How to maintain security compliance at a Fintech: A complete guide
If you're responsible for security at a financial services or fintech company, here is your comprehensive overview of what you need to do to be compliant.

The fintech industry faces some of the most stringent compliance requirements out there, due, of course, to the highly sensitive nature of the data they deal with. While compliance is non-negotiable, it doesn't have to be the insurmountable mountain it may sometimes feel like it is. This article will break down exactly how you can make sure your company is compliant, and the tools and frameworks that will get you there (and make your life much easier in the process!).
The Risks of Non-Compliance
Financial companies face a complex web of regulations and standards, but keeping on top of them all is vital because the consequences of not doing so can be severe. Almost all fintechs struggle with compliance, and over 86% paid significant fines in the last few years.
Hefty fines and an increase in transaction fees
Financial penalties are especially weighty, in order to send a strong message about the importance of adherence and operational resilience in the financial sector. A striking example is The First American Financial Corporation's 2019 data breach, which exposed 885 million financial and personal records linked to real estate transactions and cost them $10 million.
Here are some of the fines for different requirements' non-compliance:
- PCI DSS: $5k to $100k per month until the issue is fixed
- DORA: 2% of annual global turnover
- PSD2 and GDPR: Up to 4% of annual returns
Not only can you be fined, but you can face other financial consequences that increase your business costs, like payment processors charging higher transaction fees for non-compliant businesses. This would mean every single card transaction becomes more expensive.
Reputational damage
The financial industry is built on the trust that customers and stakeholders place in companies to safeguard their data and offer seamless service. Hence, a failure to comply can signal vulnerability, which will lead to customers losing that trust and ultimately taking their business elsewhere. As your reputation takes a big hit, as does your competitive position in the market.
Increased risk of breaches
Non-compliance also poses a significant security risk; if your applications are not secured up to the required standards, your chances of facing a cybersecurity incident skyrocket, including API breaches, data leaks, and operational disruptions. These both harm customers and disrupt operations, but can also lead to further regulatory scrutiny.
Operational disruptions
Compliance requires having robust incident response processes, so without this an institution is unprepared for disruptions, which can destabilize supply chains, cause economic instability, and inflict long-term financial damage.
Loss of ability to process card payments
Specific to PCI DSS, non-compliance penalties are not only fines and increased transaction costs, but if an issue escalates or a company is a repeat offender, they can become cut off from being able to accept credit card payments, which will cause significant revenue losses.

Recent regulations to keep in mind
As a fintech company, you are subject to specific payment and financial regulations while also being required to comply with general data protection and industry standards. Here are the main recent ones you need to know about:
Payment and financial regulations:
PCI DSS: This applies to any entity that processes, stores, or transmits credit card data. PCI DSS v4.0 released more than 50 new requirements last year, with the implementation deadline coming up soon, on 31 March 2025.
DORA: The Digital Operational Resilience Act is an EU regulation that promotes cyber resistance in the financial sector. Two key aspects of DORA are secure data transmission and managing third-party risks (e.g. third-party connections or shadow APIs). DORA is not just for EU-based companies but also applies to US companies with operations in the EU.
PSD2: This regulates payment services to enforce strong customer authentication as well as to strengthen the security of online banking APIs.
Data protection and privacy
GDPR: GDPR mandates the strict handling of personal data for companies operating in or serving EU citizens. Again, even if you aren't physically located in the EU, when you store the private data of EU citizens, you must comply with GDPR.
Industry standards
SOC2: This is an internationally adopted American security framework that ensures that data is securely managed by service providers, to protect business interests and clients’ privacy.
ISO 27001: This is essential for fintech companies because it centers on systematically managing sensitive company data, with a framework for creating, implementing, maintaining and evolving information security management.

