Secure your GraphQL API within your CI/CD
Enhance CI/CD security with Escape GraphQL integration. Detect vulnerabilities early, prevent costly consequences, and turn DevOps into DevSecOps
When thinking of the CI/CD pipeline, you rarely think of security since it is atypical for those pipelines to include security checks. The CI/CD pipeline is where code is written, tested, deployed, and even monitored. All that is possible without giving security a thought, but disregarding security in the CI/CD pipeline would lead to costly or catastrophic consequences.
Escape GraphQL security solution now extends to the CI/CD flow, helping DevOps turn into DevSecOps.
Our latest study on 3000 different endpoints showed that one of the most abundant security flaws was found within the access control configurations (or "who can do what?"). Digging a little further, we found out that most access control vulnerabilities are introduced to the endpoint later in the development process. We tackled this problem in our latest feature Escape’s integration in CI/CD.
Features
Escape's latest feature is a way for you to integrate its scanning functionalities within your CI/CD pipelines.
Two types of CI triggers are supported:
- Run a scan at every commit being pushed on a specific branch
- Run a scan before deploying the test environment onto production
This integration includes every regular feature of the security scan from Escape. Especially the scan triggered using this method will use the application configuration on the Escape platform. It will notify your team at the end using whatever contact channels defined for this organization (see notifications).
Intended usage
Escape is effortless to integrate into your CI/CD at two different steps of your Gitlflow.
- Run a scan at every commit being pushed on a specific branch
- Run a scan before deploying the test environment onto the production
This integration includes every regular feature of the security scan from Escape. Especially the scan triggered using this method will use the application configuration on the Escape platform. It will notify your team at the end using whatever contact channels defined for this organization (see notifications).
Quick Example
We will make usage of the presented example in our documentation. We want to set up the Escape app to trigger a non-blocking scan every time a commit is pushed on a branch.
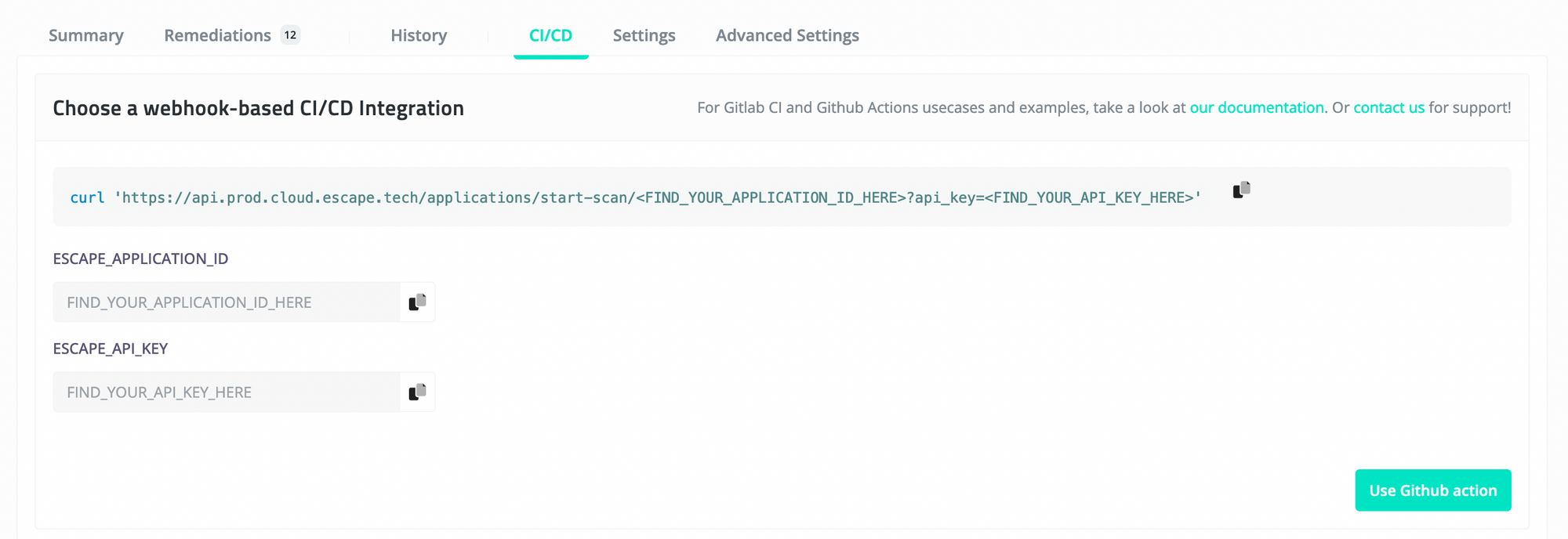
Then you'll need to add this to your Gitlab CI file:
Escape:
stage: post-deploy
needs: deploy # name of your deployment job
variables: # you can find those secrets directly in your Escape Application Settings
- ESCAPE_APPLICATION_ID: $ESCAPE_APPLICATION_ID
- ESCAPE_API_KEY: $ESCAPE_API_KEY
image: node:18-alpine
before_script:
- npm install -g @escape.tech/action
- npm show @escape.tech/action version
script:
- escape-action
allow_failure: true
only:
refs:
- merge_requestsAnd voila! You have configured a security scan that will be triggered every time a commit on the targeted branch is pushed.
We made it extra simple, and thoroughly documented. We are actively improving this feature, and our discord server is always open for needs, suggestions, or thoughts. Join it here !
Or better yet, sign up for a free trial account to explore how Escape can help you with your security issues. Our comprehensive solution identifies and mitigates over 104 advanced security issues, including resolver performance, tenant isolation, sensitive data leaks, injections, error handling, compliance, and more.
You can't secure what you can't see. Let Escape help you build a comprehensive inventory of all your APIs, including GraphQL, REST, and gRPC.
Want to learn more about GraphQL testing?
Check out our blog posts below:
