The State of GraphQL Security 2024
Insights from 13,000 GraphQL API issues: Read our deep dive into the current state of GraphQL security.
Are GraphQL APIs truly secure in 2024?
We have wondered about this since the beginning of the year, so we decided to dive in and find out! To get the answers, we scanned 160 major public GraphQL endpoints with Escape's advanced GraphQL scanner.
Want to know what we discovered? The findings highlight some serious concerns about GraphQL security today. We've laid it all out in our new State of GraphQL Security 2024 report.
Methodology
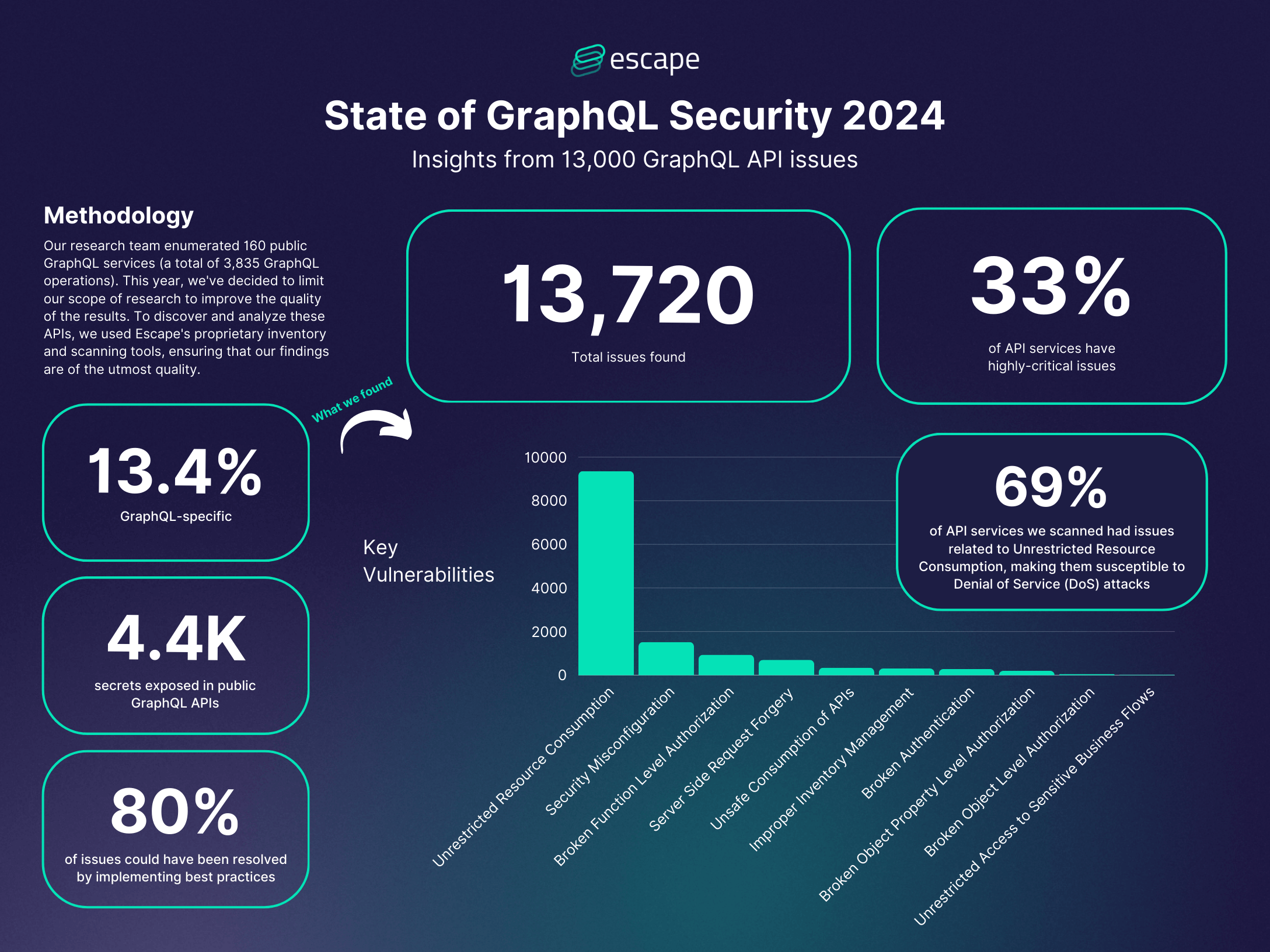
To conduct our research, our security research team enumerated 160 public GraphQL services (a total of 3,835 GraphQL operations).
Operations: Specific GraphQL operations, such as queries or mutations, e.g., getUsers or createUser.
This year, we've decided to limit our research scope to improve the quality of the results.
To discover and analyze these APIs, we used Escape's proprietary inventory and scanning tools, ensuring that our findings are of the utmost quality.
To avoid interfering with the applications we audited, all scans were run in read-only mode, unauthenticated, and with conservative rate limits.
Consequently, most of the findings presented in this report are exploitable remotely without any specific privileged authorization token.
What we found
- We discovered 13,720 issues of various severity, with 33% of API services having at least one or more high-severity issues based on CVSS classification.
- Alarmingly, we found 4,400 secrets exposed in public GraphQL APIs.
- Nearly 69% of the API services we scanned had issues related to Unrestricted Resource Consumption, making them susceptible to Denial of Service (DoS) attacks.
- Approximately 11.1% of the services experienced issues associated with Security Misconfiguration. Improper customization and configuration options in GraphQL can create security gaps if not properly managed.
- 13.4% of the vulnerabilities found are specific to the GraphQL language and its frameworks - showing that organizations do not correctly manage the new risks associated with the technology yet.
- 80% of issues could have been resolved by implementing best practices such as access control with authorization and authentication, input validation, and rate limiting to block brute-force attacks.
If you think that’s impressive, just wait until you see all we’ve included in our new State of GraphQL Security 2024 report.
Download it today to look into top GraphQL security issues and get actionable recommendations on securing your GraphQL APIs 😉
Stay secure,
Your Escape team
