MCP Endpoint Discovery & External Scanning in Escape ASM
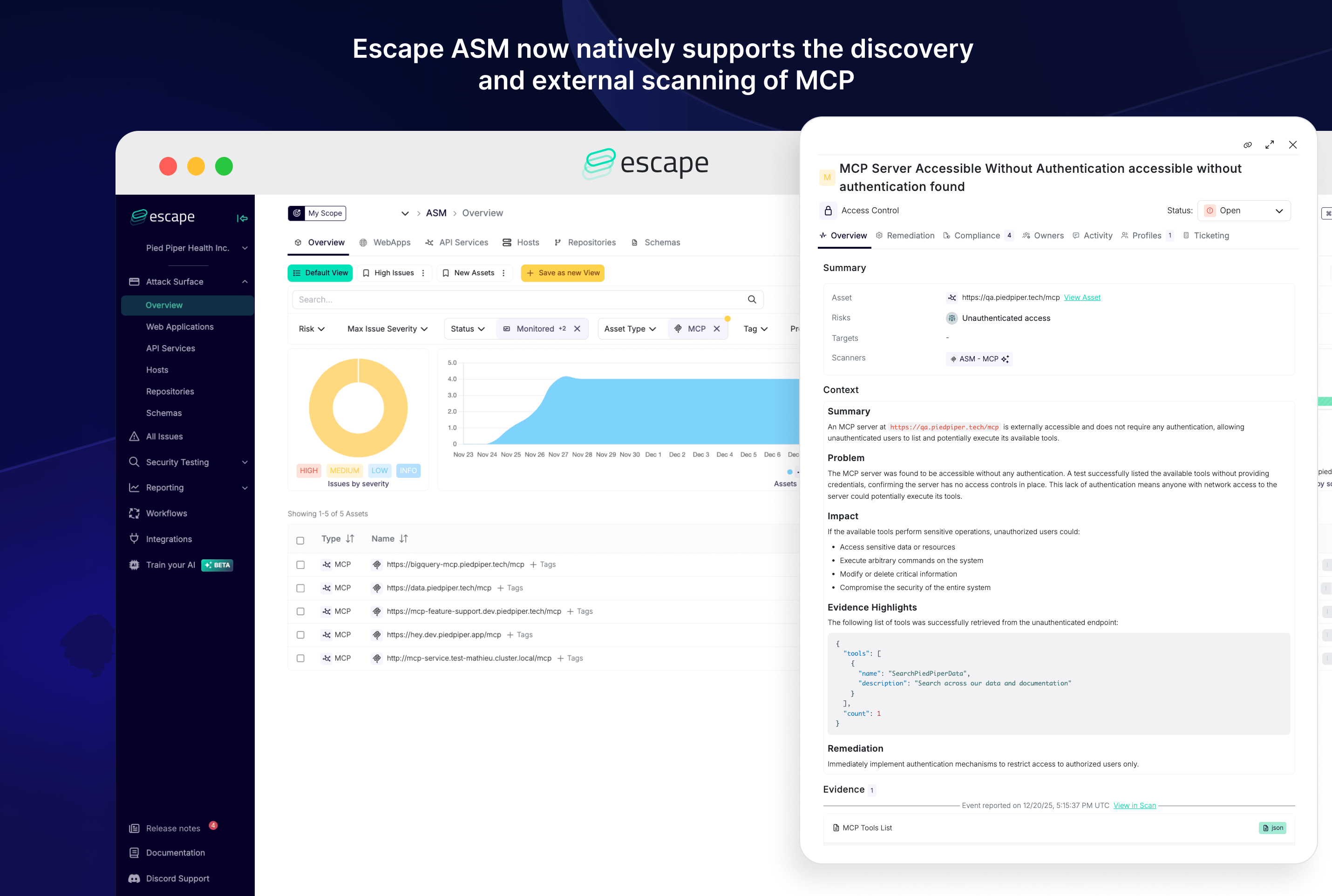
Escape ASM (Attack Surface Management) now natively supports the discovery and external scanning of unauthenticated MCP (Model Context Protocol) endpoints, extending discovery coverage to a new generation of AI-native APIs and LLM infrastructure.
As organizations increasingly adopt MCP to connect large language models (LLMs) with tools, data sources, and internal services, new externally exposed attack surfaces are emerging, often without clear visibility or security controls.
This update brings MCP endpoint discovery directly into Escape ASM’s continuous discovery and monitoring pipeline.
Why MCP Discovery and Security Matters
The rise of Model Context Protocol (MCP) is accelerating how teams build AI-powered applications. But with that speed comes risk.
As MCP servers become internet-facing, security teams must contend with:
- Unauthenticated MCP endpoints exposed to the public internet
- Misconfigured MCP servers connecting sensitive tools and data
- Blind spots in AI-native infrastructure not covered by traditional ASM
Without visibility, these endpoints can become high-impact entry points for attackers.
Security teams need to:
- Know where the MCP endpoints are exposed
- Detect unauthenticated or misconfigured MCP servers
- Continuously monitor AI-native attack surfaces
Escape ASM now addresses this gap.
What’s Included in This Release
For this initial release, we focused on the Attack Surface Management (ASM) layer, fully integrated into existing scans.
Key Capabilities
Automatic MCP Endpoint Discovery
- MCP endpoints are automatically detected like any other internet-facing asset
- No manual configuration or tagging required
External MCP Surface Scanning
Escape analyzes exposed MCP servers and configurations, including:
- Detection of unauthenticated MCP endpoints
- Identification of externally reachable MCP services that may introduce security risk
This helps teams quickly prevent MCP sprawl and identify high-risk MCP exposures before attackers do.
Setup: No Configuration Required
There’s no setup required to enable MCP discovery and scanning.
- MCP endpoint discovery is enabled by default in Escape ASM
- Existing ASM users automatically gain MCP coverage
- New MCP endpoints are continuously monitored as they appear
What’s Next: Design Partners for MCP Security Testing
This release marks the first step toward full ASM + AI pentesting coverage for MCP-based architectures. We’re actively looking for design partners using MCP in real-world environments to help shape the next phase of Escape’s dynamic application security testing for MCPs.
Design partners will get:
- Early access to authenticated MCP testing
- Influence over attack scenarios and coverage
- Direct collaboration with the Escape product team
If you’re building with MCP and want to help define the future of MCP security testing, reach out to your dedicated Escape contact!
FAQ
Is MCP scanning enabled by default?
Yes. If you’re already using Escape ASM, MCP discovery and scanning are automatically included, no setup required.
How does Escape ASM discover MCP endpoints?
Escape ASM automatically detects MCP endpoints as part of its continuous agentless asset & API discovery, without requiring agents or manual configuration.
Why are MCP endpoints a security risk?
MCP endpoints often expose powerful capabilities—tool execution, data access, or internal services. If left unauthenticated or misconfigured, they can become high-value attack surfaces for external attackers.
Does Escape test the MCP endpoints for security?
Not yet. This initial release focuses on unauthenticated and externally exposed MCP endpoints. MCP security testing is planned and currently open to design partners. Reach out to your dedicated Escape contact or at ping@escape.tech if you wish to participate in the product development.
💡 Looking for more content? Explore these related articles:
