An Analysis of Kuppinger Cole’s Selection Criteria for API Management and Security
Discover how Escape fits the Kuppinger Cole selection criteria of API Management and Security Solutions.
It is essential to know what to look for when examining the various API security solutions present on the market. Those looking into acquiring a solution for their API security needs may struggle to know what criteria to follow when choosing their provider of API Security. To help in this, Kuppinger Cole, the advisory service specialized in identity and security, has published a Buyer’s Compass focused on API Management and Security.
In this article, we will look at the functional selection criteria it described from the standpoint of an API Security tool and determine which criteria are more or less important to clients in our opinion.
Functional Selection Criteria
API Management-Focused Criteria
While management-focused criteria are important for buyers looking into a way to manage and categorize their APIs, for our purposes, we have decided to focus on analyzing the criteria that have to do with API Security specifically. As we are focused on API Security solutions, we have decided to ignore the following:
- API Design
- API Productization and Monetization
- Microservice Management
- Scalability and Performance
Let’s analyze the criteria that have to do with API Security.
Identity and Access Control
This criterion entails that a solution should be able to keep an organization's APIs secure by supporting multiple identity types and protocols and making context-based access decisions. In essence, the solution should provide visibility and management capabilities to determine who can access APIs and what actions they can perform.
This is very important to API Security as it ensures that only the right people have access to your APIs and that sensitive information is protected within this framework. This criterion also helps determine who created certain APIs and who can access them.
How we approach it at Escape
We know how crucial access control is. Escape allows you to finely manage who can view all your applications, start new scans, add integrations, or invite new members. You want to make sure only the necessary people can see exposed sensitive data or critical vulnerabilities of your APIs that still might need fixing. Whether it's your junior developers, senior security engineers, contractors, consultants, or external partners, you retain control over who has access.
From Fine-grained Authentification, RBAC (Role-Based Access Control) to Identity Federation, our goal is to empower your organization with lots of helpful features that streamline operations, enhance security, and improve the productivity of your staff.
- lowers the memory burden for your staff
- provides valuable data to track user activity for easier problem-solving
- efficiently manages app access
We go beyond providing your fine-grain access control; we also show who controls API development on your side.
We have included a feature in our API inventory that allows you to see the owner of APIs that may cause risk within your company. We even provide automatic remediations that can be sent to the API developer. Hence, it is possible to contact the owner if there is an issue directly.
API Vulnerability Management
Here, we are looking at the discovery and prioritization of API vulnerabilities to enhance your organization's general security. This may be the most important criterion presented by Kuppinger Cole, as it has to do with finding and fixing security problems within the APIs used across your entire platform.
If an API security provider does not have this included in their solution, it means there will be no help in preventing hackers and attackers in general from exploiting the weaknesses that may be present in your APIs. It is also important to be good at this. Many tools in the market today suffer from “False Positives”, meaning they will alert an organization of an issue that is not necessarily a problem. Moreover, intelligent prioritization of discovered vulnerabilities by business risk assessment improves both developer productivity and overall security posture, making it all the more crucial.
How we approach it at Escape
As an API Security Solution, our unique discovery approach sets us apart from the rest. We go beyond merely detecting weaknesses; we use our innovative algorithm, rooted in Feedback-Driven Semantic API Exploration (FDSAE) principles, to autonomously generate legitimate traffic to test API's business logic. Using techniques like Sourcing Inference and Strong Typing Inference, we ensure the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Our commitment to best practices extends through our compliance matrix, ensuring not only conformity but excellence in security standards which goes beyond the OWASP Top 10 and shows how your product aligns with a variety of regulatory standards including: PCI-DSS, GDPR, SOC 2, PSD2, ISO 27001, NIST, and more.
.webp)
Our API vulnerability scoring method is precise and thorough. We determine the severity of an issue based on how many of more than 160 security tests it passes. Each test contains different attack scenarios and payloads that’s adapted to the logic of your application.
It also has an assigned severity level, categorized by its relevance to areas such as Access Control or Information Disclosure and the likelihood of exploitation by attackers.
Moreover, our prioritization funnel meticulously tracks the progression of security issues at every stage. From the total count of security issues across your applications to those pending resolution, exposed externally, discovered without implemented authentication, marked as critical, or having a high business impact, we provide comprehensive visibility. For each stage, you can filter vulnerabilities, review their details, and understand how they were discovered.
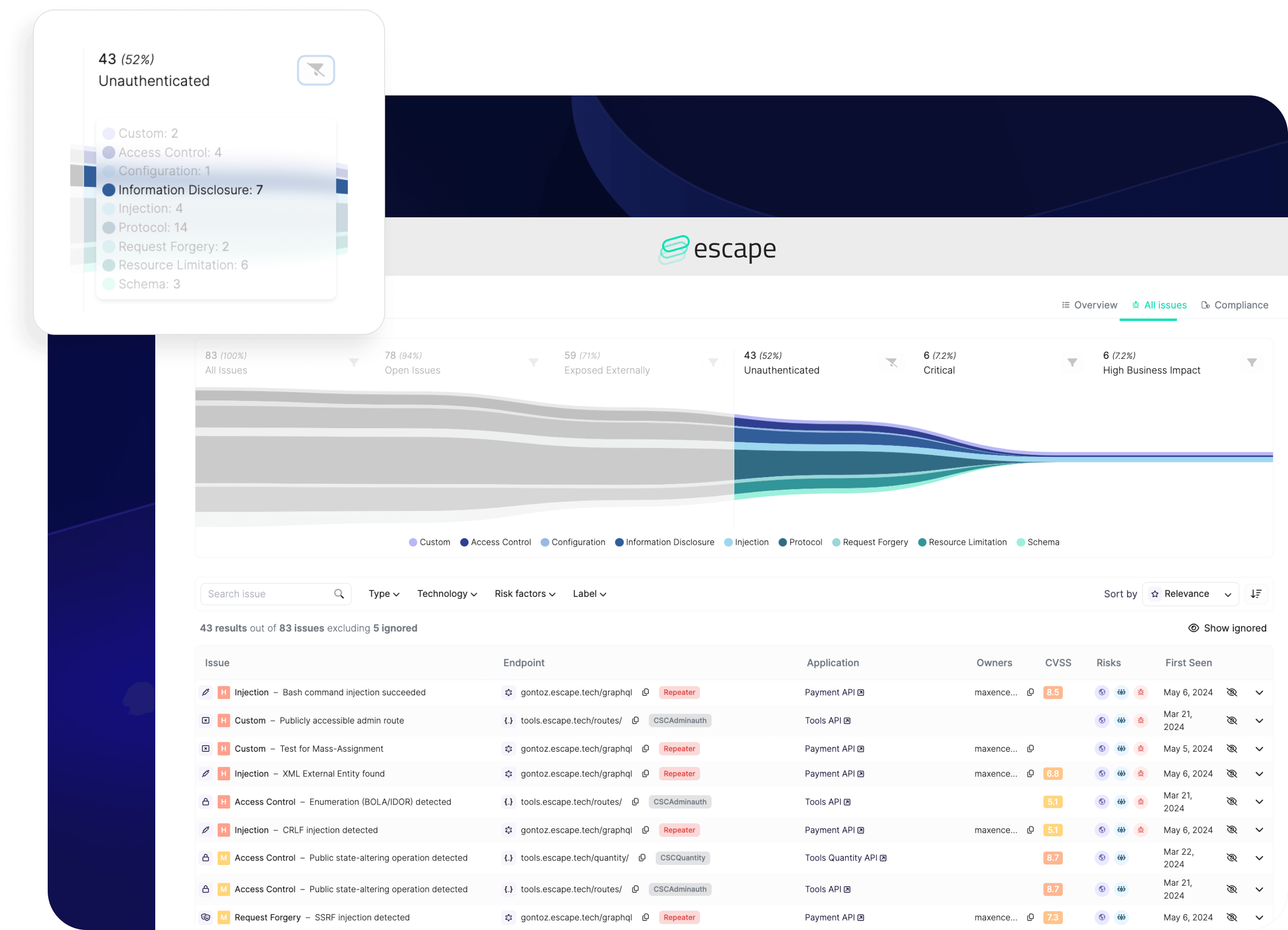
With our low false positive rate, you can trust the accuracy of our findings. If an occasional false positive does arise, it's easily dismissed and excluded from future scans, allowing you to focus on genuine security threats.
Analytics and Security Intelligence
This criteria ensures the solution vendor continuously monitors and responds to security threats and suspicious activities. Thus, an API security solution should be able to keep an eye on all API activities to spot and stop or prevent attacks.