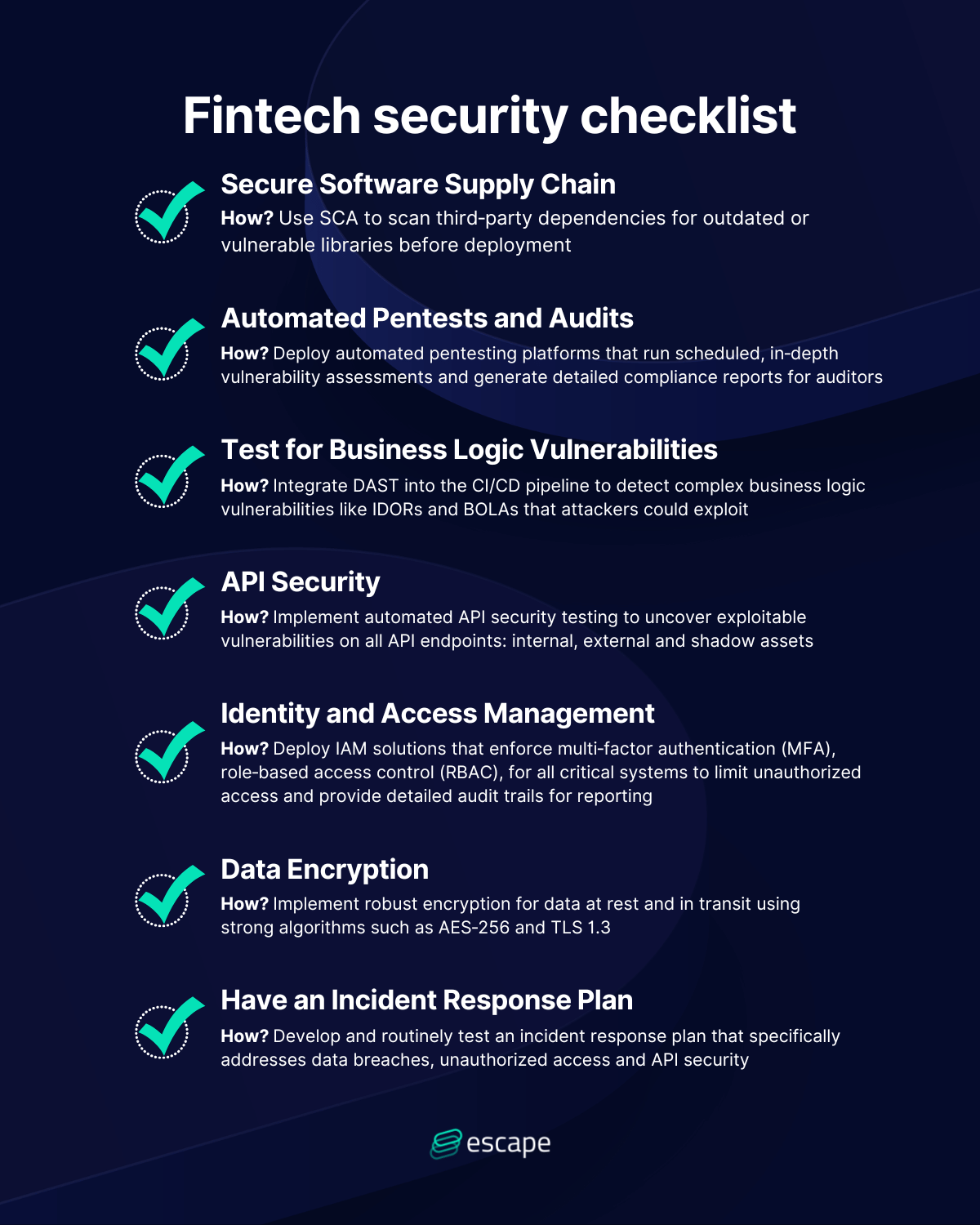
Fintech security checklist
Now what do you need in order to meet these standards and requirements? Our fintech security checklist below outlines exactly what you need to implement and how:
- Secure Software Supply Chain
How? Use Software Composition Analysis to scan third-party dependencies for outdated or known vulnerabilities in libraries before code is deployed.
Why? Standards like PCI DSS and DORA require that vulnerabilities in external components are also tested for and patched, which particularly applies to fintech companies as they tend to rely on many external libraries.
- Automated Pentests and Audits
How? Deploy automated pentesting tools that run scheduled, in-depth vulnerability assessments and generate detailed compliance reports for auditors.
Why? New compliance requirements like PCI DSS Requirement 6.4.2 require automated testing of public-facing web applications to detect and prevent web-based attacks.
- Test for Business Logic Vulnerabilities
How? Integrate Dynamic Application Security Testing into the CI/CD pipeline in order to uncover complex business logic vulnerabilities.
