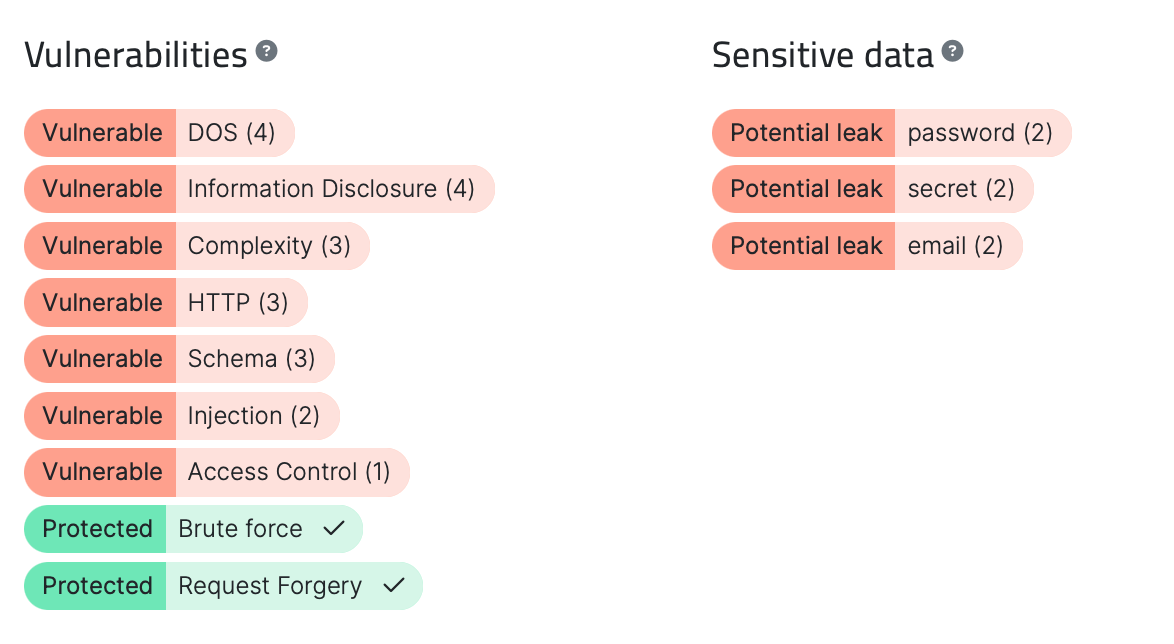
Top 5 GraphQL vulnerabilities burdening HIPAA compliance

TL;DR: GraphQL vulnerabilities will inevitably burden organizations, especially when healthcare compliances like HIPAA come into play. This article highlights how Escape makes it super easy to release compliant APIs.
The correlation between HIPAA and GraphQL is that PHI resources can be exposed through GraphQL APIs, allowing for a more efficient and flexible way of accessing and querying data. By using GraphQL, healthcare companies can improve the performance of their applications and reduce the amount of data that needs to be transmitted over the network. GraphQL facilitates more complex queries to be constructed and executed against PHI resources, which can help healthcare organizations gain deeper insights into patient data and improve decision-making.
However, like any technology, GraphQL APIs can also have vulnerabilities that can pose a significant risk to organizations, particularly those in the healthcare industry that must comply with regulations. Unauthorized FHI Data exposure can result in fines from the HHS'OCR up to $1.9m, and prison sentences can be imposed.
In this article, we will discuss the five principal vulnerabilities in GraphQL APIs that could cost a lot of trouble to a company that is supposed to be HIPAA compliant. We will use Escape to illustrate every vulnerability and how to remediate it.
1. Excessive Data Exposure
One of the benefits of GraphQL is that it allows clients to request only the data they need. However, this can also lead to excessive data exposure if not implemented properly. For instance, if an attacker gains access to a GraphQL endpoint and can execute arbitrary queries, they can potentially request FHI data that they should absolutely not access.