This is important as it allows you, as a client, to be aware of security threats and respond to them in a timely and secure manner. This allows users of an API security service to actually experience security. This criteria is how you can detect and respond properly and rapidly to security threats, preventing damage to your software or platform.
How we approach it at Escape
Threat detection is at the heart of our solution. Like mentioned above, Escape allows you to prioritize your most critical API by business use, data sensitivity, and exposure, and suggests automatic remediations so that you are able to fix these issues immediately.
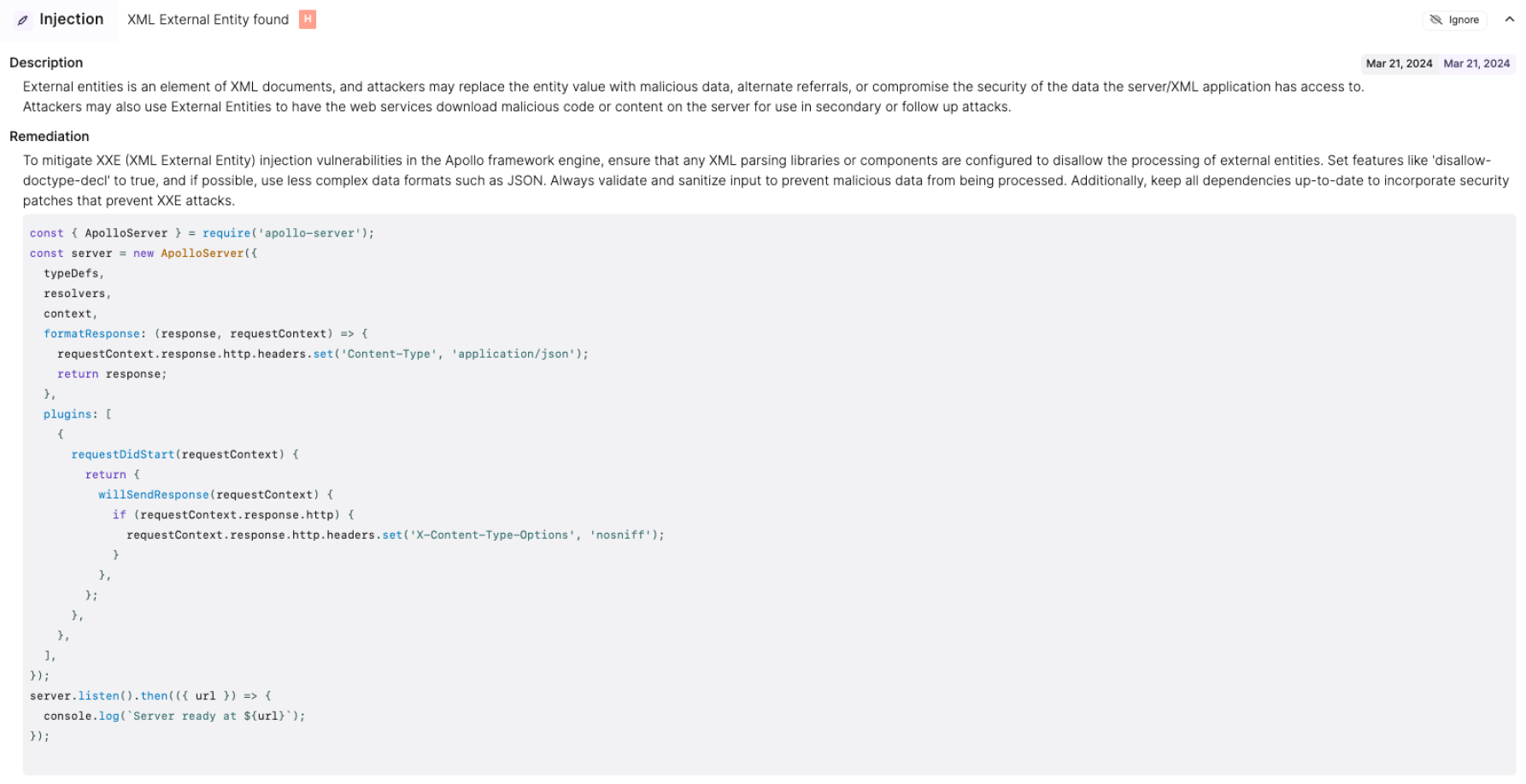
Moreover, you can set up the frequency of scans yourself, so you can choose between continuous monitoring, monitoring when a new feature is deployed, or monitoring at a specific pace.
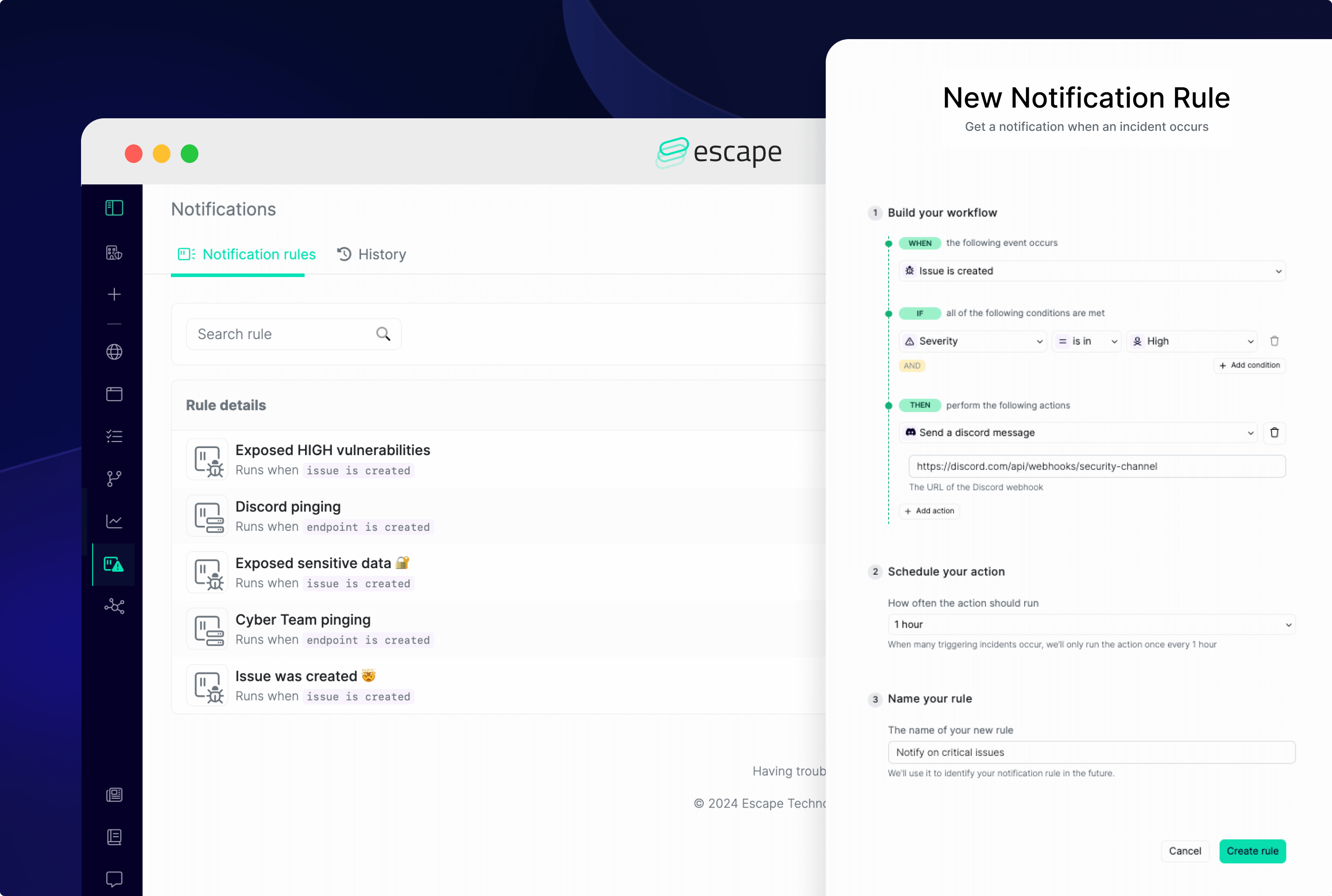
We also offer you the possibility of setting up specific notification rules, which lets you get notified about what really matters for you and your business. By implementing tailored notification systems, you can inject a sense of urgency into your incident response processes, ensuring a prompt identification of the issue and a quick remediation start. This feature ensures you can entirely customize scan alerts to your needs so that you can truly focus on what matters to you
Integrity and Threat Protection
To avoid different kinds of attacks, the software provider needs to ensure a multi-layered approach to securing your APIs. These various threats should, for instance, include transport-level and protocol-specific attacks. This criterion focuses on the importance of protecting your APIs from different types of attacks.