Why? Such vulnerabilities cannot be uncovered by static testing and can pose serious threats if exploited, for example, access control issues that can lead to serious sensitive data leaks. Article 26 of DORA requires simulating attacks that emanate real-world scenarios, to uncover exploitable threats like business logic flaws.
- API Security
How? Implement automated API security testing to discover all endpoints - internal, external, and shadow assets - and uncover exploitable vulnerabilities.
Why? API security is specified by frameworks like DORA, since they are the backbone of modern traffic (83% of web traffic flows through APIs!). Hence, they are imperative to secure as a fintech company because of the sensitive data that flows through the APIs your company uses. It is key to have visibility over all of your endpoints, including third-party ones, to make sure nobody gains unauthorized access to data.
- Identity and Access Management
How? Deploy IAM solutions that enforce multi-factor authentication (MFA) and/or role-based access control (RBAC) for all critical systems.
Why? These solutions limit unauthorized access and also provide detailed audit trails for reporting, implementing secure default principles and streamlining compliance processes.
- Data Encryption
How? Implement robust encryption for data at rest and in transit using strong algorithms such as AEs-256 and TLS 1.3
Why? Data encryption is required by multiple compliance frameworks, but equally acts as another line of defence if data is accessed, so it cannot be read.
- Have an Incident Response Plan
How? You must develop and routinely test how your team (both security and developers) react in the instance of attack incidents, detailing specifically how you address data breaches, unauthorized access, and API security.
Why? Frameworks like DORA require robust incident response plans, but they also serve to ensure that should you face a breach, you know that losses will be as minimal as possible with an efficient response framework.
All of the above are not only explicitly required by at least one compliance requirement (mostly PCI DSS and DORA), but will also strengthen your overall security posture and largely mitigate the risk of an exploitable vulnerability slipping through the cracks. This allows you not only to avoid the financial repercussions of non-compliance but also the reputational and operational damages that accompany breaches.
Meet FinTech compliance mandates quickly with Escape DAST
Get automated reports for your auditors, reduce the load on your team, and remediate even complex business logic vulnerabilities more effectively than ever
- ✅ Built for modern applications: SPAs and APIs
- ✅ Business logic security testing built in-house
- ✅ Automated reporting for DORA, PCI-DSS, and other 17 compliance frameworks
- ✅ Smart handling of complex authentication scenarios
- ✅ AI-powered exploit validation and remediation code snippets
Tools to fulfill compliance requirements
So you know what you need, as outlined above, but which tools should you implement to realize the checklist?
SAST: Automatically and continually scanning source code during development helps meet secure coding practice requirements mandated by regulations like PCI DSS (requirement 6.5) and internal security policies.
DAST: Regular DAST testing is required by PCI DSS (requirement 11) to demonstrate that production systems are free from exploitable vulnerabilities and business logic flaws and that no sensitive data is exposed in transit by APIs.
SCA: Fintech companies rely on many third-party libraries and external components; SCA tools help ensure these meet regulatory standards (e.g., PCI DSS and GDPR) by tracking and patching vulnerabilities in third-party code.
API Security: Fintech companies rely on many third-party libraries and external components; SCA tools help ensure these meet regulatory standards (e.g., PCI DSS and GDPR) by tracking and patching vulnerabilities in third-party code.
Multi-Factor Authentication and Role-Based Access Control: Reducing the risk of unauthorized access is requirement 2 in PCI DSS, but also crucial to mitigating sensitive data exposure by ensuring employees only have access to the data necessary for their roles.
Data Encryption: Encryption is a core requirement in frameworks like PCI DSS and GDPR; proper key management demonstrates adherence to best practices in data protection.
Go beyond tick-box compliance by embedding secure development practices
Compliance is not just about risk management but also about risk prevention. Since 2020, the number of cyberattacks has doubled and continues to be on the rise, with attacks on financial firms accounting for one-fifth of the total. So now more than ever, it is vital to ensure that your applications are robust, not only to avoid non-compliance fines but also to avoid the rising risk of significant losses following an attack.
To effectively mitigate vulnerabilities, security best practices need to be implemented throughout the entire application lifestyle, avoiding insecure coding in the first place and catching vulnerabilities as soon as they appear to make remediation that much easier.
There are three key ways to ensure secure coding practices in your company:
Integrate security throughout the SDLC
By implementing security tooling and practices throughout the SDLC, you can catch vulnerabilities right from the development stage up to the production stage. This proactive approach significantly reduces the likelihood of breaches happening and can largely minimize remediation costs, as vulnerabilities are easier to fix the earlier they're caught.
How do you integrate security throughout the SDLC?
- Adopt secure-by-design principles and use threat modeling
Secure-by-design principles ensure that customer security is treated as a core business requirement, by considering cyber threats right from the start, even before development, and implementing practices to mitigate the risk of breaches as much as possible.
Some crucial secure-by-design principles we recommend are: least privilege, defense in depth, and secure defaults.
Least privilege means giving employees the minimal level of data access needed for their job, which is particularly crucial for Fintechs as they handle some of the most sensitive data that is imperative not to leak.
Defense in depth means having multiple layers of security, so if one fails others are there to back it up. For example, even if physical controls like key-card access are compromised, having antivirus software and firewalls set up can still prevent a hacker from gaining unauthorized access or equally buy the security team more time to defend against the breach.
Secure defaults means when configuring, and also while maintaining, your security system, you implement the highest level of security as a default. This involves, for example, configuring access control with a "deny unless explicitly authorized" strategy, to ensure that data only goes to those for whom it is absolutely necessary.
To ensure security is built into your development process from its conception, adopting secure-by-design principles should also be accompanied by threat modeling to identify potential attack vectors and map out risks before they can even form. This enables proactive design decisions that counteract these threats, hence not only minimizing vulnerabilities and reducing the risk of a breach but also strengthening the overall resilience of the application.
- Integrate security tools like SAST and DAST throughout the SDLC
Static testing (SAST) can be implemented right from the IDE to scan code for issues like phantom packages, and DAST comes in straight behind from the CI stage, to detect complex runtime vulnerabilities like business logic flaws, BOLAs, and IDORs. Both SAST and DAST can uncover issues like SQL injections or XSS, but they are also designed to detect different vulnerabilities and help with remediation at different levels.
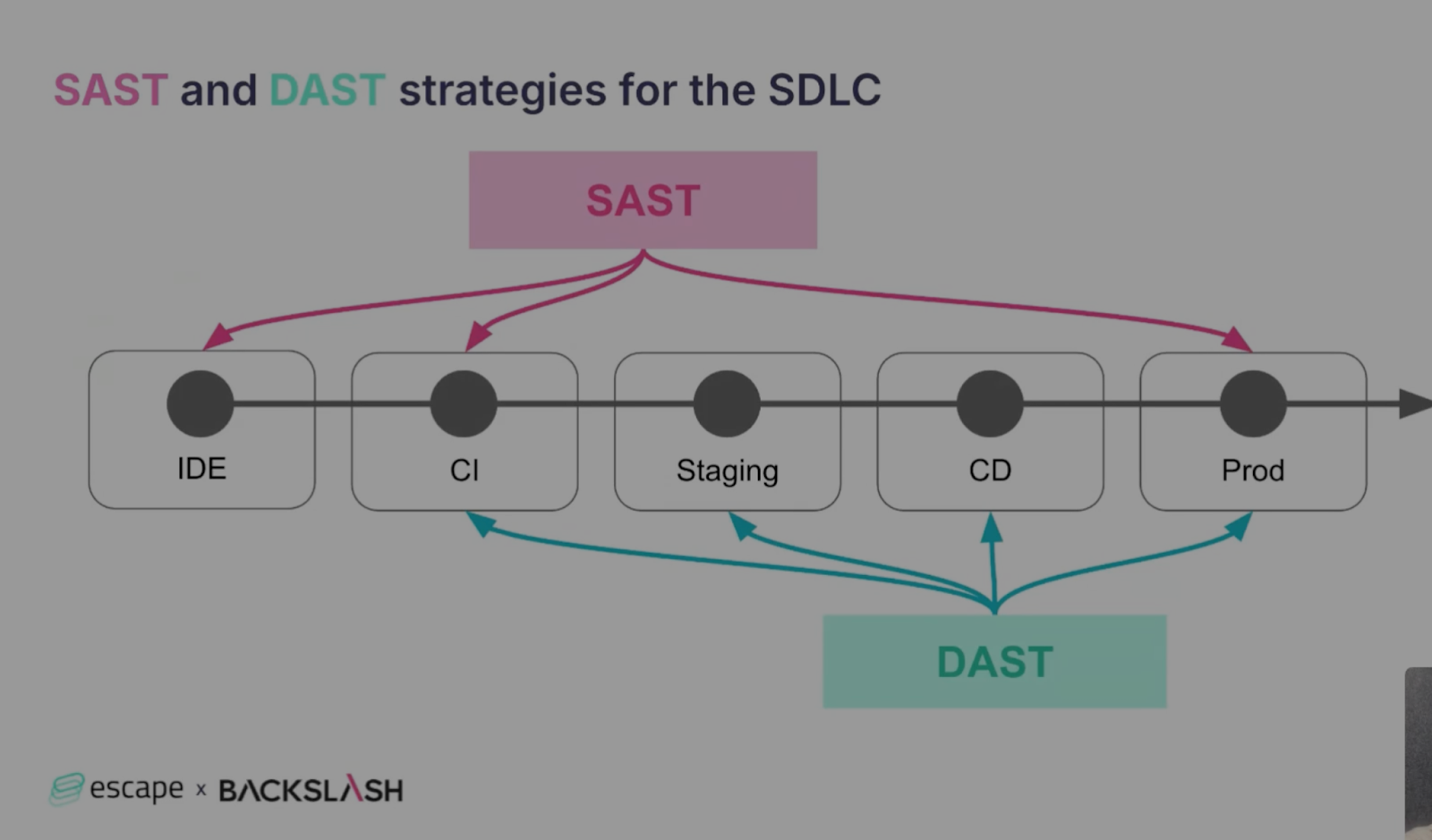
By integrating both into your SDLC, and in earlier stages, you can get full visibility over your SDLC, minimizing the risk of any vulnerabilities slipping through the cracks.
“The combination of both is really not only a way to detect different vulnerabilities, but also to detect different levels of remediation from vulnerabilities at scale that are easy to remediate.” Tristan Kalos, CEO of Escape