To mitigate this vulnerability, it is essential to implement proper access controls and authorization checks. This includes validating the input parameters of a query and ensuring that the user making the request has the necessary permissions to access the requested data.
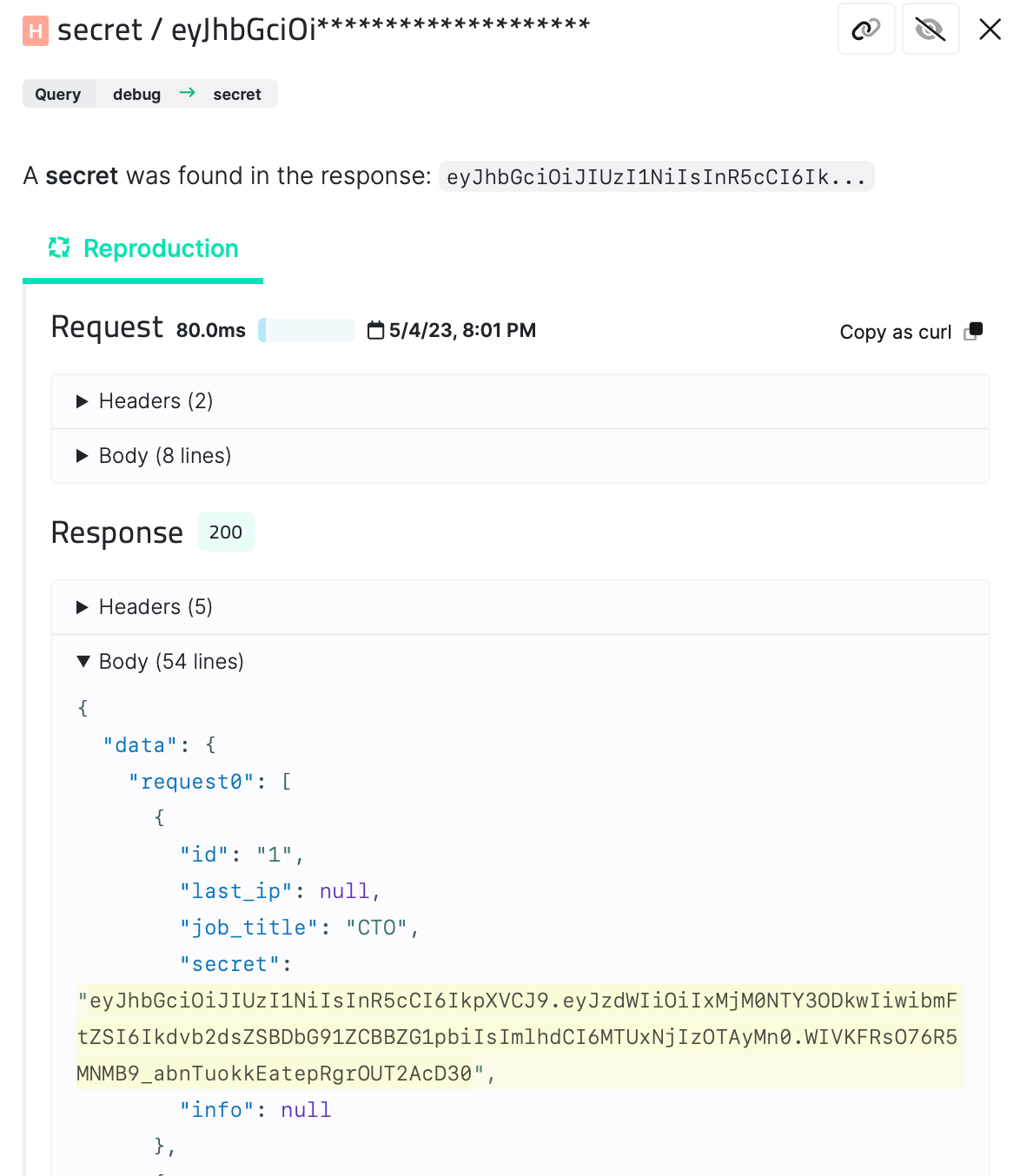
2. Injection Attacks
These occur when an attacker can inject malicious code into a query or mutation, which can lead to data leakage or data manipulation. For instance, an attacker could inject a query that retrieves sensitive data or updates data in a way that should not be authorized.