Similar to some previous criteria, this is crucial as it ensures the safety of your platform from attackers who may target certain APIs. This criterion wants to ensure that your APIs remain safe and reliable even if you are under attack by malicious actors.
How we approach it at Escape
At Escape, we focus on making sure APIs are secure before they're actually being deployed in a real-time environment. We advocate strongly for shift-left development practices since early detection and mitigation of vulnerabilities significantly reduce the risk of security breaches.
Our method of analyzing possible risks within your platform uses an AI-powered security scanner that proactively detects all of OWASP's Top 10 risks and more, including advanced security flaws, across all your APIs, like:
- Broken Object Level Authorizations (BOLAs),
- Broken Function Level Authorization (BFLAs),
- Insecure Direct Object References (IDORs)
We are able to scan multiple API types with incomparable coverage for GraphQL. Contrary to other scanners, Escape handles GraphQL natively and not as another HTTP API. Even better, our engine is capable of suggesting code fixes for all findings and all GraphQL engines to maximize developer productivity when fixing issues.
We aim to deliver the most developer-friendly GraphQL security solution on the market, with significantly broader coverage and more relevant results than the competition. Our customers observed a reduction of the API security risk by 50% in the first weeks of usage.
We have also added a feature so that you can effortlessly write and integrate custom checks to automate security tests tailored to your APIs. You can send custom requests to any URLs within your organization. This feature is particularly useful for running static security assessments on your web applications, identifying regression bugs, or investigating specialized in-house security concerns.

Strong Internal Security and Access Management
Kuppinger Cole also expresses that a vendor should be able to secure administrative and developer access with role-based control, multi-factor authentication, and audit trails. Basically, they say a vendor should be able to secure access to the tools and systems used to manage your APIs.
The importance of this criteria is almost self explanatory, it aims to prevent unauthorized access and ensures that only trusted users can make changes to the APIs.
How we approach it at Escape
On the customer side, with Escape's Role-Based Access Control, you can define user roles and their corresponding permissions in a granular manner and tailor access privileges to match specific job functions within your organization. This level of customization enhances security and allows for efficient collaboration and streamlined workflows, ensuring that every team member has access to the resources they need, precisely when they need them.
We define several out-of-the-box roles that grant specific sets of permissions, catering to various organizational needs. Escape's RBAC enhances security by ensuring users only have necessary permissions, while streamlining user management and adapting easily to organizational changes. Additionally, it provides transparency in access control, aiding in audits and reviews.
Escape's audit logs feature offers an extra layer of transparency, allowing you to track all user activities and make informed decisions. One of the key benefits of the Audit Logs is the ability to monitor changes made to critical data. Whether it's configuration changes or administrative changes, the Audit logs capture every alteration, including the date, time, and user responsible. Deleted objects retain a separate action record. This level of detail allows you to identify any unauthorized changes and take appropriate action quickly.
Scalability and Performance
This criterion expresses that an API security solution should ensure continuous availability and performance of APIs, even under high load or a denial-of-service attack, which is essential for API management. While these criteria primarily focus on management, we have decided to include it in the security aspect as well.
Essentially, it's essential to ensure that your APIs can handle a large volume of users and data without slowdowns or crashes, as system failures can serve as entry points for attackers.
At Escape, we prioritize mitigating Denial of Service attacks before APIs are released into production. Our approach focuses on preemptively securing APIs to maintain smooth operations. By addressing these challenges early in the development lifecycle, we enhance both reliability and security for our clients.
How we approach it at Escape - focus on GraphQL APIs
From a security standpoint, Escape can prevent Denial of Service or batch attacks that may occur through a GraphQL alias, in contrary to tools responsible for securing web applications like firewalls and rate limiters that cannot detect abnormal activities. Our GraphQL Security scanner allows developers to find and fix vulnerabilities in GraphQL applications during the development lifecycle before they even reach production!
Here is a useful infographic on everything you should know when you want to secure your GraphQL APIs:
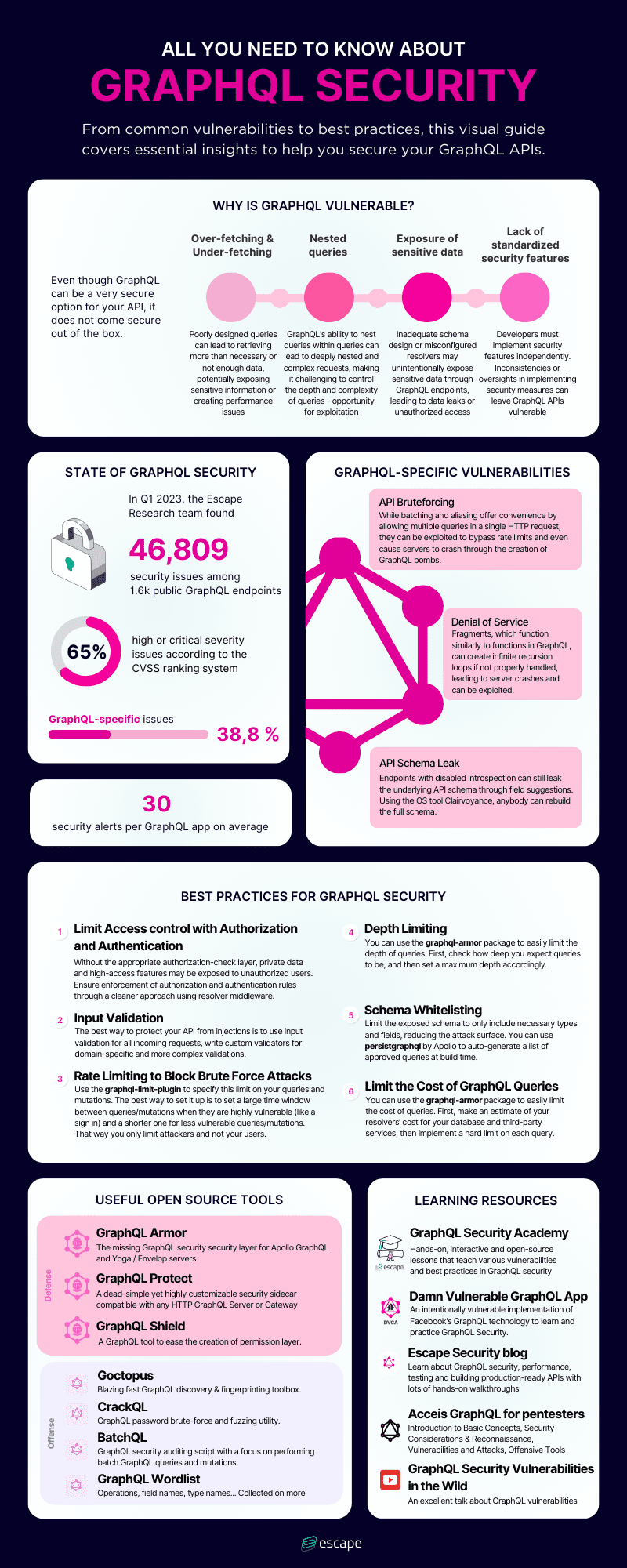
Our comprehensive solution identifies and mitigates over 104 advanced security issues, including resolver performance, tenant isolation, sensitive data leaks, injections, error handling, compliance, and more. Thus, ensuring you have the most secure possible platform in a continuous manner, and will reduce the risk of vulnerability from DDOS attacks.
Conclusion
Kuppinger Cole’s Buyer’s Compass provides a solid roadmap for selecting the right API management and security solution. By balancing both functional and security requirements, it ensures that the chosen solution supports your business goals while offering the protection your APIs need.
For organizations looking to improve API security, the key criteria highlighted above are essential—ensuring that only authorized users have access, vulnerabilities are actively managed, threats are continuously monitored, and administrative control is tightly enforced.
At Escape, we take these priorities to heart. Our solution incorporates a proprietary AI-powered algorithm for business logic testing with Escape DAST for all modern frameworks, agentless and automated API discovery, and remediation code snippets, so you not only find but also fix your vulnerabilities.
Choosing the right API security solution isn’t just about solving today’s challenges—it’s about preparing your organization for the future. By keeping these key criteria in mind, you’ll make a more informed decision that sets you up for long-term success and resilience.
Start securing your APIs with Escape DAST
See how Escape helps you build your API inventory in minutes, automate API schema generation and business logic security testing with its proprietary algorithm
Get a demo💡Want to learn more? Discover the following articles:
