protection creates a high false positives rate, making it difficult to automate the blocking of attacks.
"It took us two years to deploy [Runtime API Security Solution] on 40% of our APIs. And I am yet to find any true positive out of it." - Overheard conversation at Bsides Seattle
Secondly, these tools don't help you shift left because they're designed for network security engineers, not for developers. So the existing runtime protection tools are just not created to implement security by design, which was a key theme that ran across the conference, and you can find out more on this from our key takeaways.
And thirdly, the biggest problem with these solutions is they are simply too slow and too complex. You need to integrate all gateways, reverse proxies and the content delivery network (CDN), which firstly requires you to know what you have, which most companies do not. Then there's often numerous layers of multi-step authorizations or approvals by different teams across the enterprise, further inhibiting the ability to deploy API security at scale.
API security is a rapidly growing concern. But it currently seems impossible to effectively tackle it. What do you do then?
Reinventing API Security
Both Swan and Tristan dive into how Escape is battling these challenges, eliminating exhausting integration processes, alert fatigue, and leveraging AI to ensure API security testing is actually made specific to a business' needs.
More visibility with less integration
Using the internet as a data source, the most scalable data source available, Escape can take just a company's domain name and detect exposed APIs, even identifying shadow or unofficial API clients stored on forums or in different code repositories. With this integration, Escape can identify, and even generate, documentation for APIs because of the access to the source code. You can then progressively integrate into the CI/CD pipeline, streamlining your development operations. So security teams go from chasing down thousands of developers, to just entering a domain name. You also don't know what you don't know when you have to manually document APIs, but here they are found for you.
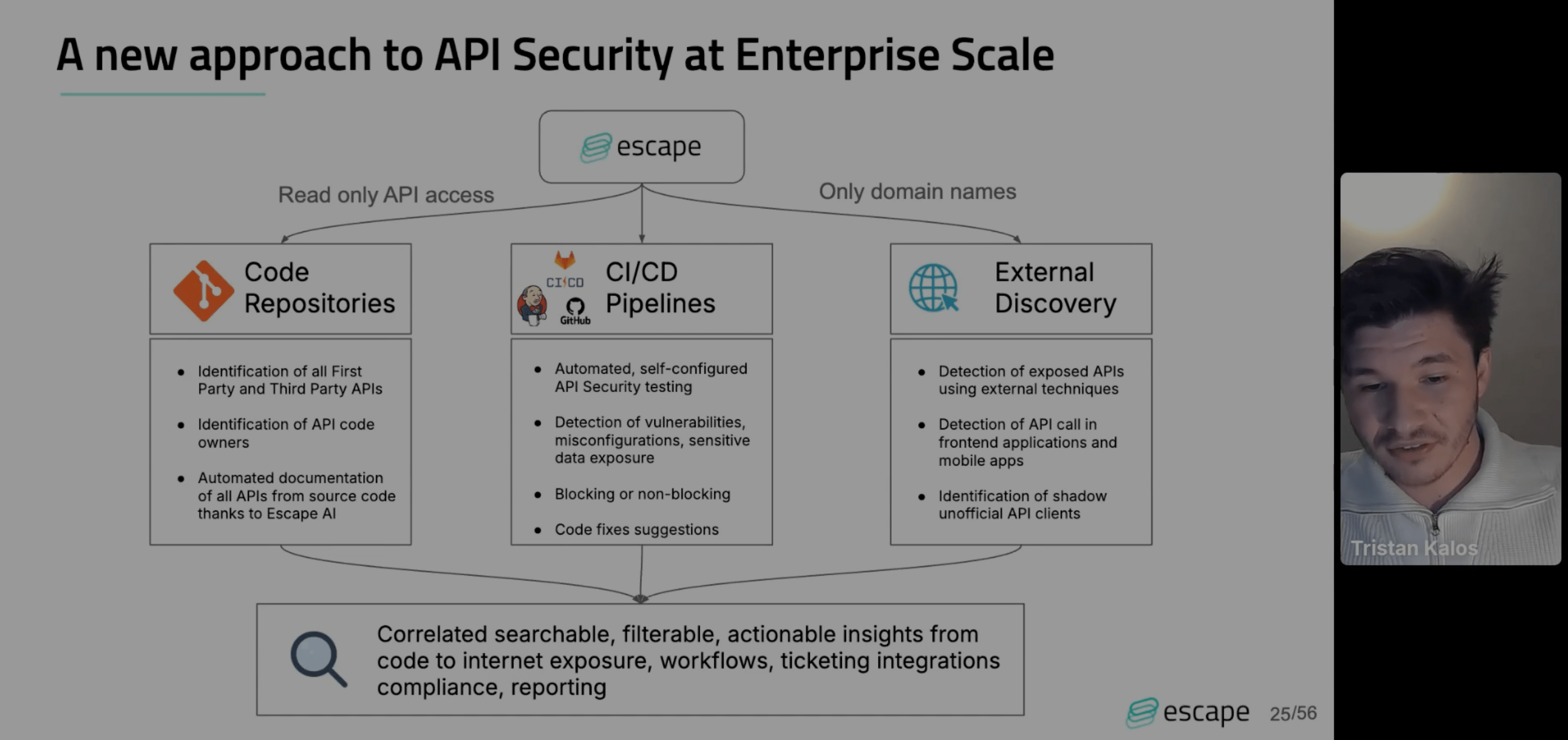
A feedback-driven hybrid approach
How does this integration work? The key is a feedback-driven API exploration technology, which uses both static and dynamic testing. API information is extracted by static analysis of front or back-end code and dynamic analysis tests every request and response in a self-improving dialogue with the API.
"It kind of acts like if a human pen tester would try to understand how an API works from the source code but it is thousands of times faster" - Tristan Kalos, CEO and Co-Founder of Escape
Crucially, this agentless approach can effortlessly scale to thousands of API endpoints. Furthermore, with a prioritization funnel, the days of alert fatigue are over as Escape is able to highlight the most pertinent fixes and provide code snippets that can integrate into a wide range of systems, making security teams' and developers' lives that much easier.
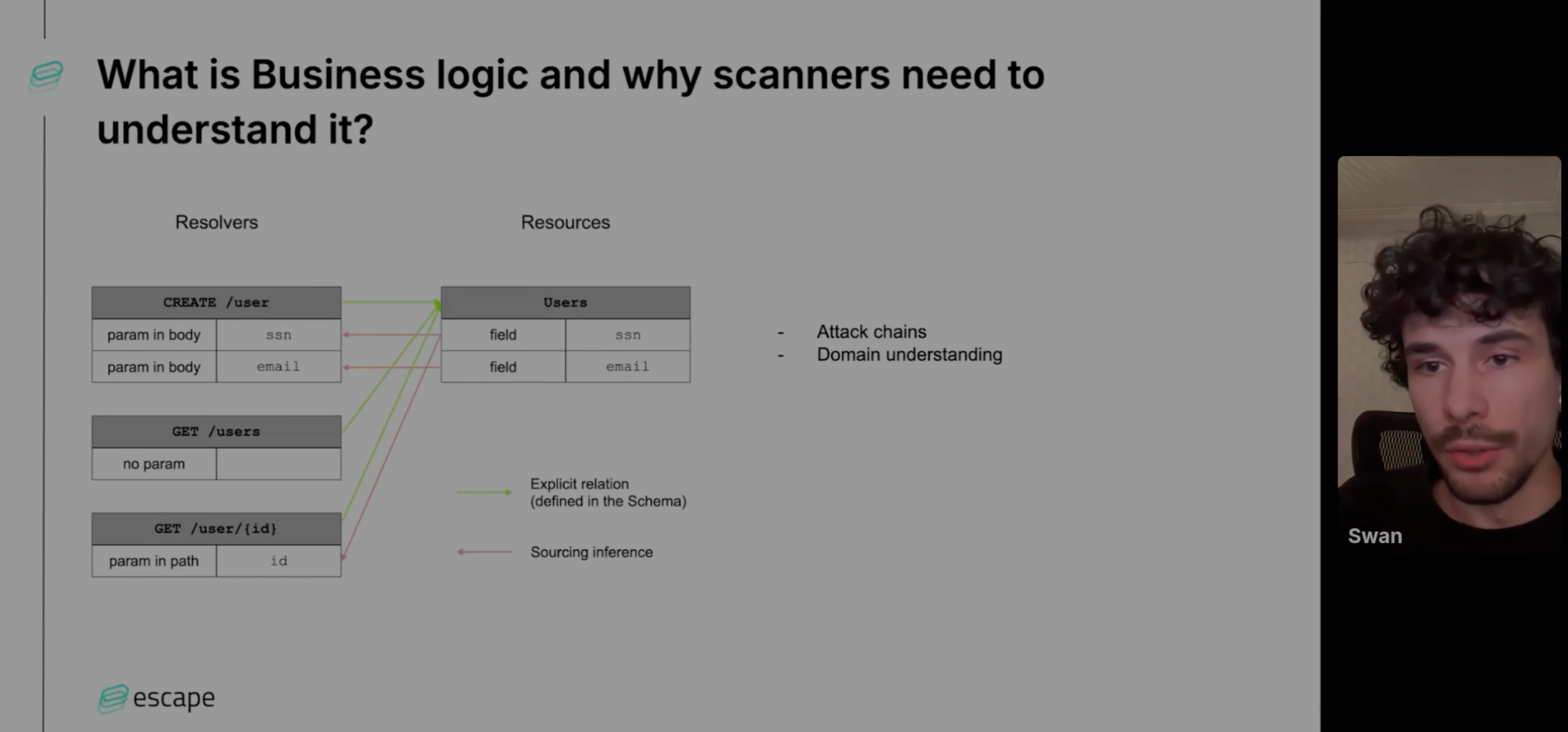
Business logic testing
Business logic testing is the final pillar to tackling the challenges of existing API security testing. The gaps found in existing DASTs can be eliminated by the harnessing of AI to test the underlying rules and relationships within an application, because, as Swan highlights, "often vulnerabilities exist within logical processes and not within code or data libraries."
Swan's talk runs through examples of business logic testing and its power in practice, from top-down approaches starting with threat modeling to ensure well-defined access controls, but he also considers the challenges of business logic testing, especially designing an algorithm that understands how values interact.
A whirlwind run through the current API security landscape, this article has considered the challenges companies face with API security and existing tools, but also how Escape is now reinventing API security to tackle these very challenges, streamlining what were once cumbersome processes by deploying innovative technologies. To dive into everything mentioned further, make sure to watch both Tristan and Swan's talks in full, as well as the rest of The Elephant in AppSec Conference for more incredible insights on all things application security.
💡 Want to discover more?