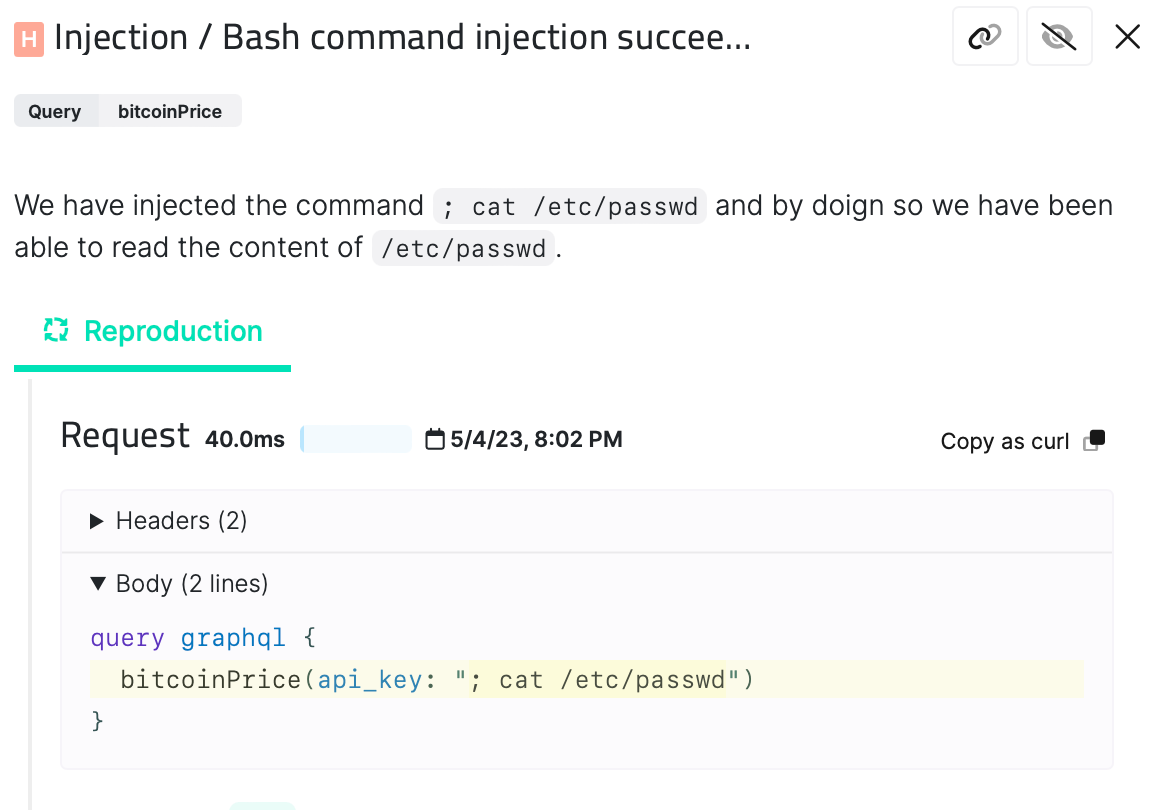
It is essential to validate input parameters and sanitize user input to prevent injection attacks. This involves ensuring that only valid data is accepted and that any input potentially used for injection attacks is adequately sanitized or escaped.