Build a security culture
Designing your security system to be resilient is vital, but for it to really be effective you have to your developers, and indeed the rest of the company, on board to security and maintaining secure practices. This is what building a security culture entails, so that security isn't just the concern of the security team but is a key tenet of the business.
Discover more about the best ways to build this culture in Jeevan Singh's The Elephant in AppSec episode:
You need continuous training and awareness to train and update developers on secure coding guidelines, which continue to evolve.
But it's no news that sometimes the last thing developers want to do is security training, so you can make these programs more effective by including collaboration (e.g. more opportunities for developers to also give feedback and security to be a two-way conversation), customization (customize the training to apply very specifically to your organization's situation), real-world examples, and gamification to sustain engagement.
- Empower security champions
Security champions are developers who are passionate about cybersecurity and advocate for secure practices within their teams. They not only help to reduce overall organizational risk, but also act as a key bi-directional liaison between security and developers. Champions can help adapt security messages to address their development team's unique needs, and work with security teams to ensure that security is optimized to developers' workflows.
A key to a security champion program is it has to be voluntary, because mandating participation can, if anything, generate resentment towards security by adding more onto a developer's plate.
“Allowing individuals who are genuinely interested to volunteer for the program leads to higher engagement and participation compared to mandating participation." - Dustin Lehr, CISO
Conclusion
Compliance is absolutely vital for fintech companies, but it doesn't have to be an insurmountable burden. Instead, you should view security as an integral component of the business' operational strategy.
By integrating security tools - ranging from SAST, DAST, and SCA for secure development to robust IAM, encryption, and automated incident response systems - into every phase of the SDLC, companies can proactively mitigate risks and prevent costly breaches. This comprehensive approach not only ensures adherence to strict regulations like PCI DSS, GDPR, and PSD2 but also builds lasting customer trust and enhances overall operational resilience.
Ultimately, by building in secure design practices, fostering a security culture and empowering security champions throughout the organization, fintechs can transform compliance from a reactive obligation into a strategic competitive advantage.
Meet FinTech compliance mandates quickly with Escape DAST
Get automated compliance reports, reduce the load on your developers, and remediate vulnerabilities more effectively than ever
Get a demo with our product expert💡 Want to discover more? Check out the following articles:
