Product Updates: Persisted GraphQL Query Support
You can now test the security of persisted GraphQL Queries with Escape's platform. This new capability enhances our GraphQL API security testing by providing deeper insights into vulnerabilities specific to persisted queries, enabling your team to protect your APIs from targeted attacks better.
We support the following formats:
What are Persisted Queries?
Persisted queries in GraphQL help to optimize network performance and enhance security. The client sends a unique identifier (a hash of the query string) instead of the entire query string to the server. The server has a pre-registered map of these identifiers to their corresponding query strings.
How Persisted Queries benefit your application?
- Network Performance: By sending just a small identifier instead of a potentially large query string, you can significantly reduce the payload size of network requests.
- Security: Persisted queries can also enhance security. Since queries must be pre-registered on the server, this prevents malicious queries from being executed.
- Versioning and Cacheability: They help in managing query versions and can make caching more efficient.
Overall, with Persisted Queries, by allowing only pre-registered queries, you can prevent certain types of injection attacks. However, it's not a silver bullet your GraphQL APIs still need to be tested for their security.
Why did we decide to add this feature?
- Enhanced Coverage for GraphQL APIs: Persisted queries are a common practice in modern applications. This feature ensures that your GraphQL API testing is comprehensive, covering both dynamic and persisted queries.
- Optimized Testing for Persisted Queries: Persisted queries are often used for performance and security optimization, but they can introduce unique vulnerabilities if not properly secured. With our new feature, you can now detect security flaws in these pre-saved queries.
- Prevention of API Misuse: Attackers can exploit persisted queries to bypass query validation and inject malicious content. Escape ensures that your queries are thoroughly tested for such risks.
- Seamless Integration with Your CI/CD Pipeline: As with other Escape features, testing persisted GraphQL queries integrates smoothly into your existing CI/CD workflows, keeping security at the forefront of your development process.
Getting Started:
- Go to the Security Scan tab, click on Tested applications, and select the application you want to test.
- Once you're on the scan result page, click on Settings and select Expert mode
- Configure your YAML file by adding the .json file for your persisted queries:
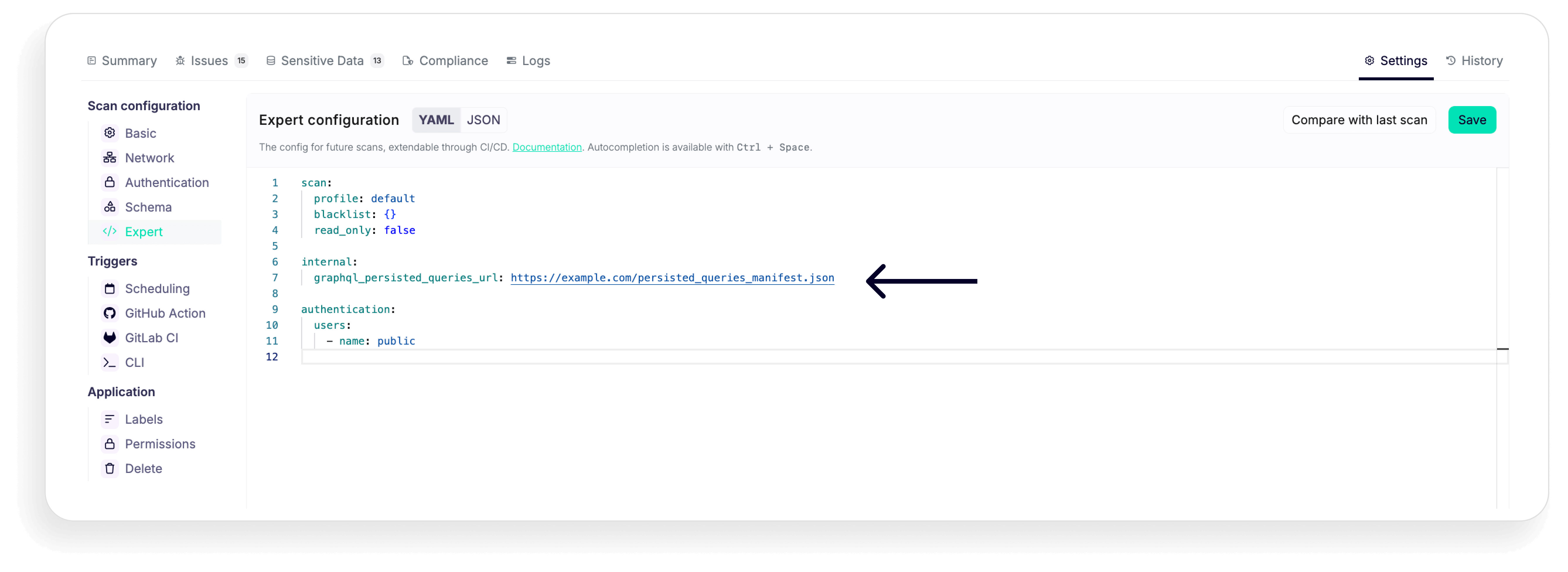
- Save the changes and restart the scan.
- Once your scan is complete, review the results to identify any potential vulnerabilities or security concerns related to your persisted GraphQL queries.
With these new updates, you should be able to tackle even the most advanced API risks with confidence. Try it out for yourself, and let us know what you think in our Slack community!