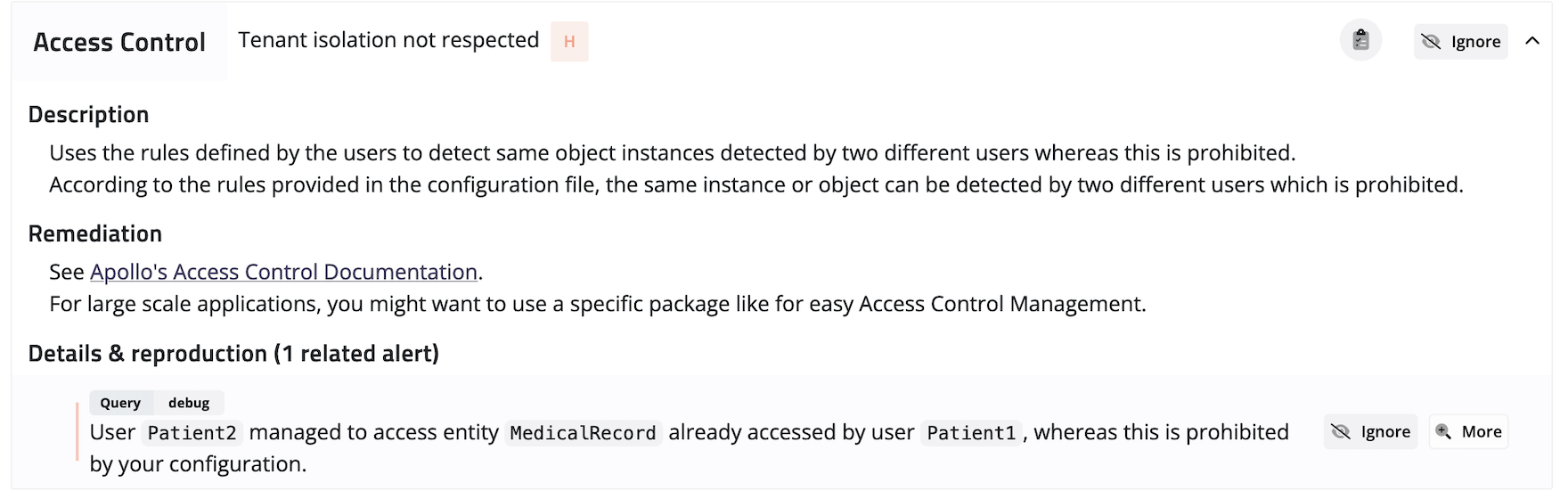
3. Access Control Vulnerabilities
Access control is one of the most critical aspects of any web application or API. It ensures that only authorized users can access sensitive information or perform certain actions. Access control vulnerabilities in GraphQL APIs can occur when attackers can bypass authentication or authorization checks and gain access to sensitive data or functionality.
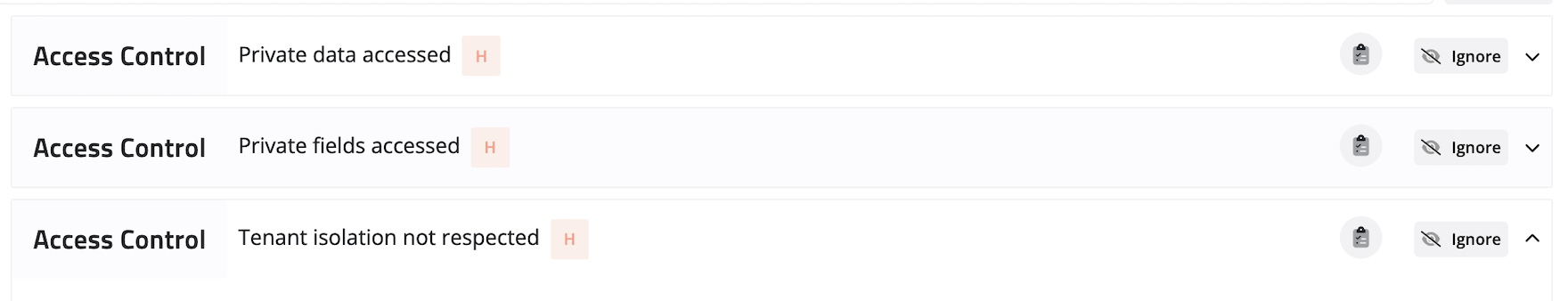
To mitigate access control vulnerabilities in GraphQL APIs, it is important to implement proper input validation and to ensure that all access control mechanisms are properly tested and audited. This includes checking that all requests are properly authenticated and authorized and that access is only granted to authorized users.
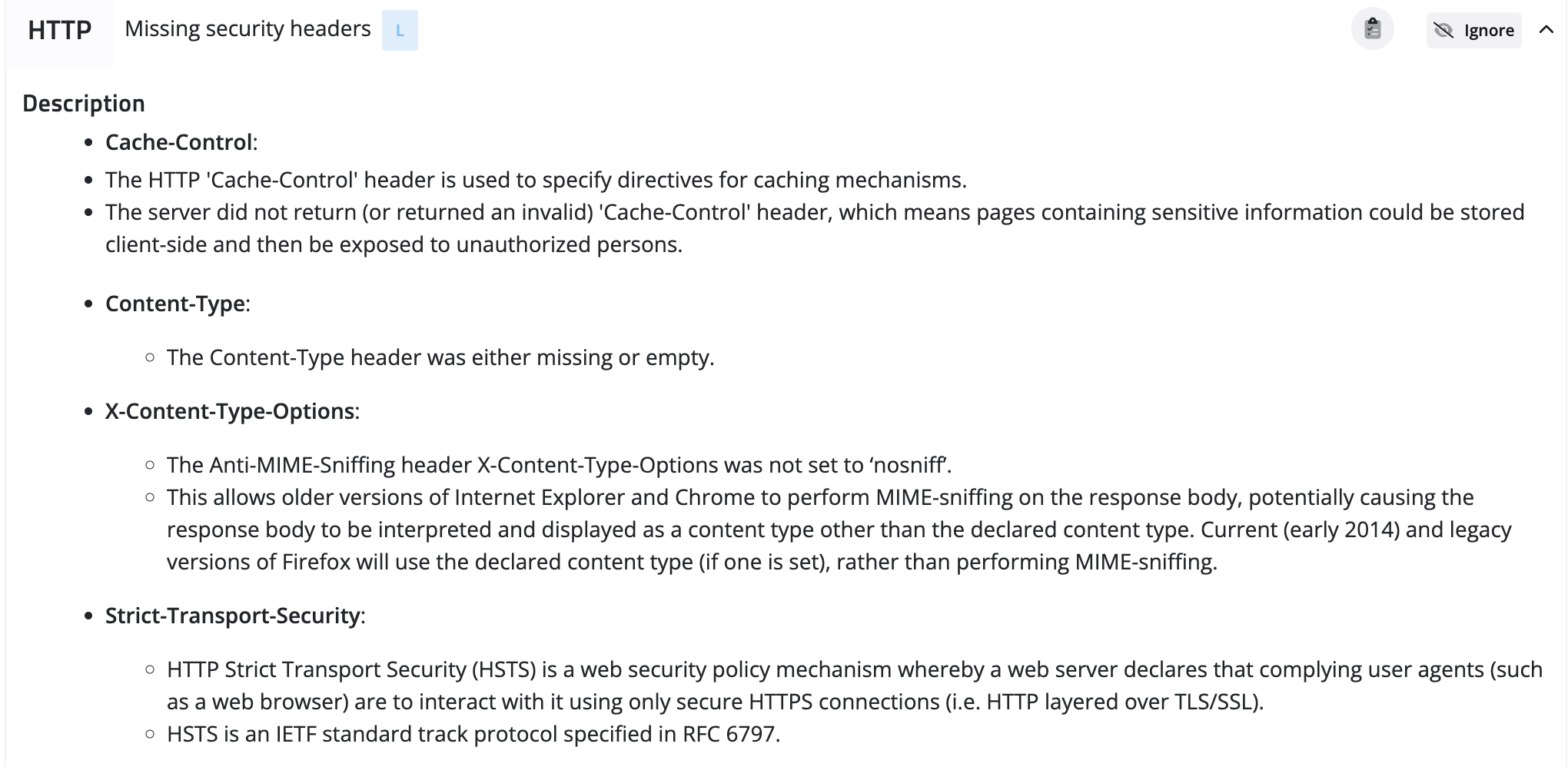
4. Misconfigured Headers
Headers are essential to HTTP requests and responses, providing additional information about the data being transmitted. Misconfigured headers can cause data leakage or allow attackers to bypass security measures. For example, if a GraphQL API is improperly configured, it may not validate headers, allowing attackers to inject arbitrary data into requests or responses. This can lead to data leakage or other security issues.
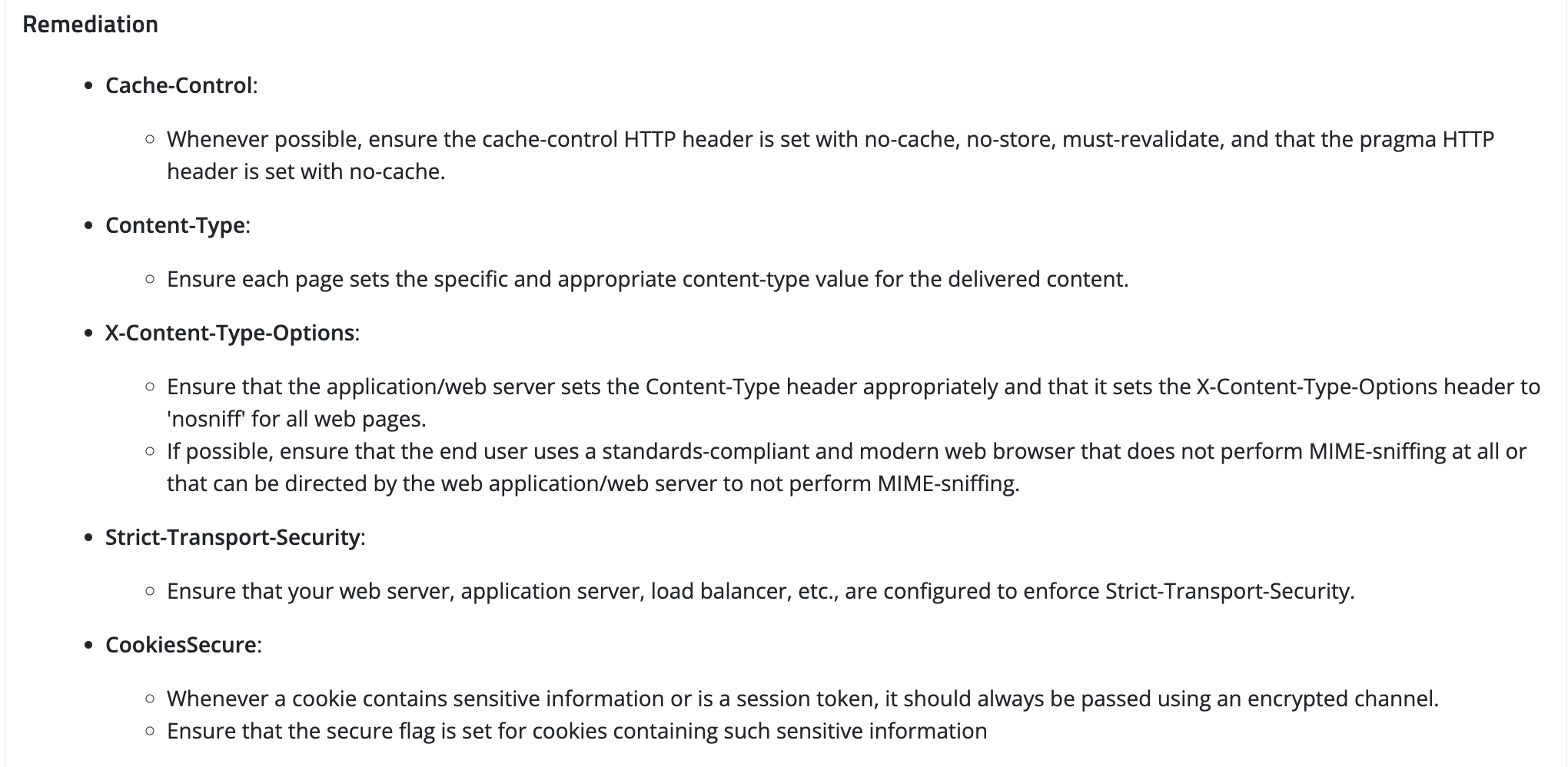
To mitigate header misconfiguration vulnerabilities in GraphQL APIs, it is important to ensure that all headers are properly validated and that access to sensitive information is restricted based on proper authentication and authorization. Additionally, it is essential to ensure that all headers are properly configured and that any unnecessary headers are removed to minimize the attack surface.
