Webinar recap: The security mistakes everyone makes in M&A
Discover exactly how to avoid the common security pitfalls during M&A from our panel of experts, who are drawing from decades of experience in the field.
"Thank you for calling me an expert because in my mind that just means I've stepped on enough landmines to know where they are." - Curtis Koenig, Head of AppSec at Gen
From a security standpoint, mergers and acquisitions (M&A) truly can feel like a minefield. With a lack of complete information, no matter how thorough your due diligence is, to then having to integrate two often vastly different security cultures, to even trying to make sure your top talent doesn't jump ship, M&A presents an endless list of challenges just waiting to explode.
Our panel of experts have certainly seen their fair share of security obstacles throughout the M&A process and drew from those experiences to walk you through exactly how to effectively integrate security systems with as little friction as possible (though zero friction is probably impossible!). This article will introduce the panelists and their experiences, then walk through: the different M&A models that exist; the necessary due diligence process; how to manage security culture clashes, integrating data, and finally building your plan for your security strategy. With a mountain of invaluable insights to dive into, let's begin!
You can watch the webinar in full below:
The panelists' backgrounds
Chris Lindsey
Chris Lindsey is an Application Security Evangelist, with over 35 years of software development experience and over 15 years of direct security experience, in which he built a lot of application security programs from scratch. During his time working in security he has been on both sides of M&As, and "learned a lot through trial and error" on what works, and what doesn't.
Izar Tarandach
Izar Tarandach is currently a Senior Product Security Architect at a large entertainment provider, but has also held security-related positions at Datadog and Squarespace, among many others. He is also a threat modeling expert, and when it comes to M&A he has experience being the "critical eye from the inside" for a team that was the one being acquired, offering a valuable alternative perspective on the M&A process.
Curtis Koenig
Curtis Koenig, too, draws from decades of security experience, previously working at Snap Inc. and Booking.com and he is currently at Gen Inc. who are a leader of multiple security brands, including Avast, Norton, and more. He also has experience being on both sides of the M&A process, but also particularly going through M&A in a startup culture as part of Snap at startup.
Understanding M&A Models
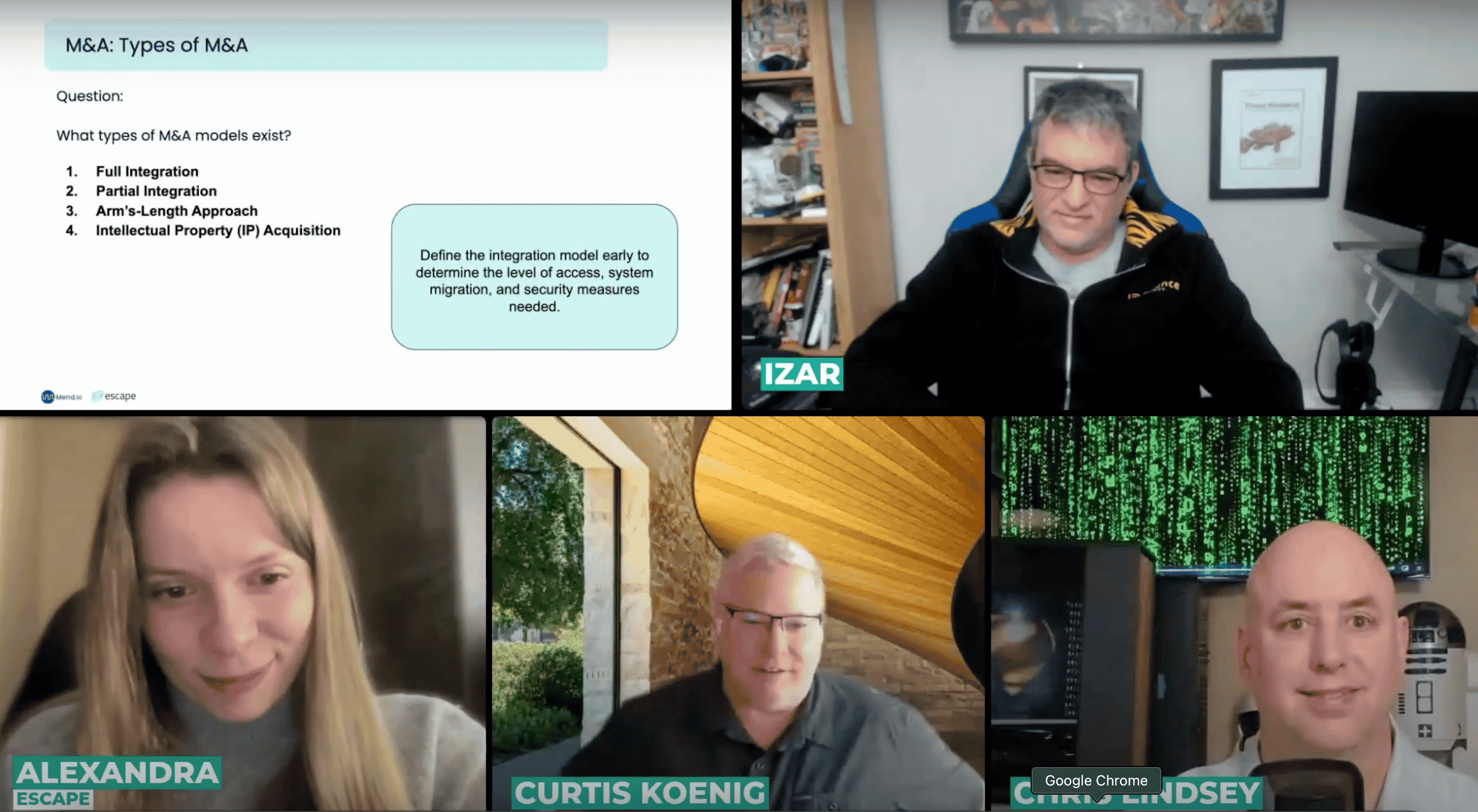
The classic conception of M&A is a complete integration, where everything from the two companies goes into the new joint entity. While this definitely happens often, it's absolutely not always the case. Sometimes, companies are partially integrated, meaning the acquiring company may only want a portion of the other enterprise or take certain pieces for their use and leave the rest alone.
This can go even further with an arm's-length approach, where a company may be acquired just for a period of time. Here, the acquiring company may just seek access to data and certain intellectual property but hold's the company at arm's length so they can cut the cords whenever necessary without having to undergo any significant structural changes.
The final approach is then just intellectual property acquisition where all the acquiring company is after is the intellectual property, but they leave the acquired company's operations, and for the most part their employees too, untouched.
"Knowing what type of acquisition it is changes the approach, it changes every aspect of what you're doing. Knowing what kind of integration you're gonna have with the company that you're acquiring is absolutely key for success down the road." - Chris Lindsey, AppSec Evangelist
The Due Diligence Process: M&A can be like a dating show
When discussing due diligence, Izar likened the first stage of M&A to a dating show, because of the getting-to-know-each-other phase where you exchange some information and evaluate as best as you can, but you cannot get a deep look.
In this early stage, regulations prevent you from being able to get access to all of the data you may need to make an in-depth evaluation. Here the law is mostly preventing companies entering into the M&A process and then backing out and running away with intellectual property. However, that means you're often only looking at financial data and the basic tech stack, which results in having to make decisions based on imperfect data.
So when is the right time to set requirements? As you get further into the M&A process, you get more permissions and you can dive deeper, but the key here is requirements and priorities are going to change through the stages of the merger or acquisition, as you move through the sections of data and identify new risks.
"I think one of the key things to keep in mind about M&A is that it's not that you set a plan and run, it's you set a plan and then you start and then you rewrite the plan, and then you get some and you rewrite the plan again." - Curtis Koenig
Use a third-party to conduct a security audit and evaluation
Chris Lindsey's key recommendation is to find a third-party company who can review the code and vulnerabilities. Because you're not privy to the source code in those earlier stages, using a third-party with no stake in the game to act as an intermediary allows you to uncover those landmines before you get too deep into the process, so you can know exactly what you're getting into bed with. Is the company riddled in tech debt or licenses? Is their security posture good? Do they even have security implemented?
Be aware of new regulations you may now be subject to
As you're peeling back the layers during due diligence, you also have to keep an eye out for regulations you have to adhere to that you previously may not have had to.
You may be acquiring a new user base with regulations in their country of origin that you have not previously had to consider. So, once again, it's about adapting your strategies as you go further through the process and uncover more, adapting your plan to account for changing requirements.
What the company being acquired should do during due diligence
When a third party is auditing, if the company being acquired is being unresponsive or uncooperative, the company that is seeking to acquire them will be able to see that. They'll see the masses of unread emails and response times.
But also, as Izar highlights, it is in the interest of the acquired company that the process succeeds, and a key way to ameliorate this process is having good documentation. If a company can offer a portfolio outlining what they have done with security and show everything is in order and up-to-date, it can make the process that much faster and you can then start closing the gap between the acquiring company's standards and expectations and what the acquired company has in place.
For the long-term: Have a risk-register and regularly review it
Everybody who is part of your M&A team needs to be identifying risks and ranking them, and getting them on a sheet and having a regular discussion about them.
Of course, the way this is formalized can depend on the company. For example, a startup may not have the bandwidth for a much more formalized process or register, but it comes back to having that documentation in place that recognizes what are the things that could go wrong, and what is being done about them, regardless of how formalized it is.
How to manage the human aspect of M&A: communication and merging security cultures
"One of the things you should be thinking about is if the cat comes out the bag, find a way to at least let your top talent know what's going on, and keep them in the loop as much as you possibly can simply because if you don't, you're gonna lose your best talent." - Chris Lindsey
During M&A there typically isn't communication to anybody outside of a select few, but when something leaks, often developers and knowledge experts may be the first to jump ship. An important strategy here is to create a day minus one plan on what communication should look like once the M&A has to be announced. You need to be ready to communicate on questions like whether you're going to freeze your code or escrow it, or having a plan to monitor that people continue to act as they're supposed to.
Then comes merging the security cultures of the two companies. This can also be a particular challenge with a startup because they may not always keep track of modeling everything, so you have to make sure they're integrated securely without everyone leaving the company.
"You're basically taking a problem that already exists in your organization, which is how do I scale security? How do I get different teams that work with different parts of the tech to have the same level of security, to care about the same things, and so on. And now you're getting a completely foreign body, and inserting it into the organism that you are taking care of." - Izar Tarandach
Here you have to consider whether both security teams have the same values and look at the risks the same way, and even if they do, do they pursue them with the same processes and at the same depth. This is where the day minus one plan is again important, as it's crucial to anticipate these frictions so you can mitigate them.
The best way to achieve this is to have transparency from the acquiring company. From literally the day after the acquisition, if the two sides can come together and understand each other's tooling, processes and practices, you can work together to adopt the best practices from both. And this is what you can use to shape your plan going forward. Here, the leadership play an important role in implementing those security practices and amalgamating the best of both cultures.
And security cultures aren't exclusive to security teams, as the company you're joining with may have developers with a "just drop a firewall in front of my code" mindset. In this case, Chris Lindsey re-highlights the value of transparency. Now on day two or three post-acquisition, application security should have an open discussion with the developers about how they approach security, how they do scans etc., and emphasize it's not a blame game but working towards the common good of getting their code integrated into the existing processes that work.
By having these transparent conversations, people are much less likely to jump ship if they have an idea of exactly what is happening and what the roadmap looks like.
Short and long-term priorities
During an M&A, security teams often feel overwhelmed with an influx of information—akin to "drinking from a fire hose." However, it's crucial to slow down and approach integration in a measured way. While regulatory, operational, and communication challenges demand attention, security teams must carefully assess and address new risks without rushing decisions.

The focus should be on strategically deploying security assets rather than making immediate changes to the tech stack. In the early phases, you should concentrate on gaining visibility into the new environment and planning what you will integrate and how you'll deploy it, and then plan the next thing to deploy and keep going from there. In the rare cases of acquiring for IP only, you may make tech stack decisions but usually decisions about retiring or modifying infrastructure should only be made after gaining full control and understanding of the acquired entity, when you're fully certain you don't need something; this can always come much later down the line.
Integrating data
One of the biggest risks is navigating different regulatory environments. Acquiring a company in another country could suddenly expose you to new laws and compliance requirements, and something as simple as backing up data together could trigger unexpected legal obligations. Before merging or moving any data, companies need to carefully assess where the data resides, who has access to it, and what laws apply - otherwise, they might find themselves violating international regulations.
The panel emphasized that, just like with security integration, data integration doesn’t have to happen immediately. Companies should take a phased approach, ensuring compliance before combining systems. Rushing to centralize data can lead to serious legal headaches—such as becoming subject to unexpected banking or privacy laws simply by connecting certain databases.
The key takeaway? Talk to your lawyers. International and privacy counsel are essential allies in ensuring that your data stays compliant. If you’re unsure about the legal implications of integrating certain datasets, ask the experts before taking action.
"The worst thing in any security is assuming you know the answer. - Curtis Koenig
Concluding thoughts
"One of the people that's most important for you to talk to is future you." - Izar Tarandach
You have to consider what are your problems today, and what will your problems be tomorrow, and build out that plan of how you will tackle everything in a measured and phased way. It's key to fight that instinct of trying to solve everything in one fell swoop because if you don't give yourself the space to spread everything out, it will make the whole process much harder than it needs to be, especially because you need to give yourself the space to account for the new risks that arise as you get deeper into the process and uncover new information.
"And it always takes longer than planned." - Chris Lindsey
To conclude, each panelist shared their most critical piece of advice for navigating security in M&A:
- First, do no harm. Prioritize stability in security integration and avoid rushing into changes that could introduce risks. (Chris Lindsey)
- Be curious, not judgmental. Maintaining your curiosity, asking the right questions, and gathering all relevant information is crucial for making informed security decisions. (Curtis Koenig)
- Communication is key. Having transparent discussions with security teams, developers, and stakeholders make the integration process so much easier and smoother. (Izar Tarandach)
💡 Want to discover more?
Webinar Recap: How to combine SAST and DAST for complete application coverage
What is wrong with the current state of DAST? Feedback from my conversations with AppSec Engineers