5. Denial of Service Attacks
GraphQL APIs are vulnerable to Denial of Service (DoS) attacks, which can overload the server and cause it to crash or become unavailable. An attacker can achieve this by sending many requests to the server, each requiring significant processing power and resources.
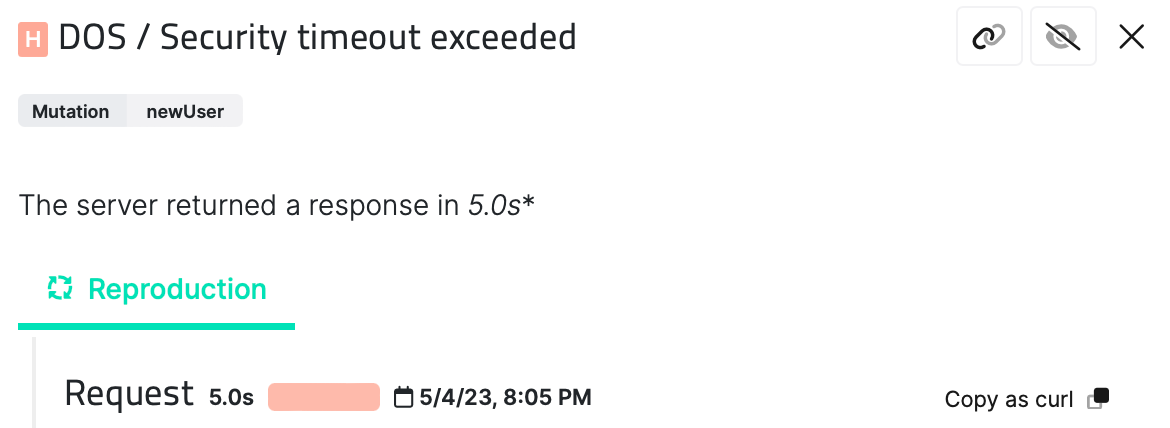
To prevent DoS attacks, it is essential to implement rate limiting and request throttling mechanisms. This involves limiting client requests within a certain period and determining the size and complexity of accepted queries.
Conclusion
GraphQL APIs can provide a powerful and efficient way to build modern applications but are not immune to vulnerabilities. To ensure that a healthcare company is HIPAA-compliant, taking the necessary measures to secure GraphQL APIs is essential. Organizations can protect themselves from potential data breaches and other security incidents by taking these precautions and by ensuring that their GraphQL endpoints are tested during every stage of the API development process.
At Escape, we are a big fan of GraphQL. Want to learn more about your API and verify HIPAA compliance? Let us assist you in creating a comprehensive inventory of all your APIs, including GraphQL, REST, and gRPC.
If you want to dig deeper into production-ready GraphQL, you can also check out our blog post on how to test GraphQL properly.
👉 Schedule a HIPAA readiness demo with our team to see how Escape simplifies compliance across your APIs.
💡 Want to learn more about GraphQL security? Check out the articles below:
